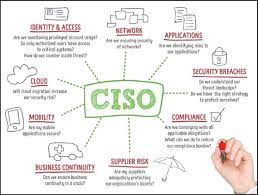
A virtual Chief Information Security Officer (vCISO) service or (CISOaaS) may be appropriate for a variety of scenarios, including:

Your clients, collaborators (partners) and some regulatory requirements anticipate the presence of an individual fulfilling the position of Chief Information Security Officer (CISO).
- Companies without an in-house CISO: Small and medium-sized companies may not have the budget or need for a full-time CISO. A vCISO service can provide these companies with access to a seasoned cybersecurity professional without having to hire a full-time employee.
- Companies experiencing rapid growth or change: Companies that are growing quickly or undergoing significant changes, such as mergers or acquisitions, may benefit from the expertise of a vCISO to help them navigate the cybersecurity implications of these changes.
- Companies with limited cybersecurity resources: Some companies may have an IT team but lack dedicated cybersecurity resources. A vCISO can help fill this gap by providing strategic guidance and oversight of the company’s cybersecurity program.
- Compliance requirements: Companies in regulated industries, such as healthcare or financial services, may require a CISO to meet regulatory requirements. A vCISO can help these companies meet compliance requirements with standards (ISO 27001) and regulations (PCI, HIPAA, NIST CSF, etc.) without having to hire a full-time CISO.
- Cybersecurity incident response: In the event of a cybersecurity incident, a vCISO can provide expertise and guidance to help the company respond effectively and minimize the impact of the incident.
Overall, a vCISO service can be a cost-effective way for companies to gain access to the expertise of a seasoned cybersecurity professional without having to hire a full-time employee.

Which organizations may need vCISO services:
- Small to Medium-Sized Enterprises (SMEs):
- These businesses may not have the resources to hire a full-time CISO but still require expert guidance to manage their cybersecurity needs.
- Industries: Technology startups, healthcare practices, legal firms, financial services, retail businesses, etc.
- Large Enterprises:
- Large companies with existing security teams may use vCISO services for additional expertise, specific projects, or temporary coverage to assist in house CISO.
- Industries: Finance, healthcare, manufacturing, utilities, telecommunications, etc.
- Non-Profit Organizations:
- These organizations often need to protect sensitive donor and beneficiary information but might lack the budget for a full-time CISO.
- Examples: Charitable organizations, educational institutions, and research entities.
- Government Agencies:
- Small to mid-sized government entities may utilize vCISO services to bolster their cybersecurity posture and comply with regulations.
- Examples: Local municipalities, state agencies, and public health departments.
- Regulated Industries:
- Companies in heavily regulated industries need to adhere to strict compliance standards and may require specialized cybersecurity expertise.
- Industries: Healthcare (HIPAA), finance (GLBA, SOX), and retail (PCI-DSS).
- Organizations Undergoing Digital Transformation:
- Businesses that are adopting new technologies, moving to the cloud, or modernizing their IT infrastructure may need vCISO services to manage the associated security risks.
- Examples: Companies implementing IoT, AI, or big data solutions.
- Businesses Experiencing Rapid Growth:
- Fast-growing companies may face evolving cybersecurity challenges and can benefit from the strategic oversight of a vCISO.
- Examples: Tech startups, e-commerce platforms, and fintech companies.
- Companies Preparing for Mergers and Acquisitions:
- Businesses involved in M&A activities need to ensure that cybersecurity due diligence is performed and that their security posture is strong to protect sensitive data.
- Examples: Investment firms, private equity groups, and merging corporations.
- Organizations Recovering from a Security Incident:
- Companies that have experienced a breach or other security incident may hire a vCISO to help with incident response, recovery, and the implementation of stronger security measures.
- Examples: Any business recovering from ransomware attacks, data breaches, or significant cybersecurity incidents to mitigate risk to an acceptable level and improves security posture
DISC InfoSec can offer tailored cybersecurity solutions that align with the specific needs and constraints of different types of organizations.

Organizations committed to prioritizing security encounter the difficulty of locating a Chief Information Security Officer (CISO) possessing the appropriate skills and knowledge. It becomes necessary for someone to take charge of the security and compliance strategy, but this requirement often surpasses the expertise possessed by operational IT/CIO.
What is CISOaaS?
Chief Information Security Officer-as-a-Service (CISOaaS) provides information security leadership from an appropriate pool of expertise. CISOaaS provides security guidance to senior management and drives the organization’s information security program.
Cert-In issues new guidelines for government bodies, mandates appointment of CISO, Read more at: https://lnkd.in/dKcdHMtP
The benefits of our CISOaaS
- Gain access to a diverse pool of highly experienced and specialized senior cyber security professionals.
- Rapidly access valuable resources and eliminate the necessity of retaining talent.
- Reduce your expenses by paying solely for the necessary support, effectively minimizing costs.
- Based on CISOaaS being engaged for four days a month annually at current prices.
- Based on your requirements, you can hire a vCISO 5-10 hours a week or per month.
- Mitigate your risk by strengthening your cyber and information strategy through the implementation of a clearly defined roadmap, thereby enhancing your overall security posture.
- Acquire valuable experience in effectively educating and presenting to board members, and non-technical senior staff across functional diverse backgrounds.
- Leverage our independent perspective and established credibility to secure comprehensive cross-business support and successfully accomplish your information security objectives.


Deura InfoSec Partners with Ostendio to Streamline Compliance & Security Offerings
- Strategic Partnership: Ostendio and Deura InfoSec have formed a partnership to enhance compliance and risk management services for Deura InfoSec clients using Ostendio’s GRC platform.
- Efficiency Gains: Deura InfoSec will leverage Ostendio’s platform to streamline compliance processes, significantly reducing the time clients spend on information security management by up to 50%.
- Client Benefits: The partnership allows Deura InfoSec to overcome the challenges of fragmented security and simplify the processes and costs of delivering complex cybersecurity programs.
CISO Conversations: The Role of the vCISO
6 ways the CISO role is evolving today
A CISO’s Guide to Avoiding Jail After a Breach
Cybersecurity: The CISO’s View
We’d love to hear from you! If you have any questions, comments, or feedback, don’t hesitate to get in touch. Our team is here to help, and we’re always looking to improve our services. You can reach us by email at info@deurainfosec.com or through our website. contact form.
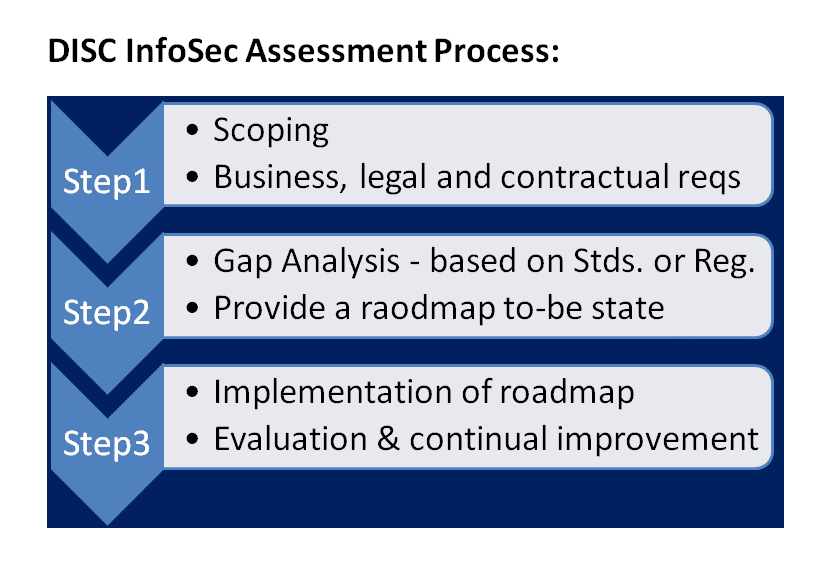
We offer discounted initial assessment based on various industry standards and regulations to demonstrate our value and identify possible areas for improvement. Potentially a roadmap for the to-be state.
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot