The Blacklotus bootkit was developed expressly for Windows, and it first appeared on hacker forums in October of the previous year. It was described as having APT-level capabilities, including the ability to circumvent secure boot and user access control (UAC), as well as the capacity to deactivate security software and defensive mechanisms on victim computers. Threat actors of various skill levels were able to purchase BlackLotus when it was first offered for sale on hacker forums for as little as $5,000, giving them access to malware that is often associated with state-sponsored hacking operations. However, the threat actor concealed the source code and charged clients $200 for rebuilds if they wished to modify the bootkit in any way.c
Microsoft published a set of resources in April that are intended to assist threat hunters in recognizing BlackLotus infections. The National Security Agency (NSA) released some guidelines in June to assist firms in strengthening their defenses against the threat.
Although it has a number of alterations in comparison to the malware’s initial form, the BlackLotus UEFI bootkit’s original source code has been made available to the public on GitHub.
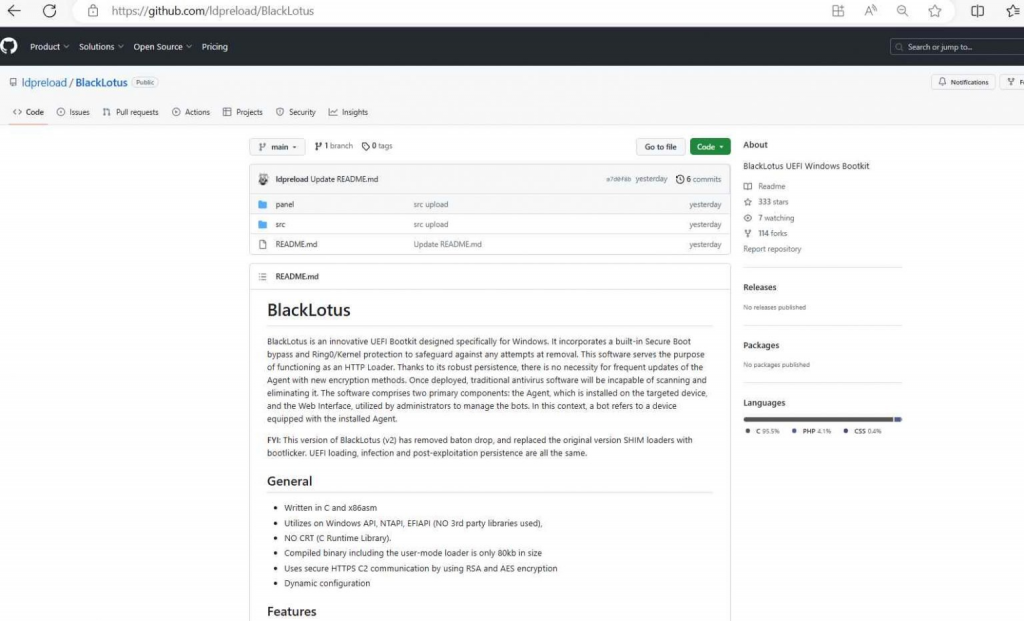
The ‘Baton Drop’ exploit that targets CVE-2022-21894 has been removed from the BlackLotus source code that was released on GitHub on Wednesday. Additionally, the BlackLotus source code now employs the bootlicker UEFI firmware rootkit, although it still retains the majority of the original code.
The fact that the bootkit’s source code is available to the public poses a considerable danger, primarily because it may be paired with newly discovered vulnerabilities to open up previously undiscovered entry points for attacks. BlackLotus was able to utilize the attack despite the fact that CVE-2022-21894 had been fixed the previous year. This was possible because the vulnerable binaries had not been put to the UEFI revocation list. This demonstrates how even vulnerabilities that have been patched may still present long-term, industry-wide supply chain impact.
However, since the source code was leaked, it is now very easy for threat actors to combine the bootkit with new bootloader vulnerabilities, whether they are known or undiscovered. The methods used by the bootkit are no longer cutting edge.
Be careful to adhere to the extensive mitigation guidance that the NSA issued a month ago in order to protect your computers against the BlackLotus UEFI bootkit attack.
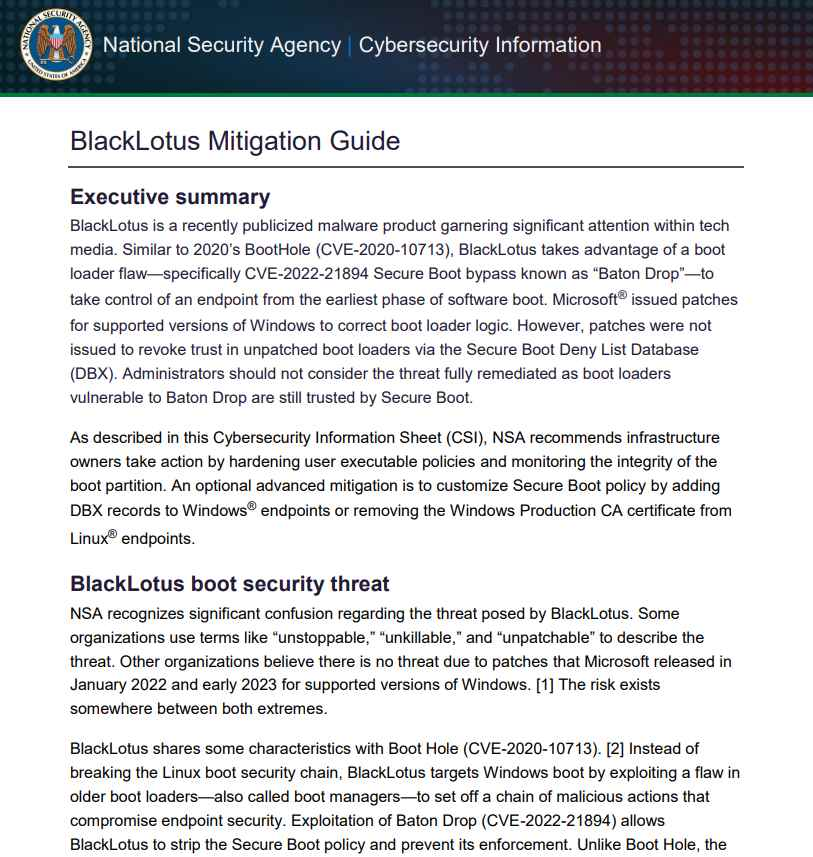
Because the source code of the bootkit is now freely accessible, it is feasible that skilled malware writers may design more powerful variations that are able to circumvent both currently available countermeasures and those that will be developed in the future.
How to Hack Like a Legend: Breaking Windows
InfoSec tools | InfoSec services | InfoSec books



