
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot
Apr 08 2024
Mar 28 2024
Wireshark stands as the undisputed leader, offering unparalleled tools for troubleshooting, analysis, development, and education.
The latest update, Wireshark 4.2.4, includes a host of fixes and updates to further cement its position as the go-to tool for network professionals and enthusiasts alike.
This release underscores the Wireshark Foundation’s commitment to advancing protocol analysis education, a mission supported by contributions from the global community.
The Wireshark team has diligently addressed several vulnerabilities in this release, notably:
Wireshark has also been the subject of CVEs assigned without coordination with the project, specifically CVE-2024-24478, CVE-2024-24479, and CVE-2024-24476.
The Wireshark team has contested these, stating they are based on invalid assumptions, and has requested their rejection, showcasing the team’s proactive stance on security matters.
The 4.2.4 update addresses a variety of bugs, improving user experience and software reliability:
While this release does not introduce new features or protocols, it significantly updates support for many existing protocols, including but not limited to 5GLI, BGP, DHCPv6, and ZigBee ZCL.
This comprehensive update ensures that Wireshark remains at the forefront of protocol analysis, capable of handling the latest network communication standards.
Wireshark 4.2.4 can be downloaded from the official Wireshark website, and detailed instructions for installation across various platforms are available.
Manual installation of this update is required for users upgrading from versions 4.2.0 or 4.2.1 on Windows.
Most Linux and Unix distributions provide Wireshark packages through their native package management systems, making installation or upgrade seamless.
For specific file locations for preference files, plugins, SNMP MIBS, and RADIUS dictionaries, users can refer to the Help section within Wireshark or use the tshark -G folders command.
Wireshark 4.2.4 exemplifies the ongoing dedication of the Wireshark Foundation and its global community to enhance the utility and security of the world’s premier network protocol analyzer.
This release ensures that Wireshark remains an indispensable tool for network professionals and enthusiasts by addressing critical vulnerabilities, fixing bugs, and updating protocol support.
As the project continues to evolve, the support and contributions from the community remain vital to its success.
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Dec 22 2023
Whether you’re a large or small business, network security is something you can’t ignore.
Threat actors can and will, infiltrate businesses of any size wreaking havoc on computer systems, maliciously encrypting data, and in some cases completely destroying a company’s ability to stay in business.
While the latter situation isn’t that common, there have been several recent instances where poor network security has led to significant security breaches.
Consider the Uber breach QAwZ from September 2022, where an MFA fatigue attack led to a breach of Uber’s systems.
A similar attack led to a breach of CISCO’s systems, and Activision ended up being hacked after an SMS phishing attack, which reportedly led to a significant data breach of Activision’s IP and employee data.
These breaches signal the need for better network security practices, and they also show how single security measures are not enough.
All of the breaches mentioned above happened because of a weakness in each company’s MFA practices, but they could’ve been mitigated by other security measures including zero trust granular access rules.
Organizations of all sizes need a network security strategy with modern, cloud-based tools and technologies to stay secure:
Before we even get to network security, organizations should deploy a Single Sign-On (SSO) identity provider with Multi-Factor Authentication (MFA) support.
SSO allows users to access multiple applications using one login.
This makes it easier for users to integrate network security practices into their daily routine without much friction, while the IT team has a much easier time keeping everyone organized.
MFA, meanwhile, adds an extra layer of security by requiring users to provide two or more pieces of evidence to prove their identity.
This is typically a username and password, followed by a one-time code, or biometric authentication such as a fingerprint or facial recognition.
Under an MFA scheme, you can require just a second authentication factor or multiple depending on the level of security you need and your threat model.
SSO with MFA also reduces the risk of password-related security incidents, such as password theft or reuse.
It also makes it harder for hackers to access your network since they have to not only steal the password but somehow obtain the second or even third factor to finally break in.
But as we mentioned at the beginning of this article there are ways to get around MFA security measures, so how do you make sure that doesn’t happen?
It starts with training and clearly defined policies that convey to employees that IT teams and outside security contractors will never ask them for their MFA security codes.
Second, you can increase the difficulty of MFA for higher privileged accounts such as a number-based challenge that requires the user to see both sets of numbers to correctly answer the MFA challenge.
Biometric measures can also be effective as long as employees understand they should never authorize an MFA request they didn’t initiate.
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Oct 17 2023
Cisco IOS XE is a robust and flexible operating system, optimized for the evolving landscape of enterprise networking and technology. It enables model-driven programmability, application hosting, and automated configuration management, thus simplifying many day-to-day tasks. IOS XE is integral in providing consistency across Cisco’s array of switching, routing, and wireless network devices.
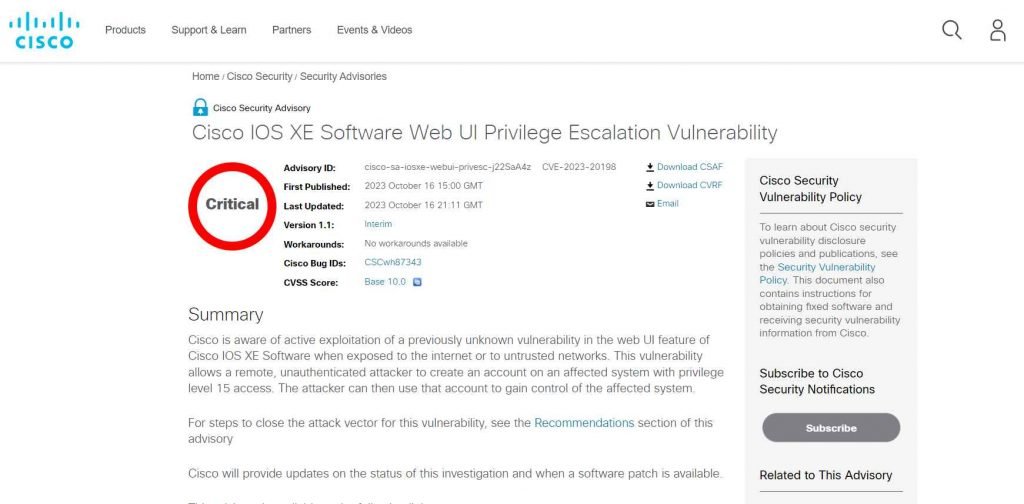
A new, critical zero-day vulnerability has emerged, labeled as CVE-2023-20198. This vulnerability, with a maximum severity rating of CVSS 10, predominantly affects devices running the Cisco IOS XE software and is currently without a patch, leaving systems vulnerable to potential exploits. The flaw can be exploited by an unauthenticated attacker to create a user account with the highest privilege level, leading to unauthorized system access.
Exploitation in the Wild
Attackers have already begun exploiting this vulnerability in the wild, utilizing it to deliver malicious implants. Organizations using the affected devices are advised to apply mitigation measures promptly to defend against these exploits.
Affected Devices and Systems
The vulnerability, CVE-2023-20198, affects all Cisco IOS XE devices that have the Web UI feature enabled, especially when exposed to the internet or untrusted networks. To ascertain if a system is vulnerable, administrators should:
show running-config | include ip http server|secure|active to check for the presence of ip http server or ip http secure-server commands in the global configuration.ip http active-session-modules none or ip http secure-active-session-modules none to determine if the vulnerability is exploitable over HTTP or HTTPS respectively.Cisco’s Response
Cisco has acknowledged the vulnerability, confirming its presence in devices running the Cisco IOS XE software. The company provided steps to identify affected systems and noted the following Indicators of Compromise (IoCs):
%SYS-5-CONFIG_P: Configured programmatically by process SEP_webui_wsma_http from console as user on line.%SEC_LOGIN-5-WEBLOGIN_SUCCESS: Login Success [user: user] [Source: source_IP_address].%WEBUI-6-INSTALL_OPERATION_INFO: User: username, Install Operation: ADD filename.curl -k -X POST "https://systemip/webui/logoutconfirm.html?logon_hash=1", if a hexadecimal string is returned, the implant is present.Cisco, alongside other cybersecurity firms like Tenable, has provided plugins to identify affected systems. While awaiting a patch, these plugins and the aforementioned checks can assist in identifying and mitigating unauthorized access attempts.
CVE-2023-20198 poses a significant threat to cybersecurity due to its maximum severity rating and the absence of a patch. Organizations using affected Cisco IOS XE devices should remain vigilant and apply necessary mitigation measures to safeguard their systems from potential exploits.
Zero Trust Architecture (Networking Technology: Security)
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Sep 03 2023
Jun 29 2023
An specialist in Russian cybersecurity who was sought by the United States has been arrested by officials in Kazakhstan, according to his employer, who made the announcement on Wednesday. At the same time, authorities in Moscow said that they will also pursue his extradition.
According to a statement released by the business, Nikita Kislitsin, an employee of the Russian cybersecurity firm F.A.C.C.T., was arrested on June 22. The Kazakh authorities are now reviewing an extradition request from the United States of America. Nikita Kislitsin was arrested in 2012 and accused of selling the usernames and passwords of American clients of the social networking firm Formspring. The facts of the arrest and the motivation for it are not clear; nonetheless, the case against Kislitsin was filed. After Group-IB left Russia earlier this year, the spinoff business that was established there and was branded as F.A.C.C.T. had Kislitsin working as the head of network security for both companies.
According to a statement released by Group-IB on Telegram, the arrest of Kislitsin is not connected to his employment there in any way. The F.A.C.C.T. said that the allegations brought against Kislitsin originated from his time “as a journalist and independent researcher,” but they could not disclose any other information. Kislitsin served as the editor-in-chief of the Russian publication “Hacker,” which is primarily concerned with information security and hacking at one point in his career.
In a separate proceeding that took place on Wednesday, a Moscow court issued a warrant for Kislitsin’s arrest on allegations that are associated with the unlawful access of confidential computer information. Russia has indicated that it would demand his extradition from Kazakhstan as well.

