For too long the cybersecurity world focused exclusively on information technology (IT), leaving operational technology (OT) to fend for itself. Traditionally, few industrial enterprises had dedicated cybersecurity leaders. Any security decisions that arose fell to the plant and factory managers, who are highly skilled technical experts in other areas but often lack cybersecurity training or knowledge.
In more recent years, an uptick in cyberattacks against industrial facilities and the trend of IT/OT convergence driven by Industry 4.0 have highlighted the vacuum of ownership around OT security. According to a new Fortinet report, most organizations are looking to Chief Information Security Officers (CISOs) to solve the problem.
Fortunately, CISOs are no strangers to change or difficult challenges. The position itself is less than 20 years old, yet in those two decades CISOs have navigated some of the most disruptive cybersecurity events that were truly watershed moments in technology.
Still, most CISOs have made their mark securing IT environments — and IT security strategies and tools rarely translate to an OT context. While the soft skills of collaboration and team-building will certainly help CISOs as they bring the factory floor into their realm of responsibility, they must also make a concentrated effort to understand the OT landscape’s unique topography and distinctive security challenges.
Safety over everything
The CIA triad — Confidentiality, Integrity & Availability — is a key concept in cybersecurity. Critically, IT and OT prioritize the elements of the triad differently — although safety is always the common denominator.
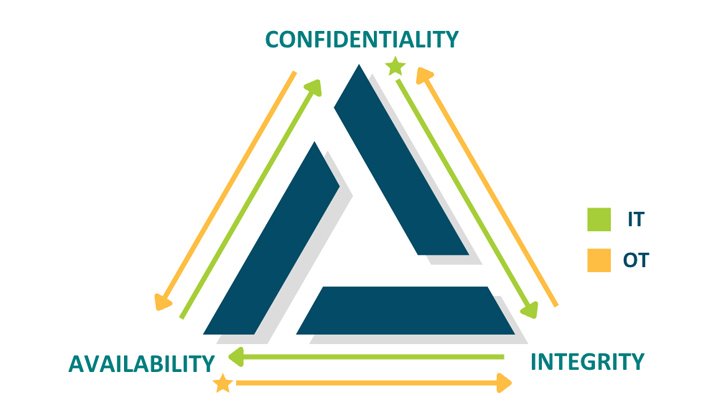
- In IT, safety means that data is protected through confidentiality. People get hurt when their sensitive, private data is compromised. For the enterprise, securing data saves them from breaches, fines, and reputational damage.
- In OT, safety means that cyber-physical systems are reliable and responsive. People get hurt when a blast furnace or an industrial boiler does not function properly. For the enterprise, availability keeps systems running on time down to the millisecond, which ensures productivity and profitability.
Somewhat ironically, the AIC triad of the OT world has resulted in systems and tools that prioritize physical safety but often come with few or no cybersecurity features at all. It will be the CISO’s responsibility to identify and implement security solutions that protect OT systems from cyberthreats without disrupting their operations.
Levels of segmentation
In both OT and IT, segmentation limits the network’s attack surface. In OT, the Purdue Model serves as a framework for how and why systems can and should communicate with each other.
In a highly simplified nutshell, the Purdue Model comprises five layers.
- Levels 4 and 5 are the outermost layers that include web and email servers, IT infrastructure, and users firewalling in remotely.
- Levels 2 and 3 are the operational layers that operate the software and applications that run OT environments.
- Levels 0 and 1 hold the devices, sensors, programmable logic controllers (PLCs), and distributed control systems (DCS) that do the actual work and must be protected from outside interference.
The purpose of these layers is to create both logical and physical separation between process levels. The closer you get to the cyber-physical operation of industrial systems like injectors, robotic arms, and industrial presses, the more checks and balances are in place to protect them.
While the concept of segmentation will not be new to CISOs, they will need to understand that the separation of zones is much stricter in OT environments and must be enforced at all times. Industrial enterprises adhere to the Purdue model or other similar frameworks to ensure safety and security and to meet many regulatory compliance mandates.
Downtime is not an option
In IT, downtime for upgrades and patches is no big deal, especially in a Software-as-a-Service (SaaS) world where new updates are released practically in real time.
Whether for safety or profit, OT systems are always up and running. They cannot be stopped or paused to download a new operating system or apply even a critical patch. Any process that requires downtime is simply a non-starter for the vast majority of OT systems. For this reason, CISOs should not be surprised to discover decades-old systems (likely running on software that reached its end-of-life date long ago) that still serve as a crucial piece of the operation.
The challenge facing CISOs will be to identify security controls that will not interrupt or interfere with delicate OT processes. The right solutions will “wrap” the existing OT infrastructure in a layer of security that protects critical processes without changing, complicating, or crowding them.
All access is “remote” access
Traditionally, OT systems have been protected through isolation. Now that organizations are connecting these environments to capitalize on Industry 4.0 or to allow easier access for contractors, all access must be monitored, controlled, and recorded.
- The IT environment is a digital place where business happens. Business users conduct their work and systems exchange data all within this space, day in and day out. To put it another way, humans are intended to actively participate in and make changes to the IT environment.
- OT systems and environments are built to run without human intervention — “set it and forget it.” Humans are meant to set them up and then let them run. Users do not remain logged into an OT environment all day the way business users would in an IT system.
In this context, anyone accessing the OT environment is effectively an outsider. Whether it is a vendor connecting remotely, a business user coming in through the IT network, or even an OT operator accessing the environment on-site, every connection comes from the outside. Recognizing this key point will help CISOs to understand that industrial secure remote access (I-SRA) tools should be used for all access scenarios, not only those that IT would consider to be “remote.”

IT tools do not (always) work for OT
Tools designed for IT hardly ever translate to OT.
- Basic functions like vulnerability scanning can interrupt OT processes and knock systems completely offline, and most devices do not have enough CPU/RAM to support endpoint security, anti-virus, or other agents.
- Most IT tools route traffic through the cloud. In OT, this can compromise availability and cannot support the numerous unconnected components common to OT environments.
- The life cycles of IT tools are typically much shorter than the life cycles of OT devices. Due to the always-up nature of OT environments, any tool that needs frequent patching, updates, or downtime is not applicable.
Forcing IT-designed tools into OT environments only adds complexity without addressing the fundamental security requirements and priorities of these environments. The sooner a CISO realizes that OT systems deserve security solutions designed for their distinctive needs, the faster they will be on their way to implementing the best tools and policies.
Soft skills are the keys to CISO success
Given that most cybersecurity leaders currently tend to come from IT security roles, it makes sense that many CISOs will have a (perhaps unconscious) bias toward IT philosophies, tools, and practices. To effectively secure OT environments, CISOs will need to become students again and lean on others to learn what they do not yet know.
The good news is that CISOs generally have a propensity to ask the right questions and seek support from the right experts while still pushing the envelope and demanding positive outcomes. At the end of the day, a CISO’s job is to lead people and teams of experts to accomplish the greater goal of securing the enterprise and enabling the business. Those willing to bridge the OT security divide through strong leadership and a willingness to learn should quickly find themselves on the road to success.
https://thehackernews.com/2023/06/5-things-cisos-need-to-know-about.html

InfoSec tools | InfoSec services | InfoSec books






