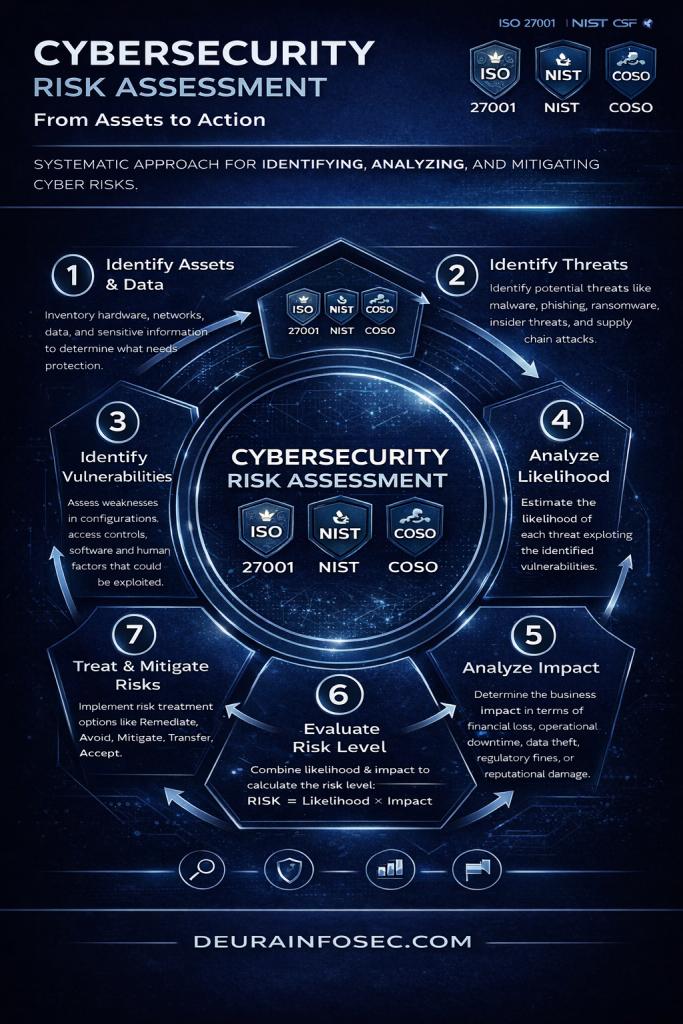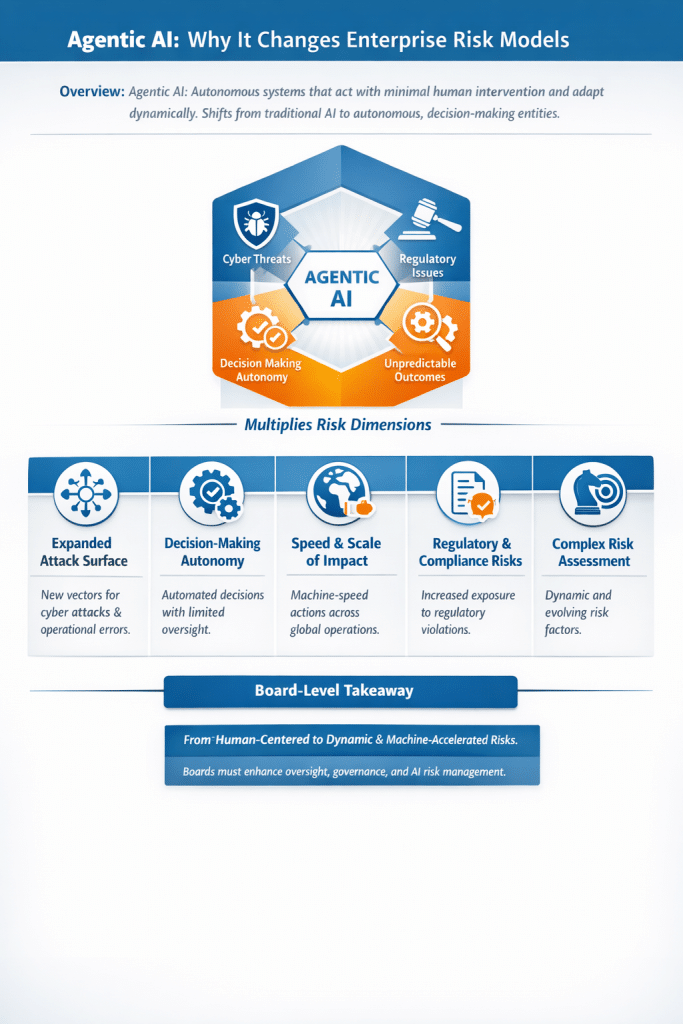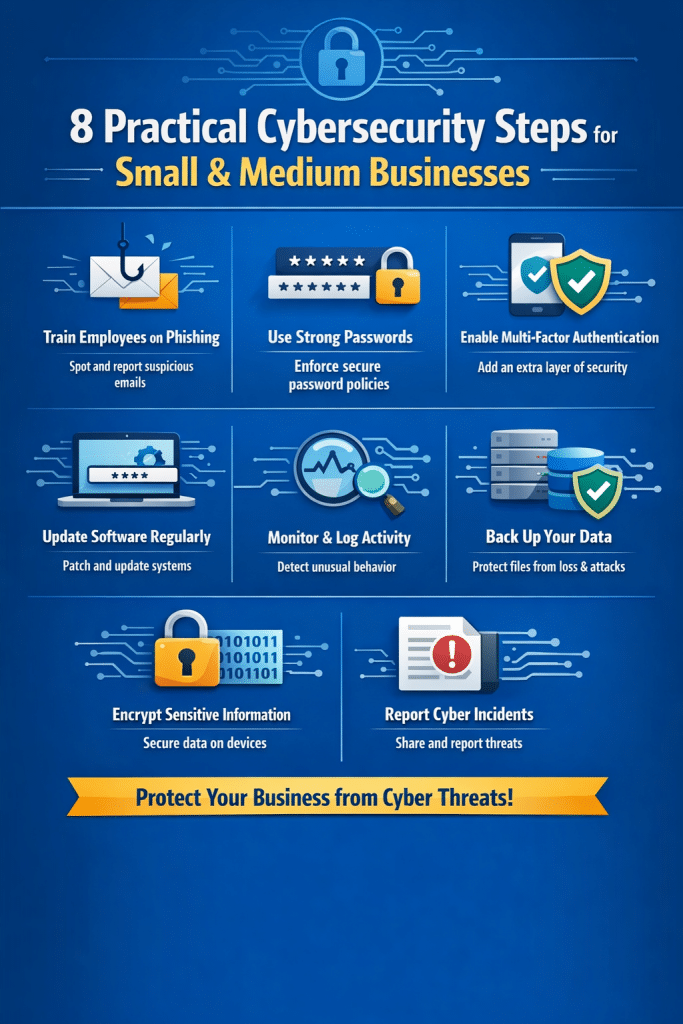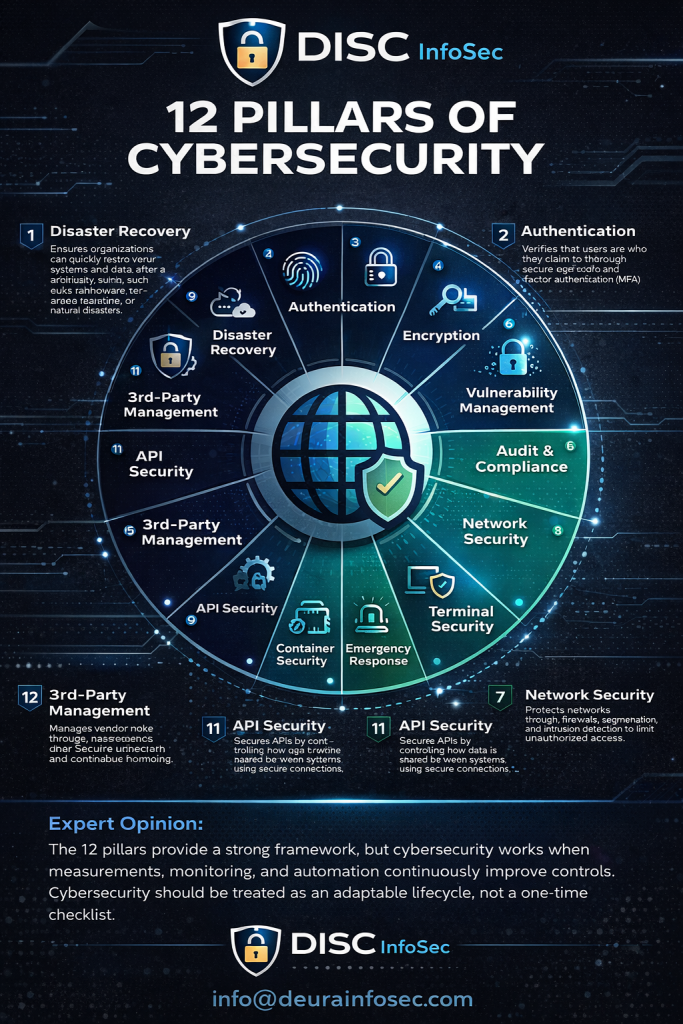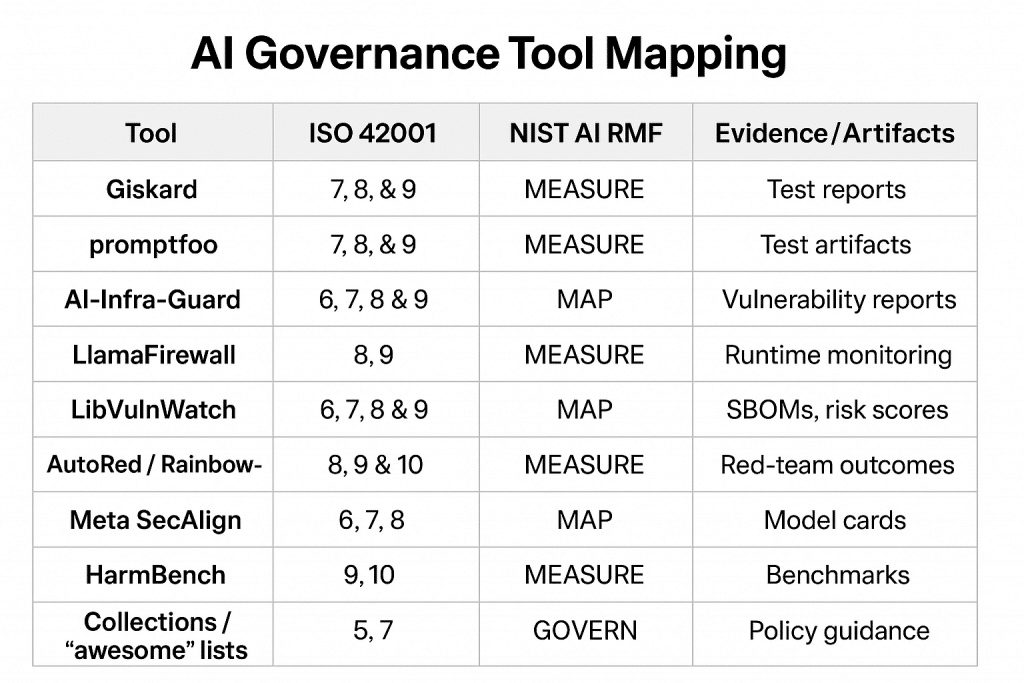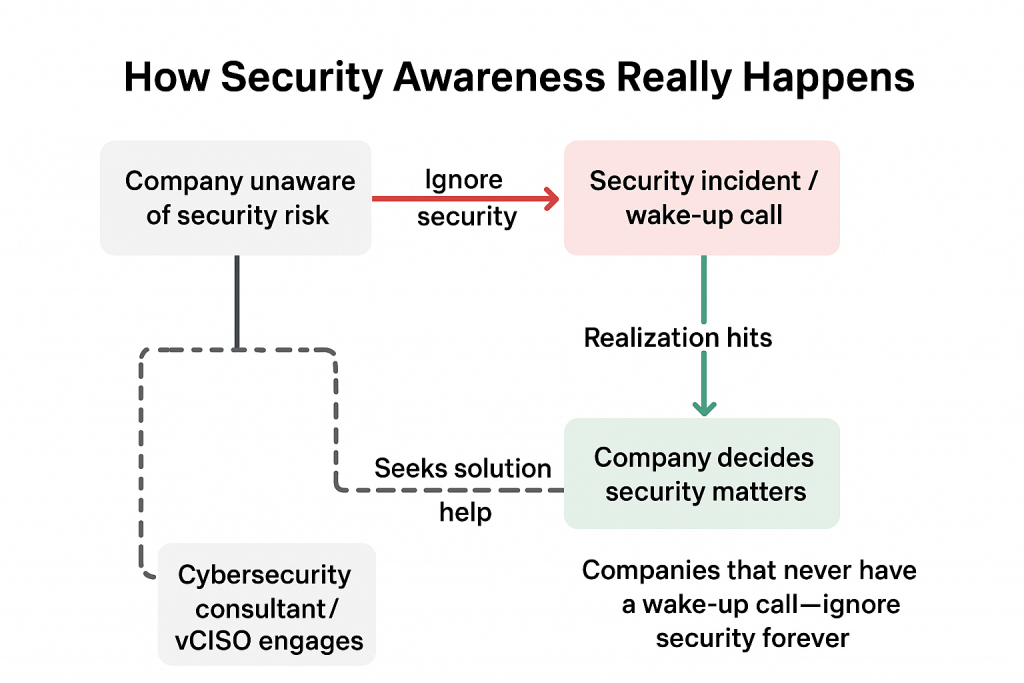
Structured summary of the difference between ISO 27001 and ISO 27002
- ISO 27001 is frequently misunderstood, and this misunderstanding is a major reason many organizations struggle even after achieving certification. The standard is often treated as a technical security guide, when in reality it is not designed to explain how to secure systems.
