
The Practical Linux Handbook: A Beginner’s Guide to Mastering Everyday Tasks
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot
Jul 25 2024
Apr 29 2024
Microsoft released multiple product security patches on their April 2024 Patch Tuesday updates.
One of the vulnerabilities addressed was CVE-2024-26218, associated with the Windows Kernel Privilege Escalation vulnerability, which had a severity of 7.8 (High).
This vulnerability relates to a TOCTOU (Time-of-Check Time-of-Use)Race Condition that could be exploited.
Successful exploitation of this vulnerability could allow a threat actor to gain SYSTEM privileges.
This vulnerability existed in multiple versions of Windows 10, Windows 11, and Windows Server (2019, 2022).
However, Microsoft has patched this vulnerability, and users are advised to update their Operating Systems accordingly.
A proof of concept for this vulnerability has been published in GitHub which consists of a DEF file, a EXP file, a LIB file and an SLN file.
Additionally, another folder was found on the repository, which had a C file, a VCXPROJ file, and a VCXPROJ filters file.
On investigating further, an explanation of this vulnerability was provided by the researcher who discovered this proof of concept.
The explanation suggests that this vulnerability exists due to a double fetch performed by the PspBuildCreateProcessContext function in Windows.
When creating a process, multiple attributes are created and provided to NtCreateUserProcess syscall via PS_ATTRIBUTE_LIST, an array of PS_ATTRIBUTE structures.
This list of attributes will reside in the user mode memory which are then processed by the PspBuildCreateProcessContext function.
As a matter of fact, this function contains a large number of scenarios for handling every attribute type it processes.
On looking deep into it, it was discovered that this PspBuildCreateProcessContext function performs a double-fetch of the Size field when handling the PsAttributeMitigationOptions and PsAttributeMitigationAuditOptions attribute types.
This is where the race condition exists in which the value of the Size field can be changed between the fetches that could potentially result in a stack buffer overflow.
Though this vulnerability has a proof of concept code in GitHub, there is no explanation of exploitation provided.
.webp)
.webp)
| Product | Fixed in Build Number |
| Windows 10 Version 22H2 for 32-bit Systems | 10.0.19045.4291 |
| Windows 10 Version 22H2 for ARM64-based Systems | 10.0.19045.4291 |
| Windows 10 Version 22H2 for x64-based Systems | 10.0.19045.4291 |
| Windows Server 2022, 23H2 Edition (Server Core installation) | 10.0.25398.830 |
| Windows 11 Version 23H2 for x64-based Systems | 10.0.22631.3447 |
| Windows 11 Version 23H2 for ARM64-based Systems | 10.0.22631.3447 |
| Windows 11 Version 22H2 for x64-based Systems | 10.0.22621.3447 |
| Windows 11 Version 22H2 for ARM64-based Systems | 10.0.22621.3447 |
| Windows 10 Version 21H2 for x64-based Systems | 10.0.19044.4291 |
| Windows 10 Version 21H2 for ARM64-based Systems | 10.0.19044.4291 |
| Windows 10 Version 21H2 for 32-bit Systems | 10.0.19044.4291 |
| Windows 11 version 21H2 for ARM64-based Systems | 10.0.22000.2899 |
| Windows 11 version 21H2 for x64-based Systems | 10.0.22000.2899 |
| Windows Server 2022 (Server Core installation) | 10.0.20348.2402 |
| Windows Server 2022 | 10.0.20348.2402 |
| Windows Server 2019 (Server Core installation) | 10.0.17763.5696 |
| Windows Server 2019 | 10.0.17763.5696 |
| Windows 10 Version 1809 for ARM64-based Systems | 10.0.17763.5696 |
| Windows 10 Version 1809 for x64-based Systems | 10.0.17763.5696 |
| Windows 10 Version 1809 for 32-bit Systems | 10.0.17763.5696 |
It is recommended that users of these vulnerable versions upgrade to the latest versions to prevent threat actors from exploiting this vulnerability.
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot
Dec 18 2023
The 8220 hacker group, which was first identified in 2017 by Cisco Talos, is exploiting both Windows and Linux web servers with crypto-jacking malware. One of their recent activities involved the exploitation of Oracle WebLogic vulnerability (CVE-2017-3506) and Log4Shell (CVE-2021-44228).
However, the history of this threat group had several exploited vulnerabilities such as Confluence, Log4j, Drupal, Hadoop YARN, and Apache Struts2 applications. Their TTPs are evolved with different publicly released exploits.
In addition to this, the group was also discovered to be exploiting (CVE-2020-14883), a Remote code execution vulnerability in Oracle WebLogic Server. This exploitation chain is combined with another authentication bypass vulnerability (CVE-2020-14882) in the Oracle WebLogic server.
The exploitation methods of these two vulnerabilities are publicly available, making it relatively easy for the threat actor to modify and exploit them for malicious purposes.
Two different exploit chains were discovered, and one of them enables the loading of an XML file used for further phases of execution of commands on the OS, whereas the other one executes Java code without the use of an XML file.
The first infection chain uses different XML files that depend on the target OS. In the case of Linux, the downloading of other files is performed via cURL, wget, lwp-download, and python urllib along with a custom bash function that encodes it to base64.
The method injects a Java code which also initially evaluates the OS and executes the same command strings executed in the first method. Once the download and execution process takes place, the compromised hosts are infected with AgentTesla, rhajk, and nasqa malware variants.
A complete report has been published, which provides detailed information about the exploitation, command used, encoding, and other information.
URL
Source IPs
Common Windows, Linux and Web Server Systems Hacking Techniques

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Sep 13 2023
Threat actors were using Windows Arbitrary File Deletion to perform Denial-of-service attacks on systems affected by this vulnerability. However, recent reports indicate that this Windows Arbitrary file deletion can be used for a full compromise.
The possibility of this attack depends on the CVE-2023-27470 arbitrary file deletion vulnerability combining it with a Time-of-Check to Time-of-Use (TOCTOU) race condition, which enables the deletion of files on a Windows system and subsequently creates an elevated Command Prompt.
CVE-2023-27470 affects N-Able’s Take Control Agent, which can lead to an arbitrary file deletion vulnerability. This vulnerability analysis was done using Microsoft’s Process Monitor, often called ProcMon.
This vulnerability exists due to insecure file operations conducted by NT AUTHORITY\SYSTEM processes that were detected with the help of ProcMon filters.
The process that was analyzed during this vulnerability was BASupSrvcUpdater.exe, belonging to Take Control Agent 7.0.41.1141.
BASupSrvcUpdater.exe attempts every 30 seconds to a non-existent folder under the C:\ProgramData\GetSupportService_N-Central\PushUpdates as an NT AUTHORITY\SYSTEM process. For further research, this PushUpdates folder and a dummy file aaa.txt were created.
BASupSrvcUpdater.exe made an attempt to read the contents of the folder and performed a deletion, which was logged in the C:\ProgramData\GetSupportService_N-Central\Logs\BASupSrvcUpdater_[DATE].log log file.
This particular action gives rise to a race condition, as a threat actor can exploit this condition by utilizing the timeframe between the deletion and logging.
To exploit this condition and perform a full system compromise, an attacker must replace a file in the PushUpdates folder with a pseudo-symlink.
A complete report about this attack has been published, which provides detailed information about the exploitation, techniques, process, and method of complete system compromise.
To prevent this attack, it is recommended for organizations using N-able to upgrade to version 7.0.43 to fix this vulnerability.

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Jul 14 2023
The Blacklotus bootkit was developed expressly for Windows, and it first appeared on hacker forums in October of the previous year. It was described as having APT-level capabilities, including the ability to circumvent secure boot and user access control (UAC), as well as the capacity to deactivate security software and defensive mechanisms on victim computers. Threat actors of various skill levels were able to purchase BlackLotus when it was first offered for sale on hacker forums for as little as $5,000, giving them access to malware that is often associated with state-sponsored hacking operations. However, the threat actor concealed the source code and charged clients $200 for rebuilds if they wished to modify the bootkit in any way.c
Microsoft published a set of resources in April that are intended to assist threat hunters in recognizing BlackLotus infections. The National Security Agency (NSA) released some guidelines in June to assist firms in strengthening their defenses against the threat.
Although it has a number of alterations in comparison to the malware’s initial form, the BlackLotus UEFI bootkit’s original source code has been made available to the public on GitHub.
The ‘Baton Drop’ exploit that targets CVE-2022-21894 has been removed from the BlackLotus source code that was released on GitHub on Wednesday. Additionally, the BlackLotus source code now employs the bootlicker UEFI firmware rootkit, although it still retains the majority of the original code.
The fact that the bootkit’s source code is available to the public poses a considerable danger, primarily because it may be paired with newly discovered vulnerabilities to open up previously undiscovered entry points for attacks. BlackLotus was able to utilize the attack despite the fact that CVE-2022-21894 had been fixed the previous year. This was possible because the vulnerable binaries had not been put to the UEFI revocation list. This demonstrates how even vulnerabilities that have been patched may still present long-term, industry-wide supply chain impact.
However, since the source code was leaked, it is now very easy for threat actors to combine the bootkit with new bootloader vulnerabilities, whether they are known or undiscovered. The methods used by the bootkit are no longer cutting edge.
Be careful to adhere to the extensive mitigation guidance that the NSA issued a month ago in order to protect your computers against the BlackLotus UEFI bootkit attack.
Because the source code of the bootkit is now freely accessible, it is feasible that skilled malware writers may design more powerful variations that are able to circumvent both currently available countermeasures and those that will be developed in the future.
How to Hack Like a Legend: Breaking Windows
InfoSec tools | InfoSec services | InfoSec books
Jun 24 2023
Exploitation, Detection, and Mitigation Strategies
The Complete Active Directory Security Handbook – by Picus Security
Download pdf

InfoSec tools | InfoSec services | InfoSec books
Mar 07 2023
Cyber Security operations center is protecting organizations and the sensitive business data of customers. It ensures active monitoring of valuable assets of the business with visibility, alerting and investigating threats, and a holistic approach to managing risk.
Analytics service can be an in-house or managed security service. Collecting event logs and analyzing logs with real-world attacks is the heart of the security operation center.
Events are generated by systems that are error codes, devices generate events with success or failure to their normal function. so event logging plays an important role to detect threats. In the organization, there are multiple numbers and flavors of Windows, Linux, firewalls, IDS, IPS, Proxy, Netflow, ODBC, AWS, Vmware, etc.
These devices usually track attackers’ footprints as logs and forward them to SIEM tools for analysis. In this article, will see how events are pushed to the log collector. To know more about windows events or event ids refer Here.

It’s a centralized server to receive logs from any device. Here I have deployed Snare Agent on Windows 10 machine. So we will collect windows event logs and Detect attacks on windows 10 machines attacks using Snare Agent.
The snare is SIEM(SECURITY INCIDENT AND EVENT MANAGEMENT) Solution for log collector and event analyzer in various operating systems Windows, Linux, OSX Apple, and supports database agent MSSQL events generated by Microsoft SQL Server. It supports both Enterprise and Opensource Agents.









NOTE: Logs can be sent to a centralized server, then the centralized server push logs to SIEM (To reduce the load in SIEM this method is used), send snare logs directly to SIEM (If your SIEM is capable of good storage for a long and short-term log retention this method can be deployed), It recommended to configure your SIEM with port details of snare and test connection should be the successor to collect logs.










NOTE: Above figures shows failed attempts followed by a successful login.
Correlation Rule : failed password attempts + Followed by successful Login = Brute-force (Incident)
Now your customer environment is ready for Known use case(Brute-force detected), you can also build or write your own use case and deploy in your SIEM to detect sophisticated cyber-attacks !!!
Previous posts on Security Logs
Mar 05 2023
ESET researchers have published the first analysis of a UEFI bootkit capable of circumventing UEFI Secure Boot, a critical platform security feature. The functionality of the bootkit and its features make researchers believe that it is a threat known as BlackLotus.

This UEFI bootkit has been sold on hacking forums for $5,000 since at least October 2022. IT can run even on fully up-to-date Windows 11 systems with UEFI Secure Boot enabled.
“Our investigation started with a few hits on what turned out to be (with a high level of confidence) the BlackLotus user-mode component — an HTTP downloader — in our telemetry late in 2022. After an initial assessment, code patterns found in the samples brought us to the discovery of six BlackLotus installers. This allowed us to explore the whole execution chain and to realize that what we were dealing with here is not just regular malware,” says Martin Smolár, the ESET researcher who led the investigation into the bootkit.
The bootkit exploits a more than one-year-old vulnerability (CVE-2022-21894) to bypass UEFI Secure Boot and set up persistence for the bootkit. This is the first publicly known, in-the-wild abuse of this vulnerability. Although the vulnerability was fixed in Microsoft’s January 2022 update, its exploitation is still possible as the affected, validly signed binaries have still not been added to the UEFI revocation list. BlackLotus takes advantage of this, bringing its own copies of legitimate — but vulnerable — binaries to the system in order to exploit the vulnerability.
BlackLotus can disable operating system security mechanisms such as BitLocker, HVCI, and Windows Defender. Once installed, the bootkit’s main goal is to deploy a kernel driver (which, among other things, protects the bootkit from removal) and an HTTP downloader responsible for communication with the Command and Control server and capable of loading additional user-mode or kernel-mode payloads. Interestingly, some of the BlackLotus installers ESET has analyzed do not proceed with bootkit installation if the compromised host uses locales from Armenia, Belarus, Kazakhstan, Moldova, Russia, or Ukraine.
BlackLotus has been advertised and sold on underground forums since at least early October 2022. “We can now present evidence that the bootkit is real, and the advertisement is not merely a scam,” says Smolár. “The low number of BlackLotus samples we have been able to obtain, both from public sources and our telemetry, leads us to believe that not many threat actors have started using it yet. We are concerned that things will change rapidly should this bootkit get into the hands of crimeware groups, based on the bootkit’s easy deployment and crimeware groups’ capabilities for spreading malware using their botnets.”
Many critical vulnerabilities affecting the security of UEFI systems have been discovered in the past few years. Unfortunately, due to the complexity of the whole UEFI ecosystem and related supply-chain problems, many of these vulnerabilities have left systems vulnerable even a long time after the vulnerabilities have been fixed, or at least since we were told they had been fixed.
UEFI bootkits are very powerful threats, having full control over the operating system boot process and thus being capable of disabling various operating system security mechanisms and deploying their own kernel-mode or user-mode payloads in early boot stages. This allows them to operate very stealthily and with high privileges. So far, only a few have been discovered in the wild and publicly described.
UEFI bootkits may lose on stealthiness when compared to firmware implants — such as LoJax, the first in-the-wild UEFI firmware implant, discovered by ESET Research in 2018 — as bootkits are located on an easily accessible FAT32 disk partition. However, running as a bootloader gives them almost the same capabilities, without having to overcome multiple layers of security features protecting against firmware implants.
“The best advice, of course, is to keep your system and its security product up to date to raise the chance that a threat will be stopped right at the beginning, before it’s able to achieve pre-OS persistence,” concludes Smolár.
ESET researchers offer the following advice:
Feb 20 2023
This article covers Active directory penetration testing that can help for penetration testers and security experts who want to secure their network.
“Active Directory Pentesting” Called as “AD penetration Testing” is a directory service that Microsoft developed for the Windows domain network. Using it you can to control domain computers and services that are running on every node of your domain.
Also Read: Active Directory Kill Chain Attack & Defense Guide
In this section, we have some levels, the first level is a reconnaissance of your network. every user can enter a domain by having an account in the domain controller (DC).
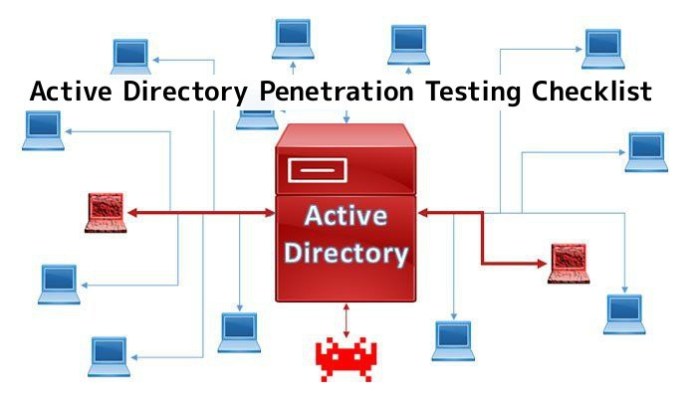
All this information is just gathered by the user that is an AD user. In the username, there are two parts the first is the domain name and the second part is your username. like below :
+ c:\ > net user
By running this command in CMD (Command Prompt) you can easily see local users on your PC.
+ c:\ >whoami
This command can help you to see the current user associated with Active Directory logged in.
+ c:\ >whoami /groups
This command helps you to show you the current group
+ c:\ > net user \domain
This command shows you all users from any group in the active directory.
also, you can see every user’s group by running this command :
+ c:\ > net user [username] domain.
To have a better look, you can user “AD Recon” script. AD Recon is a script written by “Sense of Security“.
It uses about 12 thousand lines of PowerShell script that gives you a good look to AD and all info that you will need it.
You can download this script from GitHub: https://github.com/sense-of-security/ADRecon screenshots of the report of this app:

Picture2 – List of AD GroupsPicture3 – List of DNS Record Zones
When you get all AD users, now you should take a look at the group policy. The group policy is a feature of Microsoft Windows NT family of operating systems that controls the working environment of user accounts and computer accounts. in the group policy, you can see environment policy such as”Account Lockout Policy“.
It is a method that provides you networks users to be secure from password-guessing attacks. Also, you can see “Password Policy“. A password policy is a set of rules designed to enhance computer security by encouraging users to employ strong passwords and use them properly.
When you get all the data that you need, now you can execute different attacks on users like :
To brute force attack on active directory, you can use Metasploit Framework auxiliaries. You can use below auxiliary:
msf > use auxiliary/scanner/smb/smb_login
The options of this auxiliary you can set username file and password file. and set an IP that has SMB service open.
then you can run this auxiliary by entering “run” command.
If you try false passwords more than Account Lockout Policy, you can see this message “Account Has Been Locked out“.
If you try it on all accounts, all users will be disabled and you can see disorder in the network. As you can see in Password Policy, you can set your password list to brute-force.
All hashes are stored in a file named “NTDS.dit” in this location :
C:\Windows\NTDS
You will extract hashes from this file by using mimikatz. mimikatz has a feature which utilities the Directory Replication Service (DRS) to retrieve the password hashes from NTDS.DIT file. you can run it as you can see below :
mimikatz # lsadump::dcsync /domain:pentestlab.local /all /csv
Then you can see hashes and password (if the password can be found).
The active directory includes several services that run on Windows servers, it includes user groups, applications, printers, and other resources.
It helps server administrators to manage devices connected with the network and it includes a number of services such as Domain, Certificate Services, Lightweight Directory Services, Directory Federation and rights management.
Active directory penetration testing is required for any organization, nowadays APT groups actively targeting Active Directories using different techniques.
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Jan 28 2023
PlugX malware has been around for almost a decade and has been used by multiple actors of Chinese nexus and several other cybercrime groups.
The Palo Alto Networks Unit 42 incident response team has discovered a new variant of PlugX malware that is distributed via removable USB devices and targets Windows PCs. This should not come as a surprise since 95.6% of new malware or their variants in 2022 targeted Windows.
According to Unit 42 researchers, the new variant was detected when carrying out an incident response post a Black Basta ransomware attack. The researchers uncovered several malware samples and tools on the victims’ devices. This includes the Brute Ratel C4 red-teaming tool, GootLoader malware, and an old PlugX sample.
PlugX malware has been around for almost a decade and has been used by multiple actors of Chinese nexus and several other cybercrime groups. The malware was previously used in many high-profile cyberattacks, such as the 2015 U.S. Government Office of Personnel Management (OPM) breach.
The same backdoor was also used in the 2018 malware attack on the Android devices of minority groups in China. Most recently, in November 2022, researchers linked Google Drive phishing scams to the group infamously known for using PlugX malware.
The new variant stood out among other malware because it could infect any attached removable USB device, e.g., floppy, flash, thumb drives, and any system the removable device was plugged into later.
So far, no evidence connects the PlugX backdoor or Gootkit to the Black Basta ransomware group, and researchers believe another actor could have deployed it. Moreover, researchers noted that the malware could copy all Adobe PDF and Microsoft Word documents from the host and places them in a hidden folder on the USB device. The malware itself creates this folder.

Unit 42 researchers Jen Miller-Osborn and Mike Harbison explained in their blog post that this variant of PlugX malware is a wormable, second-stage implant. It infects USB devices and stays concealed from the Windows operating file system. The user would not suspect that their USB device is being exploited to exfiltrate data from networks.
PlugX’s USB variant is different because it uses a specific Unicode character called non-breaking space/ U+00A0 to hide files in a USB device plugged into a workstation. This character prevents the Windows OS from rendering the directory name instead of leaving an anonymous folder in Explorer.
Furthermore, the malware can hide actor files in a removable USB device through a novel technique, which even works on the latest Windows OS.
The malware is designed to infect the host and copy the malicious code on any removable device connected to the host by hiding it in a recycle bin folder. Since MS Windows OS by default doesn’t show hidden files, the malicious files in recycle bin aren’t displayed, but, surprisingly, it isn’t shown even with the settings enabled. These malicious files can be viewed/downloaded only on a Unix-like OS or through mounting the USB device in a forensic tool.
InfoSec books | InfoSec tools | InfoSec services
Jan 23 2023
Jan 22 2023
Recent Windows 11 Insider builds include support for ReFS, the Resilient File System. The file system is currently only available in Windows server operating systems, but not in client systems.
Resilient File System is designed to “maximize data availability, scale efficiently to large data sets across diverse workloads, and provide data integrity with resiliency to corruption” according to Microsoft.
NTFS, the New Technology File System, is the default file system on client versions of Microsoft’s Windows operating system. It is a proprietary file system introduced in Windows NT 3.1 and also supported on Linux and BSD.
ReFS and NTFS support a wide range of features, but there are major differences between the two file systems as well.
The Resilient File System, for example, supports file and volume sizes of up to 35 petabytes. NTFS, on the other hand, supports a maximum of 256 terabytes. A petabyte equals 1024 terabytes. While most home systems are very far away from reaching these file and volume sizes, it is clear that the 256 terabyte limit will be reached eventually.
ReFS supports the following features exclusively (compared to NTFS):
ReFS lacks support for several important features that NTFS supports. Major features that are missing include file system compression and encryption support, support for disk quotas and removable media, or booting.
ReFS support adds a new option to the Windows 11 operating system. It is possible that the file system will only be supported in Enterprise, Education and Workstation editions of Windows 11. On the other hand, a Pro version of Windows 11 was used by the Twitter user who revealed the support information.
Another aspect that needs to be considered is that there is no direct NTFS to ReFS conversion; this makes it very likely that ReFS can only be selected during initial setup of the operating system, but not while it is running.
