Ransomware attacks against manufacturers, utilities and other industrial companies were up 50% last year.
The pace and sophistication of cyberattacks against industrial companies are escalating rapidly, as administration officials warn that nation-states are heavily targeting U.S. critical infrastructure sectors.
Ransomware attacks against industrial companies increased by around 50% last year, according to an annual report from cybersecurity company Dragos published Tuesday, which tracked 905 strikes.
The Hanover, Md.-based company, which specializes in protecting systems used by heavy industries such as electric grids and wastewater plants, said it tracked 28% more groups specifically targeting “operational technology” last year than the year before. The term refers to the heavy machinery and industrial control systems used by manufacturing plants, water utilities and similar organizations, as opposed to information technology, which generally comprises software such as accounting and human resources systems. Among industrial companies, manufacturers were targeted most, said Rob Lee, chief executive of Dragos.
“It’s not so much that they’re OT experts, it’s just they know that they’re impacting the revenue-generating portions of those companies,” Lee said, “so the companies are willing to pay, and pay faster.”
Even when ransomware attacks target manufacturers’ corporate technology systems and not their operational technology machinery, there can be collateral damage for production, said Mark Orsi, president of the Manufacturing Information Sharing and Analysis Center, a nonprofit that coordinates the sharing of threat data among manufacturers.
“The vast majority of ransomware variants only target the IT infrastructure of an organization, but all too often the manufacturing plant floor operations are disrupted as a result of compromise to IT systems,” he said.
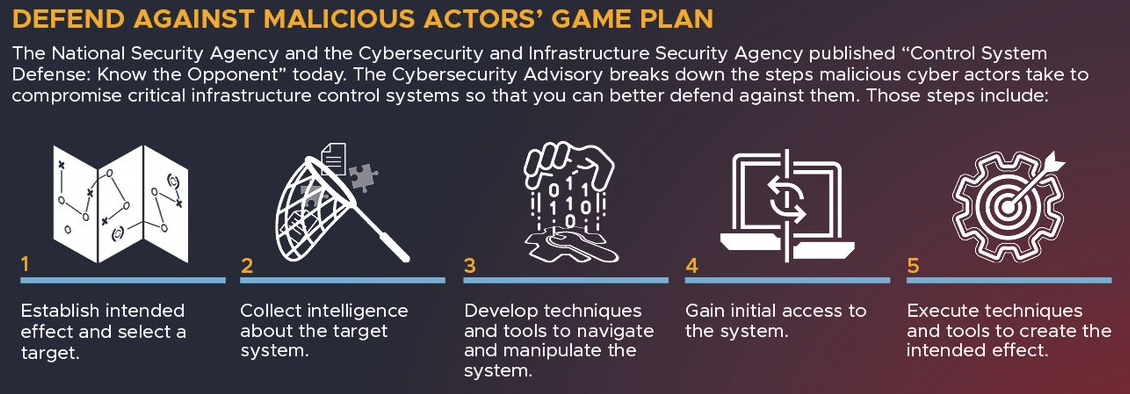
But ransomware is just the tip of the iceberg, say industry observers. The tools used by hackers to specifically target operations have become more sophisticated in recent years.
The emergence of Pipedream, for instance, a tool believed to have been authored by a nation-state team, has many concerned. Pipedream is able to target industrial systems across industries, and doesn’t rely on common attack methods, such as exploiting vulnerabilities in software.
“When Pipedream or Pipedream-like capabilities leak out into the community, they will be the Cobalt Strikes of OT. That’s the stuff that worries me,” Lee said during a call with reporters on Jan. 30, referring to a suite of cybersecurity tools, Cobalt Strike, developed for network defenders, which gave rise to a slew of malicious hacking tools when it was leaked.
U.S. officials have also ratcheted up warnings of attempts to infiltrate U.S. critical infrastructure. Christopher Wray, director of the Federal Bureau of Investigation, on Sunday said Chinese efforts to secure footholds in critical infrastructure networks are occurring at an unprecedented scale.
While Beijing routinely denies involvement in hacking, Wray’s comments follow a series of similar remarks made by Rob Joyce, cybersecurity director of the National Security Agency. Last month, Joyce told an FBI-sponsored conference that Chinese hackers are positioning themselves within those networks so as to be able to strike at U.S. infrastructure in the event of a conflict. The U.S. government in January said it disrupted one such operation, without specifying the types of infrastructure targeted.
“It’s not just an electric company issue, it’s not just a water issue or a manufacturing issue. I think it’s an issue that affects all of us,” said Jason Nations, director of enterprise security at Oklahoma City-based
OGE Energy, on the same call as Lee.
Critical infrastructure operators also face supply-chain security threats common to companies in many industries. German company
PSI Software, which said last week it had been the victim of a cyberattack, specified on Monday that it had been hit by ransomware, and took its systems offline to prevent further intrusions. PSI Software supplies software specialized for energy providers and other industrial processes. PSI didn’t respond to a request for comment.
One difficulty critical-infrastructure companies struggle with is finding cybersecurity experts to defend their networks. While there is a shortage of around 4 million corporate cyber professionals globally, according to trade association ISC2, some companies say it is especially difficult to hire people with both cyber skills and expertise in heavy machinery and industrial technology.

Practical Industrial Cybersecurity: ICS, Industry 4.0, and IIoT
Engineering-Grade OT Security: A manager’s guide
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory