Aug 21 2008
InfoSec Threats

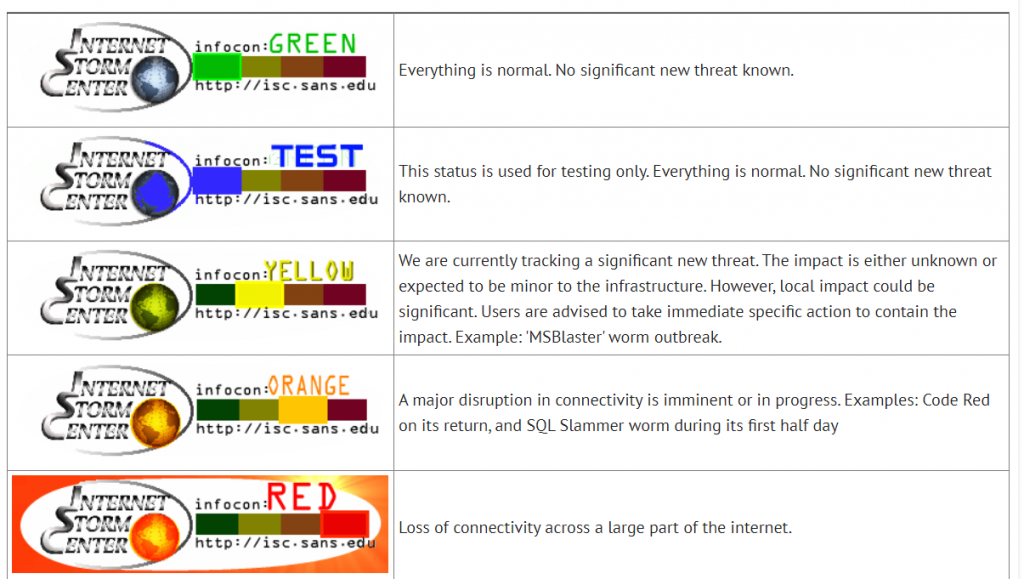
The daily Infocon alert
The daily Infocon alert Live Cyber Attack Threat Map | World’s Biggest Data Breaches & Hacks | CVE Trends | Check if you have an account that has been compromised in a data breach
Security Threats & Safeguard Solutions
DISC online store for recommended InfoSec products
Online Threat Analysis
Trend Micro Virus Scan | ESET Virus Scan | Norton Virus Scan | McAfee Virus Scan | Analyze suspicious files | Virus Removal Guides | Email Spoof Test | AbuseIPDB | AlienVault Open Threat Exchange | Shodan records historical open ports and services on the host | Google’s DNS over HTTPS service to do a PTR lookup on the IP | Malware traffic analysis | Open-source Threat Intelligence Feeds | Use a Free IP locator tool
The Mozilla Observatory has helped over 240,000 websites by teaching developers, system administrators, and security professionals how to configure their sites safely and securely.
Scan your Site
#SecureCode Journey starts with #CodeSec
Improve awareness with essential tools from Defendify
PhishTank provides information about phishing on the Internet

Shodan is the world’s first search engine for Internet-connected devices

LookingGlass Threat Map

Fortinet Threat Map
“Marc Elsberg’s brilliantly written techno-thriller vividly shows how terrorists, instead of using guns and bombs, can sit at a keyboard and use computer code to bring the world to its knees.” – Charles Belfoure, New York Times bestselling author of The Paris Architect and House of Thieves
![Blackout: A Novel by [Marc Elsberg]](https://m.media-amazon.com/images/I/519X8hXiF3L.jpg)




February 6th, 2023 10:57 am
[…] InfoSec Threats […]
February 6th, 2023 5:31 pm
[…] InfoSec Threats […]
February 8th, 2023 12:03 am
[…] InfoSec Threats […]
February 8th, 2023 11:08 am
[…] InfoSec Threats […]
February 8th, 2023 12:44 pm
[…] InfoSec Threats […]
February 9th, 2023 12:10 am
[…] InfoSec Threats […]
February 9th, 2023 10:35 am
[…] InfoSec Threats […]
February 10th, 2023 10:29 am
[…] InfoSec Threats […]
February 10th, 2023 12:50 pm
[…] InfoSec Threats […]
February 12th, 2023 2:31 pm
[…] InfoSec Threats […]
February 13th, 2023 10:44 am
[…] InfoSec Threats […]
February 14th, 2023 11:46 am
[…] InfoSec Threats […]
February 15th, 2023 9:28 am
[…] InfoSec Threats […]
February 16th, 2023 10:27 am
[…] InfoSec Threats […]
February 16th, 2023 10:56 am
[…] InfoSec Threats […]
February 17th, 2023 10:27 am
[…] InfoSec Threats […]
February 17th, 2023 11:49 am
[…] InfoSec Threats […]
February 17th, 2023 1:03 pm
[…] InfoSec Threats […]
February 20th, 2023 10:12 am
[…] InfoSec Threats […]
February 20th, 2023 12:07 pm
[…] InfoSec Threats […]
February 21st, 2023 10:37 am
[…] InfoSec Threats […]
February 22nd, 2023 9:54 am
[…] InfoSec Threats […]
February 23rd, 2023 2:10 pm
[…] InfoSec Threats […]
February 23rd, 2023 3:20 pm
[…] InfoSec Threats […]
February 24th, 2023 10:34 am
[…] InfoSec Threats […]
February 24th, 2023 2:35 pm
[…] InfoSec Threats […]
February 24th, 2023 3:29 pm
[…] InfoSec Threats […]
February 25th, 2023 4:15 pm
[…] InfoSec Threats […]
February 28th, 2023 1:10 pm
[…] InfoSec Threats […]
February 28th, 2023 2:26 pm
[…] InfoSec Threats […]
March 1st, 2023 11:25 am
[…] InfoSec Threats […]
March 1st, 2023 11:31 am
[…] InfoSec Threats […]
March 1st, 2023 1:29 pm
[…] InfoSec Threats […]
March 2nd, 2023 12:06 am
[…] InfoSec Threats […]
March 2nd, 2023 10:54 am
[…] InfoSec Threats […]
March 2nd, 2023 3:15 pm
[…] InfoSec Threats […]
March 3rd, 2023 11:50 am
[…] InfoSec Threats […]
March 3rd, 2023 4:22 pm
[…] InfoSec Threats […]
March 6th, 2023 10:20 am
[…] InfoSec Threats […]
March 6th, 2023 10:30 am
[…] InfoSec Threats […]
March 6th, 2023 12:27 pm
[…] InfoSec Threats […]
March 7th, 2023 3:38 pm
[…] InfoSec Threats […]
March 8th, 2023 9:26 am
[…] InfoSec Threats […]
March 9th, 2023 10:39 am
[…] InfoSec Threats […]
March 9th, 2023 11:15 am
[…] InfoSec Threats […]
March 10th, 2023 10:42 am
[…] InfoSec Threats […]
March 10th, 2023 12:24 pm
[…] InfoSec Threats […]
March 11th, 2023 12:10 pm
[…] InfoSec Threats […]
March 12th, 2023 12:13 am
[…] InfoSec Threats […]
March 12th, 2023 5:17 pm
[…] InfoSec Threats […]
March 13th, 2023 10:21 am
[…] InfoSec Threats […]
March 13th, 2023 12:36 pm
[…] InfoSec Threats […]
March 14th, 2023 7:57 am
[…] InfoSec Threats […]
March 19th, 2023 3:44 pm
[…] InfoSec Threats […]
March 20th, 2023 10:53 am
[…] InfoSec Threats […]
March 20th, 2023 12:05 pm
[…] InfoSec Threats […]
March 23rd, 2023 9:39 am
[…] InfoSec Threats […]
March 24th, 2023 7:08 am
[…] InfoSec Threats […]
March 24th, 2023 7:19 am
[…] InfoSec Threats […]
March 27th, 2023 12:57 pm
[…] InfoSec Threats […]
March 28th, 2023 8:25 am
[…] InfoSec Threats […]
March 28th, 2023 10:16 am
[…] InfoSec Threats […]
March 29th, 2023 8:01 am
[…] InfoSec Threats […]
March 30th, 2023 8:28 am
[…] InfoSec Threats […]
March 30th, 2023 12:44 pm
[…] InfoSec Threats […]
March 30th, 2023 3:14 pm
[…] InfoSec Threats […]
March 31st, 2023 10:09 am
[…] InfoSec Threats […]
April 3rd, 2023 3:18 pm
[…] InfoSec Threats […]
April 4th, 2023 9:17 am
[…] InfoSec Threats […]
April 5th, 2023 9:35 am
[…] InfoSec Threats […]
April 6th, 2023 12:45 pm
[…] InfoSec Threats […]
April 7th, 2023 11:21 am
[…] InfoSec Threats […]
April 8th, 2023 12:03 pm
[…] InfoSec Threats […]
April 9th, 2023 9:48 am
[…] InfoSec Threats […]
April 9th, 2023 11:09 am
[…] InfoSec Threats […]
April 10th, 2023 8:19 am
[…] InfoSec Threats […]
April 10th, 2023 8:38 am
[…] InfoSec Threats […]
April 11th, 2023 9:46 am
[…] InfoSec Threats […]
April 11th, 2023 3:15 pm
[…] InfoSec Threats […]
April 12th, 2023 8:58 am
[…] InfoSec Threats […]
April 13th, 2023 8:22 am
[…] InfoSec Threats […]
April 14th, 2023 7:32 am
[…] InfoSec Threats […]
April 16th, 2023 10:13 am
[…] InfoSec Threats […]
April 17th, 2023 8:50 am
[…] InfoSec Threats […]
April 17th, 2023 1:49 pm
[…] InfoSec Threats […]
April 18th, 2023 11:01 am
[…] InfoSec Threats […]
April 19th, 2023 11:29 am
[…] InfoSec Threats […]
April 19th, 2023 11:48 am
[…] InfoSec Threats […]
April 20th, 2023 7:56 am
[…] InfoSec Threats […]
April 24th, 2023 8:15 am
[…] InfoSec Threats […]
April 25th, 2023 9:39 am
[…] InfoSec Threats […]
April 28th, 2023 1:38 pm
[…] InfoSec Threats […]
April 28th, 2023 1:49 pm
[…] InfoSec Threats […]
April 30th, 2023 1:14 pm
[…] InfoSec Threats […]
May 3rd, 2023 11:10 pm
July 19th, 2023 9:03 am
[…] InfoSec Threats […]