Windows 11 administrators may enable ReFS on Windows 11 Insider builds using ViVeTool and the ID42189933. It is recommended to create a full system backup before attempting to install Windows 11 on ReFS.
Jan 12 2023
During the month of November, researchers at the cybersecurity firm LookingGlass examined the most significant vulnerabilities in the financial services industry in the United States.
The company looked at assets with public internet-facing assets from more than 7 million IP addresses in the industry and discovered that a seven-year-old Remote Code Execution vulnerability affecting Microsoft Windows was at the top of the list.
According to CISA, the “Financial Services Sector includes thousands of depository institutions, providers of investment products, insurance companies, other credit and financing organizations, and the providers of the critical financial utilities and services that support these functions.”
Reports stated that the industry employs about 8 million Americans and contributes $1.5 trillion, or 7.4% of the nation’s overall GDP.
Over 900 times in the financial sector have been affected by a critical remote code execution vulnerability identified as (CVE-2015-1635), affecting Microsoft Windows and it has been around for seven years.
If this vulnerability is exploited successfully, a remote attacker may execute arbitrary code with system privileges and result in a buffer overflow.
The next most often exploited vulnerability was (CVE-2021-31206), which affects Microsoft Exchange Servers. Reports say in the month of November, this vulnerability was exploited 700 times in the financial services industry in the United States.
“Our data holdings attribute roughly 7 million of these to the U.S. financial services sector, which includes insurance companies, rental & leasing companies, and creditors, among other subsectors”, explains LookingGlass researchers.
According to recent reports from the U.S. Department of Treasury, ransomware attacks alone cost U.S. financial institutions close to $1.2 billion in 2021, a nearly 200% increase from the year before.
The Financial Crimes Enforcement Network (FCEN) of the Treasury identified Russia as the main source of numerous ransomware variants hitting the industry in its study.
Joint Cybersecurity Advisory: Compromise of Microsoft Exchange Server
Dec 31 2022
Dec 29 2022

https://ethicalhackersacademy.com/blogs/ethical-hackers-academy/active-directory
Active Directory is a Microsoft service run in the Server that predominantly used to manage various permission and resources around the network, also it performs an authenticates and authorizes all users and computers in a Windows domain type networks.
Recent cyber-attacks are frequently targeting the vulnerable active directory services used in enterprise networks where the organization handling the 1000’s of computers in the single point of control called “Domain controller” which is one of the main targeted services by the APT Hackers.
Though exploiting Active directory is a challenging task, It is certain to activate directory exploitation Cheat Sheet which contains common enumeration and attack methods which including the several following phases to make it simple.
Recon Phase contains various modules, including Port scan that performs the following operations.
Import-Module Invoke-Portscan.ps1 <# Invoke-Portscan -Hosts "websrv.domain.local,wsus.domain.local,apps.domain.local" -TopPorts 50 echo websrv.domain.local | Invoke-Portscan -oG test.gnmap -f -ports "80,443,8080" Invoke-Portscan -Hosts 172.16.0.0/24 -T 4 -TopPorts 25 -oA localnet #>
The secret to being able to run AD enumeration commands from the AD Powershell module on a system without RSAT installed, is the DLL located in C:\Windows\Microsoft.NET\assembly\GAC_64\Microsoft.ActiveDirectory.Management on a system that has the RSAT installed.
Set up your AD VM, install RSAT, extract the dll and drop it to the target system used to enumerate the active directory.
Import-Module .\Microsoft.ActiveDirectory.Management.dll Get-Command get-adcom*
Get-NetDomain (PowerView) Get-ADDomain (ActiveDirectory Module)
Get-NetDomain -Domain domain.local Get-ADDomain -Identity domain.local
Get-DomainSID (Get-ADDomain).DomainSID
Get-DomainPolicy (Get-DomainPolicy)."system access"
(Get-DomainPolicy -domain domain.local)."system access"
Get-NetDomainController Get-ADDomainController
Get-NetDomainController -Domain domain.local Get-ADDomainController -DomainName domain.local -Discover NETUSER More on: To Get a list of users in the current domain Infosec books | InfoSec tools | InfoSec services
Dec 22 2022
OPINION: With every Windows release, Microsoft promises better security. And, sometimes, it makes improvements. But then, well then, we see truly ancient security holes show up yet again.

For longer than some of you have been alive, I’ve been preaching the gospel of using more secure desktop operating systems. You see, Windows has been insecure since 1985’s Windows 1.0, really an MS-DOS extension, rolled out the door. Then, as now, there were more secure options. Then it was Unix desktop operating systems. Today it’s Linux desktops.
