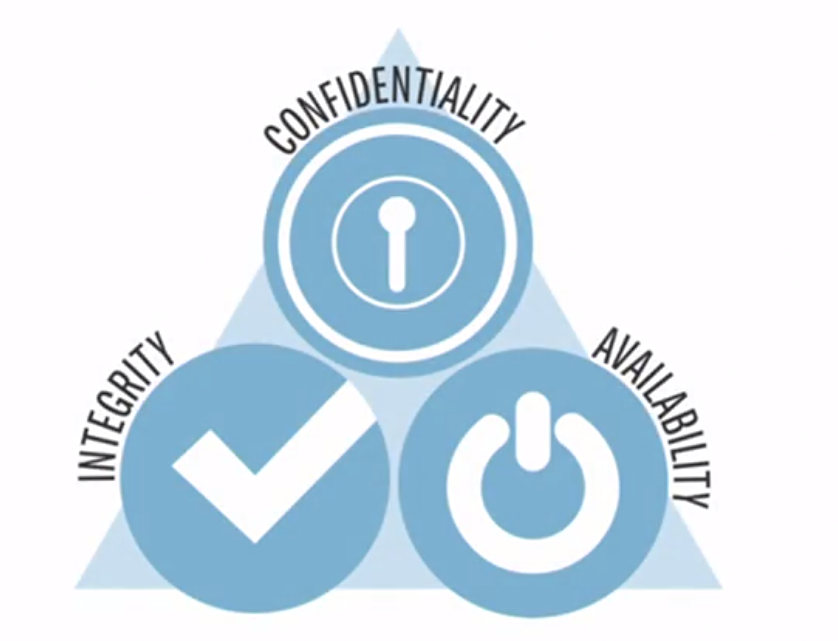
Best implementers of InfoSec program (ISMS) are those who possess both management and leadership capabilities…

CISO COMPASS: Navigating Cybersecurity Leadership Challenges with Insights from Pioneers
2020 Cybersecurity CANON Hall of Fame Winner
Todd Fitzgerald, co-author of the ground-breaking (ISC)2 CISO Leadership: Essential Principles for Success, Information Security Governance Simplified: From the Boardroom to the Keyboard, co-author for the E-C Council CISO Body of Knowledge, and contributor to many others including Official (ISC)2 Guide to the CISSP CBK, COBIT 5 for Information Security, and ISACA CSX Cybersecurity Fundamental Certification, is back with this new book incorporating practical experience in leading, building, and sustaining an information security/cybersecurity program.
CISO COMPASS includes personal, pragmatic perspectives and lessons learned of over 75 award-winning CISOs, security leaders, professional association leaders, and cybersecurity standard setters who have fought the tough battle. Todd has also, for the first time, adapted the McKinsey 7S framework (strategy, structure, systems, shared values, staff, skills and style) for organizational effectiveness to the practice of leading cybersecurity to structure the content to ensure comprehensive coverage by the CISO and security leaders to key issues impacting the delivery of the cybersecurity strategy and demonstrate to the Board of Directors due diligence. The insights will assist the security leader to create programs appreciated and supported by the organization, capable of industry/ peer award-winning recognition, enhance cybersecurity maturity, gain confidence by senior management, and avoid pitfalls.
The book is a comprehensive, soup-to-nuts book enabling security leaders to effectively protect information assets and build award-winning programs by covering topics such as developing cybersecurity strategy, emerging trends and technologies, cybersecurity organization structure and reporting models, leveraging current incidents, security control frameworks, risk management, laws and regulations, data protection and privacy, meaningful policies and procedures, multi-generational workforce team dynamics, soft skills, and communicating with the Board of Directors and executive management. The book is valuable to current and future security leaders as a valuable resource and an integral part of any college program for information/ cybersecurity.

Previous articles on the subject of Chief Information Security Officers (CISOs)
Previous articles on the subject of Virtual Chief Information Security Officers (vCISOs).
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory




































![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=1119f164-7e48-4ad2-b112-d80cd3808a1d)
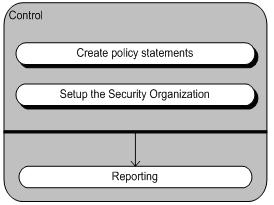
 The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level.
The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level. 


![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=2b18960c-caaa-4f56-a227-a5ede7b55594)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=2590b94c-4c68-4b01-a367-028d2bdde031)


