
Sep 27 2021
A slow-speed internet that makes you wait for ages before you can finally access a webpage is surely quite a pain! It tests your patience to the last limits and doesn’t allow you to complete your work on time. It is equally frustrating for game lovers, who always need an active internet connection to play the games. Alongside this, the slow internet hinders with user’s efficiency to a great deal.
If you are sick and tired of your slow-poke internet, here are a few ways through which you can augment the speed of your internet, easily.
This is surely an age-old formula to repair things and works quite well most of the time. If your internet connectivity is getting blocked or the connection gets interrupted quite a lot, you need to try this method for sure. All you need to do is to turn off the switch giving power to the router. Once you turn it on again, it will work well and deliver you with the speed you always wanted
Going back to the old typical cable connectivity might help you with your internet speed this time. Yes, you read that right! You may need to take that dangling wire out of your storage box and put it back to work. The speed it delivers will amaze you. This happens because there is no distraction, distortion, or blockade anymore, which might affect the signal strength of the Wi-Fi.

Sep 07 2021
Not long ago, independent software developer Tim Perry, creator of the HTTP Toolkit for intercepting and debugging web traffic…
…decided to add proxy support to his product, which, like lots of software these days, is written using Node.js.
ICYMI, Node.js is the project that took the JavaScript language out of your browser and turned it into a full-blown application development system in its own right, a bit like Java (which is unrelated to JavaScript, by the way, for all that the names sound similar).
As well as the JavaScript core, which uses the V8 JavaScript engine from Google’s Chromium project, Node.js sofware typically also relies on NPM, the Node package manager, and the NPM registry, a truly enormous repository of open-source Node tools and programming libraries.
The NPM registry runs from basic text formatting to full-on facial recognition, and almost everything in between.
Instead of writing all, of the code in your project yourself, or even most of it, you simply reference the add-on packages you want to use, and NPM will fetch them for you, along with any additional packages that your chosen package needs…
…and all the packages that those packages need, following the turtles packages all the way down until every piece of add-on code needed to complete the jigsaw has been located and installed automatically.

Poisoned proxy PACs! The NPM package with a network-wide security hole…
Aug 27 2021
The solution is, instead, to focus on building applications that are secure by design, with zero-trust security baked-in rather than bolted-on. This is one of the three key strategic criteria we see for forward-looking enterprises that are accelerating the security of their applications.
Integrating security and the WAN is the next wave in network architecture. That means embedding zero-trust and access management capabilities in applications.
Zero-trust, to continue with the sporting event analogy, requires ticket checks before fans reach the stadium; it determines if they are authentic fans and therefore whether they can enter, where they can go once they’re inside the venue and which events they can watch. Zero-trust uses context as well as identity to authenticate users, and it enables policies that permit access only within a certain time window, a particular network segment or to a specific application. It removes the element of implicit trust that is so easily exploited, whether deliberately by bad actors or accidentally by careless users.
Zero Trust Networks: Building Secure Systems in Untrusted Networks

Aug 10 2021
Evan Grant, a researcher at network security scanning company Tenable, recently decided to have a go at hacking a home router.
The idea, it seems, was more to learn about the general techniques, tools and procedures available to router hackers than to conduct a security assessment of any particular product.
Understandably, therefore, Grant picked a router model using two non-technical criteria: was it popular, and was it available in Canada (Grant’s home country)?
After opening up the router casing to get access to the circuit board, Grant made good progress, by quickly:
Grant’s first stop was to download a binary file (executable program) called httpd, which is the name under which you typically find a home or small business router’s web server, used for managing the device from a browser.
The name httpd stands for HTTP daemon, where HTTP means that the program handles web traffic, and daemon is the Unix/Linux name for what Windows users know as a service: software that runs in the background whether anyone is logged in or not. (The word daemon is properly pronounced “die-moan” or “day-moan”, but many sysadmins just call them “demons”, and you may need to follow suit to avoid causing confusion.)

Network Security Assessment: Know Your Network

May 07 2021
The task of a computer security system is to safeguard the information transmitted over the network and to adequately preserve the data stored in it.
Excluding in this discussion threats due to natural disasters, we can classify the man-made risk, to which an information system is subject, into intentional threats or unintentional threats due to negligence or inexperience.
Businesses need to protect themselves from these threats, which can put both applications and assets at serious risk.
Intentional human threats can come from individuals with an interest in acquiring information or limiting the operation of business processes, driven by the pursuit of financial or political gain, or simply for fun.
An intentional attack can come from individuals outside the organisation or from internal staff such as ex-employees, disgruntled employees or malicious actors. In fact, personnel who are familiar with the security systems and the structure of the information system and who have the authorisation to access the system itself, can get hold of information or insert malicious code more easily.
The development of the Internet and the distributed processing of information over shared lines has certainly made security a necessary duty. Therefore, the corporate network, if not adequately protected, could be subject to unauthorized access with possible network compromise and information theft.
May 04 2021

A Californian hospital operator has made the move to take is network offline after it was hit by a major cyberattack.
Reports state that the Scripps Health computer network that operates across half a dozen hospitals and a number of outpatient facilities in the San Diego, California area was forced to move to offline procedures after hackers launched a major cyberattack.
The Californian hospital operator says it has contacted law enforcement and government agencies of the cyberattack, but failed to mention specifics of the departments it has informed of the potential data breach.
Hospital Operator Takes Network Offline After Major Cyberattack
Data Protection and Privacy in Healthcare

Feb 23 2021
Network monitoring is essential for any organization with a network. Requirements may vary, but in general any IT team is going to need a single, comprehensive solution that shows the entire network in context and makes diagnosing network issues fast and easy.
An effective solution should be able to discover every device connected to the network, automatically generate a network map showing connections and give administrators an easy way to run device inventories and determine what should be monitored.
The solution should generate alerts for a myriad of network issues and support customizable thresholds, so the IT team can proactively respond before end users are impacted. It should monitor the entire network infrastructure (physical, virtual and cloud) while also supporting network traffic analysis, network and application performance monitoring, configuration management and log management. As well, the ability to automate common administrative tasks or implement self-healing actions will drastically reduce the workload of the IT team.
The importance of ease-of-use cannot be overstated! The solution also needs to be able to scale to meet future needs and should support widely geographically distributed networks. Integration with 3rd-party systems is also a key requirement, whether by out-of-the-box connectors or via a robust API.
How do I select a network monitoring solution for my business?
Apr 20 2019
Aug 05 2010
Must have official EC-Council guide to security and vulnerability assessments!
Network Defense: Security and Vulnerability Assessment (Ec-Council Press Series: Network Defense)
This book will provide you with the fundamental knowledge necessary to comprehend overall network security posture and the basic practices in vulnerability assessment. This book will prepare you to take and pass the EC-Council Network Security Administrator (ENSA) exam.
Proactive vulnerability assessment is key to any organisation’s security posture. Constant assessment for potential weakness is required to maintain a security edge. New vulnerabilities in operating systems, software, hardware, and even human elements are identified and exploited every day. This book will give you the information necessary to master this skill.
Contents of the Book:
Key Features and Benefits:
* Will provide you with the fundamental knowledge necessary to comprehend overall network security posture and the basic practices in vulnerability assessment. Helping you to ensure your organisation is well protected.
* Using this book, as well as the other four books in the Network Defense series, to prepare for the ENSA exam you can ensure yourself of the best chance possible of passing on your first attempt.
* Includes Hands-On Projects to encourage you to problem-solve and apply your knowledge. Helping you to ingrain the information in your mind in a practical way.
Book Details:
Paperback: 192 pages
Publisher: Course Technology; 1 edition (April 14, 2010)
Language: English
ISBN-10: 1435483596
ISBN-13: 978-1435483590
Product Dimensions: 10.7 x 8.5 x 0.6 inches
Shipping Weight: 15.2 ounces
Network Defense: Security and Vulnerability Assessment (Ec-Council Press Series: Network Defense)
Feb 10 2009
Traditional security schemes are incapable of meeting new security challenges of today’s business requirements. Most security architectures are perimeter centric and lack comprehensive internal controls. Organizations which are dependent on firewall security might be overtaxing (asking security mechanism to do more than it can handle). Some of the old firewalls rule set stay intact for years, which might be a liability when the firewall rule set neither represent current business requirements and nor are protecting critical assets appropriately.
“Firewalls are typically managed by a succession of administrators who create their own rules, which then accumulate over a period of years. This creates rule duplication, which can impinge on performance, but also brings risks such as the use default or open passwords.”
The first step in defense in depth is designing a corporate network segmentation policy which describes which departments, application, services and assets should reside on a separate network. Network segmentation will assure that threats are localized with minimal impact on the organization. NIST, ISO27002, and PCI emphasis the importance of network segmentation but does not mandate the requirement. At the same time PCI Standard committee emphasize in new standards that the compliance scope can be significantly minimized by placing all the related assets in the same segment. Network segmentation is not only a common sense in today’s market but also one of the most effective and economical control to implement, simply a great return on investment.
Network segmentation benefits:
o Improve network performance and reduce network congestion
o Contain attacks (viruses, worms, trojans, spam, adware) from overflowing into other networks.
o Improve security by ensuring that nodes are not visible to unauthorized networks. Reduce the size of broadcast domain
Basic idea behind defense in depth is to protect your crown jewel in multiple layers of defense, should one fail, another will provide crucial protection. Another important thing to remember is that we cannot defend everything, so our defense in depth approach should be asset centric rather than perimeter or technology centric. Perform a thorough risk assessment to find out your most important assets and apply the defense in depth approach to protect the confidentiality, integrity and availability of those critical assets. Examples of network segmentation include wireless network, where you place the wireless network users in their own segment behind a firewall with their own rule set. This rule set will help to contain the users on wireless network as well as any potential attacks on the organization. To get to the content of another segment in the network, the wireless users has to pass through all the layers of protection.
Defense in depth diagram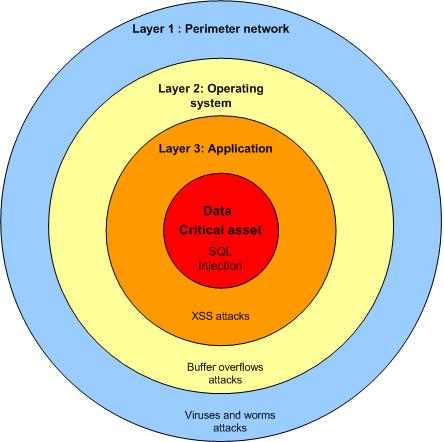
Different attacks will be handled by different layers. In the outer layer 1 will handle most of the network related attacks while the layer 2 will handle most of the script based attacks which target the operating system. Layer 3 will handle most of the application attacks which are complex and only utilized by skilled attackers. Layer 4 is your final frontier where you protect your crown jewel by moving many of the tools and techniques used at the perimeter closer to critical assets.
Related article
• Network segmentation is a common sense
Defense in depth
httpv://www.youtube.com/watch?v=zTJSMjYd9c4&feature=related