Practical Cloud Security: A Guide for Secure Design and Deployment

MicroMasters® Program in Cloud Computing

Nov 26 2021
Practical Cloud Security: A Guide for Secure Design and Deployment

MicroMasters® Program in Cloud Computing

Jun 25 2021
There are many factors to considered when selecting a public cloud provider, but 56% in a recent survey said security concerns had the most significant influence during the selection process for public cloud providers, IT services management company Ensono said.
Above: Ensono Cloud Clarity Report uncovered several areas that significantly influenced buying decisions.
Ensono: Security is a key factor when choosing a public cloud provider

Mar 09 2021
The sheer number of organizations moving to the cloud is staggering: we’re seeing 3-5 years-worth of business transformation happening in just months due to the pandemic. As cloud-enabled digital transformation continues to accelerate, there are a variety of concerns.
For example, the visibility of data. Organizations (and users) must assess what controls cloud services providers offer in order to understand the security risks and challenges. If data is stored unencrypted, that implies significant additional risk in a multi-tenant environment. Or what about the ability of security models to mimic dynamic behavior? Many anomaly detection and predictive “risk-scoring” algorithms look for abnormal user behavior to help identify security threats. With the sudden and dramatic shift to remote work last year, most models require significant adjustments and adaptation.
Normally, companies begin exploring the move to a cloud service provider with a detailed risk analysis assessment. This often involves examining assets, potential vulnerabilities, exploitation probabilities, anticipated breach-driven outcomes, and an in-depth evaluation of vendors’ capacity to effectively manage a hybrid solution (including authentication services, authorization, access controls, encryption capabilities, logging, incident response, reliability and uptime, etc.).
How to mitigate security risks as cloud services adoption spikes
May 12 2014
by Lewis Morgan @ITG
It has now been a week since Infosecurity Europe 2014. This year was my first at Infosec, and I found it to be one of the most interesting and diverse events I have ever been to.
During my short time on the IT Governance stand, I spoke to several people who were showing a keen interest in our wide range of books. It was a common opinion that our range of books is one of the broadest in the industry – something of which we are very proud.
ISO27001 / ISO27002 Pocket Guide
Governance of Enterprise IT based on COBIT®5
Penetration Testing – Protecting Networks and Systems

Jan 22 2010
What is Cloud Computing and does it provide more protection to your business?
Cloud Computing will bring many benefits to organisations, some of which include reducing operating costs, reducing power consumption and freeing you up to focus on your core business.
The concept of shifting computing to a shared service provider is not new. What may be new is that the cost of Cloud Computing is falling so dramatically that considering outsourcing to the Cloud is no longer rare, and it is now accessible enough that any individual or organisation can use it to their advantage.
Above the Clouds: Managing Risk in the World of Cloud Computing
For Cloud Computing to be a viable option, you need to be confident that your business information will be secure and that the service you offer to your customers will still be reliable. So if you want to adopt a Cloud Computing strategy, you need to make sure you carry out due diligence on the service provider before you entrust this firm with your vital data. However, the author challenges the assumption that Cloud Computing will offer less protection to your data than relying on an in-house server. Buy Now!>
Cloud Computing not only allows you to make economies of scale; it can also offer you the increased security that comes from sharing the resource. The author argues that moving over to Cloud Computing can actually help to defend your organisation from threats such as denial of service attacks, viruses and worms.
Cloud service providers will tell you that Cloud Computing is bound to be better, faster and cheaper. The reality is that before switching over to Cloud Computing, you need to think carefully about whether it will really work for your business. This book shows you what you need to do to ensure that with Cloud Computing you will continue to give the standard of service your customers require. It also offers you some valuable tips on how to choose your provider of Cloud services.
Published date: 9th February 2010.
Pre-order this book using Voucher Code: “cloud2010” to save 10%!

Sep 10 2009
De-perimeterization is a double edge sword for industry which creates scalable options for operation and huge challenges for safeguarding the assets beyond the edge. One of the major advantages for de-perimeterization is that user can access corporate information over the internet; in this situation user can access corporate data from any where, it’s hard to draw the line where the edge begins and where it ends. All you basically need a functional laptop with internet connection. On the other hand, de- perimeterization poses a great challenge due to possibility of viruses, spywares and worms spreading in your internal protected infrastructure.
In de-perimeterized environment, security attributes shall follow the data, wherever the data may go or reside.
In security architecture where firewall was considered a very effective perimeter defense has been weakens by virtualization and cloud computing. In early days of firewall defense, organization only needed to open few necessary protocols and ports to do business. Internet accessible systems were located on the DMZ and the communication was initiated from the corporate to internet. Now there are whole slew of protocols and ports which needs to be open to communicate with application in the cloud. As corporate application move out of the organization network into the cloud, the effectiveness of firewall diminished.
Defense in depth is required for additional protection of data because as new threats emerge, the firewall cannot be used as an only layer of security. The key to the security of de-perimeterization is to push security at each layer of infrastructure including application and data. Data is protected at every layer to ensure the confidentiality, integrity and availability (CIA). Various techniques can be utilized for safeguarding data including data level authentication. The idea of data level authentication is that data is encrypted with specific privileges, when the data move, those privileges are moved with the data.
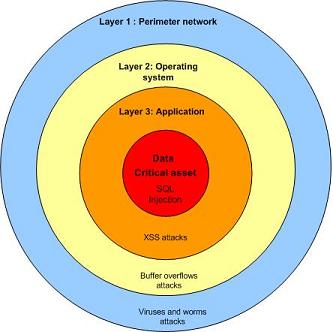
Endpoint security is relevant in today’s business environment especially for laptop and mobile devices. Agents on laptops and mobile devices utilized pull/push techniques to enforce relevant security policies. Different policies are applied depending on the location of the laptop. Where security policy will ensure which resources are available and what data need to be encrypted depending on the location of the device.
When corporate application and important data reside in the cloud, SLA should be written to protect the availability of the application and confidentiality of the data. Organizations should do their own business continuity planning so they are not totally dependent on the cloud service provider. For example backup your important data or utilize remote backup services where all data stored is encrypted.
Cloud Security and Privacy: An Enterprise Perspective on Risks and Compliance
Hosted email solution
Hosted email archiving
Hosted web monitoring
Hosted online backup
Jul 07 2009
Cloud Application Architectures: Building Applications and Infrastructure in the Cloud
 Cloud computing is the future of the computing, which happens to provide common business applications online that run from web browser and is comprised of virtual servers located over the internet. Basic idea behind cloud computing is the accessibility of application and data from any location as long as you are connected to the internet. Cloud computing makes the laptop the most essential tool to get the job done.
Cloud computing is the future of the computing, which happens to provide common business applications online that run from web browser and is comprised of virtual servers located over the internet. Basic idea behind cloud computing is the accessibility of application and data from any location as long as you are connected to the internet. Cloud computing makes the laptop the most essential tool to get the job done.
For example Hosted Email (SaaS) Security provides safeguards at the Internet level, eliminating spam and malware before they reach your internal network infrastructure. The hosted email provides centralized security with built-in redundancy, failover, and business continuity, while easing network and security administration. In the hosted email software as a service the security controls are at work at the internet level. It’s about time to expand the corporate perimeter beyond firewall and one of the major benefit of cloud computing is to give organizations capability to implement security controls at internet level and eliminate threats before they reach the internal network.
An online backup service is another example of software as a service (SaaS) which provides users with an online system for backing up and storing computer files.
Cloud computing incorporates several different types of computing, including:
software as a service (SaaS)
platform as a service (PaaS)
infrastructure as a service (IaaS)
It is a range of technologies that have come together to deliver scalable, tailored and virtualized IT resources and applications over the Internet.
Cloud Computing have several benefits and potential risks which you may want to know before signing a contract with a cloud vendor.