In an unsettling development that emerged late last week, the open-source community was thrust into a state of high alert following the disclosure that XZ Utils, a fundamental compression utility widespread across Linux distributions, had been compromised. This startling revelation has left a significant mark on the open-source ecosystem, prompting a swift and coordinated response from maintainers and security professionals alike.
Discovery of the Backdoor
The initial discovery of the backdoor was made by Andres Freund, a Microsoft software engineer, during routine diagnostics on Debian sid (development) installations. Freund’s investigation, sparked by unusually high CPU usage during SSH logins and accompanying error alerts, led to the identification of the culprit: a malicious insertion within the liblzma library, a core component of the XZ package. This finding was subsequently designated with the vulnerability identifier CVE-2024-3094. Attribution for this calculated insertion has been directed at an individual known as “Jia Tan” (JiaT75 on GitHub), who, through an elaborate scheme of social engineering and the use of sock puppet accounts, gained the trust of the XZ Utils maintainer community. This long-term infiltration underscores the advanced nature of the threat actor involved, pointing towards a highly skilled and resourceful adversary.
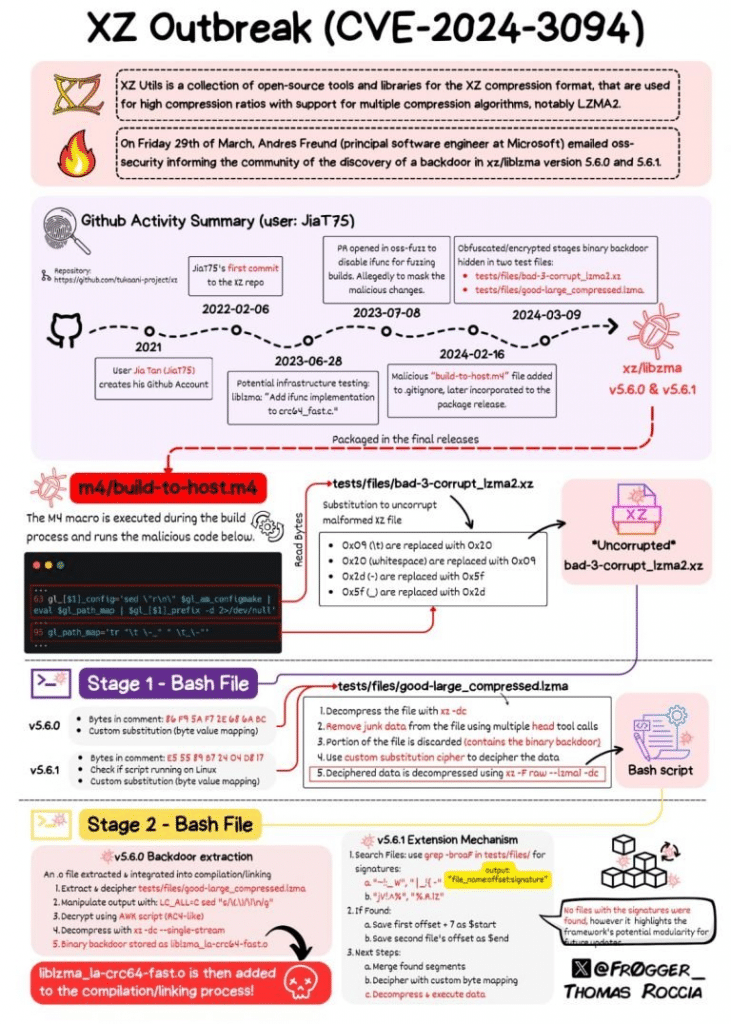
Affected Distributions and Response
| STATUS | DISTRIBUTION | RESPONSE |
|---|---|---|
| Affected | Fedora Rawhide and Fedora Linux 40 beta | Confirmed by Red Hat |
| Affected | openSUSE Tumbleweed and openSUSE MicroOS | Confirmed by openSUSE maintainers |
| Affected | Debian testing, unstable, experimental distributions | Confirmed by Debian maintainers |
| Affected | Kali Linux (updates between March 26th to March 29th) | Confirmed by OffSec |
| Affected | Some Arch Linux virtual machine and container images | Confirmed by Arch Linux maintainers |
| Not Affected | Red Hat Enterprise Linux (RHEL) | Confirmed by Red Hat |
| Not Affected | Ubuntu | Confirmed by Ubuntu |
| Not Affected | Linux Mint | Confirmed by Linux Mint |
| Not Affected | Gentoo Linux | Confirmed by Gentoo Linux |
| Not Affected | Amazon Linux and Alpine Linux | Confirmed by Amazon Linux and Alpine Linux maintainers |
Guidance and Recommendations
In light of these disclosures, affected parties have been advised to approach the situation as a definitive security incident, necessitating a comprehensive review and mitigation process. This includes the diligent examination for any unauthorized access or misuse, the rotation of exposed credentials, and a thorough security audit of systems that might have been compromised during the exposure window.
Insight into the Backdoor Mechanism
The intricacy of the backdoor, embedded within the xz-utils’ liblzma library and manifesting under precise conditions, notably through remote, unprivileged connections to public SSH ports, speaks volumes about the sophistication of the threat actors behind this maneuver. This backdoor not only raises concerns over performance degradation but also poses a significant risk to the integrity and security of the affected systems.
HOW TO DETECT IF YOU ARE A VICTIM
In light of the recent discovery of the CVE-2024-3094 backdoor in XZ Utils versions 5.6.0 and 5.6.1, the cybersecurity community has been on high alert. Binarly has introduced a free scanner to identify the presence of this backdoor in affected systems. Below is a detailed tutorial, including examples, on how to use the Binarly Free Scanner to detect the CVE-2024-3094 backdoor in your systems.
STEP 1: UNDERSTANDING THE THREAT
The CVE-2024-3094 backdoor in XZ Utils versions 5.6.0 and 5.6.1 poses a significant security risk, potentially allowing unauthorized remote access. It’s crucial to grasp the severity of this issue before proceeding.
Example: Imagine a scenario where an organization’s critical systems are running on a compromised version of XZ Utils, leaving the network vulnerable to attackers who could gain unauthorized access through the backdoor.
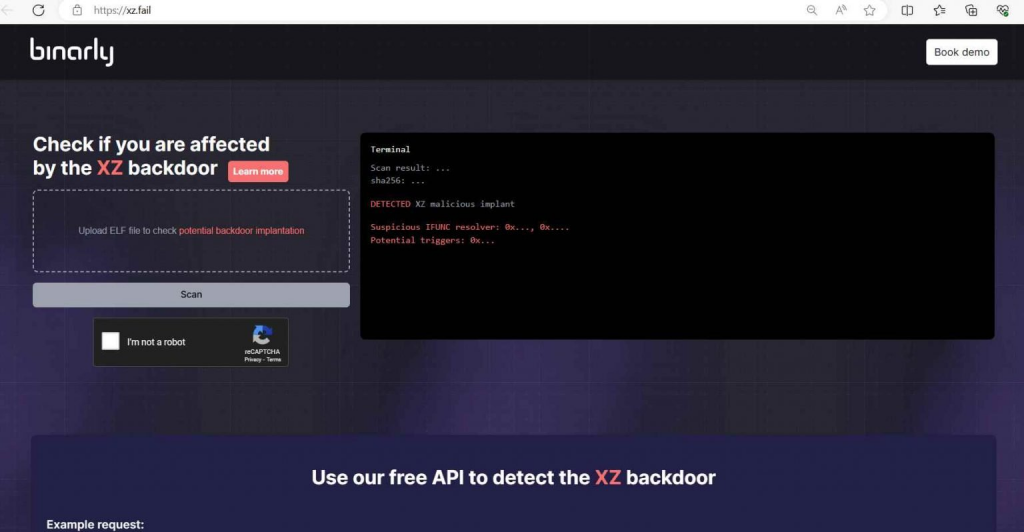
STEP 2: ACCESSING THE BINARLY FREE SCANNER
Navigate to XZ.fail, the dedicated website Binarly set up for the scanner.
Example: Open your web browser and type “https://xz.fail” in the address bar to access the Binarly Free Scanner’s homepage.
STEP 3: UTILIZING THE SCANNER
The Binarly Free Scanner uses advanced static analysis to detect the backdoor by examining ifunc transition behaviors in the binaries.
Example: After accessing XZ.fail, you’ll be prompted to upload or specify the path to the binary files you wish to scan. Suppose you want to check a file named example.xz; you would select this file for scanning through the web interface or command line, depending on the tool’s usage options provided.
STEP 4: INTERPRETING THE RESULTS
Once the scan completes, the scanner will report back on whether the CVE-2024-3094 backdoor was detected in the scanned files.
Example: If the scanner finds the backdoor in example.xz, it might display a message such as “Backdoor Detected: CVE-2024-3094 present in example.xz”. If no backdoor is found, a message like “No Backdoor Detected: Your files are clean” would appear.
STEP 5: TAKING ACTION
If the scanner detects the backdoor, immediate action is required to remove the compromised binaries and replace them with secure versions.
Example: For a system administrator who finds the backdoor in example.xz, the next steps would involve removing this file, downloading a secure version of XZ Utils from a trusted source, and replacing the compromised file with this clean version.
STEP 6: CONTINUOUS VIGILANCE
Regularly scan your systems with the Binarly Free Scanner and other security tools to ensure no new threats have compromised your binaries.
Example: Set a monthly reminder to use the Binarly Free Scanner on all critical systems, especially after installing updates or adding new software packages, to catch any instances of the CVE-2024-3094 backdoor or other vulnerabilities.
The Binarly Free Scanner is a powerful tool in the fight against the CVE-2024-3094 backdoor, offering a reliable method for detecting and addressing this significant threat. By following these steps and incorporating the examples provided, users can effectively safeguard their systems from potential compromise.
The accidental discovery of this backdoor by Freund represents a crucial turning point, underscoring the importance of vigilant and proactive security practices within the open-source domain. This incident serves as a stark reminder of the vulnerabilities that can arise in even the most trusted components of the digital infrastructure. It has sparked a renewed debate on the necessity for enhanced security protocols and collaborative efforts to safeguard crucial open-source projects against increasingly sophisticated threats.
In the aftermath, the open-source community and its stewards are called upon to reassess their security posture, emphasizing the need for comprehensive auditing, transparent communication, and the adoption of robust security measures to prevent future compromises. This incident not only highlights the vulnerabilities inherent in the digital landscape but also the resilience and collaborative spirit of the open-source community in responding to and mitigating such threats.

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory



