
Information Technology Control and Audit
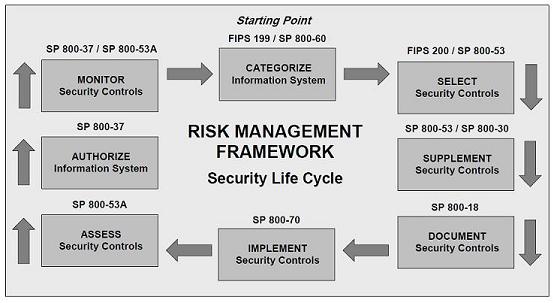
The audit is utilized as a tool to check compliance control based on standards such as ISO 27002 or NIST 800-53 etc. Some other terms which are not sometime rigorous audit have been used to asses controls are gap analysis, benchmarking and control review.
Scoping sets the boundaries of the audit, where dependencies are marked and exclusions are sorted out.
The consultant/team lead that has a thorough understanding of security risk management ought to carry out these reviews. The quality of the work depends on correct scoping, fieldwork assignment, and appropriately reporting the findings to management.
Team lead should have a clear understanding of audit scope before the initial briefing to client. Basically what exactly the client wants and who are the target audiences in the final report and presentation. Clear understanding of the scope includes making sure that the whole organization is included in the audit or just part of it. Before starting an audit, the auditor should have a complete list of assets included in the scope. Sort the assets list into different group of infrastructure which could be handed over to technical consultant for validation of the controls. At this point team lead should point out to technical consultant, the minimum number of assets which are required to be validated to satisfy sampling requirement.
Scope of final report/presentation should be clear regarding the list of non-compliance, prioritized recommendation or action plans which needs to be included in the report. During presentation of the findings, and to keep C level folks interested in the presentation, presenter needs to relate the findings to business risk and avoid using security acronym.
Scoping will take into account the length of the time available for field work, analysis, reporting and size and competence of the team to perform a successful audit. Especially if limited time is available for field work, the competence of the team matter to cover various infrastructure, to validate and document the controls effectively.


![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=518072a3-a5c1-4c5e-852e-867fa55083e6)
![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=8310531f-dd51-48b2-9dca-4a52b857f987)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=75ca6076-5285-4eaa-9251-01afd6576cbb)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=e4df808e-97bc-4fa0-a3a0-4ff663bf0824)


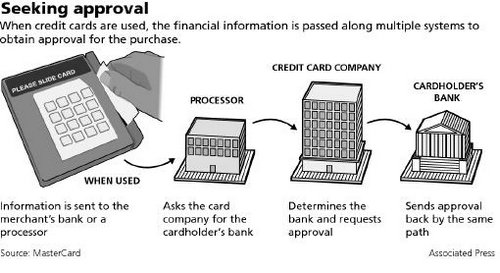
 Cloud computing is the future of the computing, which happens to provide common business applications online that run from web browser and is comprised of virtual servers located over the internet. Basic idea behind cloud computing is the accessibility of application and data from any location as long as you are connected to the internet. Cloud computing makes the
Cloud computing is the future of the computing, which happens to provide common business applications online that run from web browser and is comprised of virtual servers located over the internet. Basic idea behind cloud computing is the accessibility of application and data from any location as long as you are connected to the internet. Cloud computing makes the![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=e7f7ca92-d521-4be7-b5c4-dfc3282c607f)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=f0daa4e0-f026-4af4-8494-36325d4cff42)
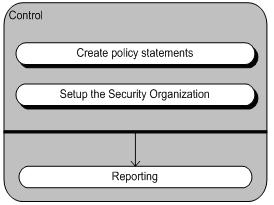
 Usually security breach occurs due to lack of basic security controls or lack of effective control which is not relevant over the time. Security controls also disintegrate over the time due to lack of maintenance and monitoring.
Usually security breach occurs due to lack of basic security controls or lack of effective control which is not relevant over the time. Security controls also disintegrate over the time due to lack of maintenance and monitoring.![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=4734aa88-27e0-45d9-a802-a6d2377faf3b)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=e39877b8-3658-48d6-a82b-d789a6584701)
![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=387e665b-1265-4cae-aa94-ab7d9c93d400)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=d72b1680-f22d-43af-a9d0-a6e58dec37a9)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=44c6818b-40c1-4e78-9e2d-f4a92edb802a)


![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=c0f0d90e-bec6-4fb0-8cc1-da10b6d29d91)
![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=1119f164-7e48-4ad2-b112-d80cd3808a1d)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=895f8198-7497-4c41-9dc5-c391622d8afe)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=0216a272-b6d6-471e-8232-9c849b4c867c)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=fdb4c0e1-9dfb-4fb9-b9cc-67ec87f659a8)