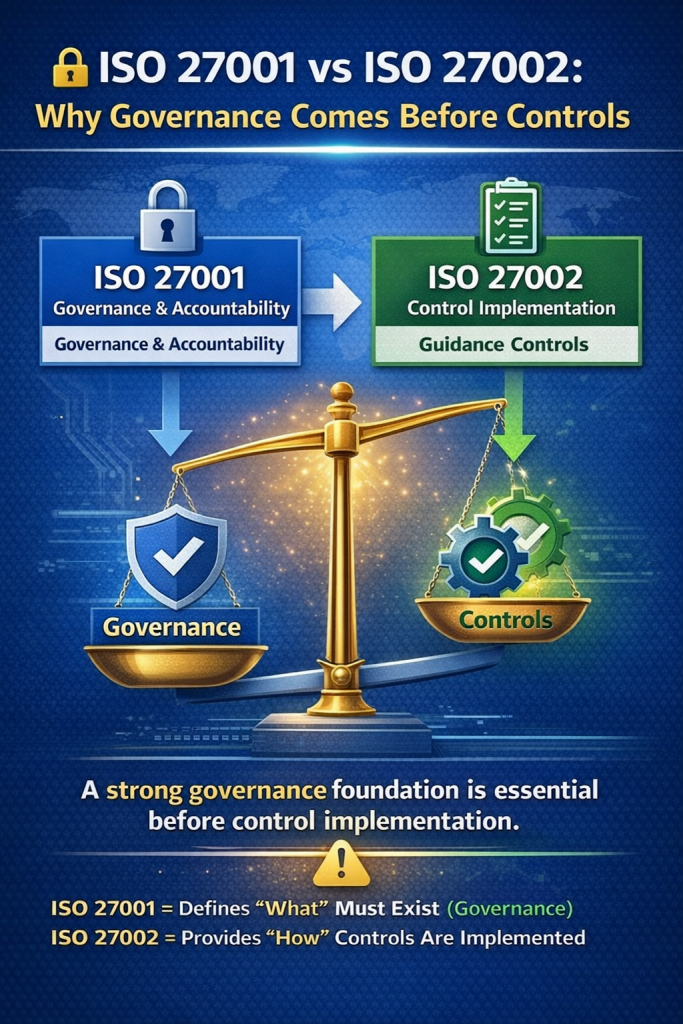
- At its core, ISO 27001 defines the management system for information security. It focuses on governance, leadership responsibility, risk ownership, and accountability rather than technical implementation details.
- The standard answers the question of what must exist in an organization: clear policies, defined roles, risk-based decision-making, and management oversight for information security.
- ISO 27002, on the other hand, plays a very different role. It is not a certification standard and does not make an organization compliant on its own.
- Instead, ISO 27002 provides practical guidance and best practices for implementing security controls. It explains how controls can be designed, deployed, and operated effectively.
- However, ISO 27002 only delivers value when strong governance already exists. Without the structure defined by ISO 27001, control guidance becomes fragmented and inconsistently applied.
- A useful way to think about the relationship is simple: ISO 27001 defines governance and accountability, while ISO 27002 supports control implementation and operational execution.
- In practice, many organizations make the mistake of deploying tools and controls first, without establishing clear ownership and risk accountability. This often leads to audit findings despite significant security investments.
- Controls rarely fail on their own. When controls break down, the root cause is usually weak governance, unclear responsibilities, or poor risk decision-making rather than technical shortcomings.
- When used together, ISO 27001 and ISO 27002 go beyond helping organizations pass audits. They strengthen risk management, improve audit outcomes, and build long-term trust with regulators, customers, and stakeholders.
My opinion:
The real difference between ISO 27001 and ISO 27002 is the difference between certification and security maturity. Organizations that chase controls without governance may pass short-term checks but remain fragile. True resilience comes when leadership owns risk, governance drives decisions, and controls are implemented as a consequence—not a substitute—for accountability.
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
- How AI Is Reshaping the Future of Cyber Risk Governance
- Risk Registers vs. GRC Charters: What Comes First?
- Stop Confusing LLMs, RAG, and AI Agents — Here’s the Real Difference
- From Security Leader to Business Enabler: The Modern CISO Role
- AI in Cybersecurity: Building Proactive and Adaptive Digital Defense