InfoSec tools | InfoSec services | InfoSec books
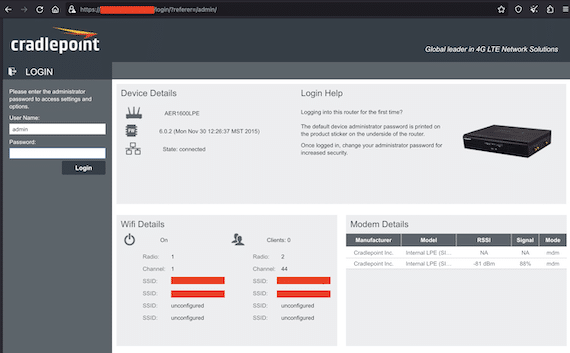
Jun 28 2023
Researchers at Censys have analyzed the attack surfaces of more than 50 Federal Civilian Executive Branch (FCEB) organizations and sub-organizations and discovered more than 13,000 distinct hosts across 100 autonomous systems.
The experts focused on roughly 1,300 of these hosts that were accessible online and discovered hundreds of devices with management interfaces exposed to the public internet.
These devices clearly are not compliant with the BOD 23-02 directive released in June by the US CISA with the objective of mitigating the risks associated with remotely accessible management interfaces.
“The Directive requires federal civilian executive branch (FCEB) agencies to take steps to reduce their attack surface created by insecure or misconfigured management interfaces across certain classes of devices.” states CISA.
Censys specifically looked for publicly accessible remote management interfaces associated with networked devices, including routers, access points, firewalls, VPNs, and other remote server management technologies.
“In the course of our research, we discovered nearly 250 instances of web interfaces for hosts exposing network appliances, many of which were running remote protocols such as SSH and TELNET.” reads the analysis published by Censys. “Among these were various Cisco network devices with exposed Adaptive Security Device Manager interfaces, enterprise Cradlepoint router interfaces exposing wireless network details, and many popular firewall solutions such as Fortinet Fortiguard and SonicWall appliances.”
The researchers discovered 15 instances of exposed remote access protocols such as FTP, SMB, NetBIOS, and SNMP that were running on hosts exposed by Federal Civilian Executive Branches (FCEB). These protocols are known to be plagued by multiple security vulnerabilities that can be exploited by threat actors to compromise them and gain remote unauthorized access to government infrastructure.
The report also states that multiple out-of-band remote server management devices such as Lantronix SLC console servers were exposed only despite CISA’s directive stating that “these out-of-band interfaces should never be directly accessible via the public internet.”
The study also revealed that multiple federal civilian executive branch were exposing managed file transfer tools, such as MOVEit transfer, GoAnywhere MFT, VanDyke VShell file transfer, and SolarWinds Serv-U file transfer. These devices are often the targets of attacks from different threat actors.
“Exposed physical Barracuda Email Security Gateway appliances, which recently made headlines after a critical zero day was discovered being actively exploited to steal data” concludes the report. “Over 150 instances of end-of-life software, including Microsoft IIS, OpenSSL, and Exim. End-of-life software is more susceptible to new vulnerabilities and exploits because it no longer receives security updates, making it an easy target.”
According to BOD 23-02, FCEB agencies have to secure the devices within 14 days of identifying one of these devices.
InfoSec tools | InfoSec services | InfoSec books

May 18 2023
Check Point Research has been monitoring sophisticated attacks on authorities in numerous European countries since January 2023. The campaign made use of a broad number of tools, one of which was an implant, which is a tactic that is often linked with Chinese government-backed cybercriminals. This action has substantial infrastructure similarities with activities that have been previously published by Avast and ESET, which links it to the “Mustang Panda” malware family. This cluster of suspicious behavior is
being monitored by CPR as “Camaro Dragon” at the moment.
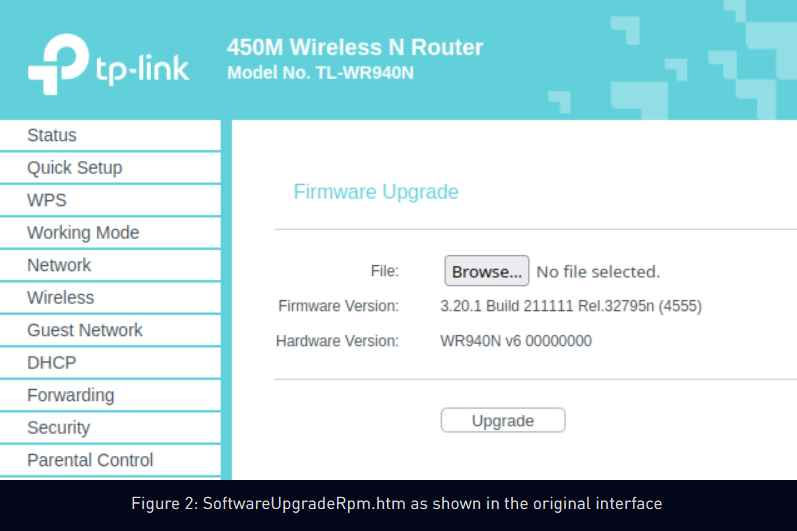
According to experts from Check Point named Itay Cohen and Radoslaw Madej, an investigation of these attacks has uncovered a bespoke firmware implant that was created specifically for TP-Link routers. “The implant features several malicious components, including a custom backdoor named ‘Horse Shell,’ that enables the attackers to maintain persistent access, build anonymous infrastructure, and enable lateral movement into compromised networks,” the firm claimed.

