On the morning of August 4, 2022, Advanced, a supplier for the UK’s National Health Service (NHS), was hit by a major cyberattack. Key services including NHS 111 (the NHS’s 24/7 health helpline) and urgent treatment centers were taken offline, causing widespread disruption. This attack served as a brutal reminder of what can happen without a standardized set of controls in place. To protect themselves, organizations should look to ISO 27001.
ISO 27001 is an internationally recognized Information Security Management System standard. It was first published in 2005 to help businesses implement and maintain a solid information security framework for managing risks such as cyberattacks, data leaks and theft. As of October 25, 2022, it has been updated in several important ways.
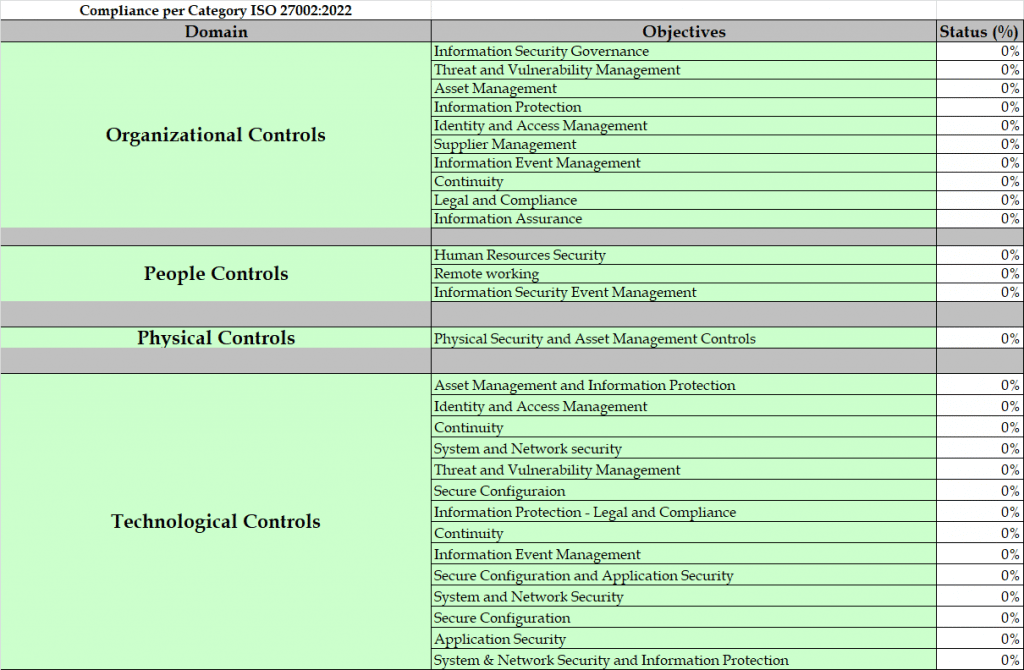
The standard is made up of a set of clauses (clauses 4 through 10) that define the management system, and Annex A which defines a set of controls. The clauses include risk management, scope and information security policy, while Annex A’s controls include patch management, antivirus and access control. It’s worth noting that not all of the controls are mandatory; businesses can choose to use those that suit them best.
Why is ISO 27001 being updated?
It’s been nine years since the standard was last updated, and in that time, the technology world has changed in profound ways. New technologies have grown to dominate the industry, and this has certainly left its mark on the cybersecurity landscape.
With these changes in mind, the standard has been reviewed and revised to reflect the state of cyber- and information security today. We have already seen ISO 27002 (the guidance on applying the Annex A controls) updated. The number of controls has been reduced from 114 to 93, a process that combined several previously existing controls and added 11 new ones.
Many of the new controls were geared to bring the standard in line with modern technology. There is now, for example, a new control for cloud technology. When the controls were first created in 2013, cloud was still emerging. Today, cloud technology is a dominant force across the tech sector. The new controls thus help bring the standard up to date.
In October, ISO 27001 was updated and brought in line with the new version of ISO 27002. Businesses can now achieve compliance with the updated 2022 controls, certifying themselves as meeting this new standard, rather than the now-outdated list from 2013.
How can ISO 27001 certification benefit your business?
Implementing ISO 27001 brings a host of information security advantages that benefit companies from the outset.
Companies that have invested time in achieving ISO 27001 certification will be recognized by their customers as organizations that take information security seriously. Companies that are focused on the needs of their customers should want to address the general feeling of insecurity in their users’ minds.
Moreover, as part of the increasingly rigorous due-diligence processes that many companies are now undertaking, ISO 27001 is becoming mandatory. Therefore, organizations will benefit from taking the initiative early to avoid missing out commercially.
In the case of cyber-defense, prevention is always better than cure. Attacks mean disruption, which almost always proves costly for an organization, in regard to both reputation and finances. Therefore, we might view ISO 27001 as a form of cyber-insurance, where the correct steps are taken preemptively to save organizations money in the long term.
There’s also the matter of education. Often, an organization’s weakest point, and thus the point most often targeted, is the user. Compromised user credentials can lead to data breaches and compromised services. If users were more aware of the nature of the threats they face, the likelihood of their credentials being compromised would decrease significantly. ISO 27001 offers clear and cogent steps to educate users on the risks they face.
Ultimately, whatever causes a business to choose implementation of ISO 27001, the key to getting the most out of it is ingraining its processes and procedures in their everyday activity.
Overcoming the challenge of ISO 27001 certification
A lot of companies have already implemented many controls from ISO 27001, including access control, backup procedures and training. It might seem at first glance that, as a result, they’ve already achieved a higher standard of cybersecurity across their organization. However, what they continue to lack is a comprehensive management system to actually manage the organization’s information security, ensuring that it is aligned with business objectives, tied into a continuous improvement cycle, and part of business-as-usual activities.
While the benefits of ISO 27001 may be obvious to many in the tech industry, overcoming obstacles to certification is far from straightforward. Here are some steps to take to tackle two of the biggest issues that drag on organizations seeking ISO 27001 certification:
- Resources — time, money, and manpower: Businesses will be asking themselves: How can we find the extra budget and dedicate the finite time of our employees to a project that could last six to nine months? The key here is to place trust in the industry experts within your business. They are the people who will be implementing the standard day-by-day, and they should be placed at the wheel.
- Lack of in-house knowledge: How can businesses that have no prior experience implementing the standard get it right? In this case, we advise bringing in third-party expertise. External specialists have done this all before: They have already made the mistakes and learned from them, meaning they can come into your organization directly focused on implementing what works. In the long run, getting it right from the outset is a more cost-effective strategy because it will achieve certification in a shorter time.
Next steps toward a successful future
While making this all a reality for your business can seem daunting, with the right plan in place, businesses can rapidly benefit from all that ISO 27001 certification has to offer.
It’s also important to recognize that this October was not the cutoff point for businesses to achieve certification for the new version of the standard. Businesses will have a few months before certification bodies will be ready to offer certification, and there will likely then be a two-year transition period after the new standard’s publication before ISO 27001:2013 is fully retired.
Ultimately, it’s vital to remember that while implementation comes with challenges, ISO 27001 compliance is invaluable for businesses that want to build their reputations as trusted and secure partners in today’s hyper-connected world.
Source: https://wordpress.com/read/blogs/126020344/posts/2830377
ISO 27001 Risk Assessment and Gap Assessment
ISO 27001 Compliance and Certification



















![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=8310531f-dd51-48b2-9dca-4a52b857f987)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=75ca6076-5285-4eaa-9251-01afd6576cbb)
![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=1119f164-7e48-4ad2-b112-d80cd3808a1d)


![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=eea54cc4-9d5a-43d1-af8a-db857566fd66)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=388a1882-ddc8-487a-bc63-9310f0c69ecc)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=6b35ca8c-42a0-4753-be84-5a6d5b4c5394)


