The NIST Gap Assessment Tool will cost-effectively assess your organization against the NIST SP 800-171 standard. It will help you to:
- Understand the NIST SP 800-171 requirements for storing, processing, and transmitting CUI (Controlled Unclassified Information)
- Quickly identify your NIST SP 800-171 compliance gaps
- Plan and prioritise your NIST SP 800-171 project to ensure data handling meets U.S. DoD (Department of Defense) requirements

Get started with your NIST SP 800-171 compliance project
The DoD requires U.S. contractors and their subcontractors to have an available assessment of their compliance with NIST SP 800-171. As part of a national movement to have a consistent approach to cybersecurity across the U.S., even organizations that store, process, or transmit unclassified and/or sensitive information must complete an assessment.
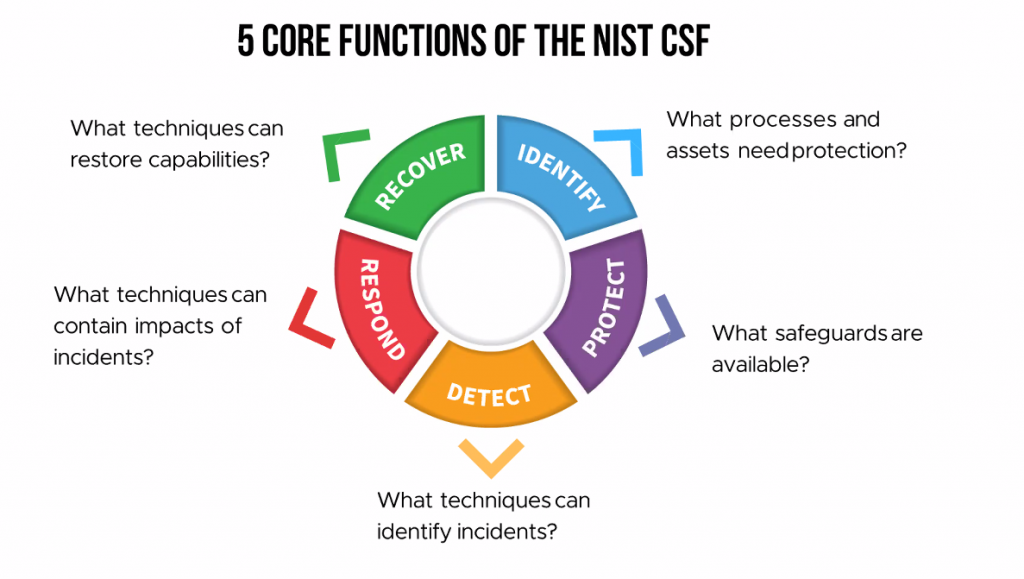
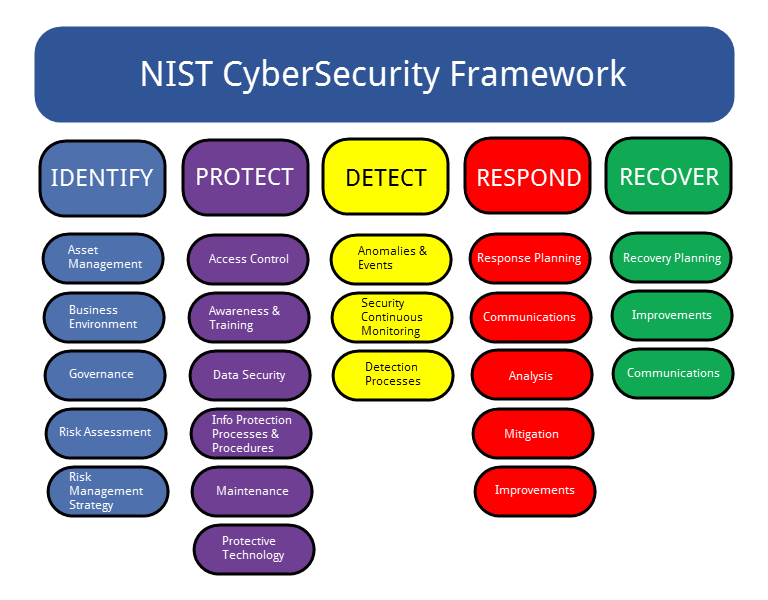
ITG NIST Gap Assessment Tool provides the assessment template you need to guide you through compliance with the DoD’s requirements for NIST SP 800-171. The tool lays out all 14 categories and 110 security controls from the Standard, in Excel format, so you can complete a full and easy-to-use assessment with concise data reporting.
What does the tool do?
- Features the following tabs: ‘Instructions’, ‘Summary’, and ‘Assessment and SSP (System Security Plan)’.
- The ‘Instructions’ tab provides an easy explanation of how to use the tool and assess your compliance project, so you can complete the process without hassle.
- The ‘Assessment and SSP’ tab shows all control numbers and requires you to complete your assessment of each control.
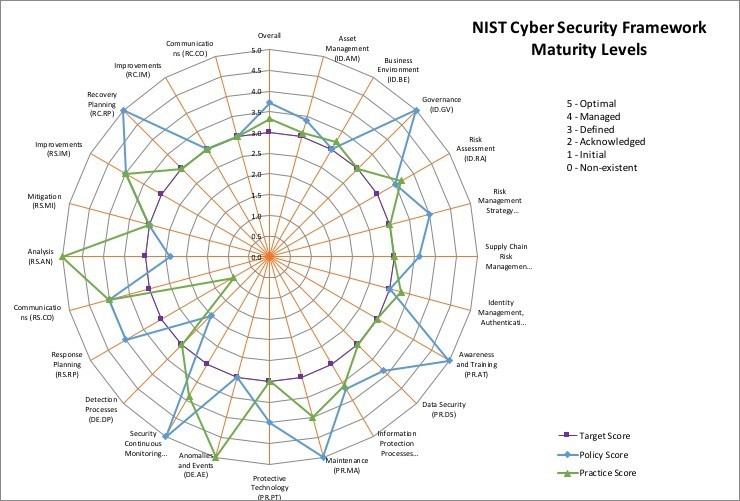
- Once you have completed the full assessment, the ‘Summary’ tab provides high-level graphs for each category and overall completion. Analysis includes an overall compliance score and shows the amount of security controls that are completed, ongoing, or not applied in your organization.
- The ‘Summary’ tab also provides clear direction for areas of development and how you should plan and prioritize your project effectively, so you can start the journey of providing a completed NIST SP 800-171 assessment to the DoD.
This NIST Gap Assessment Tool is designed for conducting a comprehensive compliance assessment. NIST SP 800-171 Assessment Tool.
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory