Cisco IOS XE is a robust and flexible operating system, optimized for the evolving landscape of enterprise networking and technology. It enables model-driven programmability, application hosting, and automated configuration management, thus simplifying many day-to-day tasks. IOS XE is integral in providing consistency across Cisco’s array of switching, routing, and wireless network devices.
THE VULNERABILITY: CVE-2023-20198
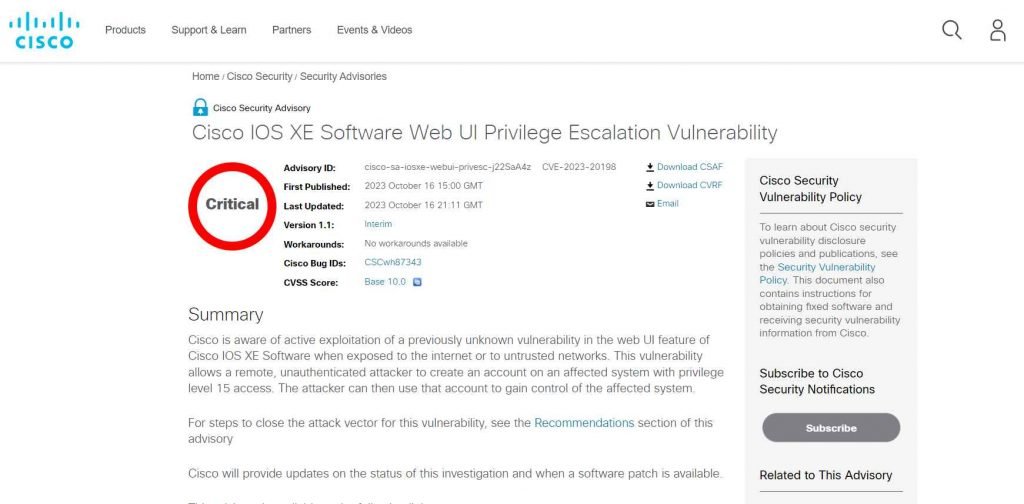
A new, critical zero-day vulnerability has emerged, labeled as CVE-2023-20198. This vulnerability, with a maximum severity rating of CVSS 10, predominantly affects devices running the Cisco IOS XE software and is currently without a patch, leaving systems vulnerable to potential exploits. The flaw can be exploited by an unauthenticated attacker to create a user account with the highest privilege level, leading to unauthorized system access.
Exploitation in the Wild
Attackers have already begun exploiting this vulnerability in the wild, utilizing it to deliver malicious implants. Organizations using the affected devices are advised to apply mitigation measures promptly to defend against these exploits.
Affected Devices and Systems
The vulnerability, CVE-2023-20198, affects all Cisco IOS XE devices that have the Web UI feature enabled, especially when exposed to the internet or untrusted networks. To ascertain if a system is vulnerable, administrators should:
- Utilize the command
show running-config | include ip http server|secure|activeto check for the presence ofip http serverorip http secure-servercommands in the global configuration. - Inspect the configuration for
ip http active-session-modules noneorip http secure-active-session-modules noneto determine if the vulnerability is exploitable over HTTP or HTTPS respectively.
Cisco’s Response
Cisco has acknowledged the vulnerability, confirming its presence in devices running the Cisco IOS XE software. The company provided steps to identify affected systems and noted the following Indicators of Compromise (IoCs):
- System logs containing messages indicating programmatic configuration by unfamiliar users, such as:
%SYS-5-CONFIG_P: Configured programmatically by process SEP_webui_wsma_http from console as user on line.%SEC_LOGIN-5-WEBLOGIN_SUCCESS: Login Success [user: user] [Source: source_IP_address].
- System logs containing messages about unknown file installation actions, like:
%WEBUI-6-INSTALL_OPERATION_INFO: User: username, Install Operation: ADD filename.
- Presence of an implant, checked by issuing the following command from a workstation with access to the affected system:
curl -k -X POST "https://systemip/webui/logoutconfirm.html?logon_hash=1", if a hexadecimal string is returned, the implant is present.
Cisco, alongside other cybersecurity firms like Tenable, has provided plugins to identify affected systems. While awaiting a patch, these plugins and the aforementioned checks can assist in identifying and mitigating unauthorized access attempts.
CVE-2023-20198 poses a significant threat to cybersecurity due to its maximum severity rating and the absence of a patch. Organizations using affected Cisco IOS XE devices should remain vigilant and apply necessary mitigation measures to safeguard their systems from potential exploits.
Zero Trust Architecture (Networking Technology: Security)
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory