
The Practical Linux Handbook: A Beginner’s Guide to Mastering Everyday Tasks
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot
Jul 25 2024
Apr 03 2024
In an unsettling development that emerged late last week, the open-source community was thrust into a state of high alert following the disclosure that XZ Utils, a fundamental compression utility widespread across Linux distributions, had been compromised. This startling revelation has left a significant mark on the open-source ecosystem, prompting a swift and coordinated response from maintainers and security professionals alike.
Discovery of the Backdoor
The initial discovery of the backdoor was made by Andres Freund, a Microsoft software engineer, during routine diagnostics on Debian sid (development) installations. Freund’s investigation, sparked by unusually high CPU usage during SSH logins and accompanying error alerts, led to the identification of the culprit: a malicious insertion within the liblzma library, a core component of the XZ package. This finding was subsequently designated with the vulnerability identifier CVE-2024-3094. Attribution for this calculated insertion has been directed at an individual known as “Jia Tan” (JiaT75 on GitHub), who, through an elaborate scheme of social engineering and the use of sock puppet accounts, gained the trust of the XZ Utils maintainer community. This long-term infiltration underscores the advanced nature of the threat actor involved, pointing towards a highly skilled and resourceful adversary.
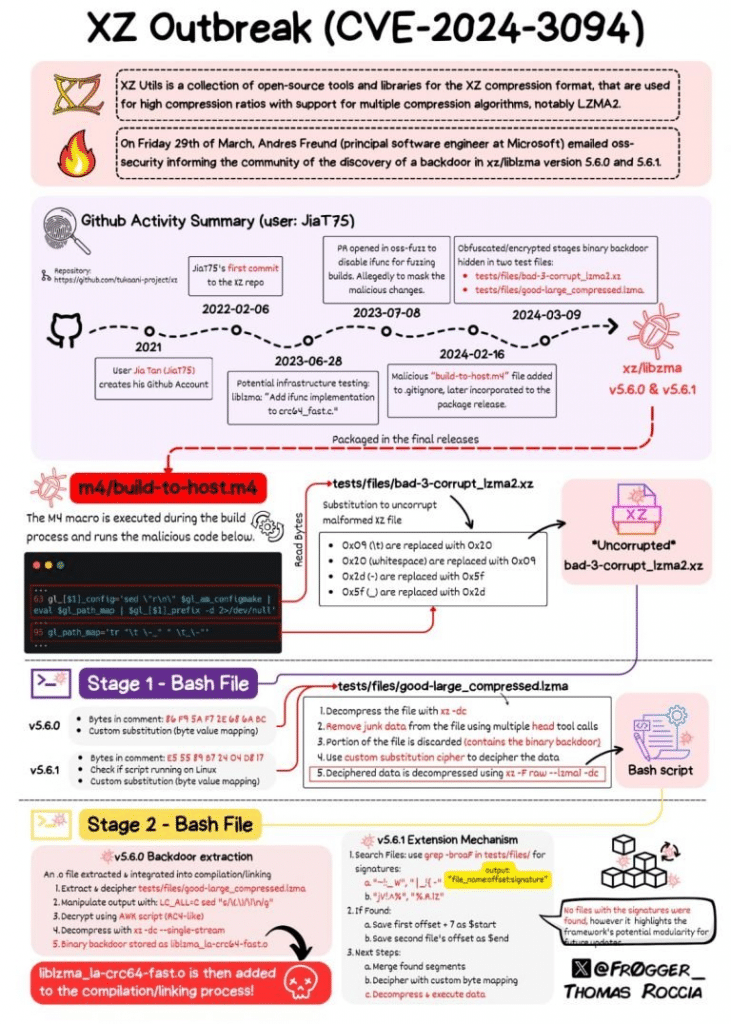
Affected Distributions and Response
| STATUS | DISTRIBUTION | RESPONSE |
|---|---|---|
| Affected | Fedora Rawhide and Fedora Linux 40 beta | Confirmed by Red Hat |
| Affected | openSUSE Tumbleweed and openSUSE MicroOS | Confirmed by openSUSE maintainers |
| Affected | Debian testing, unstable, experimental distributions | Confirmed by Debian maintainers |
| Affected | Kali Linux (updates between March 26th to March 29th) | Confirmed by OffSec |
| Affected | Some Arch Linux virtual machine and container images | Confirmed by Arch Linux maintainers |
| Not Affected | Red Hat Enterprise Linux (RHEL) | Confirmed by Red Hat |
| Not Affected | Ubuntu | Confirmed by Ubuntu |
| Not Affected | Linux Mint | Confirmed by Linux Mint |
| Not Affected | Gentoo Linux | Confirmed by Gentoo Linux |
| Not Affected | Amazon Linux and Alpine Linux | Confirmed by Amazon Linux and Alpine Linux maintainers |
Guidance and Recommendations
In light of these disclosures, affected parties have been advised to approach the situation as a definitive security incident, necessitating a comprehensive review and mitigation process. This includes the diligent examination for any unauthorized access or misuse, the rotation of exposed credentials, and a thorough security audit of systems that might have been compromised during the exposure window.
Insight into the Backdoor Mechanism
The intricacy of the backdoor, embedded within the xz-utils’ liblzma library and manifesting under precise conditions, notably through remote, unprivileged connections to public SSH ports, speaks volumes about the sophistication of the threat actors behind this maneuver. This backdoor not only raises concerns over performance degradation but also poses a significant risk to the integrity and security of the affected systems.
In light of the recent discovery of the CVE-2024-3094 backdoor in XZ Utils versions 5.6.0 and 5.6.1, the cybersecurity community has been on high alert. Binarly has introduced a free scanner to identify the presence of this backdoor in affected systems. Below is a detailed tutorial, including examples, on how to use the Binarly Free Scanner to detect the CVE-2024-3094 backdoor in your systems.
The CVE-2024-3094 backdoor in XZ Utils versions 5.6.0 and 5.6.1 poses a significant security risk, potentially allowing unauthorized remote access. It’s crucial to grasp the severity of this issue before proceeding.
Example: Imagine a scenario where an organization’s critical systems are running on a compromised version of XZ Utils, leaving the network vulnerable to attackers who could gain unauthorized access through the backdoor.
Navigate to XZ.fail, the dedicated website Binarly set up for the scanner.
Example: Open your web browser and type “https://xz.fail” in the address bar to access the Binarly Free Scanner’s homepage.
The Binarly Free Scanner uses advanced static analysis to detect the backdoor by examining ifunc transition behaviors in the binaries.
Example: After accessing XZ.fail, you’ll be prompted to upload or specify the path to the binary files you wish to scan. Suppose you want to check a file named example.xz; you would select this file for scanning through the web interface or command line, depending on the tool’s usage options provided.
Once the scan completes, the scanner will report back on whether the CVE-2024-3094 backdoor was detected in the scanned files.
Example: If the scanner finds the backdoor in example.xz, it might display a message such as “Backdoor Detected: CVE-2024-3094 present in example.xz”. If no backdoor is found, a message like “No Backdoor Detected: Your files are clean” would appear.
If the scanner detects the backdoor, immediate action is required to remove the compromised binaries and replace them with secure versions.
Example: For a system administrator who finds the backdoor in example.xz, the next steps would involve removing this file, downloading a secure version of XZ Utils from a trusted source, and replacing the compromised file with this clean version.
Regularly scan your systems with the Binarly Free Scanner and other security tools to ensure no new threats have compromised your binaries.
Example: Set a monthly reminder to use the Binarly Free Scanner on all critical systems, especially after installing updates or adding new software packages, to catch any instances of the CVE-2024-3094 backdoor or other vulnerabilities.
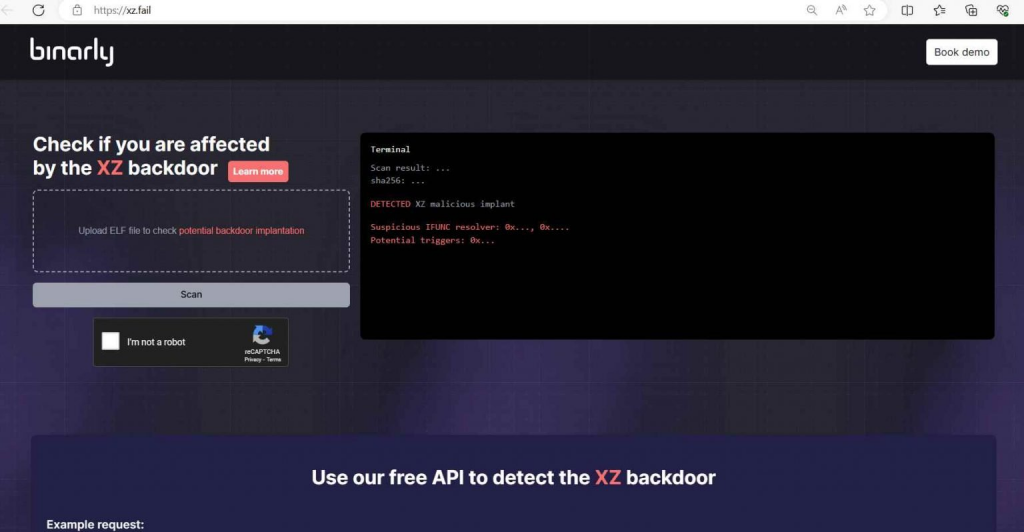
The Binarly Free Scanner is a powerful tool in the fight against the CVE-2024-3094 backdoor, offering a reliable method for detecting and addressing this significant threat. By following these steps and incorporating the examples provided, users can effectively safeguard their systems from potential compromise.
The accidental discovery of this backdoor by Freund represents a crucial turning point, underscoring the importance of vigilant and proactive security practices within the open-source domain. This incident serves as a stark reminder of the vulnerabilities that can arise in even the most trusted components of the digital infrastructure. It has sparked a renewed debate on the necessity for enhanced security protocols and collaborative efforts to safeguard crucial open-source projects against increasingly sophisticated threats.
In the aftermath, the open-source community and its stewards are called upon to reassess their security posture, emphasizing the need for comprehensive auditing, transparent communication, and the adoption of robust security measures to prevent future compromises. This incident not only highlights the vulnerabilities inherent in the digital landscape but also the resilience and collaborative spirit of the open-source community in responding to and mitigating such threats.

