ISO Self assessment tools list includes but not limited to Privacy, ISO 27001, ISO 9001 and ISO 14001 & ISO/IEC 27701 2019 Standard and Toolkit
Jan 27 2021

ISO Self assessment tools list includes but not limited to Privacy, ISO 27001, ISO 9001 and ISO 14001 & ISO/IEC 27701 2019 Standard and Toolkit
Nov 03 2020
Brave Browser, the privacy-focused web browser, announced today that it grew in usage by over 130% in its first year of the release of its ‘Stable’ version.
Source: Privacy-focused Brave browser grew over 130% in the past year
Brave Browser Review 2020: Should you make the switch?
httpv://www.youtube.com/watch?v=cQuTwpUFIXU&ab_channel=dottotech
Why you should download Brave Browser NOW!
Apr 11 2019
Public Wi-Fi is rife with security risks, and cybersecurity professionals aren’t taking any chances, according to a Lastline report.
Source: Half of security pros would rather walk barefoot in a public restroom than use public Wi-Fi

Nov 15 2016
The Electronic Frontier Foundation aims to protect Web traffic by encrypting the entire Internet using HTTPS. Chrome now puts a little warning marker in the Address Bar next to any non-secure HTTP address. Encryption is important, and not only for Web surfing. If you encrypt all of the sensitive documents on your desktop or laptop, a hacker or laptop thief won’t be able to steal your identity, or takeover your bank account, or perhaps steal your credit card information. To help you select an encryption product that’s right for your situation, we’ve rounded up a collection of current products.
Folder Lock can lock access to files for quick, easy protection, and also keep them in encrypted lockers for serious protection. It combines a wide range of features with a bright, easy-to-use interface. Read the full review ››
Cypherix PC creates encrypted volumes for storing your sensitive files. Lock the volume and nobody can access the files. It does the job, though it lacks secure deletion. Read the full review ››
Cypherix SecureIT handles the basic task of encrypting and decrypting files and folders in a workmanlike fashion, but it lacks advanced features offered by the competition. Read the full review ››
Jul 21 2010
By David Scott
It’s rather interesting to monitor what’s happening in the UK right now. Data protection legislation is moving forward. And… business there supports data protection legislation.
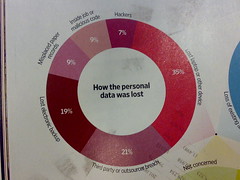
A survey of 1200 businesses indicates that those businesses are concerned about the strength of laws: Nearly 50% feel that laws are weak and require revision, and 87% believe that organizations should be required to divulge breaches of sensitive content where information about the public is involved. [Source: Sophos].
Here in the U.S., I rather doubt business is keen on more legislative oversight. Generally speaking, I’m wary of new legislation – new laws must be thoroughly reviewed so as to guard against unintended – and negative – consequences, particularly where business is concerned. In today’s economy, we don’t want to impinge businesses’ opportunities for hearty conduct and growth.
However, I do like the breach notification idea. It serves a couple purposes that come readily to mind:
– Stakeholders (the public, customers, allied agencies…) are entitled to know about breaches that affect them, or ones that just have the potential to affect the general well-being of the business.
– Also, healthy exposure and just that potential help to motivate businesses in the currency of their ongoing security measures.
Particularly for small/medium business, and smaller government agencies such as those at county/municipality level: Do you have in-house security professionals who cast the horizon for new threats, with attendant posture of proactivity? And, do you have strong security partners in the form of advisors, vendors and allied security products?
How do readers of the Exchange feel about it? Would you welcome new legislation? Are you confident regarding data security in your organization?

Apr 02 2009
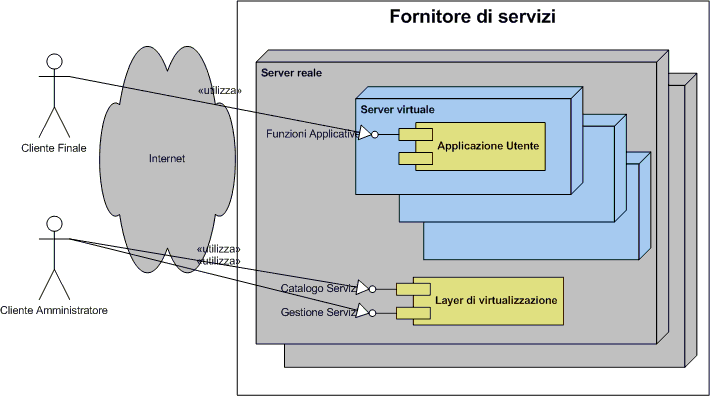
https://commons.wikimedia.org/wiki/File:Cloud_comp_architettura.png
Cloud computing provide common business applications online that run from web browser and is comprised of virtual servers located over the internet. Main concern for security and privacy of user is who has access to their data at various cloud computing locations and what will happen if their data is exposed to an unauthorized user. Perhaps the bigger question is; can end user trust the service provider with their confidential and private data.
“Customers must demand transparency, avoiding vendors that refuse to provide detailed information on security programs. Ask questions related to the qualifications of policy makers, architects, coders and operators; risk-control processes and technical mechanisms; and the level of testing that’s been done to verify that service and control processes are functioning as intended, and that vendors can identify unanticipated vulnerabilities.”
Three categories of cloud computing technologies:
Cloud computing is offering lots of new services which increase the exposure and add new risk factors. Of course it depends on applications vulnerabilities which end up exposing data and cloud computing service provider transparent policies spelling out responsibilities which will increase end user trust. Cloud computing will eventually be used by criminals to gain their objectives. The transparent policies will help to sort out legal compliance issues and to decide if the responsibility of security breach lies on end user or service provider shoulders.
Complexities of cloud computing will introduce new risks and complexity is the enemy of security. The organizations and end users should be mindful of this security principle before introducing this new variable into their risk equation. As a consumer you need to watch out and research your potential risks before buying this service and consider getting a comprehensive security assessment from a neutral third party before committing to a cloud vendor.
Possible risks involved in cloud computing
Complete data segregation
Complete mediation
Separation of duties
Regulatory compliance (SOX, HIPAA, NIST, PCI)
User Access
Physical Location of data
Availability of data
Recovery of data
Investigative & forensic support
Viability and longevity of the provider
Economy of mechanism
Related articles by ZemantaCloud Computing Security Framework May Nudge The Enterprises Towards Clouds (cloudave.com)Security in the clouds - or clouds in security? (theregister.co.uk)Your privacy: cloud computing report & tips; privacy notices & ICO consultation (consumingexperience.com)Are your bumper stickers revealing too much about your family?
Continue reading “Cloud computing and security”