Why hasn’t Microsoft ever gotten its security act together? The fundamental problem is that Windows was never, ever meant to work on a network. It worked as a standalone PC operating system. And, even today, 37 years later, the same pre-internet problems keep showing up. Unix and Linux started with the premise that there’s more than one user on the system, and you need to secure accounts and programs from other users, local or remote. This has served these operating systems well.
In addition, the developers from Redmond may say they rewrite Windows code from the bottom up to make it more secure. But, they don’t.
Take, for example, Microsoft recently patched zero-day remote code execution Windows Scripting Languages Remote Code Execution Vulnerability, CVE-2022-41128, With a Common Vulnerability Scoring System (CVSS) rating of 8.8, it’s a baddie. This is a Windows JavaScript scripting language security hole. Specifically, it’s a hole in Internet Explorer (IE) 11’s JScript9 JavaScript engine.
Also: Hackers are still finding — and using — flaws in Internet Explorer
It’s a nasty one. It affects every version of currently supported Windows. That includes everything from Windows 8.1 to all the various Windows Servers and Windows 11. Since it showed up, North Korean hackers exploited it to infect South Korean users with malware.
It works by presenting the victims with a malicious document. When an innocent opens the document, it then downloads a rich text file (RTF) remote template. The HTML inside would then be rendered by the IE engine. Then — ta-da! — you’ve got a case of some malware or the other.
The Google Threat Analysis Group (TAG) that found it said, “This technique has been widely used to distribute IE exploits via Office files since 2017. Delivering IE exploits via this vector has the advantage of not requiring the target to use Internet Explorer as its default browser.”
Oh, guys, it is so, so much older than that. I described this kind of problem in the long-defunct magazine PC Sources in 1992 when I found it in Windows for WorkGroup 3.1. Then, as now, Windows and its native programs treated document data as programming instructions.
That’s why according to Atlas VPN, “Microsoft Office remains the most widely exploited software for malware delivery.” How bad is it? Try 78.5% of all attacks. Office on your PC, Office 365, it doesn’t matter. They’re all open to attacks.
Now, then, what’s the elephant in the room I haven’t mentioned yet? It’s that IE retired back in June 2022. It’s been replaced by Microsoft Edge.
So, why the heck are all versions of Windows vulnerable to an IE attack in late 2022? Isn’t it history? I mean, IE was never in Windows 11, anyway. You’d like to think that, but no matter what version of Windows you’re using, the IE engine is still in Windows and still ready to run JavaScript attacks.
Windows’s fundamental security flaws have never been fixed. They never will be. Backward compatibility is far more important to Microsoft than security. So, the company continues to play patch a hole.
If, like me, you favor security over backward compatibility, you’ll run Linux. Despite what you’ve heard, Linux is not that hard to use. But, if you’d rather not go to the effort, just buy a Chromebook. Anyone can use a Chromebook, and, since it’s based on Linux, it’s a lot more secure.
Infosec books | InfoSec tools | InfoSec services
Dec 21 2022
It has recently been discovered by researchers that Windows has a vulnerability that allows code execution that rivals EternalBlue in terms of potential. It is possible for an attacker to execute malicious code without authentication by exploiting this newly-tracked vulnerability CVE-2022-37958.
It is possible to exploit this vulnerability in a wormable way, which can lead to a chain reaction that can impact other systems that are vulnerable, and a new attack can be launched.
A greater range of network protocols is affected by this vulnerability as opposed to the earlier version, which gave attackers more flexibility.
Successful exploitation of this vulnerability allows any Windows application protocol that accesses the NEGOEX protocol may enable an attacker to remotely execute arbitrary code.
Despite the list of protocols that have been identified, there could be other protocols and standards that are affected as well.
On a target system, there is no user input or authentication required by a victim in order for this vulnerability to succeed. This vulnerability has been classified by Microsoft as “Critical,” with a maximum severity for all categories.
As a result, CVSS 3.1 now has an overall score of 8.1 out of 10. It is important to note that systems with unpatched default configurations are vulnerable to this flaw.
The reclassification was performed by X-Force Red in accordance with its responsible disclosure policy with Microsoft.
For the time being, IBM won’t release the full technical details regarding the vulnerabilities and patches until Q2 2023, in order to give defenders a chance and enough time to apply them.
Security Intelligence recommends that users and administrators apply the patch as soon as possible due to the widespread use of SPNEGO, which ensures that they are protected.
All systems running Windows 7 and newer are compatible with this fix, which is part of the security updates for September 2022.
Moreover, X-Force Red recommends the following additional recommendations:-

Infosec books | InfoSec tools | InfoSec services
Dec 16 2022
Microsoft revised the severity rate for the CVE-2022-37958 vulnerability, the IT giant now rated it as “critical” because it discovered that threat actors can exploit the bug to achieve remote code execution.
The CVE-2022-37958 was originally classified as an information disclosure vulnerability that impacts the SPNEGO Extended Negotiation (NEGOEX) security mechanism.
The SPNEGO Extended Negotiation Security Mechanism (NEGOEX) extends Simple and Protected GSS-API Negotiation Mechanism (SPNEGO) described in [RFC4178].
The SPNEGO Extended Negotiation (NEGOEX) Security Mechanism allows a client and server to negotiate the choice of security mechanism to use.
The issue was initially rated as high severity because the successful exploitation of this issue required an attacker to prepare the target environment to improve exploit reliability.
Microsoft addressed the vulnerability with the release of Patch Tuesday security updates for September 2022.
IBM Security X-Force researcher Valentina Palmiotti demonstrated that this vulnerability is a pre-authentication remote code execution issue that impacts a wide range of protocols. It has the potential to be wormable and can be exploited to achieve remote code execution.
“The vulnerability could allow attackers to remotely execute arbitrary code by accessing the NEGOEX protocol via any Windows application protocol that authenticates, such as Server Message Block (SMB) or Remote Desktop Protocol (RDP), by default.” reads the post published by IBM. “This list of affected protocols is not complete and may exist wherever SPNEGO is in use, including in Simple Message Transport Protocol (SMTP) and Hyper Text Transfer Protocol (HTTP) when SPNEGO authentication negotiation is enabled, such as for use with Kerberos or Net-NTLM authentication.”
Unlike the CVE-2017-0144 flaw triggered by the EternalBlue exploit, which only affected the SMB protocol, the CVE-2022-37958 flaw could potentially affect a wider range of Windows systems due to a larger attack surface of services exposed to the public internet (HTTP, RDP, SMB) or on internal networks. The expert pointed out that this flaw can be exploited without user interaction or authentication.
IBM announced it will release full technical details in Q2 2023 to give time organizations to apply the security updates.

Mastering Windows Security and Hardening: Secure and protect your Windows environment from intruders, malware attacks, and other cyber threats
Dec 12 2022
Malware attacks are a growing problem in our increasingly digital world. By infiltrating computers and networks, malicious software can cause serious harm to those affected by it.
One of the most common types of malware is ransomware (encryption-based malware), which prevents users from accessing their files until they pay a hefty fee to the cyber attacker. This type of attack has been used to target everything from individuals to large organizations, including government agencies and healthcare providers.
In addition to financial losses, malware attacks can have devastating effects on businesses and individuals. In some cases, sensitive data can be stolen or destroyed as part of an attack. This can lead to identity theft and other forms of fraud, as well as put organizations at risk for long-term damage if confidential information is exposed or compromised.
A recent study by Atlas VPN shows how malware infection is on the rise and the trends in the new malware samples found in the first three quarters of 2022.
According to researchers, 59.58 million samples of new Windows malware were found in the first three quarters of 2022 and these make up 95.6% of all new malware discovered during that time period.
This analysis was based on data by AV-TEST GmbH, an independent organization that evaluates and rates antivirus and supplies services in IT Security and Antivirus Research. The study also includes new malware samples detected in the four quarters of 2021 and the first three quarters of 2022.
Overall, there is a downward trend in the data with the malware samples this year has decreased by 34% as compared to the same period last year. However, the numbers are still exceptionally high.
Following Windows on the list is Linux malware with 1.76 million new malware samples – 2.8% of the total malware threats in 2022.
Android malware takes third place with the first three quarters of 2022 seeing 938,379 new Android malware threats, constituting 1.5% of the total new malware.
Lastly, 8,329 samples of never before seen malware threats aimed at macOS were observed in the same period.
The study also shows that the total number of malware threats found in the first three quarters of 2022 across all operating systems amount to 62.29 million. This is about 228,164 malware threats daily.
If we make a quarter-by-quarter comparison, the first quarter of 2022 saw the most significant number of malware samples – 22.35 million. However, this number dropped by 4% to 21.49 million in the second quarter of this year. Again, it decreased by another 14% to 18.45 million.
The numbers continue to plummet into the fourth quarter of the year with 7.62 million new threats found in October and November – nearly 60% less than at the same time last year.
Malware is a pervasive threat to internet users on both personal and professional networks. It can cause serious damage to computers, networks, and data that can be expensive to fix. Fortunately, there are steps you can take to protect yourself from malware.
The most important step in protecting your network from malware is keeping your anti-malware software up to date. Regularly updating anti-malware programs ensures that they’re able to detect the latest threats and keep them away from your computer or network.
Additionally, be sure not to click on suspicious links or download files from unknown sources as these could contain malicious code that could harm your system.
Another way to stay safe online is by using a secure web browser with built-in security features like pop-up blockers, phishing protection, and ad blockers ((don’t use it on Hackread.com though :0)) for enhanced protection against malicious activities.
