Information risk management is the process of identifying the ways an organisation can be affected by a disruptive incident and how it can limit the damage.
It encompasses any scenario in which the confidentiality, integrity and availability of data is compromised.
As such, it’s not just cyber attacks that you should be worried about. Information risk management also includes threats within your organisation – such as negligent or malicious employees – as well as residual risks.
For example, the framework can help you address misconfigured databases, software vulnerabilities and poor security practices at third parties.
In this blog, we take a closer look at the way information risk management works and how organisations can use its guidance to bolster their security defences.
Why is information risk management important?
In the face of ever-growing cyber threats, it can be difficult for an organisation to protect its information assets.
Last year, the World Economic Forum listed cyber crime alongside COVID-19, climate change and the debt crisis as the biggest threats facing society in the next decade. It’s clear, then, that organisations need a plan for identifying and addressing security risks.
With an information risk management system, organisations gain a better understanding of where their information assets are, how to protect them and how to respond when a breach occurs.
One way it does this is by forcing organisations to not only identify but also assess their risks. This ensures that organisations prioritise scenarios that are most likely to occur or that will cause the most damage, enabling them to make informed decisions in line with their security budget.
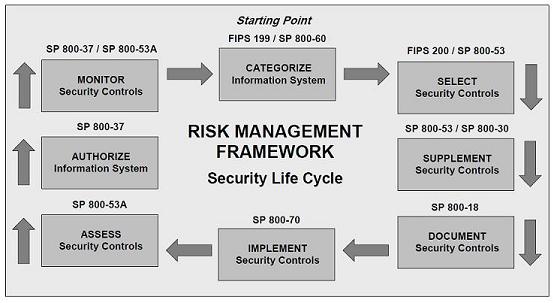
How risk management works
To understand how risk management programmes work, we need to take a closer look at what ‘risk’ actually is.
In an information security context, risk can be defined as the combination of a vulnerability and a threat.
As we’ve previous discussed, a vulnerability is a known flaw that can be exploited to compromise sensitive information.
These are often related to software flaws and the ways that criminal hackers can exploit them to perform tasks that they weren’t intended for.
They can also include physical vulnerabilities, such as inherent human weaknesses, such as our susceptibility to phishing scams or the likelihood that we’ll misplace a sensitive file.
This is different from a threat, which is defined as the actions that result in information being compromised.
So, to use the examples above, threats include a criminal hacker exploiting a software flaw or duping an employee with a bogus email.
When a threat meets a vulnerability, you get a risk. In the case of the criminal hacker phishing an employee, the risk is that the attacker will gain access to the employee’s work account and steal sensitive information. This can result in financial losses, loss of privacy, reputational damage and regulatory action.
A risk management system helps organisations identify the ways in which vulnerabilities, threats and risks intertwine. More importantly, it gives organisations the ability to determine which risks must be prioritised and identify which controls are best equipped to mitigate the risk.
Start protecting your business
At the heart of risk management is the risk assessment. This is the process where threats and vulnerabilities are identified. Organisations can use the result of the assessment to plan their next moves.

This process can be labour-intensive, but you can simplify the task with our risk assessment tool vsRisk.
With vsRisk, you’ll receive simple tools that are specifically designed to tackle each part of the risk assessment.
This software package is:
- Easy to use. The process is as simple as selecting some options and clicking a few buttons.
- Able to generate audit reports. Documents such as the Statement of Applicability and risk treatment plan can be exported, edited and shared across the business and with auditors.
- Geared for repeatability. The assessment process is delivered consistently year after year (or whenever circumstances change).
- Streamlined and accurate. Drastically reduces the chance of human error.
Risk Management Training





































![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=8310531f-dd51-48b2-9dca-4a52b857f987)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=75ca6076-5285-4eaa-9251-01afd6576cbb)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=388a1882-ddc8-487a-bc63-9310f0c69ecc)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=28dcae72-914e-4823-9632-cd34145194b7)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=f4c7607a-8a48-4ed1-bba2-9bb41450aa23)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=a4367ffd-91c3-481f-b56e-6c1bbc7cc7ea)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=6b35ca8c-42a0-4753-be84-5a6d5b4c5394)
 The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level.
The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level. 


![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=2b18960c-caaa-4f56-a227-a5ede7b55594)


