ISO Self assessment tools list includes but not limited to Privacy, ISO 27001, ISO 9001 and ISO 14001 & ISO/IEC 27701 2019 Standard and Toolkit
Jan 27 2021

ISO Self assessment tools list includes but not limited to Privacy, ISO 27001, ISO 9001 and ISO 14001 & ISO/IEC 27701 2019 Standard and Toolkit
Jan 13 2011
Three years ago, California state IT council adopted the information security program guide which help organizations to comply with SB 1386. The council advised the use of information security standard ISO 27002 framework to comply and meet the needs of SB 1386.
This legislation deals with the security of personal information and is applicable to all organisations (state and government agencies, non-profit, companies of all sizes, regardless of geographic location) holding personal data on any person living in California. SB-1386 requires such information holders to disclose any unauthorised access of computerised data files containing personal information.
In response, IT Governance’s comprehensive ‘SB-1386 & ISO27002 Implementation Toolkit’ is specifically designed by experts in data compliance legislation to guide organisations on how to conform to SB-1386. The toolkit conforms to ISO27002 and, if desired, also helps organisations prepare for any external certification process (ISO 27001) that would demonstrate conformance with such a standard. The State of California has itself formally adopted ISO/IEC 27002 as its standard for information security and recommended that organisations use this standard as guidance in their efforts to comply with California law.
Which businesses are affected by SB 1386 law?
o If you have a business in California
o Outsourcing company who does business with a company in California or have customers in California
o Data centers outside of California which store information of California residents
Toolkits are designed to help organizations who need to comply with a law like SB 1386. SB 1386 and ISO 27002 implementation toolkit assist ISO 27002 compliance. Also help organizations who are interested in certification to lay in the ground work for (ISO 27001) certification that would demonstrate the conformance with world class information security management systems.
The Comprehensive SB1386 Implementation toolkit comprises of:
1. The SB 1386 Documentation Toolkit: a download with nearly 400 of densely packed pages of fit-for-purpose policies and procedures ensuring full compliance with SB 1386.
2. International IT Governance: An Executive Guide to ISO 17799/ISO 27001 (Soft Cover) This is the US version of the long established world leading manual on designing and implementing an Information Security Management System (ISMS) in line with the best practice guidance of ISO27001/ISO17799.
3. vsRisk™- the Definitive ISO 27001: 2005-Compliant Information Security Risk Assessment Tool which in summary:
o automates and delivers an ISO/IEC 27001-compliant risk assessment
o Uniquely, can assess confidentiality, integrity & availability for each of business, legal and contractual aspects of information assets – as required by ISO 27001
o Comprehensive best-practice alignment
o Supports ISO 27001
o Supports ISO 27002 (ISO/IEC 17799)
o Conforms to ISO/IEC 27005
o Conforms to NIST SP 800-30
o The wizard-based approach simplifies and accelerates the risk assessment process;
o Integrated, regularly updated, BS7799-3 compliant threat and vulnerability databases.
4. Plus an electronic copy of the Information Security Standard ISO/IEC 27002: (formerly ISO 17799).
Buy The SB-1386 & ISO27002 Implementation Toolkit NOW!
ISO assessment is a great first step towards ISO 27002 compliance and toward the final goal of ISO 27001 certification.
vsRisk and security risk assessment
ISO 27002 Framework for Today’s Security Challenges
httpv://www.youtube.com/watch?v=yRFMfiLbNj8
Sep 10 2009
De-perimeterization is a double edge sword for industry which creates scalable options for operation and huge challenges for safeguarding the assets beyond the edge. One of the major advantages for de-perimeterization is that user can access corporate information over the internet; in this situation user can access corporate data from any where, it’s hard to draw the line where the edge begins and where it ends. All you basically need a functional laptop with internet connection. On the other hand, de- perimeterization poses a great challenge due to possibility of viruses, spywares and worms spreading in your internal protected infrastructure.
In de-perimeterized environment, security attributes shall follow the data, wherever the data may go or reside.
In security architecture where firewall was considered a very effective perimeter defense has been weakens by virtualization and cloud computing. In early days of firewall defense, organization only needed to open few necessary protocols and ports to do business. Internet accessible systems were located on the DMZ and the communication was initiated from the corporate to internet. Now there are whole slew of protocols and ports which needs to be open to communicate with application in the cloud. As corporate application move out of the organization network into the cloud, the effectiveness of firewall diminished.
Defense in depth is required for additional protection of data because as new threats emerge, the firewall cannot be used as an only layer of security. The key to the security of de-perimeterization is to push security at each layer of infrastructure including application and data. Data is protected at every layer to ensure the confidentiality, integrity and availability (CIA). Various techniques can be utilized for safeguarding data including data level authentication. The idea of data level authentication is that data is encrypted with specific privileges, when the data move, those privileges are moved with the data.
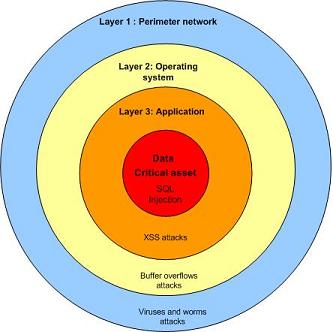
Endpoint security is relevant in today’s business environment especially for laptop and mobile devices. Agents on laptops and mobile devices utilized pull/push techniques to enforce relevant security policies. Different policies are applied depending on the location of the laptop. Where security policy will ensure which resources are available and what data need to be encrypted depending on the location of the device.
When corporate application and important data reside in the cloud, SLA should be written to protect the availability of the application and confidentiality of the data. Organizations should do their own business continuity planning so they are not totally dependent on the cloud service provider. For example backup your important data or utilize remote backup services where all data stored is encrypted.
Cloud Security and Privacy: An Enterprise Perspective on Risks and Compliance
Hosted email solution
Hosted email archiving
Hosted web monitoring
Hosted online backup
Aug 18 2009
![]()
Information Security Risk Analysis
In risk management, risk treatment process begins after completion of a comprehensive risk assessment.
Once risks have been assessed, risk manager utilize the following techniques to manage the risks
• Avoidance (eliminate)
• Reduction (mitigate)
• Transfer (outsource or insure)
• Retention (accept and budget)
Now the question is how to select an appropriate control to avoid or reduce risk. While selecting appropriate control to mitigate and avoid risk we need to consider compensating control to cut cost and supplemental control to increase protection for sensitive or classified assets.
Compensating control is a safeguard or countermeasure is employed by an organization in lieu of recommended security control from standards such as ISO 27002 or NIST 800-53. Compensating control provides an equivalent or comparable protection for information system to the original control requirement form standard. For example, even though most standards recommend separation of duties, but for a small operation it might be an unacceptable cost to separate the duties of system administration and system auditing. In that case system owner can utilize compensating control such as strengthening the audit and personnel security.
On the other hand with supplemental control, the system owner may decide to supplement the control to achieve more protection for sensitive and classified assets. If there is high likelihood or magnitude of impact is high should a threat exploit a given vulnerability you might want to consider a supplemental control because overall risk is high. For example you might want to utilize defense in depth method to safeguard your crown jewel.
Implementing and monitoring security control can be expensive, system owner are pressured by management to look for cost savings without any reduction in the security posture of an organization. The system owner can either inherit the common controls or segment the system exposure to reduce cost and risks.
Common controls are the security controls which have been implemented by another information system that your system can utilize. Basically working with another system owner who has utilized some of the security controls need to be implemented in your system. For example utilize the corporate office base line hardening configuration for Windows and Unix system instead of developing your own. This will significantly reduce the cost of developing, testing and maintaining a secure baseline configuration.
Best and cheapest method of cost reduction is to segment the information system into multiple systems which will add different layers and levels of security into each system. Basically you put your crown jewel in multiple layers of security if one control breaks there is another control in place to monitor and protect your assets. This will allow the system owner to focus implementing higher security controls to the segment with most sensitive or classified information instead of entire system
Feb 12 2009
In April 20007, California state IT council adopted the information security program guide which help organizations to comply with SB 1386. The council advised the use of information security standard ISO 27002 framework to comply and meet the needs of SB 1386.
[Table = 13]
Which businesses are affected by SB 1386 law?
o If you have a business in California
o Outsourcing company who does business with a company in California or have customers in California
o Data centers outside of California which store information of California residents
Toolkits are designed to help organizations who need to comply with a law like SB 1386. SB 1386 and ISO 27002 implementation toolkit assist ISO 27002 compliance. Also help organizations who are interested in certification to lay in the ground work for (ISO 27001) certification that would demonstrate the conformance with world class information security management systems.
The Comprehensive SB1386 Implementation toolkit comprises of:
1. The SB 1386 Documentation Toolkit: a download with nearly 400 of densely packed pages of fit-for-purpose policies and procedures ensuring full compliance with SB 1386.
2. International IT Governance: An Executive Guide to ISO 17799/ISO 27001 (Soft Cover) This is the US version of the long established world leading manual on designing and implementing an Information Security Management System (ISMS) in line with the best practice guidance of ISO27001/ISO17799.
3. vsRisk™- the Definitive ISO 27001: 2005-Compliant Information Security Risk Assessment Tool which in summary:
o automates and delivers an ISO/IEC 27001-compliant risk assessment
o Uniquely, can assess confidentiality, integrity & availability for each of business, legal and contractual aspects of information assets – as required by ISO 27001
o Comprehensive best-practice alignment
o Supports ISO 27001
o Supports ISO 27002 (ISO/IEC 17799)
o Conforms to ISO/IEC 27005
o Conforms to NIST SP 800-30
o The wizard-based approach simplifies and accelerates the risk assessment process;
o Integrated, regularly updated, BS7799-3 compliant threat and vulnerability databases.
4. Plus an electronic copy of the Information Security Standard ISO/IEC 27002: (formerly ISO 17799).
Buy The SB-1386 & ISO27002 Implementation Toolkit NOW!
ISO assessment is a great first step towards ISO 27002 compliance and toward the final goal of ISO 27001 certification audit or for that matter any compliance audit.
ISO 27002 Framework for Today’s Security Challenges
httpv://www.youtube.com/watch?v=yRFMfiLbNj8
Aug 08 2008
Security review is performed to identify and analyze risks and weaknesses in the current security posture of an organization. An ISO assessment is performed utilizing international standard ISO 27002 and company security policy, the purpose of the review is to evaluate the information security posture of an organization based on international standard. The level of compliance will indicate how close your organization is to meeting the key objectives for each 133 controls defined within 11 security control clauses collectively containing a total of 39 main security categories and one introductory clause introducing risk assessment and treatment.
It is important to not only assess the control for completeness (all relevant areas are addressed) and comprehensiveness (each individual area is covered completely), but also this balanced framework serves as the basis for both measuring an organization’s effectiveness in addressing risk and structuring an organization’s overall security program. Because ISO 27002 requirements are largely a superset of other major regulations, achieving ISO 27002 compliance positions most organizations to be well on their way to meeting the requirements of SOX, HIPAA and GLBA.
To achieve ISO compliance, thorough assessment utilizing all 133 controls will provide mitigating solution guidelines for gaps. To give your business an edge, conduct a security review based on ISO controls, if you would like to compare your security practices with international standard.
The result of the assessment will not only establish and maintain security policy, but also validates the policy’s completeness, design new controls and provide a road map to mitigate risks. An assessment of risks will determine what issues need to be addressed and provide a guideline to meet security regulations and a road map to build a world class ISMS (Information Security Management System).
ISO27001 is an international standard which is considered as an information security best practice or due diligence and is part of the security controls and audit controls specification document. ISO27002 is a code of practice which recommends guidelines for information security management systems and is closely linked to ISO 27001. ISO27001 continues to provide comprehensive best-practice advice and guidance to private and public organizations around the globe on how to design and implement a compliant information security management system ISMS.
An ISMS is not simply a set of documents. Maintaining and improving ISMS allows it to grow over time to address new business requirements. An ISMS is simply a system which addresses information security risks facing an organization and identifies the level of organization compliance with applicable regulations.