Chief Information Security Officers (CISOs) hold a critical and challenging role in today’s rapidly evolving cybersecurity landscape. Here are the common security challenges CISOs face…
As organizations increasingly rely on technology to drive their operations, CISOs face complex security challenges that demand their expertise and strategic decision-making.
These challenges arise from the constant emergence of sophisticated cyber threats, the need to protect sensitive data, and the ever-evolving regulatory landscape.
The role of a CISO requires balancing proactive risk mitigation with the ability to respond swiftly to incidents and breaches.
This article will delve into the top challenges CISOs face, including protecting digital assets, managing security incidents, ensuring compliance, dealing with insider threats, and the relentless pursuit of cyber resilience.
By understanding these challenges, CISOs can develop robust cybersecurity strategies and lead their organizations toward a secure and resilient future.
Who is a CISO?
Chief Information Security Officer (CISO) is a senior executive responsible for overseeing and administering an organization’s information security plan.
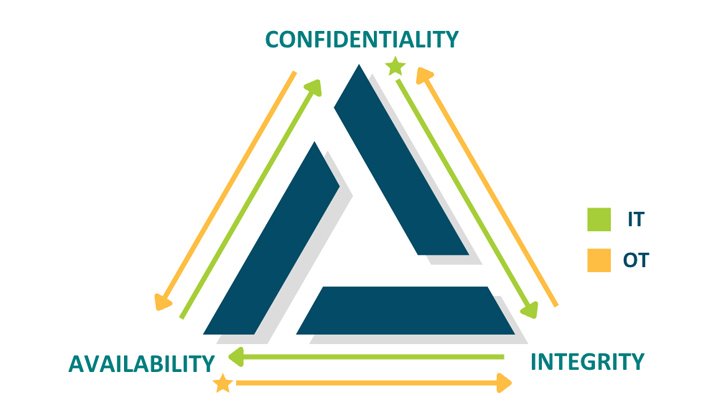
A CISO’s primary responsibility is safeguarding the confidentiality, availability, and integrity of an organization’s information assets and systems.
They are accountable for creating and enforcing strategies, policies, and procedures to defend against cyber threats, protect sensitive data, and mitigate security risks.
CISOs play a crucial role in maintaining an organization’s security posture by establishing and enforcing security standards, conducting risk assessments, and implementing appropriate security controls.
They collaborate with other executives, IT teams, and stakeholders to align security initiatives with business objectives and ensure that security measures are integrated into the organization’s operations.
In addition to their technical expertise, CISOs often engage in risk management, incident response planning, security awareness training, and compliance with regulatory requirements.
They stay updated on the latest cybersecurity trends, threats, and technologies to address emerging risks and implement appropriate security measures effectively.
The role of a CISO has become increasingly important as cyber threats evolve in complexity and frequency.
CISOs are responsible for safeguarding the organization’s sensitive information, maintaining the trust of customers and stakeholders, and ensuring business continuity in the face of cybersecurity challenges.
What are all the Roles and Responsibilities of CISO?
- Developing and Implementing Information Security Strategy: The CISO is responsible for developing and implementing an overarching information security strategy aligned with the organization’s business objectives. This includes setting security goals, defining security policies and procedures, and establishing risk management frameworks.
- Leading the Security Team: The CISO manages and provides leadership to the security team, including hiring, training, and supervising security personnel. They ensure the team has the necessary skills, resources, and support to carry out their responsibilities effectively.
- Overseeing Security Operations: The CISO oversees day-to-day security operations, including incident response, vulnerability management, threat intelligence, and security monitoring. They ensure appropriate controls, technologies, and processes are in place to protect the organization’s assets.
- Risk Management: The CISO is responsible for identifying and assessing security risks to the organization’s information systems and assets. They develop and implement risk management strategies to safeguard critical data and systems, including risk mitigation, transfer, and acceptance.
- Compliance and Regulatory Requirements: The CISO ensures that the organization complies with relevant security regulations, industry standards, and legal requirements. They stay updated on emerging regulations and ensure appropriate controls and processes are in place to meet compliance obligations.
- Security Incident Response: The CISO leads the organization’s response to security incidents, including data breaches, malware attacks, and other security breaches. They establish incident response plans, coordinate efforts, and collaborate with relevant stakeholders, such as legal, PR, and law enforcement agencies.
- Security Awareness and Training: The CISO promotes a culture of security awareness throughout the organization. They develop and deliver security awareness programs and training initiatives to educate employees on security best practices and minimize human-related security risks.
- Vendor and Third-Party Risk Management: The CISO assesses and manages security risks associated with third-party vendors and partners. They establish vendor security requirements, conduct due diligence, and monitor compliance with security standards and contractual obligations.
- Security Governance and Reporting: The CISO provides regular reports and updates on the organization’s security posture to executive management, board members, and other relevant stakeholders. They ensure that security metrics and key performance indicators (KPIs) are established to measure the effectiveness of security programs.
- Incident Investigation and Forensics: In the event of security incidents, the CISO oversees the investigation and forensic analysis to identify the root cause, assess the impact, and prevent future occurrences. As required, they collaborate with internal and external resources, such as forensic experts and law enforcement agencies.
GLOBAL CISO – STRATEGY, TACTICS, & LEADERSHIP: How to Succeed in InfoSec and CyberSecurity
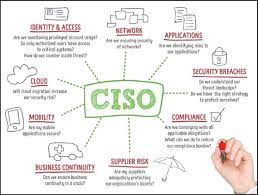
Security Challenges CISOs Face
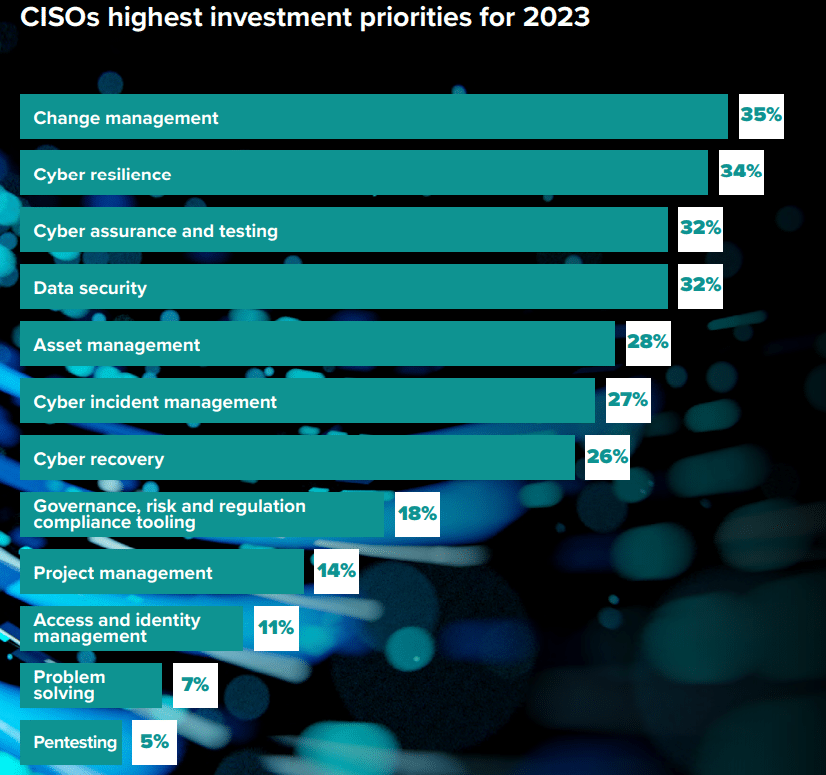
CISOs face various common security challenges as they strive to protect their organizations’ digital assets and information. Perimeter 81 Guide helps CISOs to prevent their network from being at Risk. Some of the key challenges they encounter include:
- Sophisticated Cyberattacks: CISOs must defend against increasingly sophisticated cyber threats, including advanced persistent threats (APTs), ransomware attacks, social engineering, and zero-day exploits. These attacks can bypass traditional security measures and require constant vigilance and adaptive security strategies.
