Trace and Log Analysis: A Pattern Reference for Diagnostics and Anomaly Detection
![Trace and Log Analysis: A Pattern Reference for Diagnostics and Anomaly Detection by [Dmitry Vostokov, Software Diagnostics Institute]](https://m.media-amazon.com/images/I/5148hRrenTL.jpg)
Dec 27 2021
Dec 24 2021
Elastic Security researchers uncovered a malware campaign that leverages a new malware and a stealthy loader tracked as BLISTER, that uses a valid code signing certificate issued by Sectigo to evade detection.
BLISTER loads second-stage payloads that are executed directly in the memory of the Windows system and maintain persistence. The malicious code has a low detection rate and implements multiple tricks to avoid detection.
“A valid code signing certificate is used to sign malware to help the attackers remain under the radar of the security community. We also discovered a novel malware loader used in the campaign, which we’ve named BLISTER. The majority of the malware samples observed have very low, or no, detections in VirusTotal.” “The infection vector and goals of the attackers remain unknown at this time.”

The certificate used to sign the loader code was issued by Sectigo for a company called Blist LLC, which has an email address from a Russian provider Mail.Ru.
The loader is embedded into legitimate libraries, such as colorui.dll, to avoid raising suspicion, it can be initially written to disk from simple dropper executables.
Upon execution, BLISTER decodes bootstrapping code stored in the resource section with a simple 4-byte XOR routine. The malware authors heavily obfuscated the bootstrapping code that initially sleeps for 10 minutes before executing in an attempt to evade sandbox analysis.
Then the loader decrypts the embedded malware payload, experts reported the use of CobaltStrike and BitRat as embedded payloads. The payload is loaded into the current process or injected into a newly pawned WerFault.exe process.
In order to achieve persistence, BLISTER copy itself to the C:\ProgramData folder and re-names a local copy of rundll32.exe. Then it creates a link to the current user’s Startup folder to launch the malware at logon as a child of explorer.exe.
Elastic’s researchers shared Yara rules for this campaign along with indicators of compromise.
Malware Analysis and Detection Engineering: A Comprehensive Approach to Detect and Analyze Modern Malware

InfoSec is the page where the InfoSec community interacts, and share InfoSec & compliance related information.
“You Become What You Think About Ask; and it shall be given to you Seek; and you shall find Knock; and it shall be opened unto you.”
Dec 22 2021
Microsoft released an alert on a couple of Active Directory vulnerabilities, that have been fixed with the November 2021 Patch Tuesday security updates, that could allow threat actors to takeover Windows domains.
The flaws, tracked as CVE-2021-42287 and CVE-2021-42278, can be chained to impersonate domain controllers and gain administrative privileges on Active Directory.
Microsoft is now warning customers to address both issues immediately due to the public availability of Proof-of-concept exploit code. The IT giant also published a guide to help customers in detecting the attempts of exploitation of both issues.
“Both vulnerabilities are described as a ‘Windows Active Directory domain service privilege escalation vulnerability’.A few weeks later, on December 12, 2021, a proof-of-concept tool leveraging these vulnerabilities was publicly disclosed.” states Microsoft. “When combining these two vulnerabilities, an attacker can create a straightforward path to a Domain Admin user in an Active Directory environment that hasn’t applied these new updates. This escalation attack allows attackers to easily elevate their privilege to that of a Domain Admin once they compromise a regular user in the domain.”
The CVE-2021-42278 vulnerability is a security bypass issue that allows potential attackers to impersonate a domain controller using computer account sAMAccountName spoofing.
Experts pointed out that sAMAccountName attributes usually end with “$” in their name. “$” was used to distinguish between user objects and computer objects. With default settings, a normal user has permission to modify a machine account (up to 10 machines) and as its owner, they also have the permissions to edit its sAMAccountName attribute.

Sep 18 2021
Using OMI on Microsoft Azure? Drop everything and patch this critical vulnerability, snappily named OMIGOD. But wait! You probably don’t know whether you’re using OMI or not.
Y’see, Open Management Infrastructure (OMI) is often silently installed on Azure—as a prerequisite. And, to make matters worse, Microsoft hasn’t rolled out the patch for you—despite publishing the code a month ago. So much for the promise of ‘The Cloud.’
What a mess. In today’s SB Blogwatch, we put the “mess” into message.
Your humble blogwatcher curated these bloggy bits for your entertainment. Not to mention: Difficult Hollywood.
What’s the craic? Simon Sharwood says—“Microsoft makes fixing deadly OMIGOD flaws on Azure your job”:
Your next step”
Microsoft Azure users running Linux VMs in the … Azure cloud need to take action to protect themselves against the four “OMIGOD” bugs in the … OMI framework, because Microsoft hasn’t. … The worst is rated critical at 9.8/10 … on the Common Vulnerability Scoring System.
…
Complicating matters is that running OMI is not something Azure users actively choose. … Understandably, Microsoft’s actions – or lack thereof – have not gone down well. [And it] has kept deploying known bad versions of OMI. … The Windows giant publicly fixed the holes in its OMI source in mid-August … and only now is advising customers.
…
Your next step is therefore obvious: patch ASAP.
‘OMIGOD’ Azure Critical Bugfix? Do It Yourself—Because Microsoft Won’t

Sep 08 2021
Details are scarce so far, but Microsoft is warning Office users about a bug that’s dubbed
The bug doesn’t have a patch yet, so it’s what’s known as a zero-day, shorthand for “the Good Guys were zero days ahead of the Bad Guys with a patch for this vulnerability.”
In other words: the crooks got there first.
As far as we can tell, the treachery works like this:
MSHTML isn’t a full-on browser, like Internet Explorer or Edge, but is a part of the operating system that can be used to create browsers or browser-like applications that need or want to display HTML files.
Even though HTML is most closely associated with web browsing, many apps other than browsers find it useful to be able to render and display web content, for example as a convenient and good-looking way to present documentation and help files, or to let users fill in and submit support tickets.
This “stripped down minibrowser” concept can be found not only on Windows but also on Google’s Android and Apple’s iOS, where the components Blink and WebKit respectively provide the same sort of functionality as MSHTML on Microsoft platforms. Mozilla products such as Firefox and Thunderbird are based on a similar idea, known as Gecko. On iOS, interestingly, Apple not only uses WebKit as the core of its own browser, Safari, but also mandates the use of WebKit in browsers or browser-like apps from all other vendors. That’s why Firefox on iOS is the only version of that product that doesn’t include Gecko -it has no choice but to use WebKit instead.
Sep 03 2021
A set of 16 security flaws in commercial Bluetooth stacks, collectively tracked as BrakTooth, can be exploited by threat actors to execute arbitrary code and crash the devices via DoS attacks.
The issues were discovered by the ASSET (Automated Systems SEcuriTy) Research Group from the Singapore University of Technology and Design (SUTD), their name comes from the Norwegian word “Brak” which translates to ‘crash’.
The BrakTooth flaws impact 13 Bluetooth chipsets from 11 vendors, including Intel, Qualcomm, and Texas Instruments, experts estimated that more than 1,400 commercial products may be impacted.
As of today, the researchers discovered 16 security vulnerabilities, with 20 common vulnerability exposures (CVEs) already assigned and four vulnerabilities are pending CVE assignment from Intel and Qualcomm.
“we disclose BrakTooth, a family of new security vulnerabilities in commercial BT stacks that range from denial of service (DoS) via firmware crashes and deadlocks in commodity hardware to arbitrary code execution (ACE) in certain IoTs.” reads the post published by the researchers. “All the vulnerabilities are already reported to the respective vendors, with several vulnerabilities already patched and the rest being in the process of replication and patching. Moreover, four of the BrakTooth vulnerabilities have received bug bounty from Espressif System and Xiaomi. “
The attack scenario tested by the experts only requires a cheap ESP32 development kit (ESP-WROVER-KIT) with a custom (non-compliant) LMP firmware and a PC to run the PoC tool they developed. The tool communicates with the ESP32 board via serial port (/dev/ttyUSB1) and launches the attacks targeting the BDAddress (<target bdaddr>) using the specific exploit (<exploit_name>).
The ASSET group has released the PoC tool to allow vendors to test their devices against the vulnerabilities

Guide to Bluetooth Security: Recommendations of the National Institute of Standards and Technology (Special Publication 800-121 Revision 1)

Aug 31 2021
Windows 11 won’t auto-update on slightly old PCs. It appears this includes security updates—although Microsoft PR is doing its usual trick of ghosting reporters who ask.
This sounds like a terrible idea: A fleet of unpatched Windows 11 PCs connected to the internet? That’s a recipe for disaster.
Stand by for Redmond to walk this one back in an embarrassing climbdown. In today’s SB Blogwatch, we hope against hope.
Your humble blogwatcher curated these bloggy bits for your entertainment. Not to mention: Olivia vs. Paramore.
What’s the craic? Sean Hollister reports—“Microsoft is threatening to withhold Windows 11 updates if your CPU is old”:
Why leave us in the dark?”
Windows 11 won’t technically leave millions of PCs behind … so long as you download and manually install an ISO file. … But it turns out even that technicality has a technicality: Microsoft is now threatening to withhold Windows Updates … potentially even security updates.
…
It’s quite possible this is just a cover-your-ass measure. … But it’s also possible Microsoft genuinely does mean to withhold patches. … Microsoft declined to clarify things further.
…
Windows 11 could theoretically be an operating system where you go back to the days of manually downloading [security] updates. … Feature updates are probably less of a big deal. [But] why leave us in the dark?


Aug 26 2021
It should be noted that this is a local privilege escalation (LPE) vulnerability, which means that you need to have a Razer devices and physical access to a computer. With that said, the bug is so easy to exploit as you just need to spend $20 on Amazon for Razer mouse and plug it into Windows 10 to become an admin.
Privileged Attack Vectors

Razer DeathAdder Essential Gaming Mouse

Aug 23 2021
Razer gaming mice come with a buggy installer. It starts automatically when you plug in one of Razer’s devices.
The installer runs as SYSTEM. And it lets you start a shell—which also runs as SYSTEM. A classic elevation-of-privilege bug. And one that’s incredibly simple to exploit.
Déjà vu? It’s like PrintNightmare all over again. In today’s SB Blogwatch, we point the fingers of blame.
Your humble blogwatcher curated these bloggy bits for your entertainment. Not to mention: A VHS player with a window.
What’s the craic? Lawrence Abrams reports—“Become a Windows 10 admin by plugging in a mouse”:
It took us about two minutes”
Razer is a very popular computer peripherals manufacturer known for its gaming mouses and keyboards. When plugging in a Razer device into Windows 10 or Windows 11, the operating system will automatically download and begin installing the Razer Synapse software.
…
A zero-day vulnerability in the plug-and-play Razer Synapse installation … allows users to gain SYSTEM privileges [which is] the highest user rights available in Windows. … It took us about two minutes to gain SYSTEM privileges in Windows 10 after plugging in our mouse.
…
Razer has contacted the security researcher to let them know that they will be issuing a fix. … Razer also told the researcher that he would be receiving a bug bounty reward.
O RLY? Surur Davids adds—“All you need to gain admin privileges on Windows 10 is to plug in a Razer mouse”:
This Mouse Gives you Admin on Windows
Mastering Windows Security and Hardening: Secure and protect your Windows environment from intruders, malware attacks, and other cyber threats

Aug 09 2021
Researchers at the security consultancy Dolos Group, hired to test the security of one client’s network, received a new Lenovo computer preconfigured to use the standard security stack for the organization. They received no test credentials, configuration details, or other information about the machine.
They were not only able to get into the BitLocker-encrypted computer, but then use the computer to get into the corporate network.
Trusted Platform Modules: Why, when and how to use them

Jul 24 2021
Security researcher Gilles Lionel (aka Topotam) has discovered a vulnerability in the Windows operating system that allows an attacker to force remote Windows machines to authenticate and share their password hashes with him. The news of the attack was first reported by The Record.
The attack abuse the Encrypting File System Remote (EFSRPC) protocol, which is used to perform maintenance and management operations on encrypted data that is stored remotely and accessed over a network.
Lionel also published a proof-of-concept (PoC) exploit code on GitHub.
“PoC tool to coerce Windows hosts to authenticate to other machines via MS-EFSRPC EfsRpcOpenFileRaw function. This is possible via other protocols and functions as well .” reads the description provided by the expert.
“The tools use the LSARPC named pipe with inteface c681d488-d850-11d0-8c52-00c04fd90f7e because it’s more prevalent. But it’s possible to trigger with the EFSRPC named pipe and interface df1941c5-fe89-4e79-bf10-463657acf44d.”
In the PetitPotam attack demonstrated by the expert, he sent SMB requests to a remote system’s MS-EFSRPC interface and forced its system to initiate an authentication procedure and share its NTLM authentication hash.
The NTLM authentication hash can be used to carry out a relay attack or can be lately cracked to obtain the victim’s password. The PetitPotam attack can be very dangerous because it allows attackers to take over a domain controller and compromise the entire organization.

Jul 21 2021
Windows “hives” contain registry data, some of it secret. The nightmare is that these files aren’t properly protected against snooping.
As if one Windows Nightmare dogging all our printers were not enough…
…here’s another bug, disclosed by Microsoft on 2021-07-20, that could expose critical secrets from the Windows registry.
Denoted CVE-2021-36934, this one has variously been nicknamed HiveNightmare and SeriousSAM.
The moniker HiveNightmare comes from the fact that Windows stores its registry data in a small number of proprietary database files, known in Microsoft jargon as hives or hive files.
These hive files include a trio called SAM, SECURITY and SYSTEM, which between them include secret data including passwords and security tokens that regular users aren’t supposed to be able to access.
They’re kept in a special, and supposedly secure, folder under the Windows directory called C:\Windows\System32\config, as you see here:
C:\Windows\System32\config> dir [. . .] Directory of C:\Windows\System32\config [. . .] 21/07/2021 12:57 524,288 BBI 25/06/2021 06:21 28,672 BCD-Template 21/07/2021 14:45 32,768,000 COMPONENTS 21/07/2021 12:57 786,432 DEFAULT 21/07/2021 12:32 4,194,304 DRIVERS [. . .] 21/07/2021 12:57 65,536 SAM <--some system secrets included 21/07/2021 12:57 32,768 SECURITY <--some system secrets included 21/07/2021 12:57 87,556,096 SOFTWARE 21/07/2021 12:57 11,272,192 SYSTEM <--some system secrets included [. . .] The moniker SeriousSAM comes from the filenameSAM, which is short for Security Account Manager, a name that sounds as serious as the file’s content’s are.
Jun 26 2021
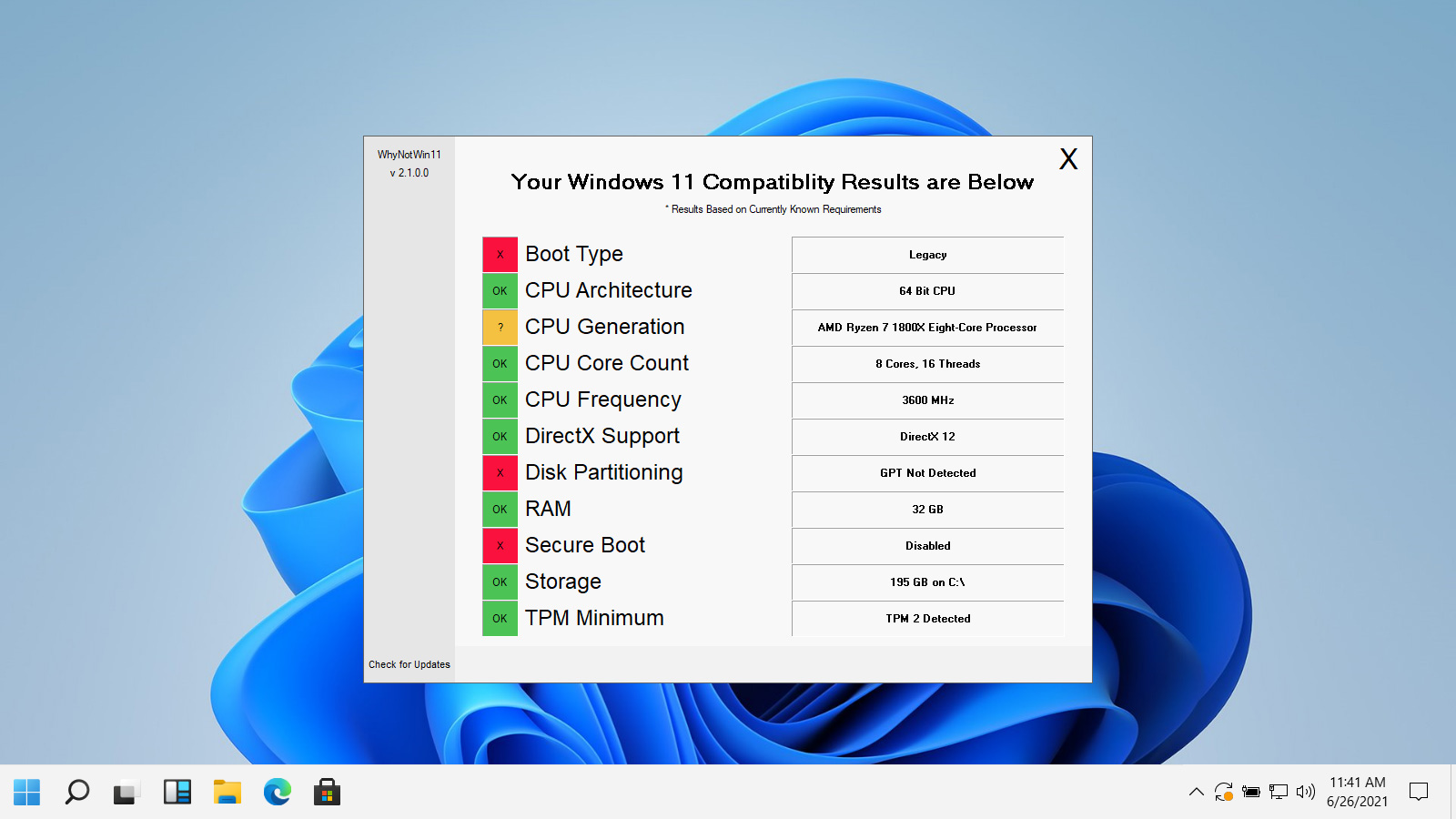
An open-source application called WhyNotWin11 acts as a better drop-in replacement for Microsoft’s PC Health Check app to determine if your hardware is compatible with Windows 11.
This week, Microsoft announced that the next version of Windows is Windows 11 would be the next version of Windows and that it would be released as a free upgrade this fall.
As part of this announcement, Microsoft also published Windows 11’s minimum hardware requirements needed to upgrade or install Windows 11.
Microsoft released the PC Health Check app to check your computer’s hardware and tell you if it is compatible with Windows 11.
Unfortunately, Microsoft’s first version of the PC Health Check app did not tell users what hardware was failing tests, leading to even more confusion.
For many people, the issue was that they did not have a required TPM 2 compatible security processor enabled on their computer. As a result, Microsoft released an updated PC Health Check app that specifically warned users that a TPM 2 device was missing.
Source: WhyNotWin11 is a better replacement for Windows 11’s PC Health Check
Microsoft Introducing Windows 11
May 24 2021
Microsoft Patch Tuesday for May 2021 security updates addressed 55 vulnerabilities in Microsoft including a critical HTTP Protocol Stack Remote Code Execution vulnerability tracked as CVE-2021-31166. The flaw could be exploited by an unauthenticated attacker by sending a specially crafted packet to a targeted server utilizing the HTTP Protocol Stack (http.sys) to process packets.
This stack is used by the Windows built-in IIS server, which means that it could be easily exploited if the server is enabled. The flaw is wormable and affects different versions of Windows 10, Windows Server 2004 and Windows Server 20H2.
The security researcher Axel Souchet has published over the weekend a proof-of-concept exploit code for the wormable flaw that impacted Windows IIS.
The PoC exploit code allows to crash an unpatched Windows system running an IIS server, it does not implement worming capabilities. Anyway, attackers could start triggering the vulnerability in the wild, the PoC code could be improved to be actively exploited.
Now, the security researcher Jim DeVries reported that the issue also impacts Windows 10 and Server devices running the Windows Remote Management (WinRM) service. a component of the Windows Hardware Management feature set which also makes use of the vulnerable HTTP.sys.
Windows Remote Management (WinRM) is the Microsoft implementation of WS-Management Protocol, a standard Simple Object Access Protocol (SOAP)-based, firewall-friendly protocol that allows hardware and operating systems, from different vendors, to interoperate.
The WinRM service is enabled by default on Windows servers running versions 2004 or 20H2 for this reason it only poses a serious risk to corporate environments, DeVries explained to BleepingComputer.
Windows Security and Hardening