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Mar 15 2024
☝️ Pdf download ☝️

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Feb 03 2024
The recent discovery of a significant flaw in the GNU C Library (glibc), a fundamental component of major Linux distributions, has raised serious security concerns. This flaw grants attackers root access, posing a critical threat to the security of Linux systems.
__vsyslog_internal() function, which is called by the widely-used syslog and vsyslog functions.The discovery of the glibc flaw that grants root access to major Linux distributions is a stark reminder of the importance of system security and the need for constant vigilance. Users and administrators must take immediate action to mitigate the risk by applying patches and employing security best practices. As Linux continues to be a backbone for many systems and networks, ensuring its security is paramount for the integrity of countless applications and services.

Linux Basics for Hackers: Getting Started with Networking, Scripting, and Security in Kali
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Dec 27 2023
Researchers at AhnLab Security Emergency Response Center (ASEC) are warning about attacks targeting poorly managed Linux SSH servers, primarily focused on installing DDoS bots and CoinMiners.
In the reconnaissance phase, the threat actors perform IP scanning to look for servers with the SSH service, or port 22 activated, then launch a brute force or dictionary attack to obtain the ID and password.
Threat actors can also install malware to scan, perform brute force attacks, and sell breached IP and account credentials on the dark web.
Common malware used in attacks against poorly managed Linux SSH servers include ShellBot [1][2], Tsunami [3], ChinaZ DDoS Bot [4], and XMRig CoinMiner [5].

Once successfully logged in, the threat actor first executed the following command to check the total number of CPU cores.
| > grep -c ^processor /proc/cpuinfo |
“The execution of this command signifies that the threat actor has obtained the account credentials. Afterward, the threat actor logged in again using the same account credentials and downloaded a compressed file.” reads the analysis published by ASEC. “The compressed file contains a port scanner and an SSH dictionary attack tool. Additionally, commands accidentally typed by the threat actor can be seen, such as “cd /ev/network” and “unaem 0a”.”
These researchers believe that the tools employed in the attacks are based on the ones that have been created by the PRG old Team. Each threat actor created its custom version of the tools by modifying them.

The researchers recommend administrators should use strong passwords that are difficult to guess and change them periodically. These measures should protect the Linux SSH servers from brute force attacks and dictionary attacks. The experts also recommend updating to the latest patch to prevent attacks exploiting known vulnerabilities.
“Administrators should also use security programs such as firewalls for servers that are accessible from the outside to restrict access from threat actors. Finally, caution must be practiced by updating V3 to the latest version to block malware infection in advance.” concludes the report.

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Dec 18 2023
The 8220 hacker group, which was first identified in 2017 by Cisco Talos, is exploiting both Windows and Linux web servers with crypto-jacking malware. One of their recent activities involved the exploitation of Oracle WebLogic vulnerability (CVE-2017-3506) and Log4Shell (CVE-2021-44228).
However, the history of this threat group had several exploited vulnerabilities such as Confluence, Log4j, Drupal, Hadoop YARN, and Apache Struts2 applications. Their TTPs are evolved with different publicly released exploits.
In addition to this, the group was also discovered to be exploiting (CVE-2020-14883), a Remote code execution vulnerability in Oracle WebLogic Server. This exploitation chain is combined with another authentication bypass vulnerability (CVE-2020-14882) in the Oracle WebLogic server.
The exploitation methods of these two vulnerabilities are publicly available, making it relatively easy for the threat actor to modify and exploit them for malicious purposes.
Two different exploit chains were discovered, and one of them enables the loading of an XML file used for further phases of execution of commands on the OS, whereas the other one executes Java code without the use of an XML file.
The first infection chain uses different XML files that depend on the target OS. In the case of Linux, the downloading of other files is performed via cURL, wget, lwp-download, and python urllib along with a custom bash function that encodes it to base64.
The method injects a Java code which also initially evaluates the OS and executes the same command strings executed in the first method. Once the download and execution process takes place, the compromised hosts are infected with AgentTesla, rhajk, and nasqa malware variants.
A complete report has been published, which provides detailed information about the exploitation, command used, encoding, and other information.
URL
Source IPs
Common Windows, Linux and Web Server Systems Hacking Techniques

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Nov 09 2023
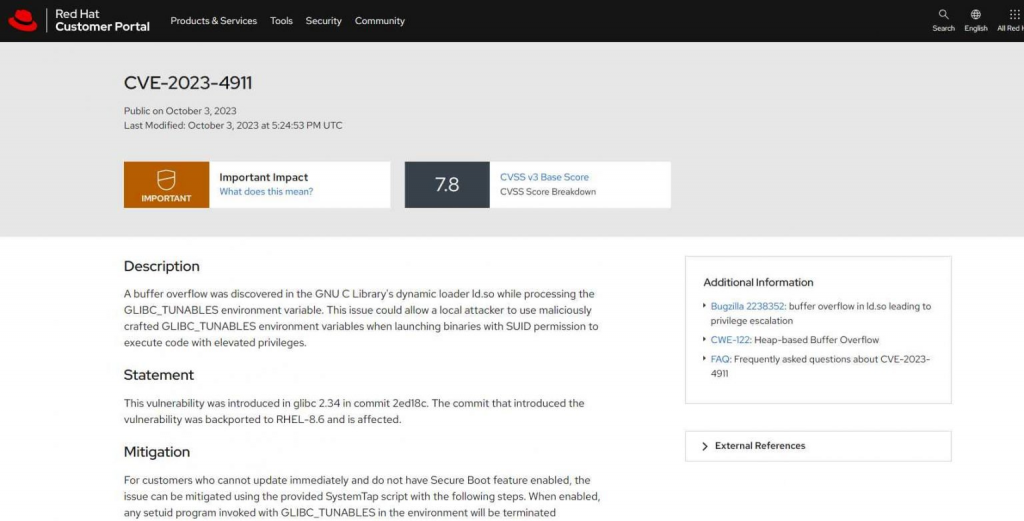
CVE-2023-4911 is a serious security vulnerability within the GNU C Library (glibc), specifically in the dynamic loader ld.so, associated with the processing of the GLIBC_TUNABLES environment variable. This vulnerability has been exploited in cloud attacks, particularly by a group using the Kinsing malware for cryptojacking operations.
The flaw is a buffer overflow that can be exploited by a local attacker using specially crafted GLIBC_TUNABLES environment variables when launching binaries with Set-UID (SUID) permissions, which could potentially allow the execution of code with elevated privileges. The Qualys Threat Research Unit has been credited with discovering this vulnerability.
This vulnerability has been given a severity score of 7.8, which classifies it as high severity. Exploitation of this flaw could enable an attacker to gain root permission on a Linux system that is running a vulnerable version of GLIBC, specifically version 2.34 or similar.
The issue has been noted to impact major Linux distributions, and organizations that use Linux systems, especially in cloud environments, are advised to patch this vulnerability promptly to mitigate the risks associated with it.
Exploit
To exploit CVE-2023-4911, threat actors would typically follow a sequence of steps that hinge on local access to a vulnerable system. The exploitation process can generally be broken down into the following stages:
ld.so is affected by the buffer overflow. This access could be obtained through various means, such as compromising a low-privileged user account.GLIBC_TUNABLES environment variable. This variable is meant to be used for tuning performance and behavior aspects of the GNU C Library, but when crafted maliciously, it can trigger a buffer overflow.ld.so) is handling the environment variable.Here’s a hypothetical example:
GLIBC_TUNABLES variable and uses it in conjunction with a vulnerable application that has SUID set to run as root.ld.so, which Bob exploits to redirect the application’s execution flow to his shellcode.It’s important to note that exploitation of CVE-2023-4911, like many vulnerabilities, requires specific conditions to be met and often sophisticated knowledge of software internals, memory layout, and exploitation techniques. The exact details of the exploit can vary based on the system’s configuration, the attacker’s goals, and the environment variables involved.
The Aqua Nautilus team documented an attack by the Kinsing malware that exploited CVE-2023-4911 to elevate permissions on a compromised machine. Here’s how they described the exploitation process:
/tmp.gnu-acme.py, which was an exploit for the Looney Tunables vulnerability (CVE-2023-4911), allowing for local privilege escalation by exploiting a buffer overflow in the handling of the GLIBC_TUNABLES environment variable by ld.so.This attack demonstrates the attackers’ sophisticated capabilities in chaining vulnerabilities to penetrate cloud environments, gain unauthorized access, and elevate privileges within the system.
Kinsing aims to gather CSP credentials, potentially exposing sensitive data, like AWS instance identity, which poses risks in cloud environments.
Here below, we have mentioned all the types of credentials and data that could be exposed:-
Mitigation
To mitigate an attack exploiting CVE-2023-4911, you should take the following steps:
By following these steps, you can significantly reduce the risk of exploitation and mitigate potential damage from attacks like those involving CVE-2023-4911.
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Oct 09 2023
Kali Linux turns 10 this year, and to celebrate, the Linux penetration testing distribution has added defensive security tools to its arsenal of open-source security tools.
It remains to be seen if Kali Purple will do for defensive open source security tools what Kali Linux has done for open source pentesting, but the addition of more than 100 open source tools for SIEM, incident response, intrusion detection and more should raise the profile of those defensive tools.
For now, Kali is primarily known for its roughly 600 open source pentesting tools, allowing pentesters to easily install a full range of offensive security tools.
In this article, we’ll focus primarily on how to use this powerful OS to run a pentest and mistakes to avoid. We’ll give you an overview of what can be achieved with Kali Linux using a short selection of pre-installed tools. While this guide serves as an introduction to common pentesting phases, with practical examples that highlight best practices, it’s not a substitution for a complete professional pentesting methodology.
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Oct 05 2023
The team at Qualys Threat Research Unit has unveiled a fresh vulnerability within the Linux operating system, allowing local attackers to escalate their access level to root privileges. This escalation is made possible by exploiting a buffer overflow weakness located in the GNU C Library’s ld.so dynamic loader. Assigned the identification CVE-2023-4911 and nicknamed “Looney Tunables,” this vulnerability is recognized as high-risk with a CVSS score of 7.8, signifying its high severity.
“Looney Tunables” allows bad actors to exploit a buffer overflow within the ld.so dynamic loader of the GNU C Library (glibc). This exploitation path provides local attackers with a mechanism to elevate their privileges to root level, thereby gaining unparalleled access and control over the system. Given that root privileges allow complete control over a system, attackers can execute a variety of malicious activities, from accessing sensitive information to altering system settings and functionalities, underscoring the critical nature of this security flaw.
The GNU C Library, or glibc, is fundamentally integral to the operation of a majority of systems based on the Linux kernel. This crucial library facilitates numerous system calls, from elementary functions like open, malloc, and printf to more complex ones such as exit, serving as the operational backbone for these systems. As such, glibc plays a pivotal role in the functionality and performance of Linux-based systems, making any vulnerability within this library particularly concerning for system administrators and users alike.
Within glibc, the ld.so dynamic loader is an element of paramount importance. This component is tasked with the significant responsibility of initializing and running programs on Linux systems that rely on glibc for their operation. Its role is crucial as it ensures the smooth execution of various applications and services on a Linux system, making it an indispensable part of the operating environment. Given its central function, any vulnerability within the ld.so dynamic loader is a matter of serious concern as it could potentially compromise the security and stability of a wide range of systems.
In light of the discovery of “Looney Tunables”, it is imperative for organizations and users utilizing Linux-based systems to acknowledge and address this security vulnerability swiftly to safeguard their systems against potential exploits. Immediate mitigation steps, including the application of security patches and updates, should be undertaken to protect systems from the risks associated with this high-severity vulnerability. Users and administrators should stay vigilant and monitor any security advisories and updates issued by the Linux community and cybersecurity experts to ensure timely and effective protection against this newly identified threat.
Furthermore, it would be prudent for organizations to adopt and enforce a set of security best practices. These might include the regular updating and patching of systems, the use of reliable security solutions, conducting cybersecurity awareness and training programs for employees, and implementing network segmentation strategies. These proactive measures can significantly enhance the security posture of an organization, providing robust defense mechanisms against “Looney Tunables” and other similar security threats that might emerge in the future.
The GNU C Library’s ld.so dynamic loader was found to include the security flaw, which exposed a crack in the armor. During the processing of the ‘GLIBC_TUNABLES’ environment variable, this security hole might manifest itself. To put it more simply, a hostile attacker on the local network who has some dexterity and cunning may insert text into the ‘GLIBC_TUNABLES’ environment variable. The attacker is able to execute code with dangerously high privileges if they do this while beginning binaries that have the SUID permission.
This vulnerability was discovered by the observant members of the Qualys Threat Research Unit. According to an investigation into the origin of the vulnerability, it was first discovered in April 2021, when glibc version 2.34 was being distributed. Ironically, the commit was made with the intention of improving security by correcting the behavior of SXID_ERASE in setuid applications.
It is important to keep in mind that attackers, even those with just the most basic privileges, are able to take advantage of this severe gap. since of their simplicity and since they don’t need any input from the user, these assaults are particularly alarming.
There is a solution available for those who are unable to update their software promptly and do not have the Secure Boot capability. A SystemTap script has been made available, and once it is enabled, it will immediately stop any setuid application that has been launched with the ‘GLIBC_TUNABLES’ environment variable present. To securely call the setuid program thereafter, one just has to unset or remove the ‘GLIBC_TUNABLES’ environment variable, for instance by executing the command ‘GLIBC_TUNABLES= sudo’.
According to Saeed Abbasi, who is the Product Manager at Qualys’ Threat Research Unit, “Our successful exploitation, leading to full root privileges on major distributions like Fedora, Ubuntu, and Debian, underscores the profound and ubiquitous nature of this vulnerability.”
While the Qualys team has indicated that they will not release its exploit code at this time, the inherent simplicity of transforming the buffer overflow into a data-only assault suggests that other research teams may soon take up the challenge.
Systems that are running Debian 12 and 13, Ubuntu 22.04 and 23.04, or Fedora 37 and 38 are vulnerable to the CVE-2023-4911 flaw and should be avoided at all costs. The extent of the possible harm might be enormous due to the widespread use of the glibc library in Linux’s many different distributions. Distributions such as Alpine Linux, which use the musl libc library instead of the glibc library, are given a little bit of wiggle room.
Linux Pocket Guide: Essential Commands
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Aug 19 2023
The Linux Distros is generally acknowledged as the third of the holy triplet of PC programs, along with Windows and macOS. Here we have provided you with a top 10 best Linux distros in 2023 for all professionals.
Hence Linux can be defined as the most rebellious among the three, as it’s flexible and customizable, including a bunch of various Best Linux distros designed by unique associations for various values.
Moreover, the Linux “core” (kernel) and most distros are free, which is a significant trading point for the OS when it is compared to Windows and macOS.
As there are several Linux distros are available for various situations. Even if you are behind an OS that is customized for desktops, workstations, laptops, servers, gaming, or A/V editing, there is a distro over there for everyone.
Hence, we are trying to summarize the most reliable and popular Linux distros accessible, each of which is customized for desktop use.
Therefore, you can install those Linux distros on a Chromebook, PC, or Mac as a substitute for your prevailing operating system, utilize both in a dual-boot scenario or in combination with one of the best practical tools out there.
Well, if you want a Linux distro similar to Windows? Or do you like to apply commands rather than click? Or do you want something special on privacy? These and several other determinants will help you decide which would be the most suitable Linux distro for you.
Usually, the top Linux distros list is customized to meet users’ requirements. For example, Kali Linux is specifically created for digital forensics and penetration testing.
Hence, here in this article, we have selected the top 10 best Linux distros list, and we have updated this list from Popular Linux distro 2022.
As we have said before that Linux is flexible and customizable, which includes a bunch of unique features for different uses.
Moreover, we can also say that Linux is a house to nearly each programming language, and it is a Unix-like operating system.
Hence, this open-source operating system is basically designed as per the Linux kernel and is usually collected in multiple Linux distributions.
Thus the Linux distributions, traditionally known as a distro, are operating systems that progressed from a software compilation based on the Linux kernel.
Various users use Linux by downloading one of the various Linux distros. Linux operating systems are most common to coders, programmers, and gamers.
Thus, we can say that Linux is a worldly gift that has shaped our modern lives. In today’s world, we can’t imagine a particular moment outwardly technology.

| Distro | Key Features |
| Ubuntu | Compiz performance improvements. Kernel 3.11 LibreOffice 4.12 |
| CentOS | Excellent documentation and support community. Based on Debian. Open stack interface. |
| Debian | Morden branch of GnuPG UEFI support improved MariaDB is default |
| Linux Mint | Software manager Automatic updates Better file search in Nemo |
| Arch Linux | Easy installation Great learning tool |
| Tails | Stream isolation Onion circuit’s graphical frontend Network manager |
| Fedora | Dynamic firewall Better end-user software Virtual desktop support |
| Elementary OS | Easy image resizing Keyboard shortcut cheat sheet Bold use of color |
| Kali Linux | Full customization Full disk encryption Metapackages |
| MX Linux | One-click enabling event sound. Hibernation is now enabled by default. Easy and flexible installation. |
Therefore, Linux has produced the most significant innovations in the creation of modern technology.
At first, Linux was not like the form it is; it has evolved a long way through varied crafting and drafting from an open-source friendly association.
Thus, without a doubt, we can say that Linux does not only appear with a delicate-looking desktop manager, but it also contributes a wide range of beneficial and productive sets of free and open-source software for performing all the basic and necessary needs of the users.
Now, without wasting much time, let’s explore the list below.
InfoSec tools | InfoSec services | InfoSec books | Follow our blog
Jul 28 2023
Two vulnerabilities in the Linux operating system Ubuntu have been found by researchers. Both of these vulnerabilities have the ability to offer attackers elevated privileges.There have been indications that a vulnerability that allows for an increase in privilege may be detected in the OverlayFS module of Ubuntu operating systems.
A Linux filesystem known as OverlayFS has seen significant adoption in the container industry. OverlayFS makes it possible to deploy dynamic filesystems while maintaining compatibility with pre-built images.
When invoking the ovl_do_setxattr function on Ubuntu kernels, the ovl_copy_up_meta_inode_data module has the potential to bypass permission checks. This vulnerability occurs as a result. This vulnerability has been assigned a CVSS score of 7.8, which is considered to be High.
There is a flaw in Ubuntu known as SAUCE: overlayfs bypass permission checks for trusted that leads to this vulnerability.overlayfs. * xattrs. * xattrs.
This vulnerability may be exploited by an attacker who does not have rights by establishing privileged extended attributes on the mounted files and then setting them on the other files without necessary checks being performed. This vulnerability has been assigned a CVSS score of 7.8, which is considered to be High.
The Ubuntu Patch from 2018 is in Conflict with the Linux Kernel Project from 2019 and 2022.
Since the OverlayFS module may be used by non-privileged users via user namespaces, it is a perfect candidate for local privilege escalation. In 2018, Ubuntu released patches that addressed these security flaws.
Despite this, researchers working for Wix discovered that the Linux Kernel Project released many new versions in the years 2019 and 2022.
There was a problem between the older patches and the most recent version as a direct consequence of the changes that were made to the OverlayFS module.
These exploits are already accessible to the public in their exploitable forms. It is strongly advised that anyone using Ubuntu versions earlier than 23.04 update to the most recent release in order to prevent these vulnerabilities from being exploited. On the other hand, the majority of cloud security providers (CSPs) have been using insecure versions of the Ubuntu Operating System as their default system.
Researchers believe that around forty percent of computers running Ubuntu might have been affected by the issue, making the anticipated scope a large one. According to Canonical, the business that is responsible for Ubuntu and also operates for profit, the desktop version of the software was installed more than 20 million times in 2017. Ubuntu has issued a security alert that addresses many vulnerabilities and gives credit to the researchers who discovered them.
InfoSec books | InfoSec tools | InfoSec services
May 11 2023
The Linux kernel is the most important part of the Linux operating system. It is in charge of managing system resources, delivering necessary services, and guaranteeing the general stability of the system. As a result, any vulnerability inside the kernel has the potential to have major implications, which might put the system’s overall security and integrity at risk. The Linux kernel has been found to include a major security flaw, which has been given the identifier CVE-2023-32233. This flaw makes it possible for locally authenticated users to gain additional rights while using the system. A locally authenticated attacker is able to get elevated privileges as root by submitting a specifically constructed request thanks to the vulnerability, which is caused by a use-after-free hole in Netfilter nf_tables while processing batch requests. The bug was caused by a use-after-free flaw. Linux has a subsystem known as netfilter nf_tables that is responsible for managing the setup of firewall rules. The problem is that Netfilter nf_tables is accepting some improper modifications to its configuration, which is causing the issue.
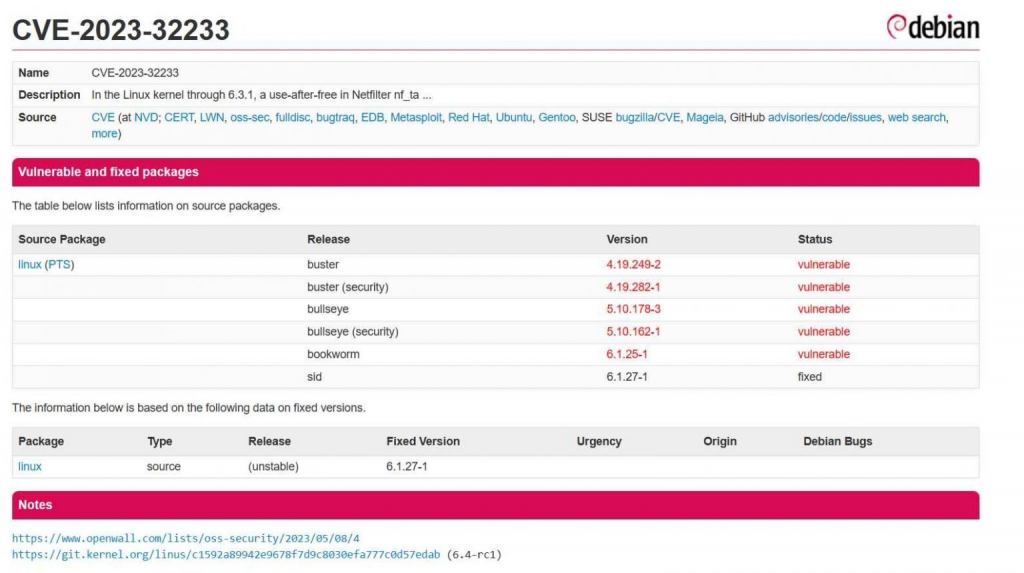
Security researchers Piotr Krysiuk and Piotr Krysiuk found the vulnerability and built an attack for it. The exploit makes it possible for local users without administrative privileges to launch a root shell by exploiting the problem. This attack was discussed in confidence with the Linux kernel security developers so that they may get assistance in developing a solution.
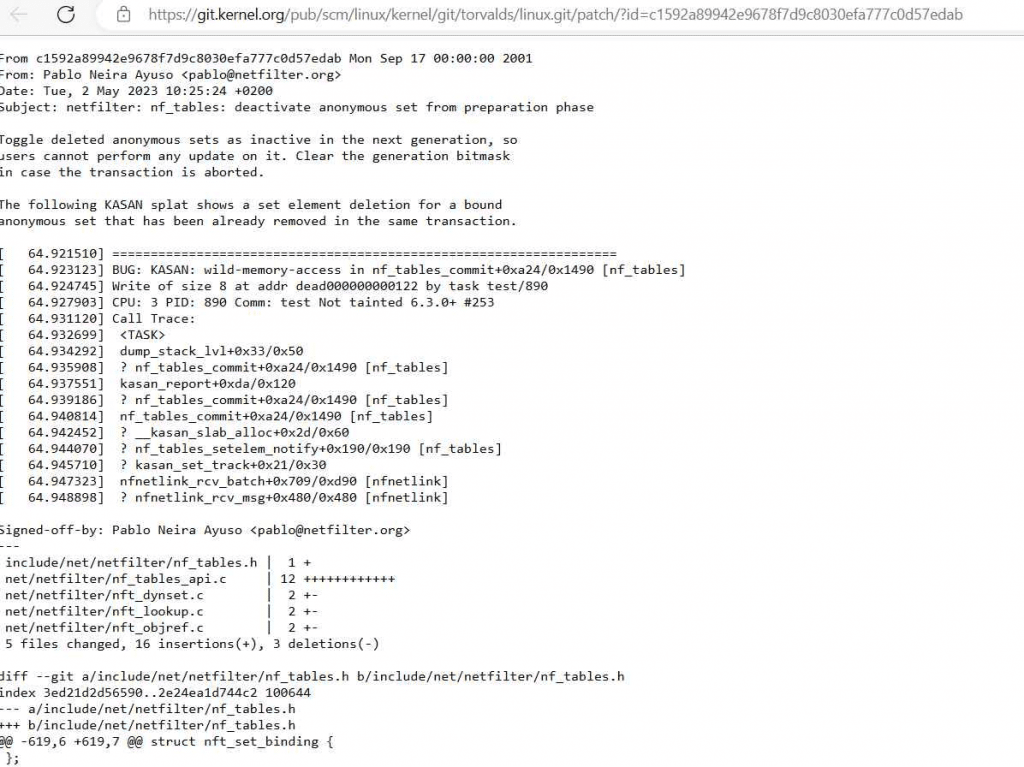
An adversary might take advantage of this vulnerability in a particular situation by constructing an erroneous batch request that includes actions that lead to a corruption of the internal state of Netfilter nf_tables. Because of this, the attacker is granted the ability to obtain root access to the system and further elevate their privileges.
The mainline kernel git repository now provides a patch that may be used to resolve the vulnerability that was discovered. Administrators and users of the system are strongly encouraged to deploy the patch as quickly as they can in order to prevent their systems from the possibility of being exploited.
Multiple versions of the Linux kernel, including the most recent stable release, Linux 6.3.1, have been used to successfully replicate the issue. If this vulnerability is not fixed, it may be used by hostile actors to obtain unauthorized access to the system with elevated privileges. As a result, sensitive data may be compromised, and serious disruption may occur.
InfoSec tools | InfoSec services | InfoSec books