- Insider Threats: CISOs need to address the risks posed by insiders, including employees, contractors, or partners who have authorized access to systems and data. Insider threats can involve accidental data breaches, negligence, or malicious intent, requiring a balance between enabling productivity and implementing controls to prevent unauthorized access or data leakage.
- Compliance and Regulatory Requirements: CISOs must ensure their organizations comply with industry-specific regulations, such as GDPR, HIPAA, PCI-DSS, or SOX, and evolving privacy laws. Navigating complex compliance requirements and maintaining a robust security posture to meet these standards can be a significant challenge.
- Cloud Security: As organizations increasingly adopt cloud services and infrastructure, CISOs must address the unique security challenges associated with cloud computing. This includes securing data stored in the cloud, managing access controls, and ensuring the security of cloud service providers (CSPs) and their environments.
- Security Skills Gap: CISOs often need more skilled cybersecurity professionals. The industry’s rapid growth and evolving threat landscape have resulted in high demand for cybersecurity talent, making recruiting and retaining qualified professionals challenging.
- Third-Party Risk: Organizations rely on third-party vendors and suppliers, introducing potential security risks. CISOs must assess the security posture of third parties, establish contractual security obligations, and monitor their adherence to security standards to mitigate the risk of breaches through these external connections.
- Security Awareness and Training: Human error remains a significant factor in cybersecurity incidents. CISOs must promote a strong security culture, provide regular training and awareness programs, and educate employees about cybersecurity best practices to minimize the risk of social engineering, phishing attacks, and other user-related vulnerabilities.
- Incident Response and Recovery: CISOs must develop and test robust incident response plans to manage and recover from security incidents effectively. This involves identifying and containing breaches, conducting forensic investigations, and implementing remediation measures to minimize the impact and prevent future incidents.
- Emerging Technologies: Adopting technologies like the Internet of Things (IoT), artificial intelligence (AI), and blockchain introduces new security challenges. CISOs must understand the security implications of these technologies, assess risks, and implement appropriate controls to protect against potential vulnerabilities and attacks.
- Budget and Resource Constraints: CISOs often face budget limitations and the need to prioritize security initiatives. Balancing the allocation of resources to address immediate security needs while investing in long-term security capabilities can be a significant challenge.
The Phantom CISO: Time to step out of the shadow
What are the Security Compliance CISO Should Follow
As a Chief Information Security Officer (CISO), there are several security compliance frameworks and regulations that you should consider following, depending on the nature of your organization and its operations. Here are some of the key security compliance frameworks and regulations:
- General Data Protection Regulation (GDPR): If your organization deals with the personal data of individuals in the European Union (EU), GDPR sets requirements for the protection, processing, and transfer of personal data. It includes principles for data minimization, consent, data breach notification, and the rights of individuals.
- Payment Card Industry Data Security Standard (PCI DSS): PCI DSS applies to organizations that handle credit card information. It sets requirements for securing payment card data, including network security, encryption, access controls, and regular vulnerability assessments.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA applies to organizations in the healthcare industry that handle protected health information (PHI). It establishes requirements for the privacy and security of PHI, including access controls, encryption, risk assessments, and breach notification.
- Sarbanes-Oxley Act (SOX): SOX applies to publicly traded companies in the United States. It sets requirements for financial reporting and establishes controls and processes to ensure the accuracy and integrity of financial statements. While not solely focused on security, it includes provisions for protecting financial data.
- National Institute of Standards and Technology (NIST) Cybersecurity Framework: The NIST Cybersecurity Framework provides guidelines and best practices for managing cybersecurity risks. It covers risk assessment, security controls, incident response, and continuous monitoring.
- ISO 27001: ISO 27001 is an international standard that provides a framework for establishing, implementing, maintaining, and continually improving an information security management system (ISMS). It covers various aspects of information security, including risk management, access controls, incident management, and security awareness.
- Federal Information Security Management Act (FISMA): FISMA applies to U.S. federal agencies and sets requirements for securing federal information and systems. It mandates risk assessments, security controls, incident response planning, and continuous monitoring.
Security Challenges CISOs Face to Manage Security Team
Managing a security team as a Chief Information Security Officer (CISO) requires effective leadership, communication, and coordination. Here are some key aspects to consider when managing a security team:
- Establish Clear Roles and Responsibilities: Clearly define the roles and responsibilities of each team member to ensure everyone understands their specific duties and areas of expertise. This clarity helps streamline operations and avoid confusion.
- Set Goals and Objectives: Define strategic goals and objectives for the security team aligned with the organization’s overall security strategy. Communicate these goals to the team and regularly track progress to ensure everyone is working towards the same objectives.
- Provide Guidance and Mentorship: Offer team members guidance, mentorship, and professional development opportunities. Encourage skill development, certifications, and staying up-to-date with the latest security trends and technologies—support team members in their career growth.
- Foster Collaboration and Communication: Promote a collaborative and open communication culture within the team. Encourage knowledge sharing, cross-functional collaboration, and effective communication channels. Regular team meetings, brainstorming sessions, and updates are valuable for aligning efforts.
- Support Decision-Making: Empower team members to make decisions within their areas of responsibility. Provide guidance and support when needed, but encourage autonomy and ownership in decision-making. Foster an environment where team members feel comfortable taking calculated risks.
- Establish Incident Response Procedures: Develop clear incident response procedures and ensure the team is well-prepared to handle security incidents effectively. Conduct regular drills, tabletop exercises, and simulations to test and improve the team’s incident response capabilities.
- Stay Informed and Adapt: Stay up-to-date with the latest security threats, industry trends, and best practices. Encourage continuous learning and professional development for the team. Adapt security strategies and measures as the threat landscape evolves.
- Collaborate with Other Departments: Work closely with other departments, such as IT, legal, HR, and executive management, to ensure security initiatives are aligned with business objectives and integrated into overall organizational operations. Build relationships and foster a culture of security awareness throughout the organization.
- Regularly Evaluate and Improve: Regularly evaluate the team’s performance, processes, and procedures. Collect feedback from team members and stakeholders to identify areas for improvement. Implement changes and adjustments as necessary to enhance the team’s effectiveness and efficiency.
- Lead by Example: Demonstrate strong leadership skills, integrity, and a commitment to security best practices. Lead by example in adhering to security policies and procedures. Encourage a positive and supportive work environment.
The CISO Evolution: Business Knowledge for Cybersecurity Executives
Final Thoughts
CISOs face many common security challenges as protectors of their organization’s digital assets and information.
From sophisticated cyberattacks and insider threats to compliance requirements and resource constraints, these challenges highlight the complex and evolving nature of the cybersecurity landscape.
CISOs must navigate these challenges by adopting a proactive and strategic approach to security, leveraging advanced technologies, fostering a strong security culture, and collaborating with stakeholders.
To overcome these challenges, CISOs must stay abreast of emerging threats, continuously evaluate and improve their security measures, and prioritize investments in critical security capabilities.
They must also foster strong partnerships with internal teams, third-party vendors, and industry peers to collectively address security challenges and share best practices.
While the security challenges CISOs face may seem daunting, they also present opportunities for innovation and growth.
By effectively addressing these challenges, CISOs can enhance their organizations’ security posture, safeguard critical assets, and instill confidence in customers and stakeholders.
Ultimately, the role of a CISO requires a comprehensive and adaptable approach to cybersecurity, where staying one step ahead of threats and continuously improving security measures are paramount.
By embracing these challenges, CISOs can help shape a secure and resilient future for their organizations in an increasingly interconnected and threat-filled digital landscape.

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory