Powershell Tips & Tricks – via Hadess | حادث

PowerShell Pocket Reference: Portable Help for PowerShell Scripters

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Dec 09 2023
Powershell Tips & Tricks – via Hadess | حادث

PowerShell Pocket Reference: Portable Help for PowerShell Scripters

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Sep 11 2023
Cybercriminals Using PowerShell to Steal NTLMv2 Hashes from Compromised Windows
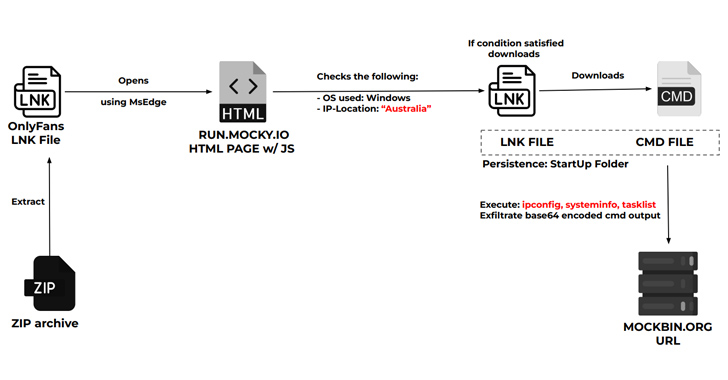
A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red teaming tool to plunder NTLMv2 hashes from compromised Windows systems primarily located in Australia, Poland, and Belgium.
The activity has been codenamed Steal-It by Zscaler ThreatLabz.
“In this campaign, the threat actors steal and exfiltrate NTLMv2 hashes using customized versions of Nishang’s Start-CaptureServer PowerShell script, executing various system commands, and exfiltrating the retrieved data via Mockbin APIs,” security researchers Niraj Shivtarkar and Avinash Kumar said.
Nishang is a framework and collection of PowerShell scripts and payloads for offensive security, penetration testing, and red teaming.
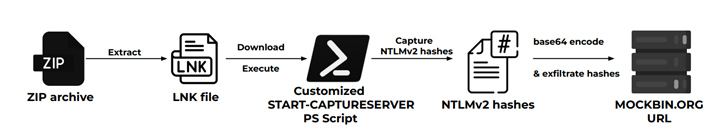
The attacks leverage as many as five different infection chains, although they all leverage phishing emails containing ZIP archives as the starting point to infiltrate specific targets using geofencing techniques –
It’s worth noting that the last attack sequence was highlighted by the Computer Emergency Response Team of Ukraine (CERT-UA) in May 2023 as part of an APT28 campaign directed against government institutions in the country.
This raises the possibility that the Steal-It campaign could also be the work of the Russian state-sponsored threat actor.
“The threat actors’ custom PowerShell scripts and strategic use of LNK files within ZIP archives highlights their technical expertise,” the researchers said. “The persistence maintained by moving files from the Downloads to Startup folder and renaming them underscores the threat actors’ dedication to prolonged access.”
Learn PowerShell in a Month of Lunches, Fourth Edition: Covers Windows, Linux, and macOS
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Jan 17 2023
Jan 02 2023
Aug 17 2021
An authenticated attacker could execute arbitrary commands as the root user on the underlying system via the SAML server configuration page. Experts pointed out that the flaw could be chained with an authentication bypass flaw that could allow an attacker
The vulnerability impacts Fortinet FortiWeb versions 6.3.11 and earlier, an authenticated attacker could exploit the issue to take complete control of servers running vulnerable versions of the FortiWeb WAF.
An authenticated attacker could execute arbitrary commands as the root user on the underlying system via the SAML server configuration page. Experts pointed out that the flaw could be chained with an authentication bypass flaw (i.e. CVE-2020-29015) to allow an unauthenticated attacker to trigger the vulnerability.
The vulnerability was reported by the researcher William Vu from Rapid7.
“An attacker, who is first authenticated to the management interface of the FortiWeb device, can smuggle commands using backticks in the “Name” field of the SAML Server configuration page. These commands are then executed as the root user of the underlying operating system.” reads the post published by Rapid7. “An attacker can leverage this vulnerability to take complete control of the affected device, with the highest possible privileges. “
The flaw could allow an attacker to deploy a persistent shell, install crypto mining software, or other malware families. If the management interface is exposed to the internet, an attacker could trigger the issue to reach into the affected network beyond the DMZ. Rapid7 researchers discovered less than three hundred devices exposing their management interfaces online. Let’s remind that management interfaces for devices like FortiWeb should not be exposed online!
![OWASP WEB APPLICATION SECURITY THREATS – MARKET INTEREST TREND : FULL REPORT PACKAGE by [CURIOSITY PUBLISHERS]](https://m.media-amazon.com/images/I/41MW20-YgdL.jpg)
May 14 2021
Magecart hackers are distributing malicious PHP web shells hidden in website favicon to inject JavaScript e-skimmers into online stores and steal payment information.
Researchers from Malwarebytes observed threat actors, likely Magecart Group 12, using this technique in attacks aimed at online stores running on Magento 1 websites.
The web shells employed in the attacks are tracked as Smilodon or Megalodon, they dynamically load JavaScript skimming code via server-side requests into online stores. This technique allows bypassing most client-side security tools.
“While performing a crawl of Magento 1 websites, we detected a new piece of malware disguised as a favicon. The file named Magento.png attempts to pass itself as ‘image/png’ but does not have the proper PNG format for a valid image file.” reads the analysis published by Malwarebytes.
Feb 12 2021
Jul 05 2019
PowerShell is a valuable tool for automating Windows administration tasks, including laborious security chores
Source: 10 essential PowerShell security scripts for Windows administrators
Defending Against PowerShell Attacks