Mar 11 2023
Looking to enhance your Linux skills? Practical examples to build a strong foundation in Linux – credit: Ramesh Nararajan
*******************************************

Mastering Linux Security and Hardening: A practical guide to protecting your Linux system from cyber attacks
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Feb 15 2023
The Linux Distros is generally acknowledged as the third of the holy triplet of PC programs, simultaneously with Windows and macOS. Here we have provided you with a top 10 best Linux distros list 2023 for all professionals.
Hence Linux can be defined as the most rebellious among the three, as it’s flexible and customization, including a bunch of various Best Linux distros designed by unique associations for various values.
Moreover, the Linux “core” (kernel) and most distros are free, which is a significant trading point for the OS when it is compared to Windows and macOS.
As there are several Linux distros are available for various situations. Even if you are behind an OS that is customized for desktops, workstations, laptops, servers, gaming, or A/V editing, there is a distro over there for everyone.
Hence, we are trying to give you a summary of the most reliable and popular Linux distros accessible, each of which is customized for desktop use.
Therefore, you can install those Linux distros on a Chromebook, PC, or Mac as a substitute for your prevailing operating system, utilize both in a dual-boot scenario, or utilize them in combination with one of the best practical tools out there.
Well, if you want a Linux distro similar to windows? Or do you like to apply commands rather than click? Or do you want something special on privacy? Each of these and several other determinants will conclude which would be the most suitable Linux Distros for you.
Usually, the top Linux distros list is customized to meet the requirements of users. For example, Kali Linux is specifically created for digital forensics and penetration testing. Hence, here in this article, we have selected the top 10 best Linux distros list and we have updated this list from Popular Linux distro 2022.
As we have said before that Linux is flexible and customizable, which includes a bunch of unique features for different uses.
Moreover, we can also say that Linux is a house to nearly each programming language, and it is a Unix-like operating system.
Hence, this open-source operating system is basically designed as per the Linux kernel and is usually collected in multiple Linux distributions.
Thus the Linux distributions, traditionally known as a distro, are operating systems that progressed from a software compilation based on the Linux kernel.
Various users use Linux by downloading one of the various Linux distros. Linux operating systems are most common to coders, programmers, and gamers.
Thus, we can say that Linux is a worldly gift that has formed our modern life. Well, in today’s world, we can’t imagine a particular moment outwardly technology.
| Distro | Key Features |
| Ubuntu | Compiz performance improvements. Kernel 3.11 LibreOffice 4.12 |
| CentOS | Excellent documentation and support community. Based on Debian. Open stack interface. |
| Debian | Morden branch of GnuPG UEFI support improved MariaDB is default |
| Linux Mint | Software manager Automatic updates Better file search file in Nemo |
| Arch Linux | Easy installation Great learning tool |
| Tails | Stream isolation Onion circuit’s graphical frontend Network manager |
| Fedora | Dynamic firewall Better end-user software Virtual desktop support |
| Elementary OS | Easy image resizing Keyboard shortcuts cheat sheet Bold use of color |
| Kali Linux | Full customization Full disk encryption Metapackages |
| MX Linux | One-click enabling event sound. Hibernation is now enabled by default. Easy and flexible installation. |
Therefore, Linux has produced the most significant and meaningful innovations in the creation of modern technology.
At first, Linux was not like the form as now it is, it has evolved a long way through varied crafting and drafting from an open-source friendly association.
Thus, with no doubt, we can say that Linux does not only appear with a delicate-looking desktop manager, but it also contributes a wide range of beneficial and productive sets of free and open-source software for performing all the basic and necessary needs of the users.
Now without wasting much time, let’s get started and simply explore the whole list that we have mentioned below.

Linux for Beginners: A Practical and Comprehensive Guide to Learn Linux Operating System and Master Linux Command Line. Contains Self-Evaluation Tests to Verify Your Learning Level
Previous posts on Linux Security
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Jan 20 2023
Sudo is one of the most essential, powerful, and often used tools that comes as a core command pre-installed on macOS and practically every other UNIX or Linux-based operating system. It is also one of the programs that comes pre-installed as a core command. A system administrator has the ability to delegate authority to certain users or groups of users through the use of the sudo (su “do”) command, which provides an audit trail of the commands that were executed and the arguments that were passed to those commands. This allows the administrator to give certain users or groups of users the ability to run some or all commands as root or another user.
A new sudo vulnerability was found. It was on sudoedit (sudo -e) flaw. With it, attackers can edit arbitrary files, and therefore machines were at the risk of the pwned and having information steeled.
Researchers Matthieu Barjole and Victor Cutillas of Synacktiv uncovered the weakness, which was given the identifier CVE-2023-22809, in the sudoedit function for Linux. This vulnerability might enable a malicious user with sudoedit access to edit arbitrary files on a system running Linux.
In order to give its users with the ability to pick the editor of their choosing, Sudo makes use of environment variables that are supplied by the user. The contents of these variables provide additional information to the command that is ultimately sent to the sudo edit() function. The latter, on the other hand, is dependent on the existence of the — argument in order to establish the list of files that need to be edited. This list may be changed by the insertion of an additional — argument into one of the approved environment variables, which can then lead to a privilege escalation through the modification of any other file with the rights of the RunAs user. This problem appears after the sudoers policy validation has been completed.
Versions of sudo that came out before 1.8.0 built the argument vector in a different way and are not impacted by this issue. It is strongly suggested that users get their systems up to date with the most recent version.
Checkout our previous posts on topic of Linux Security
InfoSec books | InfoSec tools | InfoSec services
Jan 16 2023
A new privilege escalation vulnerability has been identified in the Linux kernel by researcher Davide Ornaghi. This vulnerability might enable a local attacker to execute code on vulnerable computers with elevated rights if the kernel is installed on those systems. Additionally, Davide published the proof-of-concept and the write-up. The vulnerability, which has been assigned the tracking number CVE-2023-0179, is a stack-based buffer overflow that exists in the Netfilter subsystem. An authorized attacker might exploit this issue to get elevated privileges as root if the attacker executed a program that had been carefully written for the purpose.
The Linux kernel has a framework known as netfilter that enables a variety of networking-related actions to be performed in the form of individualized handlers. This may be accomplished by filtering incoming network packets. Netfilter provides the functionality necessary for directing packets through a network and preventing packets from reaching sensitive locations within a network by offering a variety of functions and operations for packet filtering, network address translation, and port translation. [1] These features allow Netfilter to provide the functionality required for directing packets through a network.

Linux Basics: The Command Line Interface
Jan 03 2023
If you’re interested in penetration testing and digital forensics, you know that Kali Linux is worth a try. And if you’re already doing it, chances are good you are already using it.
We talked to Jim O’Gorman, Chief Content and Strategy Officer at Offensive Security (OffSec), about the direction in which the development of the open-source distro is headed.
[The answers have been edited for clarity.]
Two questions drive Kali’s development:
1. What needs to be done to ensure that Kali Linux is the best possible platform for professional and hobbyist information security work?
2. What needs to be done to ensure that Kali is the best possible platform for information security training?
There is a lot of overlap between those two questions, but realistically they are separate and distinct items. However, by getting them both right on a single platform, we create an environment where people can train, study, and learn, but also use the same platform for real-world efforts. In essence, it means that you train like you fight.
The answer to the first question is driven by input from the Kali and OffSec teams. As infosec professionals ourselves, what are the things we run into on a day-to-day basis and how do we make our life easier by ensuring the toolset is of the highest quality possible? We also work closely with OffSec’s pentesting team.
We also listen to input from other Kali users. Kali is a totally open-source project and anyone and everyone can pitch in and contribute. And they do! If you wish a tool to be included in Kali, package it and submit it! If you wish a configuration worked a certain way out of the box, modify the package and submit the change. It’s very direct and easy to do, and it is in our documentation. Anyone – regardless of their background – can play a part.
The second way users influence development is through bug reports, feature requests, and conversations on OffSec’s Discord and other social media. The Kali team is out there as part of the infosec community – talk to us and let us know what you are seeing. Also, when possible, we will set up private conversations with large organizations that use Kali to get a feel for their unique needs.
The answer the second question – How to make Kali the best possible platform for training? – we work very closely with the OffSec content development team to find out what tools they are using for training, what sort of default environment works best for learners, and what we can do in Kali to support general education efforts.
Surprisingly, even though Kali is built for advanced information security work, it is often the first Linux many users ever use. So we are careful with the design of Kali to ensure that it is approachable. We want to ensure that you don’t have to be a Linux professional to utilize Kali successfully in OffSec courses.
The changing of attack techniques over time does not impact Kali as much as you might think, as techniques are more often than not implemented in tools and scripts. While the tools and scripts change, Kali Linux as a platform to launch them does not have to change much. The closest item to this is expanding Kali to run everywhere. Our goal is to put the Kali toolset as close as possible to you no matter where you are.
Kali installed on bare metal, Kali in a VM, Kali in containers (Docker & LXC), Kali on WSL, Kali on various ARM devices such as Raspberry Pi, Kali in a cloud instance such as AWS and Azure, Kali on your Android phone or tablet – we even have Kali running on a watch! No matter where you are or what your needs are, we want Kali to be easy to access and run.
Kali is primarily gered towards pentesting and red teaming, but we are looking at expanding into other areas of information security as well.
What tools run in Kali is really a matter of input from the team, community, and OffSec. Our goal is to have the most frequently used and important tools installed and working out of the box. Other common tools are installed quickly and easily with a single command.
We add new tools based on the answers to a number of questions: What functionality does the tool provide and is it unique or different enough from functionalities of other tools? Is the tool going to be maintained and updated over a reasonable period of time? How functional is the tool? It is a wrapper for another tool? Does the developer have a positive reputation?
If a tool stops being updated and stops working, we’ll try to work with the author. If they are unresponsive and the effort of maintaining the tool becomes too complex, we document this and then often remove it.
We get a lot of input from the OffSec pentesting team on what tools they are using in the field today, as well as the OffSec content developers on what tools are being used as part of the courseware. The idea is to have all the tools used in OffSec coursework out of the box to keep things easy for students.
When prioritizing features, we look at what is needed at the current time. We release Kali in quarterly updates so that dictates our development cycle. Each cycle we look at what is happening in the industry, where the gaps are, and determine what to prioritize.
On this front, there is a lot to balance. Everything from the distribution of Kali, installation, user experience, tools, stability, so on and so forth. It’s a full operating system and a small team so we have to pick and choose what goes into it, we can’t do everything each cycle. Again, input from the community and OffSec sets the priorities.
As Kali is a base OS, not right now. For tools that run in Kali, perhaps in time. As soon as the tools are there we will add them into Kali if they are any good. But there are also always fad trends so we tend not to get over-excited about them until they start to actually deliver results.
We have seen demonstrations of tools being developed with some of the PoC which have been creating some buzz, but as they are not ready to be released we are a ways off from this yet.
5 Kali Linux tools you should learn how to use
5 Kali Linux books you should read this year
New Book: Advanced Security Testing with Kali Linux!
Infosec books | InfoSec tools | InfoSec services
Dec 27 2022
Just before the Christmas weekend – in fact, at about the same time that beleaguered password management service LastPass was admitting that, yes, your password vaults were stolen by criminals after all – we noticed a serious-sounding Linux kernel vulnerability that hit the news.
The alerts came from Trend Micro’s Zero Day Initiative (ZDI), probably best known for buying up zero-day security bugs via the popular Pwn2Own competitions, where bug-bounty hunting teams compete live on stage for potentially large cash prizes.
In return for sponsoring the prize money, the vendors of products ranging from operating systems and browsers to networked printers and internet routers hope to buy up brand new security flaws, so they can fix the holes responsibly. (To collect their prizes, participants have to provide a proper write-up, and agree not to share any information about the flaw until the vendor has had a fair chance to fix it.)
But ZDI doesn’t just deal in competitive bug hunting in its twice-a-year contests, so it also regularly puts out vulnerability notices for zero-days that were disclosed in more conventional ways, like this one, entitled Linux Kernel ksmbd Use-After-Free Remote Code Execution Vulnerability.
SMB is short for server message block, and it’s the protocol that underpins Windows networking, so almost any Linux server that provides network services to Windows computers will be running software to support SMB.
As you can therefore imagine, SMB-related security bugs, especially ones that can be exploited over the network without the attacker needing to logon first, as is the case here, are potentially serious issues for most large corporate networks.
SMB support is also generally needed in home and small-business NAS (network attached storage) devices, which generally run Linux internally, and provide easy-to-use, plug-it-in-and-go file server features for small networks.
No need to learn Linux yourself, or to set up a full-blown server, or to learn how to configure Linux networking – just plug-and-play with the NAS device, which has SMB support built-in and ready to go for you.
In this case, the bug wasn’t deliberately disclosed on the night before the night before the night before Christmas in a not-so-ho-ho-ho bid to spoil your festive season by freaking you out.
And it wasn’t reported just before the weekend in a bid to bury bad PR by hoping you’d be vacation-minded enough either to miss the story completely or to shrug it off until the New Year.
The good news is that, as usually happens under the umbrella of responsible disclosure, the date for ZDI’s report was agreeed in advance, presumably when the flaw was disclosed, thus giving the Linux kernel team sufficient time to fix the problem properly, while nevertheless not allowing them to put the issue off indefinitely.
In this case, the bug report is listed as having happened on 2022-07-26, and what ZDI refers to as the “co-ordinated public release of [the] advisory” was set for 2022-12-22, which turns out to be exactly 150 days, if you count old-school style and include the full day at each end.
So, even though this bug has had some dramatic coverage over the holiday weekend, given that it was a remote code execution (RCE) hole in the Linux kernel itself, and came with a so-called CVSS score of 10/10, considered Critical…
…it was patched in the Linux source code within just two days of disclosure, and the fix was accepted and packaged into the official Linux kernel source code in time for the release of Linux 5.15.61, back on 2022-08-17, just 23 days after the report first came in.
In other words, if you’ve updated your Linux kernel any time since then, you’re already safe, no matter what kernel compilation settings you or your distro used. (This includes 24 subsequent updates to the kernel 5.15 series, now at 5.15.85, along with any versions of kernel 6.0, kernel 6.1 and the still-in-candidate-stage kernel 6.2, all of which had their first releases after August 2022.)
Also, although it sounds at first glance as though this bug will inevitably affect any Linux server or device supporting Windows networking, that’s not true either.
Most sysadmins, and in our experience most NAS programmers, provide Windows SMB supprt via a long-running and well-respected open source toolkit called Samba, where the name Samba is simply the closest pronounceable word that the original developer, open-source luminary Andrew “Tridge” Tridgell OAM, could find to represent the abbreviation SMB.
Anyone who has used Samba will know that the software runs as a regular application, in what’s known as user space, in other words, without needing its own code running inside the kernel, where even modest bugs could have dangerous repercussions.
Indeed, the main Samba program file is called smbd, where the trailing -D is a typical Unixism standing for daemon, or background process – what Windows admins would call a service.
This bug, as you can see from the ZDI report, is in a kernel module called ksmbd, where the -D denotes a background service, the -SMB- denotes Windows networking support, and the K- means runs in kernel space, i.e. right inside the kernel itself.
At this point, you’re probably asking yourself, “Why bury the complexity of supporting SMB right into the kernel, given that we’ve already got a reliable and well-respected user-space product in the form of Samba, and given that the risks are much greater?”
Why, indeed?
As so often, there seem to be two main reasons: [A] because we can! and [B] because performance.
By pushing what are typically high-level software features down into the kernel, you can often improve performance, though you almost always pay the price of a corresponding, and possibly considerable, decrease in safety and security.
ksmbd. Most popular distros neither compile it in, nor build it as a module, so you can’t load it or activate it, even by mistake.ksmbd, even if it still has a kernel version that is vulnerable in theory.COMMANDS YOU CAN USE TO CHECK YOUR EXPOSURE
Any Linux from 5.15.61 on, or any 6.x, is already patched. To check your Linux version: $ uname -o -r 6.1.1 GNU/Linux
To see if this kernel feature is compiled in, you can dump the compile-time configuration of the running kernel: $ zcat /proc/config.gz | grep SMB_SERVER # CONFIG_SMB_SERVER is not set If this compile-time configuration setting is unset, or set to "n" for no, the feature wasn't built at all. If it says "y" for yes, then the kernel SMB server is compiled right into your kernel, so ensure you have a patched version. If it says "m" for module, then the kernel build probably includes a run-time module that can be loaded on demand.
To see if your kernel has a loadable module available: $ /sbin/modprobe --show ksmbd modprobe: FATAL: Module ksmbd not found in directory /lib/modules/6.1.1 Note that "--show" means "do not actually do it, just show if loading it would actually work or not".
To see if your system has the ksmbd module already active: $ lsmod | grep ksmbd
If you see no output, the module wasn’t matched in the list.
To stop the module loading in case it ever shows up, add a file with a name such as ksmbd.conf to the directory /lib/modules.d or /etc/modules.d with this line in it: blacklist ksmbd

Infosec books | InfoSec tools | InfoSec services
Dec 05 2022
The Threat Research Unit at Qualys’ has revealed how a new Linux flaw tracked as (CVE-2022-3328), may be combined with two other, seemingly insignificant flaws to gain full root rights on a compromised system.
The Linux snap-confine function, a SUID-root program installed by default on Ubuntu, is where the vulnerability is located.
The snap-confine program is used internally by snapd to construct the execution environment for snap applications, an internal tool for confining snappy applications.
The newly discovered flaw, tracked as CVE-2022-3328, is a race condition in Snapd, a Canonical-developed tool used for the Snap software packaging and deployment system.
The issue specifically affects the ‘snap-confine’ tool that Snapd uses to build the environment in which Snap applications are executed.
“In February 2022, Qualys Threat Research Unit (TRU) published CVE-2021-44731 in our “Lemmings” advisory. The vulnerability (CVE-2022-3328) was introduced in February 2022 by the patch for CVE-2021-44731).” reads the post published by Qualys.
“The Qualys Threat Research Unit (TRU) exploited this bug in Ubuntu Server by combining it with two vulnerabilities in multipathd called Leeloo Multipath (an authorization bypass and a symlink attack, CVE-2022-41974, and CVE-2022-41973), to obtain full root privileges”.
The CVE-2022-3328 weakness was chained by the researchers to two other flaws in Multipathd, a daemon responsible for looking for failed paths. Particularly, in several distributions’ default installations, including Ubuntu, Multipathd runs as root.
The device-mapper-multipath, when used alone or in conjunction with CVE-2022-41973, enables local users to gain root access.
In this case, the access controls can be evaded and the multipath configuration can be changed by local users who have the ability to write to UNIX domain sockets.
This problem arises because using arithmetic ADD rather than bitwise OR causes a keyword to be incorrectly handled when repeated by an attacker. Local privilege escalation to root may result from this.
Together with CVE-2022-41974, the device-mapper-multipath enables local users to get root access. Further, due to improper symlink handling, local users with access to /dev/shm can modify symlinks in multipathd, which could result in controlled file writes outside of the /dev/shm directory. Hence, this could be used indirectly to elevate local privileges to the root.
Notably, any unprivileged user might get root access to a vulnerable device by chaining the Snapd vulnerability with the two Multipathd vulnerabilities.
“Qualys security researchers have verified the vulnerability, developed an exploit, and obtained full root privileges on default installations of Ubuntu,” Qualys said.
On Ubuntu default installations, Qualys security researchers have confirmed the vulnerability, developed an exploit and got full root access.
Although the vulnerability cannot be used remotely, the cybersecurity company issues a warning that it is unsafe because it can be used by an unprivileged user.

Mastering Linux Security and Hardening
#InfoSecTools and #InfoSectraining
Ask DISC an InfoSec & compliance related question
Nov 16 2022
Kali Linux is a specialized Linux distribution developed by Offensive Security, designed for experienced Linux users who need a customized platform for penetration testing.
Kali Linux also comes with several hundred specialized tools for carrying out penetration testing, security research, computer forensics, reverse engineering, vulnerability management, and red team testing. Here are 5 you should learn how to use.

Aircrack-ng is a complete suite of tools to assess Wi-Fi network security, focusing on:


John the Ripper is an open-source password security auditing and password recovery tool. Its primary purpose is to detect weak Unix passwords. Besides several crypt(3) password hash types most commonly found on various Unix flavors, supported out of the box are Kerberos/AFS and Windows LM hashes, as well as DES-based tripcodes, plus hundreds of additional hashes and ciphers in “-jumbo” versions.


Lynis performs an extensive health scan of your systems to support system hardening and compliance testing. Lynis is open-source and flexible, and used for several different purposes. Typical use cases include:


Metasploit is the world’s most used penetration testing framework. A collaboration between the open source community and Rapid7, Metasploit helps security teams do more than just verify vulnerabilities, manage security assessments, and improve security awareness; it empowers and arms defenders to always stay one step (or two) ahead of the game.
For more information about the past, present and future of Metasploit, watch our video with Spencer McIntyre, Lead Security Researcher at Rapid7.


Nmap is a free and open-source utility for network discovery and security auditing. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.


More Kali Linux content to check out:
Checkout our previous posts on Linux Security
