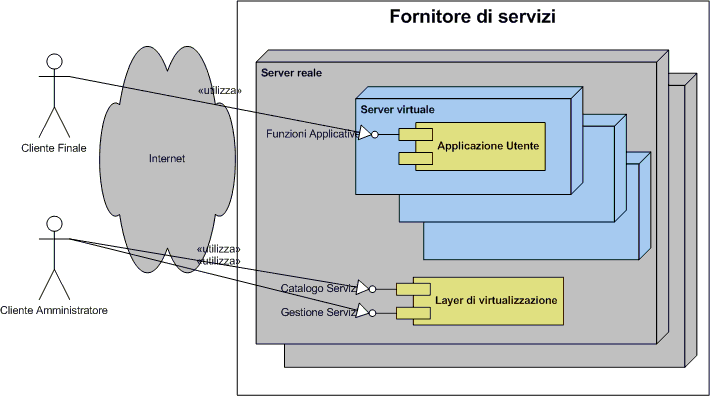
https://commons.wikimedia.org/wiki/File:Cloud_comp_architettura.png
Cloud computing provide common business applications online that run from web browser and is comprised of virtual servers located over the internet. Main concern for security and privacy of user is who has access to their data at various cloud computing locations and what will happen if their data is exposed to an unauthorized user. Perhaps the bigger question is; can end user trust the service provider with their confidential and private data.
“Customers must demand transparency, avoiding vendors that refuse to provide detailed information on security programs. Ask questions related to the qualifications of policy makers, architects, coders and operators; risk-control processes and technical mechanisms; and the level of testing that’s been done to verify that service and control processes are functioning as intended, and that vendors can identify unanticipated vulnerabilities.”
Three categories of cloud computing technologies:
- Infrastructure as a Service (IaaS)
- Platform as a Service (PaaS)
- Software as a Service (SaaS)
Cloud computing is offering lots of new services which increase the exposure and add new risk factors. Of course it depends on applications vulnerabilities which end up exposing data and cloud computing service provider transparent policies spelling out responsibilities which will increase end user trust. Cloud computing will eventually be used by criminals to gain their objectives. The transparent policies will help to sort out legal compliance issues and to decide if the responsibility of security breach lies on end user or service provider shoulders.
Complexities of cloud computing will introduce new risks and complexity is the enemy of security. The organizations and end users should be mindful of this security principle before introducing this new variable into their risk equation. As a consumer you need to watch out and research your potential risks before buying this service and consider getting a comprehensive security assessment from a neutral third party before committing to a cloud vendor.
Possible risks involved in cloud computing
Complete data segregation
Complete mediation
Separation of duties
Regulatory compliance (SOX, HIPAA, NIST, PCI)
User Access
Physical Location of data
Availability of data
Recovery of data
Investigative & forensic support
Viability and longevity of the provider
Economy of mechanism
Related articles by Zemanta
Cloud Computing Security Framework May Nudge The Enterprises Towards Clouds (cloudave.com)Security in the clouds - or clouds in security? (theregister.co.uk)Your privacy: cloud computing report & tips; privacy notices & ICO consultation (consumingexperience.com)-
Are your bumper stickers revealing too much about your family?
Continue reading “Cloud computing and security”



