MITRE and the US Cybersecurity and Infrastructure Security Agency (CISA) have collaborated to develop a new open source tool that simulates cyber-attacks on operational technology (OT). The product was published recently.
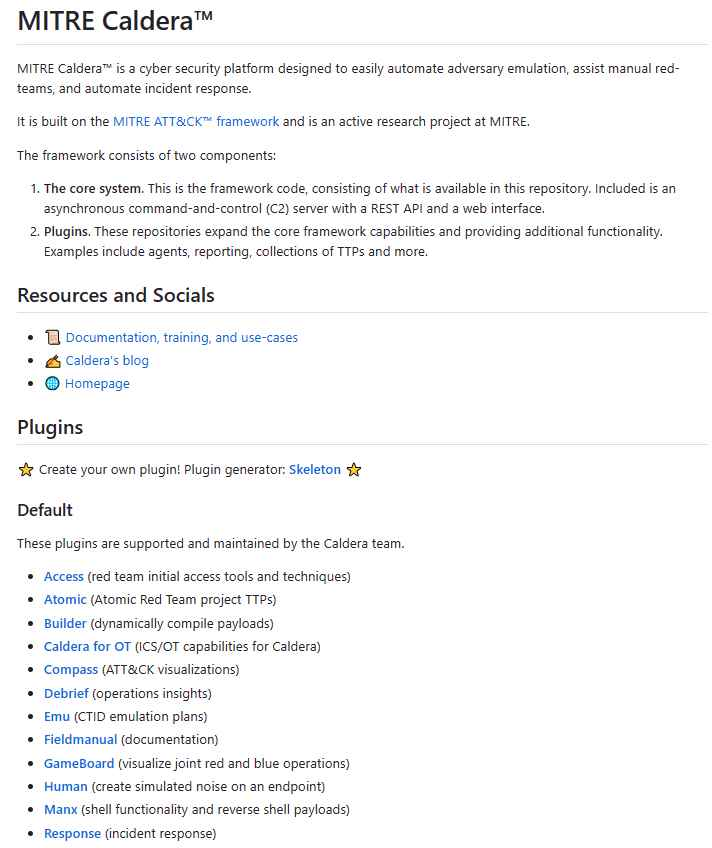
The MITRE Calder for OT is now accessible to the general public as an addition to the open-source Caldera platform that may be found on GitHub. This would make it possible for cybersecurity specialists who deal with industrial control systems (ICS) to carry out automated adversary simulation exercises. These exercises will have the goal of testing and improving their cyber defenses on a constant basis. In addition to this, this includes security inspections as well as exercises involving red, blue, and purple teams.
This Caldera extension for OT was created via a collaborative effort between CISA and the Homeland Security Systems Engineering and Development Institute (HSSEDI). HSSEDI is a research and development institution that is financed by the federal government and is maintained and run by MITRE on behalf of the Department of Homeland Security (DHS).
The program contributes to the goal of the federal government to strengthen the security of vital infrastructure that is dependent on OT. Some examples of such infrastructure are water and electricity. This objective was elaborated upon in the United States’ National Cybersecurity Strategy, which was published in March 2023, and in the Executive Order on Improving the Nation’s Cybersecurity, which was issued by President Biden in May 2021.
Work done by CISA and HSSEDI to automate opponent emulation simulations in CISA’s Control Environment Laboratory Resource (CELR) served as the foundation for the OT extension, which was developed upon that work. This made it possible to identify hostile strategies that may be implemented in Caldera.
The defensive mechanisms and testing capabilities of critical infrastructure systems are slated to get a boost from the use of these plugins.
These plugins, which are stored in the “caldera-ot” repository, are essential instruments for the protection of operational technology (OT) settings.
They are made available as Git submodules, which enables researchers and experts in the security industry to quickly and readily access them.
The purpose of these plugins is to facilitate enemy simulation inside the OT environment. This was the driving force behind their development.
Because of this, companies are given the ability to strengthen their security defenses and better prepare for possible attacks.
In addition to this, it is compatible with classic use cases for Caldera, such as rigorous testing of security mechanisms and operator training.
The move that has been taken by MITRE marks a major step forward in the continuing endeavor to secure critical infrastructure systems and to strengthen security within the OT sector.
A presentation titled “Emulating Adversary Actions in the Operational Environment with Caldera (TM) for OT” has also been made available by MITRE for individuals who are looking for further information of a more in-depth kind.
Users may apply the following command in order to install the whole collection of Caldera for OT plugins:
git clone https://github.com/mitre/caldera-ot.git –recursive
Individuals also have the option of configuring certain plugins on their own, which allows them to personalize their approach to OT security to meet their unique requirements.
At the moment, the following three important plugins are available:
- BACnet Catering to Building Automation and Control Networks (BACnet) protocol.
- DNP Addressing the Distributed Network Protocol 3 (DNP3).
- Modbus Supporting the Modbus protocol.
Open-Source OT Protocol Libraries That Are Unified And Exposed To Users. Caldera for OT plugins is a service provided by MITRE that aims to standardize and expose open-source OT protocol libraries, making them available for use as protocol-specific plugins. Each plugin comes with its own extensive documentation.
Cyber Defence Strategy using NIST and MITRE ATT&CK Frameworks
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory













