Primary Account Number (PAN) is a
“12-digit or 19-digit numeric code embossed on the face side of a bank card, and also encoded in the Magnetic Stripe. The primary account number is a composite number containing: the Major Industry Identifier of the card issuer; an individual account identifier, which includes part of the account number; and a Check Digit or code that verifies the authenticity of the embossed account number.”
There are three pieces of information that are included in a financial transaction. Which are PAN, primary identification number (PIN) and card’ expiration date. The PAN is 12 to 19 digit number embossed on the front of the card.
For a successful transaction PIN, PAN and card expiration date are transmitted along with other information from the merchant, the merchant will transmit the information to merchant bank, the merchant bank will transmit the information to service provider (processor), the processor will transmit to the card issuer entity to authorize the transaction.
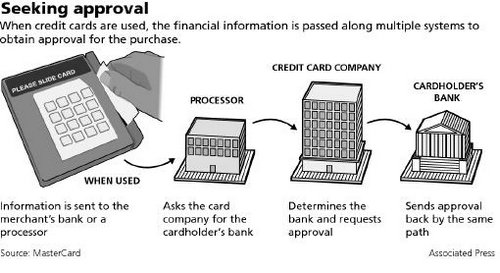
Credit card authorization process:
1) Creditholder swipes card at merchant. A request is sent to merchants bank
2) Merchants bank “asks” processor to determine the cardholder bank
3) Processing network finds cardholders bank and request approval for purchase
4) Cardholders bank approves purchase and generates a approval code
5) Processor sends an approval code merchants bank
6) Merchants bank sends approval code to merchant
7) Purchase is complete and cardholder receives a receipt
“Every time you swipe your credit card and wait for the transaction to be approved, sensitive data including your name and account number are ferried from store to bank through computer networks, each step a potential opening for hackers.”
The PIN is protected from malicious activity by encryption from POS terminal to all the way to the cardholder bank; However PAN is currently transmitted unencrypted. Valid PAN in wrong hands increase the possibility of credit card fraud. So the industry has decided that PAN must be protected. Below are the requirements for PAN protection.
Requirements for PAN protection
1. The PAN protection mechanism must support multiple source methods, including manual entry, magnetic swipe, chip, and NFC.
2. The PAN protection mechanism is encryption using an X9 or ISO approved algorithm.
3. Financial transaction message format and protocol standards must be modified to handle encrypted PAN data.
4. Transaction processing systems must be able to access some of the PAN digits.
5. For different transactions, encryption of the same PAN with a given encryption key should not predictably produce the same encrypted value.
6. For transaction routing by an intermediary between a sender and a receiver, the PAN must be translated from the sender’s encryption key to the receiver’s encryption key.
7. PAN translation must reveal some of the PAN digits for the intermediary to process the transaction.
8. PAN encryption keys must be changed periodically using X9 or ISO approved key management methods.
9. PAN encryption keys must only be used for their intended purpose.
10. Different encryption keys must be used for protection of PAN storage and transmission.
11. PAN encryption keys and the associated key encryption key (KEK) must be protected using X9 or ISO approved tamper resistant security modules (TRSM).
12. The customer must be advised in writing of the importance of the PAN with guidelines on the proper use of the card and the PAN.
PAN encryption is a major step forward toward protecting the card holder data.
Related articles by Zemanta
- New standard for encrypting card data in the works; backers include Heartland (computerworld.com)
- Credit card authorization process weakness (deurainfosec.com)
- PIN Crackers Nab Holy Grail of Bank-Card Security (wired.com)
Fake a Credit Card
httpv://www.youtube.com/watch?v=V3pElQD8UZg


![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=f0daa4e0-f026-4af4-8494-36325d4cff42)


