Kali Linux turns 10 this year, and to celebrate, the Linux penetration testing distribution has added defensive security tools to its arsenal of open-source security tools.
It remains to be seen if Kali Purple will do for defensive open source security tools what Kali Linux has done for open source pentesting, but the addition of more than 100 open source tools for SIEM, incident response, intrusion detection and more should raise the profile of those defensive tools.
For now, Kali is primarily known for its roughly 600 open source pentesting tools, allowing pentesters to easily install a full range of offensive security tools.
In this article, we’ll focus primarily on how to use this powerful OS to run a pentest and mistakes to avoid. We’ll give you an overview of what can be achieved with Kali Linux using a short selection of pre-installed tools. While this guide serves as an introduction to common pentesting phases, with practical examples that highlight best practices, it’s not a substitution for a complete professional pentesting methodology.
- What is Kali Linux?
- Getting Started: How to Install Kali Linux
- Using Kali Linux: Finding Tools
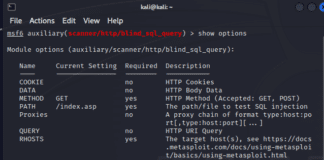
- Using a Pentesting Framework
- How To Use Kali Linux for Pentesting
- Open-source Alternatives to Kali Linux
- Kali Purple Edition
- Resources for Kali Linux Training
- Bottom Line: Kali Linux
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory



