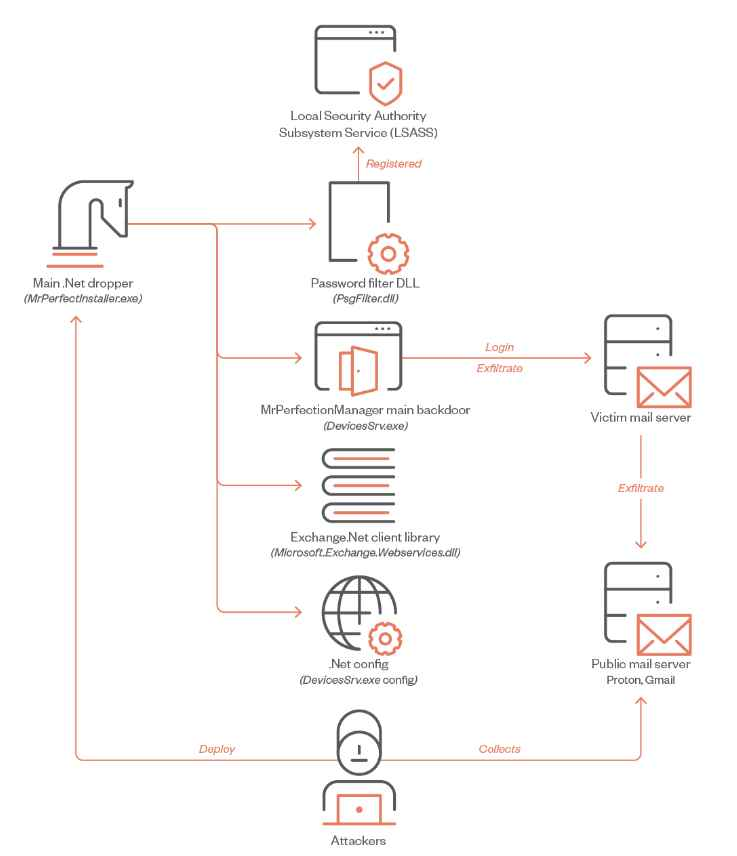
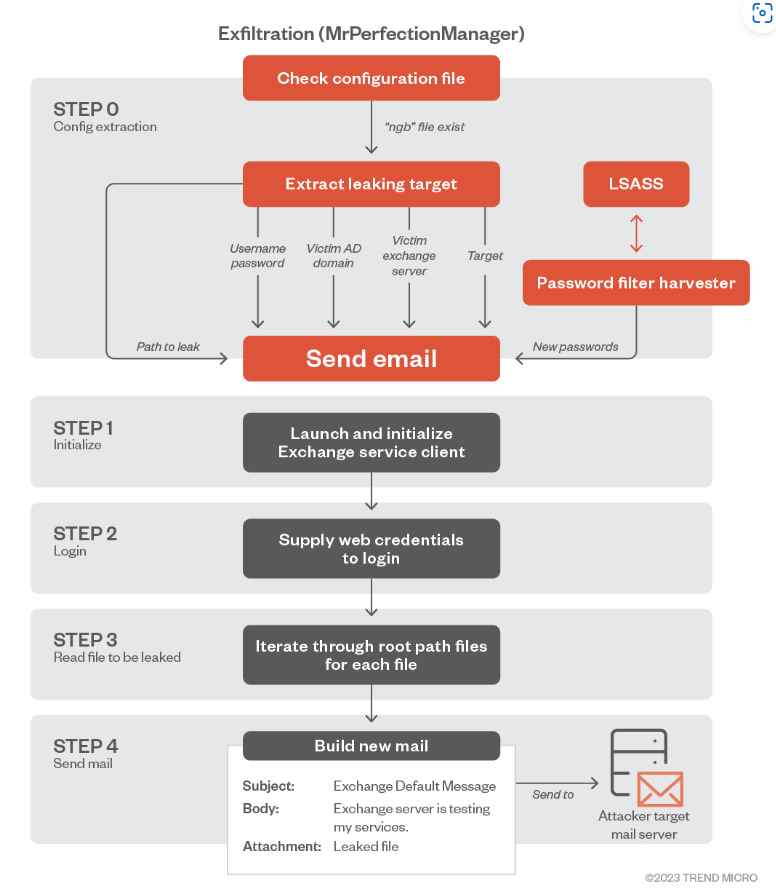
Chinese state-sponsored hackers have been found exploiting Juniper networking devices, planting backdoors to gain persistent and stealthy access to targeted networks. Security researchers discovered that these attackers are leveraging zero-day vulnerabilities in Juniper routers to infiltrate organizations discreetly.
Once inside, the attackers deploy custom malware and backdoors, allowing them to maintain access even after security patches are applied. These tactics enable long-term espionage, data theft, and the ability to launch further attacks while avoiding detection.
The attack specifically targets government agencies, critical infrastructure, and enterprises, indicating a focus on intelligence gathering and cyber-espionage. By compromising network routers, the hackers can monitor and manipulate traffic without triggering security alerts.
Juniper has released security updates addressing these vulnerabilities, urging organizations to apply patches immediately and strengthen their network defenses. Companies are also advised to implement intrusion detection systems and conduct regular security audits to identify potential compromises.
This incident highlights the growing risks associated with router and network infrastructure attacks. As state-sponsored cyber threats evolve, organizations must prioritize proactive cybersecurity measures to safeguard their critical systems from persistent adversaries.

The compromise of Juniper routers by Chinese state-sponsored hackers has serious implications for cybersecurity, affecting national security, corporate operations, and individual privacy. These backdoor implants allow attackers to maintain persistent, stealthy access to networks, enabling espionage, data manipulation, and potential sabotage. Here are the key consequences of this attack:
1. National Security Risks
Since these attacks target government agencies and critical infrastructure, they pose a direct threat to national security. Foreign adversaries gaining access to sensitive communications and classified data can disrupt operations, manipulate intelligence, or even prepare for future cyber warfare.
2. Corporate Espionage and Financial Losses
Enterprises relying on Juniper routers risk intellectual property theft, financial fraud, and operational disruptions. Cybercriminals or state actors could steal trade secrets, research data, and confidential customer information, leading to financial losses and competitive disadvantages.
3. Network Manipulation and Supply Chain Attacks
By compromising core network infrastructure, attackers can intercept, alter, or reroute data traffic. This not only affects the integrity of communications but also opens the door for further exploitation, such as supply chain attacks, where hackers use compromised routers to infiltrate connected systems.
4. Persistent Threats and Long-Term Espionage
Even if organizations apply security patches, backdoors may remain undetected, allowing attackers to maintain long-term surveillance. This makes incident response and remediation challenging, as security teams may struggle to detect and remove all traces of the intrusion.
5. Erosion of Trust in Network Security
The breach highlights the vulnerabilities in networking hardware and raises concerns about the trustworthiness of network infrastructure providers. Organizations may need to rethink their vendor security policies, implement stricter monitoring, and diversify their network equipment suppliers to reduce reliance on potentially compromised hardware.
Mitigation Measures
To minimize risks, organizations should immediately apply Juniper’s security patches, conduct forensic investigations, and monitor network traffic for anomalies. Strengthening intrusion detection systems (IDS), implementing zero-trust security models, and segmenting networks can also help reduce the impact of such cyber threats.
This incident underscores the growing dangers of router and network infrastructure attacks, emphasizing the need for proactive cybersecurity measures to protect against state-sponsored cyber threats and advanced persistent threats (APTs).
Cyber Dragon: Inside China’s Information Warfare and Cyber Operations (The Changing Face of War)
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | Security Risk Assessment Services