May 21 2021
A Pass the Hash (PTH) attack is a technique whereby an attacker captures a password hash as opposed to the password itself (characters) thereby gaining access (authentication) to the networked systems. This technique is used to steal credentials and enable lateral movement within a network. In a Windows environment, the challenge-response model used by NTLM security is abused to enable a malicious user to authenticate as a valid domain user without knowing their password. Now that Kerberos has replaced NTLM as the preferred authentication method for Windows domains, NTLM is still enabled in many Windows domains for compatibility reasons. And so, pass the hash attacks remain an effective tool in the hands of attackers. It is worth noting that there are other attacks associated with Keberos such as Pass the ticket and Kerberos-brute force attack etc. I will be discussing this in my next guide. Below are some articles relating to this topic: NT LAN Manager: How to prevent NTLM credentials from being sent to remote servers, Active Directory Authentication methods:How do Kerberos and NTLM work, and How to configure a service account for Kerberos delegation.

Mar 03 2021
Microsoft has awarded the security researcher Laxman Muthiyah $50,000 for reporting a vulnerability that could have allowed anyone to hijack users’ accounts without consent.
According to the expert, the vulnerability only impacts consumer accounts.
The vulnerability is related to the possibility to launch a bruteforce attack to guess the seven-digit security code that is sent via email or SMS as a method of verification in password reset procedure.
“To reset a Microsoft account’s password, we need to enter our email address or phone number in their forgot password page, after that we will be asked to select the email or mobile number that can be used to receive security code.” the expert wrote. “Once we receive the 7 digit security code, we will have to enter it to reset the password. Here, if we can bruteforce all the combination of 7 digit code (that will be 10^7 = 10 million codes), we will be able to reset any user’s password without permission.”
The researcher pointed out that rate limits are implemented to limit the number of attempts and protect the accounts.
The analysis of the HTTP POST request sent to validate the code revealed that the code is encrypted before being sent, this means that in order to automate bruteforce attacks it was necessary to break the encryption.
Feb 28 2021
There is a solution to both these issues – durability and security.
Rugged devices are designed specifically for your hardworking enterprise operations. They integrate seamlessly into UEM and MDM platforms, can be trained to only engage with secure networks, and can be geofenced to turn themselves into expensive paperweights if taken off-property.
Rugged devices are not only trusted for their durability and performance, but their security capabilities are also unparalleled when it comes to providing your IT security team with top-down controls over device management and data security.
Their sturdy construction, replaceable shift batteries, and stable software platform ensures that your investment will last for years and will eliminate “down-time” (if used correctly).
What’s more, a survey conducted by Samsung found that employees were not only open to using ruggedized devices, over 90% of respondents currently using rugged tech – and over half of non-user respondents – wanted management to invest more into such devices.
Why enterprises need rugged devices with integrated endpoint management systems
Feb 19 2021
Due to the recent rise in cryptocurrency trading prices, most online systems these days are often under the assault of crypto-mining botnets seeking to gain a foothold on unsecured systems and make a profit for their criminal overlords.
The latest of these threats is a botnet named WatchDog. Discovered by Unit 42, a threat intelligence division at Palo Alto Networks, this crypto-mining botnet has been active since January 2019.
Written in the Go programming language, researchers say they’ve seen WatchDog infect both Windows and Linux systems.
The point of entry for their attacks has been outdated enterprise apps. According to an analysis of the WatchDog botnet operations published on Wednesday, Unit 42 said the botnet operators used 33 different exploits to target 32 vulnerabilities in software such as:
Windows and Linux servers targeted by new WatchDog botnet for almost two years
Feb 10 2021
There were 56 newly-reported vulnerabilities fixed in this month’s patches from Microsoft, with four of them offering attackers the chance of finding remote code execution (RCE) exploits.
Remote code execution is where otherwise innocent-looking data that’s sent in from outside your network can trigger a bug and take over your computer.
Bugs that make it possible for booby-trapped chunks of data to trick your computer into executing untrusted code are much sought after by cybercriminals, because they typically allow crooks to break in and implant malware…
…without popping up any “are you sure” warnings, without needing niceties like a username and a password, and sometimes without even leaving any obvious traces in your system logs.
With all of that in mind, the statistic “56 fixes including 4 RCEs” signals more than enough risk on its own to make patching promptly a priority.