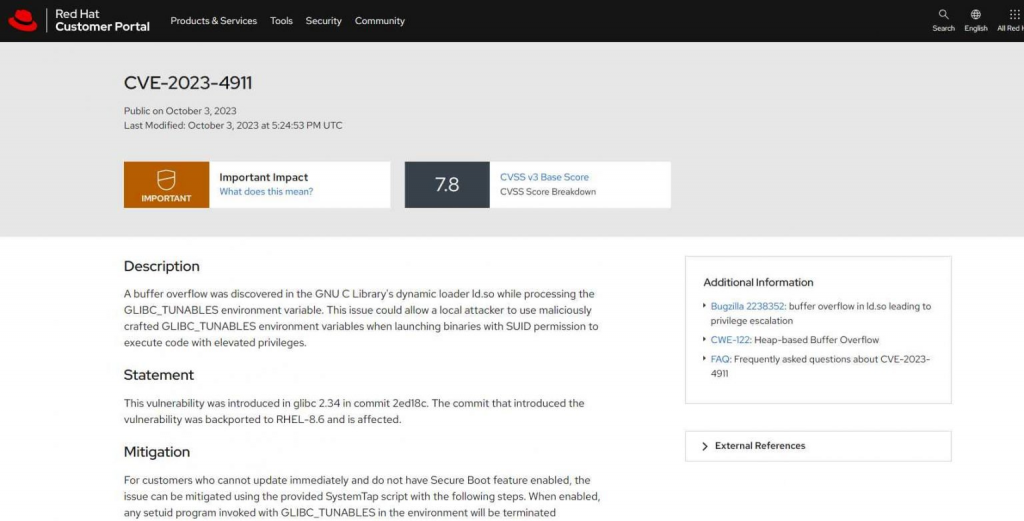
The team at Qualys Threat Research Unit has unveiled a fresh vulnerability within the Linux operating system, allowing local attackers to escalate their access level to root privileges. This escalation is made possible by exploiting a buffer overflow weakness located in the GNU C Library’s ld.so dynamic loader. Assigned the identification CVE-2023-4911 and nicknamed “Looney Tunables,” this vulnerability is recognized as high-risk with a CVSS score of 7.8, signifying its high severity.
“Looney Tunables” allows bad actors to exploit a buffer overflow within the ld.so dynamic loader of the GNU C Library (glibc). This exploitation path provides local attackers with a mechanism to elevate their privileges to root level, thereby gaining unparalleled access and control over the system. Given that root privileges allow complete control over a system, attackers can execute a variety of malicious activities, from accessing sensitive information to altering system settings and functionalities, underscoring the critical nature of this security flaw.
The GNU C Library, or glibc, is fundamentally integral to the operation of a majority of systems based on the Linux kernel. This crucial library facilitates numerous system calls, from elementary functions like open, malloc, and printf to more complex ones such as exit, serving as the operational backbone for these systems. As such, glibc plays a pivotal role in the functionality and performance of Linux-based systems, making any vulnerability within this library particularly concerning for system administrators and users alike.
Within glibc, the ld.so dynamic loader is an element of paramount importance. This component is tasked with the significant responsibility of initializing and running programs on Linux systems that rely on glibc for their operation. Its role is crucial as it ensures the smooth execution of various applications and services on a Linux system, making it an indispensable part of the operating environment. Given its central function, any vulnerability within the ld.so dynamic loader is a matter of serious concern as it could potentially compromise the security and stability of a wide range of systems.
In light of the discovery of “Looney Tunables”, it is imperative for organizations and users utilizing Linux-based systems to acknowledge and address this security vulnerability swiftly to safeguard their systems against potential exploits. Immediate mitigation steps, including the application of security patches and updates, should be undertaken to protect systems from the risks associated with this high-severity vulnerability. Users and administrators should stay vigilant and monitor any security advisories and updates issued by the Linux community and cybersecurity experts to ensure timely and effective protection against this newly identified threat.
Furthermore, it would be prudent for organizations to adopt and enforce a set of security best practices. These might include the regular updating and patching of systems, the use of reliable security solutions, conducting cybersecurity awareness and training programs for employees, and implementing network segmentation strategies. These proactive measures can significantly enhance the security posture of an organization, providing robust defense mechanisms against “Looney Tunables” and other similar security threats that might emerge in the future.
The GNU C Library’s ld.so dynamic loader was found to include the security flaw, which exposed a crack in the armor. During the processing of the ‘GLIBC_TUNABLES’ environment variable, this security hole might manifest itself. To put it more simply, a hostile attacker on the local network who has some dexterity and cunning may insert text into the ‘GLIBC_TUNABLES’ environment variable. The attacker is able to execute code with dangerously high privileges if they do this while beginning binaries that have the SUID permission.
This vulnerability was discovered by the observant members of the Qualys Threat Research Unit. According to an investigation into the origin of the vulnerability, it was first discovered in April 2021, when glibc version 2.34 was being distributed. Ironically, the commit was made with the intention of improving security by correcting the behavior of SXID_ERASE in setuid applications.
It is important to keep in mind that attackers, even those with just the most basic privileges, are able to take advantage of this severe gap. since of their simplicity and since they don’t need any input from the user, these assaults are particularly alarming.
There is a solution available for those who are unable to update their software promptly and do not have the Secure Boot capability. A SystemTap script has been made available, and once it is enabled, it will immediately stop any setuid application that has been launched with the ‘GLIBC_TUNABLES’ environment variable present. To securely call the setuid program thereafter, one just has to unset or remove the ‘GLIBC_TUNABLES’ environment variable, for instance by executing the command ‘GLIBC_TUNABLES= sudo’.
According to Saeed Abbasi, who is the Product Manager at Qualys’ Threat Research Unit, “Our successful exploitation, leading to full root privileges on major distributions like Fedora, Ubuntu, and Debian, underscores the profound and ubiquitous nature of this vulnerability.”
While the Qualys team has indicated that they will not release its exploit code at this time, the inherent simplicity of transforming the buffer overflow into a data-only assault suggests that other research teams may soon take up the challenge.
Systems that are running Debian 12 and 13, Ubuntu 22.04 and 23.04, or Fedora 37 and 38 are vulnerable to the CVE-2023-4911 flaw and should be avoided at all costs. The extent of the possible harm might be enormous due to the widespread use of the glibc library in Linux’s many different distributions. Distributions such as Alpine Linux, which use the musl libc library instead of the glibc library, are given a little bit of wiggle room.
Linux Pocket Guide: Essential Commands
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory



