The recent discovery of a significant flaw in the GNU C Library (glibc), a fundamental component of major Linux distributions, has raised serious security concerns. This flaw grants attackers root access, posing a critical threat to the security of Linux systems.
- Vulnerability in GNU C Library (glibc): The GNU C Library, commonly known as glibc, is an essential part of Linux distributions. It provides the core libraries for the system, including those used for file handling, mathematical computations, and system calls.
- Root Access Granted: The flaw discovered in glibc allows attackers to gain full root access to Linux machines. Root access means having complete control over the system, enabling an attacker to perform any action, including installing software, accessing all files, and modifying system configurations.
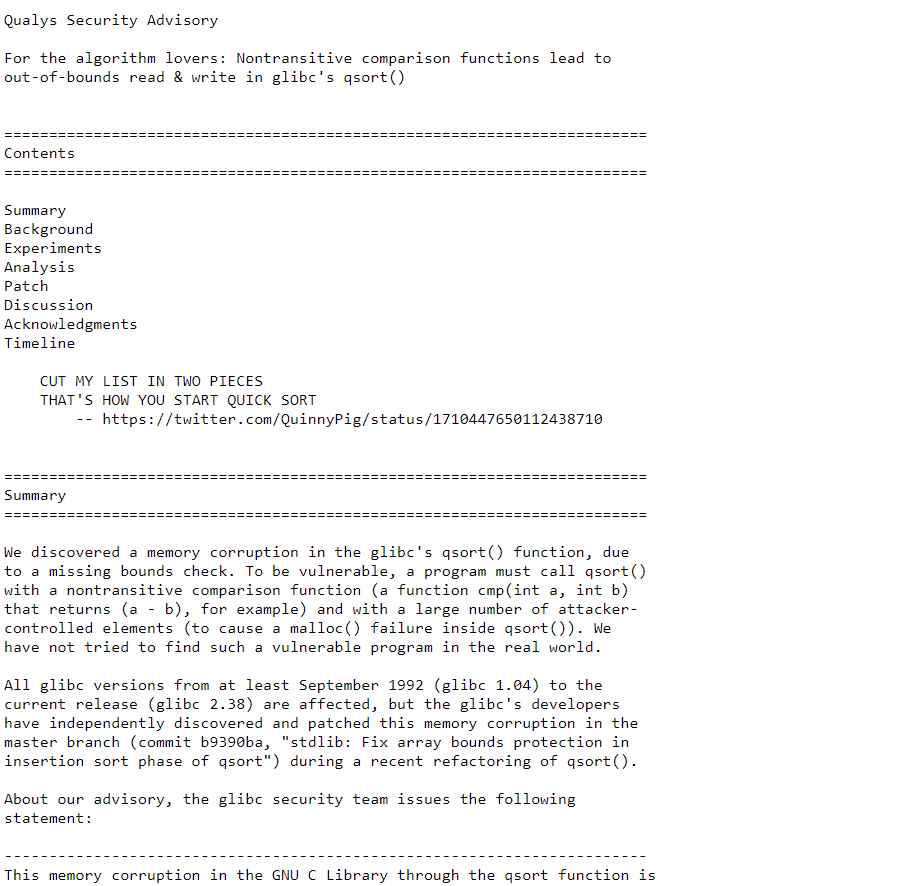
CVE ID: CVE-2023-6246
- Description: This vulnerability is related to a dynamic memory buffer overflow and is classified as a Local Privilege Escalation (LPE) issue. It was found in glibc’s
__vsyslog_internal()function, which is called by the widely-used syslog and vsyslog functions. - Impact: The flaw allows unprivileged attackers to gain root access on various major Linux distributions in their default configurations. This level of access can enable attackers to take complete control over the affected system.
- Severity: Given its potential for granting root access, this vulnerability is considered highly severe.
HOW THE FLAW WORKS
- Local Privilege Escalation: The vulnerability is a local privilege escalation (LPE) issue. This means that an attacker who already has access to the system (even with limited privileges) can exploit this flaw to gain root-level access.
- Exploitation Requirements: To exploit this flaw, attackers need a Set-User-ID (SUID) binary. SUID is a special type of file permission that allows users to execute a program with the permissions of the file owner, which in many cases is the root user.
IMPACT AND SEVERITY
- Widespread Impact: Given the ubiquitous use of glibc in Linux distributions, the impact of this vulnerability is widespread, affecting a vast number of systems and applications.
- High Severity: The flaw is considered high severity due to its potential to grant attackers complete control over the affected systems.
MITIGATION AND RESPONSE
- Disabling SUID Binaries: One suggested mitigation is to disable SUID binaries using “no new privileges” mode, which can be implemented with tools like systemd or bwrap.
- Patch and Update: Users and administrators are urged to apply patches and updates provided by their Linux distribution as soon as they become available. Staying updated is crucial in preventing the exploitation of this vulnerability.
The discovery of the glibc flaw that grants root access to major Linux distributions is a stark reminder of the importance of system security and the need for constant vigilance. Users and administrators must take immediate action to mitigate the risk by applying patches and employing security best practices. As Linux continues to be a backbone for many systems and networks, ensuring its security is paramount for the integrity of countless applications and services.

Linux Basics for Hackers: Getting Started with Networking, Scripting, and Security in Kali
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory