
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot
Apr 08 2024
Jun 13 2021
If there is any moral to this, it’s one that all of my blog readers should already know: trust is essential to security. And the number of people you need to trust is larger than you might originally think. For an app to be secure, you need to trust the hardware, the operating system, the software, the update mechanism, the login mechanism, and on and on and on. If one of those is untrustworthy, the whole system is insecure.
It’s the same reason blockchain-based currencies are so insecure, even if the cryptography is sound.

Jun 11 2020
Encryption is a critical component of a defense-in-depth strategy, which is a security approach with a series of defensive mechanisms designed so that if one security mechanism fails, there’s at least one more still operating. As more organizations look to operate faster and at scale, they need ways to meet critical compliance requirements and improve […]
Source: The importance of encryption and how AWS can help | Amazon Web Services
Why is Encryption Important? – Why is Cybersecurity Important Episode 1
httpv://www.youtube.com/watch?v=EZSjs8A7lmA
Download a Security Risk Assessment steps paper!
Subscribe to DISC InfoSec blog by Email
Nov 15 2016
The Electronic Frontier Foundation aims to protect Web traffic by encrypting the entire Internet using HTTPS. Chrome now puts a little warning marker in the Address Bar next to any non-secure HTTP address. Encryption is important, and not only for Web surfing. If you encrypt all of the sensitive documents on your desktop or laptop, a hacker or laptop thief won’t be able to steal your identity, or takeover your bank account, or perhaps steal your credit card information. To help you select an encryption product that’s right for your situation, we’ve rounded up a collection of current products.
Folder Lock can lock access to files for quick, easy protection, and also keep them in encrypted lockers for serious protection. It combines a wide range of features with a bright, easy-to-use interface. Read the full review ››
Cypherix PC creates encrypted volumes for storing your sensitive files. Lock the volume and nobody can access the files. It does the job, though it lacks secure deletion. Read the full review ››
Cypherix SecureIT handles the basic task of encrypting and decrypting files and folders in a workmanlike fashion, but it lacks advanced features offered by the competition. Read the full review ››
Jul 02 2009
Primary Account Number (PAN) is a
“12-digit or 19-digit numeric code embossed on the face side of a bank card, and also encoded in the Magnetic Stripe. The primary account number is a composite number containing: the Major Industry Identifier of the card issuer; an individual account identifier, which includes part of the account number; and a Check Digit or code that verifies the authenticity of the embossed account number.”
There are three pieces of information that are included in a financial transaction. Which are PAN, primary identification number (PIN) and card’ expiration date. The PAN is 12 to 19 digit number embossed on the front of the card.
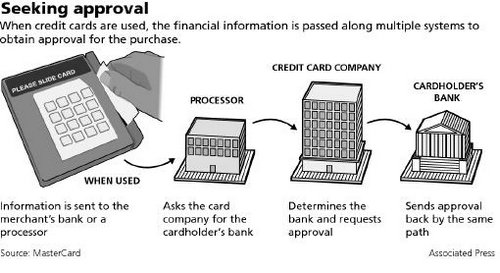
For a successful transaction PIN, PAN and card expiration date are transmitted along with other information from the merchant, the merchant will transmit the information to merchant bank, the merchant bank will transmit the information to service provider (processor), the processor will transmit to the card issuer entity to authorize the transaction.
Credit card authorization process:
1) Creditholder swipes card at merchant. A request is sent to merchants bank
2) Merchants bank “asks” processor to determine the cardholder bank
3) Processing network finds cardholders bank and request approval for purchase
4) Cardholders bank approves purchase and generates a approval code
5) Processor sends an approval code merchants bank
6) Merchants bank sends approval code to merchant
7) Purchase is complete and cardholder receives a receipt
“Every time you swipe your credit card and wait for the transaction to be approved, sensitive data including your name and account number are ferried from store to bank through computer networks, each step a potential opening for hackers.”
The PIN is protected from malicious activity by encryption from POS terminal to all the way to the cardholder bank; However PAN is currently transmitted unencrypted. Valid PAN in wrong hands increase the possibility of credit card fraud. So the industry has decided that PAN must be protected. Below are the requirements for PAN protection.
Requirements for PAN protection
1. The PAN protection mechanism must support multiple source methods, including manual entry, magnetic swipe, chip, and NFC.
2. The PAN protection mechanism is encryption using an X9 or ISO approved algorithm.
3. Financial transaction message format and protocol standards must be modified to handle encrypted PAN data.
4. Transaction processing systems must be able to access some of the PAN digits.
5. For different transactions, encryption of the same PAN with a given encryption key should not predictably produce the same encrypted value.
6. For transaction routing by an intermediary between a sender and a receiver, the PAN must be translated from the sender’s encryption key to the receiver’s encryption key.
7. PAN translation must reveal some of the PAN digits for the intermediary to process the transaction.
8. PAN encryption keys must be changed periodically using X9 or ISO approved key management methods.
9. PAN encryption keys must only be used for their intended purpose.
10. Different encryption keys must be used for protection of PAN storage and transmission.
11. PAN encryption keys and the associated key encryption key (KEK) must be protected using X9 or ISO approved tamper resistant security modules (TRSM).
12. The customer must be advised in writing of the importance of the PAN with guidelines on the proper use of the card and the PAN.
PAN encryption is a major step forward toward protecting the card holder data.
Fake a Credit Card
httpv://www.youtube.com/watch?v=V3pElQD8UZg
Oct 29 2008
Best practice emphasize the fact to backup the data if you can’t live without it, in the same way a traveler must avoid taking sensitive data on the road unless it’s absolutely necessary to do so. If you do plan to take sensitive data with you on the laptop, the necessary security controls must be implemented and go with the sensitive data. The data protection controls should be based on your information security policy data classification.
The laptop hardware itself is only worth few hundred dollars these days, but on the other hand it’s hard to put a price tag on the exposed data which may have a drastic impact on your organization, especially these days when most of the organizations are at the edge due to financial chaos.
Frequent travelers know it’s possible to lose a laptop or lose data because laptop may become inoperable due to hardware malfunction. Planning an important business trip should include encrypting sensitive data and backup on a remote website (Carbonite). So in case you lose your laptop or it’s is inoperable for some reason, you can remotely recover backed up files from site within reasonable time.
[TABLE=8]
Here is how you can encrypt your data on Windows laptop with built-in utility EFS
1. Create a new folder, and name the folder Private.
2. Right click the new folder and choose properties
3. Click advanced button
4. Check encrypt contents to secure data box and then click OK, Apply and OK again.
You have created a secure area where you can put your sensitive documents. Any file or subfolder you add to this folder (Private) will be encrypted automatically. Basically any type of file except Windows system file will be encrypted in this folder. Now if the attacker steal your laptop and remove your hard drive and mount on a system where the attacker has administrative privileges, the attacker will not be able to access the contents of the folder Private. On the other hand 256-bit AES encryption key is stored in encrypted form as a file attribute called the data decryption field (DDF). The EFS private key, needed to decrypt the DDF and extract the file encryption key, is also stored in encrypted form in the registry. The master key, which is used to obtain the key needed to access the EFS private key, is encrypted by the systems key and also stored locally. So the attacker will be able to decrypt the EFS protected files if he can somehow get possession of the system key.
Luckily we do have a choice whether to store the system key locally on your laptop. If you click start, then Run and then launch syskey.exe utility, you can choose how and where the system key will be stored. The dialogue box will present three options.
1. Store the startup key locally
2. Store the startup key on the floppy disk
3. Generate the startup key from a password
With the two non default options, you will be requiring to either insert the floppy or enter the password whenever the laptop is BOOTED. The floppy option is highly inconvenient for laptop users but the password options seem sufficient to protect the laptop data. On the laptop which doesn’t have a floppy drive, don’t try to click the floppy option because when you boot next time the laptop will be looking for the system key on a floppy before booting.
Survey: CISOs worried about mobile data security
**The real Hustle – Laptop Theft Scam
httpv://www.youtube.com/watch?v=Gb3ZiTJkCaA
Oct 17 2008
Mobile spyware is malicious software which is used to spy and control mobile devices (BlackBerry, PDAs, Windows Mobile and Cell Phones). Mobile spyware will not only intercept the message between two devices but also determine the location of the device. Basically, mobile spyware software is installed on a mobile device to spy on them.
Small businesses are usually not equipped to handle these threats. Just like laptops and desktops – mobile devices need security controls like antivirus, personal firewall, encryption and VPN to provide needed level of protection. Small businesses need to be aware of the security threats, like they might think that they are installing a game, which might very well be a key logger (logs your key strokes) or trojan software.
[TABLE=6]
Hackers on the move, WSJ August 11, 2008 by Roger Cheng – where he writes about more companies are letting employees use their personal smart phone at work and the security experts warns about the present threats in the industry. http://online.wsj.com/article/SB121803418845416977.html
Tips to safeguard your smartphone
httpv://www.youtube.com/watch?v=S64J4BCCoi4
(Free Two-Day Shipping from Amazon Prime). Great books
Sep 18 2008
As we know, it is possible to spoof an email sender’s name, so now the question of how to authenticate the sender has become even more important, since email has been used to send sensitive information.
In the recent case of Gov. Sarah Palin’s email, her email account got hacked and the hacker posted the screen shot of her email to WikiLeaks. Freedom of information laws require messages from government email accounts to be placed into the public record, so some public officials try to use Yahoo/Gmail to keep the information out of public scrutiny.
First of all public figures should avoid using public email addresses and even if you do don’t make it so obvious by naming it eponymously as did Gov.Palin. This information is owned by the commercial email sites and system administrators can see the email in the mailbox and can capture the text in transit. In commercial sites you will draw a great amount of attention, If you happen to be a high profile figure.
Second, perhaps we should not use commercial channels for private or sensitive information. If it’s necessary to use email as for sensitive information, make sure your email is encrypted in accordance with the Advanced Encryption Standard.
Third, two factor authentication for sensitive email is industry standard now, which requires the user to possess something (Token) and something only the user knows (Password or PIN). Two factor authentications provide identity theft protection.
Finally, strong authentication is a solution to secure identities and use of the Advanced Encryption Standard minimizes the exposure of email content.
(Free Two-Day Shipping from Amazon Prime).