“Because of the implant’s firmware-agnostic design,” its components may be incorporated into different types of software by a variety of different manufacturers. At this time, the precise mechanism that was utilized to distribute the altered firmware images on the compromised routers is unclear. Likewise, its utilization and participation in real attacks are also unknown. It is believed that the first access may have been gained by taking advantage of security holes that were already known about or by brute-forcing devices that had passwords that were either the default or readily guessed.
According to what is currently known, the C++-based Horse Shell implant gives attackers the ability to run arbitrary shell commands, upload and download files to and from the router, and relay communication between two separate clients. However, in an intriguing turn of events, it is suspected that the router backdoor targets random devices on residential and home networks. This finding lends credence to the theory that hacked routers are being co-opted into a mesh network with the intention of establishing a “chain of nodes between main infections and real command-and-control.”
The purpose of relaying communications between infected routers by utilizing a SOCKS tunnel is to establish an extra layer of anonymity and disguise the end server. This is accomplished by the fact that each node in the chain possesses information only about the nodes that came before and after it in the chain.
To put it another way, the approaches obfuscate the origin and destination of the traffic in a manner that is comparable to how TOR works, which makes it far more difficult to discover the scope of the attack and disrupt it. The finding is just one more illustration of a long-standing pattern in which Chinese threat actors target internet-facing network equipment in order to manipulate the underlying software or firmware of such devices.
InfoSec tools | InfoSec services | InfoSec books

May 12 2023
Because IoT devices often have weak security and are easily hacked, the Internet of Things (IoT) has been an increasingly attractive target for cyber assaults in recent years. This is due to the fact that IoT devices are connected to the internet. Pwn2Own was a competition held in Toronto in the last year that focused on hacking into Internet of Things (IoT) devices such as printers, routers, network-attached storage (NAS) devices, routers, and smart speakers. The competition was organized by the Zero Day Initiative (ZDI), which aimed to bring attention to the vulnerabilities of IoT devices and encourage better security practices from manufacturers. This competition invited skilled hackers to showcase their expertise in locating and exploiting flaws in the devices being used. As part of their investigation and participation in the Pwn2Own Toronto hacking competition that took place in December of last year, Team82 exposed five vulnerabilities that were found in NETGEAR’s Nighthawk RAX30 routers.
If an exploit is successful, an attacker may be able to monitor the online activities of users, hijack users’ connections to the internet, and redirect traffic to malicious websites, as well as insert malware into network traffic.

These vulnerabilities might potentially be used by an attacker to obtain access to and manage networked smart devices (such as security cameras, thermostats, and smart locks), modify router settings (such as passwords or DNS settings), or exploit a network that has been hacked to launch attacks against other devices or networks.
NETGEAR products come with a dedicated server known as soap_serverd that operates on port 5000 (HTTP) and port 5043 (HTTPS). This server serves as a programmatic application programming interface (SOAP) for the router.
Users are given the ability to query the device and make changes to its settings thanks to the available API. The NETGEAR Nighthawk App for iOS and Android is the primary client that connects to the server. The vulnerabilities that were targeted are listed below.

They are able to extract the device serial number by using the CVE-2023-27357 vulnerability, which is known as Sensitive Information Exposed Without Authentication.
By using CVE-2023-27369, also known as an SSL Read stack overflow, researchers are able to deliver an HTTPS payload without being constrained by size requirements.
They are able to create a payload that is sufficiently large to replace the socket IP, bypass authentication, and obtain the device settings by using CVE-2023-27368, which is a sscanf stack overflow vulnerability.
They were able to alter the admin password by using CVE-2023-27370 (Plain text secrets in the configuration), which allowed us to access the plain-text answers to the security questions, along with the serial number that we obtained before.
Once they have updated the password, they were able to send a magic packet to the device in order to activate a limited telnet server. They get root access and remote code execution on the device by using the CVE-2023-27367 vulnerability, which is a restricted shell escape.
It is possible to compromise vulnerable RAX30 routers by chaining together these five CVEs. The most serious of these flaws allows for pre-authentication remote code execution on the device. NETGEAR has patched all five vulnerabilities uncovered by Team82, three of which were high-severity vulnerabilities that enable pre-authentication remote code execution, command injection, or authentication bypasses.
InfoSec tools | InfoSec services | InfoSec books

Apr 14 2023
Whether you’re a large or small business, network security is something you can’t ignore.
Threat actors can and will, infiltrate businesses of any size wreaking havoc on computer systems, maliciously encrypting data, and in some cases completely destroying a company’s ability to stay in business.
While the latter situation isn’t that common, there have been several recent instances where poor network security has led to significant security breaches.
Consider the Uber breach QAwZ from September 2022, where an MFA fatigue attack led to a breach of Uber’s systems.
A similar attack led to a breach of CISCO’s systems, and Activision ended up being hacked after an SMS phishing attack, which reportedly led to a significant data breach of Activision’s IP and employee data.
These breaches signal the need for better network security practices, and they also show how single security measures are not enough.
All of the breaches mentioned above happened because of a weakness in each company’s MFA practices, but they could’ve been mitigated by other security measures including zero trust granular access rules.

Organizations of all sizes need a network security strategy with modern, cloud-based tools and technologies to stay secure:
Before we even get to network security, organizations should deploy a Single Sign-On (SSO) identity provider with Multi-Factor Authentication (MFA) support.
SSO allows users to access multiple applications using one login.
This makes it easier for users to integrate network security practices into their daily routine without much friction, while the IT team has a much easier time keeping everyone organized.
MFA, meanwhile, adds an extra layer of security by requiring users to provide two or more pieces of evidence to prove their identity.
This is typically a username and password, followed by a one-time code, or biometric authentication such as a fingerprint or facial recognition.
Under an MFA scheme, you can require just a second authentication factor or multiple depending on the level of security you need and your threat model.
SSO with MFA also reduces the risk of password-related security incidents, such as password theft or reuse.
It also makes it harder for hackers to access your network since they have to not only steal the password but somehow obtain the second or even third factor to finally break in.
But as we mentioned at the beginning of this article there are ways to get around MFA security measures, so how do you make sure that doesn’t happen?
It starts with training and clearly defined policies that convey to employees that IT teams and outside security contractors will never ask them for their MFA security codes.
Second, you can increase the difficulty of MFA for higher privileged accounts such as a number-based challenge that requires the user to see both sets of numbers to correctly answer the MFA challenge.
Biometric measures can also be effective as long as employees understand they should never authorize an MFA request they didn’t initiate.
One of the biggest and most important strategies in modern network security is the deployment of Zero Trust Network Access. ZTNA assumes that all network traffic is untrusted, even if it originates from inside the network itself.
ZTNA requires that users prove their identity, and then meet specific security requirements before accessing network resources.
This includes granular access rules that can be user- or group-specific. Then context-based verification allows organizations to limit access to resources based on specific criteria, such as device posture, location of the user requesting access, and time of day.
These contexts are also continually verified to ensure that a user’s security posture doesn’t suddenly change, which can be an indication of malicious activity.
Device posture is an important part of context since it demands that user devices meet certain security requirements before accessing resources.
This can be criteria such as the presence of a specific antivirus suite, a custom security certificate, and a minimum operating system version, among others.
When you put it all together Zero Trust Network Access reduces the risk of unauthorized access to sensitive data and resources.
This is a far better approach than the legacy-based VPN and firewall. Under the old model, you would log in with a VPN, and then once you had access to company resources that was it.
There were limited access rules about who could see what and no context-based requirements with continuous verification.
That meant that once a hacker gained access to a system they had an easier time achieving lateral movement (moving from one server or resource to another).
After lateral movement, hackers would often obtain higher privileged account credentials ultimately gaining access to employee and customer data, or sensitive trade secrets.
ZTNA provides better control over network access, which enables organizations to detect and respond to security incidents more effectively.
Malware is one of the biggest and most common threats to network security.
It can infect computers and networks leading to damage to computer systems, malicious data encryption (ransomware), and data exfiltration.
Malware protection solutions are designed to detect and prevent malware from infecting your network via the most common vehicle for infiltration: the Internet.
While you can get infected through malicious USB keys and drives, the most common way is through a malicious website or downloading a malicious file from the Internet.
Malware protection guards against these threats by analyzing web traffic to identify and block malware.
This usually includes a number of techniques such as signature-based detection, behavior-based detection, and virtual code emulation, to identify and block malware.
Putting together a proper malware protection solution can prevent everything from known malware infections to zero-day exploits and advanced persistent threats (APTs).
Web filtering is a security mechanism that blocks access to malicious websites and content.
This is a list-based solution that blocks known malicious websites, and it can also be used to prevent employees from venturing into problematic areas of the Internet that may violate company policies, break local laws, or simply be time-wasting distractions.
The focus, however, is to reduce the risk of employees accessing malicious websites and content, which can lead to malware infections, data breaches, and other forms of cyber threats.
Web Filtering can also reduce the workload for IT teams if they no longer have to deal with issues related to web usage.
Although not directly part of network security, compliance is a key consideration when looking at tools and technologies to keep your network secure.
Many companies are responsible for maintaining records for their customers including private information such as health data, credit card data, addresses, and more.
Holding onto information like this as a necessary part of your business only increases the need for solid network security as the consequences of a breach are that much greater.
That’s why Zero Trust Network Access and other modern tools are so important.
Under a traditional perimeter-based approach hackers will have an easier time obtaining sensitive information after a successful breach.
Now that we understand what tools you need, how do you choose the right network security solution for your organization?
First, you need to anticipate growth and increased demand for your network security needs.
Opt for solutions that can scale with your business, as well as offer the flexibility to adapt to new threats, and regulatory requirements. Quite often cloud-based platforms are the best choice when it comes to flexibility.
Cost is another important issue; network security investment isn’t just about upfront costs.
There can be many ongoing expenses, especially for hardware-based solutions that require regular maintenance, updates, and support.
And don’t forget about potential hidden costs such as additional licensing fees for certain features or upgrades after your initial service contract expires–it pays (literally) to do your due diligence to discover any potential hidden costs.
If your team is too small to allow for a full-time security expert then consider alternatives such as managed service providers (MSPs).
These specialized organizations offer a wide range of fully managed IT services. By outsourcing some or all of your network security functions to an MSP, your organization can benefit from the expertise and resources of a dedicated security team.
MSPs typically offer 24/7 monitoring and support, threat intelligence, and access to the latest security technologies, ensuring that your organization’s network is continuously protected.
Suppose you have pre-existing systems that cannot be replaced or are crucial for your business. In that case, you should also consider solutions that offer seamless compatibility with those systems.
Some common pre-existing hardware includes a data center firewall or possibly SD-Wan appliances.
By considering issues such as scalability, compliance, the total cost of ownership, and legacy integration, you can make an informed decision and select the most suitable network security solution for your organization.
Putting together all of these essential network security features and tools is easy with Perimeter 81.
This cloud-based, converged network security solution provides comprehensive network security focusing on ease of use, lightning-fast deployment, and easy scalability.
Most importantly, however, Perimeter 81 allows you to use ZTNA, Malware Protection, and Web Filtering from a single management console for easier all-around management.
If your ZTNA needs are simpler than most you can also use Perimeter 81’sFirewall as a Service to protect on-prem and cloud-based resources.
While you can permit access to all services to everyone in the company using the firewall, that is not recommended as granular access control is simple to implement with Perimeter 81 even for those with seemingly basic requirements.
A comprehensive network security strategy is critical for all organizations that want to protect their network and data from cyber threats.
This checklist allows organizations to build a robust and effective network security strategy that meets their specific needs and requirements.
Network Security Checklist – Download Free E-Book
Network Security: Private Communication in a Public World

InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Mar 27 2023
This lesson on TLS – Transport Layer Security – analyzes a TLS 1.2 connection with Wireshark.
🔷🔷 About 🔷🔷
TLS 1.2 Wireshark analysis
Wireshark 101: Essential Skills for Network Analysis

SharkTap Gigabit Network Sniffer
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Jan 26 2023
The Wireshark Team has recently unveiled the latest iteration of their widely-utilized packet analyzer, Wireshark 4.0.3.
This version boasts a multitude of improvements, including new features and updates, as well as the resolution of various bugs to ensure a smooth and efficient user experience.
The Wireshark packet analyzer is a free and open-source application that is available for all major platforms. In addition to troubleshooting networks, Wireshark can be used to analyze network traffic, develop software or communications protocols, and can even be used for educational purposes in the cybersecurity field.
Wireshark supports a wide range of network protocols, and with Wireshark, a security professional can see the details of network packets in real-time, including the:-

Many organizations utilize this tool on a regular basis as part of their daily business operations so that they can monitor the day-to-day tasks of their businesses.
Wireshark 4.0.3 packet analyzer is available for all major platforms and operating systems, and below we have given you a list of them in case you need them:-
The 32-bit Windows packages for Wireshark 4.0 and later can’t be downloaded from the official Wireshark website, and cannot be installed on your computer. Currently, Qt 5.12.2 is the version shipped with Windows installers as the standard version.
There are several new fixes for the multitude of vulnerabilities and bugs that have been added to this new version. However, here below we have mentioned new things added to this version:-
Here below we have mentioned the vulnerabilities that have been fixed in this new version:-
Here below we have mentioned the bugs that have been fixed in this new version:-
Listed below are all the updated protocol support that is supported by the current version:-
It is absolutely crucial that users upgrade their current version of Wireshark to the newly released 4.0.3 version as soon as possible.
The Wireshark team has put a great effort into adding new features and fixing bugs to improve the overall user experience. Failure to update will result in missing out on the many enhancements and refinements this version has to offer.
In addition, if you are interested in getting the latest version of the application, you may click this link.
Explore latest WireShark Titles
InfoSec books | InfoSec tools | InfoSec services
Jan 16 2023
Network Penetration Testing determines vulnerabilities in the network posture by discovering Open ports, Troubleshooting live systems, services and grabbing system banners.
The pen-testing helps administrator to close unused ports, additional services, Hide or Customize banners, Troubleshooting services and to calibrate firewall rules.You should test in all ways to guarantee there is no security loophole.
Let’s see how we conduct a step by step Network penetration testing by using some famous network scanners.
Footprinting is the first and important phase were one gather information about their target system.
DNS footprinting helps to enumerate DNS records like (A, MX, NS, SRV, PTR, SOA, CNAME) resolving to the target domain.
We can detect live hosts, accessible hosts in the target network by using network scanning tools such as Advanced IP scanner, NMAP, HPING3, NESSUS.
To obtain Whois information and name server of a webisteroot@kali:~# whois testdomain.com
Traceroute
Network Diagonastic tool that displays route path and transit delay in packetsroot@kali:~# traceroute google.com
Online Tools
Perform port scanning using tools such as Nmap, Hping3, Netscan tools, Network monitor. These tools help us to probe a server or host on the target network for open ports.
Open ports are the gateway for attackers to enter in and to install malicious backdoor applications.root@kali:~# nmap –open gbhackers.com To find all open portsroot@kali:~# nmap -p 80 192.168.169.128 Specific Portroot@kali:~# nmap -p 80-200 192.168.169.128 Range of portsroot@kali:~# nmap -p “*” 192.168.169.128 To scan all ports
Online Tools
Perform banner Grabbing/OS fingerprinting such as Telnet, IDServe, NMAP determines the operating system of the target host and the operating system.
Once you know the version and operating system of the target, we need to find the vulnerabilities and exploit.Try to gain control over the system.root@kali:~# nmap -A 192.168.169.128root@kali:~# nmap -v -A 192.168.169.128 with high verbosity level
IDserve another good tool for Banner Grabbing.

Online Tools
Scan the network using Vulnerabilities using GIFLanguard, Nessus, Ratina CS, SAINT.
These tools help us in finding vulnerabilities with the target system and operating systems.With this steps, you can find loopholes in the target network system.
It acts as a security consultant and offers patch Management, Vulnerability assessment, and network auditing services.
Nessus a vulnerability scanner tool that searches bug in the software and finds a specific way to violate the security of a software product.
Draw a network diagram about the organization that helps you to understand logical connection path to the target host in the network.
The network diagram can be drawn by LANmanager, LANstate, Friendly pinger, Network view.
Proxies act as an intermediary between two networking devices. A proxy can protect the local network from outside access.
With proxy servers, we can anonymize web browsing and filter unwanted contents such as ads and many other.
Proxies such as Proxifier, SSL Proxy, Proxy Finder..etc, to hide yourself from being caught.
The last and the very important step is to document all the Findings from Penetration testing.
This document will help you in finding potential vulnerabilities in your network. Once you determine the Vulnerabilities you can plan counteractions accordingly.
You can download rules and scope Worksheet here – Rules and Scope sheet
Thus, penetration testing helps in assessing your network before it gets into real trouble that may cause severe loss in terms of value and finance.
Kali Linux, Backtrack5 R3, Security Onion
Smartwhois, MxToolbox, CentralOps, dnsstuff, nslookup, DIG, netcraft
Angry IP scanner, Colasoft ping tool, nmap, Maltego, NetResident,LanSurveyor, OpManager
Nessus, GFI Languard, Retina,SAINT, Nexpose
Ncrack, Cain & Abel, LC5, Ophcrack, pwdump7, fgdump, John The Ripper,Rainbow Crack
Wireshark, Ettercap, Capsa Network Analyzer
Metasploit, Core ImpactThese are the Most important checklist you should concentrate with Network penetration Testing .
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity courses online to keep your self-updated.

Checkout our previous posts on Pen Testing…
Contact DISC InfoSec
InfoSec books | InfoSec tools | InfoSec services
Dec 16 2022

Network Security Checklist via Ethical Hackers Academy
Network Security Assessment: Know Your Network

InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Oct 27 2022
A new version of Wireshark has been released recently by the Wireshark Team, it’s Wireshark 4.0.1, which contains several enhancements, new updates, and bug fixes.
Wireshark is one of the most widely used open-source free software packet analyzers that are currently available on the market, and it is available in a variety of options for different platforms.
There are many people who use Wireshark packet analyzers for the analysis of packets, not just network administrators only. As security analysts also use Wireshark packet analyzers for packet analysis purposes.
Several organizations make use of this tool to manage and monitor all the activities of their business operations on a regular basis.
Wireshark recently released its Wireshark 4.0.0 and the current Wireshark 4.0.1 is a quick update from the previous one.
For all the major platforms or operating systems, the Wireshark 4.0.1 packet analyzer is available and here below we have mentioned them:-
There are several primary purposes for using Wireshark as a network protocol analyzer, including:-
Wireshark 4.0 and later do not have any official 32-bit Windows packages that you can install on your computer. Qt 5.12.2 is now the standard version that ships with Windows installers. The previous version of these packages was Qt 6.2.3, which was shipped by default.
This release removes the experimental syntax for the display filter used in Wireshark 4.0.0 that allowed literals to be displayed just using angle brackets <…>. You can use the colon prefix instead while dealing with byte arrays.

Oct 05 2022
There are several open-source packet analyzers available, but Wireshark is among the most popular. Moreover, the application has been upgraded to version 4.0.0 and comes with multiple new features and fixes.
It is not only network administrators who use Wireshark packet analyzers to analyze packets, but also security analysts to analyze packets.
Wireshark network protocol analyzer can be used for the following primary purposes:-
An array of organizations use the tool to manage their business activities related to their business, and it has been adopted by organizations of all sizes.
The official Windows 32-bit package of Wireshark is no longer being distributed with the release of this version. Here below we have mentioned all the new additions:-
In this latest release, Here below we have mentioned all the new and updated features:-

Wireshark for Security Professionals
Feb 23 2022
DPI has become popular since it provides very detailed traffic analysis. However, this approach requires designated hardware sensors and large amounts of processing power, while at the same time being blind to encrypted network traffic and only analysing data flowing over the mirrored infrastructure.
Metadata analysis (MA) overcomes these limitations to provide detailed and insight-enriched visibility into the entire network. In addition, MA is completely unaffected by encryption and ever-increasing network traffic. These advantages make MA-based NDR solutions a superior and future-proof alternative to NDR solution relying on deep packet inspection.
Modern organisations are characterised by complex IT environments and expanding attack surfaces. To protect themselves, they need a robust cyber architecture with a reliable Network Detection and Response (NDR) solution. NDR is crucial to detect suspicious behaviours and malicious actors, and quickly respond to threats. NDR tools continuously analyse traffic to build models of “normal” behaviour on enterprise networks, detect suspicious traffic, and raise alerts.
Traditional NDR solutions rely on deep packet inspection (DPI). This approach supports detailed analysis and has thus become quite popular. But as data volumes increase and network traffic becomes increasingly encrypted, such solutions are becoming inadequate to protect enterprise networks moving forward. What organisations now need is a more future-proof NDR solution relying on metadata analysis.
In this article, we explore and compare two NDR approaches: deep packet inspection and metadata analysis. We will examine why metadata analysis is a superior detection technology to protect IT/OT networks from advanced cyber threats.
Deep packet inspection is the traditional approach to NDR. DPI monitors enterprise traffic by inspecting the data packets flowing across a specific connection point or core switch. It evaluates the packet’s entire payload, i.e., its header and data part to look for intrusions, viruses, spam, and other issues. If it finds such issues, it blocks the packet from going through the connection point.
DPI relies on traffic mirroring. In effect, the core switch provides a copy (“mirror”) of the network traffic to the sensor that then uses DPI to analyse the packet’s payload. Thus, DPI provides rich information and supports detailed analysis of each packet on the monitored connection points. This is one of its biggest benefits.
However, its drawbacks outnumber this benefit. As network traffic continues to increase and IT environments become increasingly complex and distributed, DPI is reaching its limits.

Why DPI can’t detect or prevent advanced cyberattacks
Feb 10 2022
Technological advancements have come a long way – from when internet utility was very limited to when internet connection was achieved only through internet protocol (IP) version 4 (IPv4) addresses to this modern age where IPv6 is the next big thing.
IPv6 stands for internet protocol version 6, as you might have figured out by now, and was first introduced in 2012.
It became imperative after developers discovered that IPv4 had a finite number and addresses. It would not take long before we ran out of possible commutations for the fourth IP version.
As such, a new version that would allow humanity to generate an infinite number of IP addresses was born; IPv6. And several technologies have been built and designed in its wake.
IPv6 proxy, for instance, was subsequently developed to make things easy. IPv6 had several benefits, such as routing traffic and packet headers conveniently and attracting many organizations to start hosting their servers on it.
However, traffic and connections coming from the older IPv4 could not reach or interact with these new servers because they operated on different standards.
Therefore, it became necessary to build a tool that could translate all IPv4 traffic to reach IPv6 hosted servers, hence the IPv6 proxy.
A proxy is a device or computer that can serve as the middleman between different servers or networks.
It can stand anywhere between the user and the internet and transfer data and connections back and forth quickly and securely.
This traffic transfer is often done using its IP and location while concealing the user’s details. This helps to provide necessary security and anonymity for the internet user.
Proxies are not the only tools used in re-routing users’ connections, but they are one of the most effective, and this is evident in the way they work:
Proxies are essential for several reasons, and below are some of the most common:
The internet may be a lovely place for both individuals and brands, but it can also turn sour quickly.
There are cybercriminals monitoring traffic at every turn and waiting for what data to breach.
Proxies are used because they can hide your IP and sensitive data and filter traffic to ensure the user is protected at all times.
Servers are just like every other type of machine – they can only handle what is within their capacity.
When a server has to deal with too much traffic every day, it doesn’t take long before it crashes.
Proxies are helpful because they are excellent at reducing the workload on servers. For instance, proxies can allocate traffic to the available server to prevent one server from taking too much load.
Proxies can also deploy caching mechanisms where they store results from past queries. This way, they can pull the data from what has been stored instead of disturbing the servers.
There are several limitations and restrictions that people face when surfing the internet. Some users can get banned or blocked when they use the same IP to interact with a website or server repeatedly.
Other users can get restricted from using particular services or accessing specific content because of where they live.
Proxies are used to prevent both types of limitations as they can supply users with an extensive collection of IPs to prevent bans and multiple locations from bypassing geo-restrictions.
An IPv6 proxy can be defined as a type of proxy that translates IPv4 traffic into IPv6 traffic. It could be software or hardware that stands between users and the internet and translate this older traffic into the IPv6 version.
The purpose is often to allow traffic from devices using the older IP versions to reach servers hosted on the IP6 standard.
Without this tool, it would be impossible for anyone using the older IP versions to interact with IPv6 standards.
The IPv6 proxy can also perform other essential functions of a regular proxy, including concealing the user’s networks to provide online privacy and filtering traffic to boost online security.
As the world adopts IPv6 standards and gradually moves towards it, several users, including organizations and service providers still using the IPv4 standard, need a tool to help them translate and forward their traffic.
IPv6 proxies work by intercepting traffic from the older IP standard, translating the address and header, and routing the information before forwarding them to an IPv6 server or target device.
There are several ways the IPv6 proxy can be used (visit Oxylabs for more info), including the following:
Like all significant proxies, the IPv4 proxies also play a massive role in boosting your security and that of your data. Whatever your online activity, you can hide your identity using these proxies with zero cost to your browsing speed and performance.
If you experience bans, blockings, and restrictions very often online, you may want to consider switching to the IPv6 proxies as they can easily bypass these challenges. You can easily choose a different IP and location to appear like a completely different user.
IPv4 proxies can also be used with a dedicated scraper to harvest a large amount of data from different sources at once. This capability comes from the fact that an IPv6 proxy can translate and re-route any traffic to help it reach any server. It can also provide you with multiple IP addresses and locations to help you perform these repetitive tasks without using an IP twice.
IPv6 Essentials: Integrating IPv6 into Your IPv4 Network
Jan 08 2022