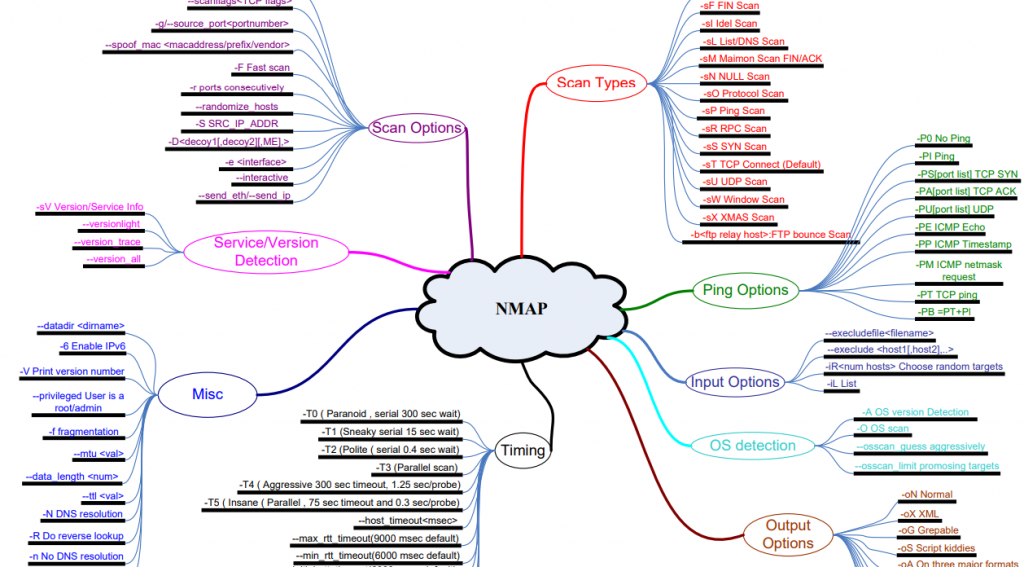
Mastering Nmap: A Comprehensive Guide to Network Discovery and Security
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Sep 03 2023
Aug 27 2023
Windows Forensics, include the process of conducting or performing forensic investigations of systems which run on Windows operating systems, It includes analysis of incident response, recovery, and auditing of equipment used in executing any criminal activity.

Malware Forensics Field Guide for Windows Systems: Digital Forensics Field Guides
Windows event log analysis and incident response guide
Diving Deeper Into Windows Event logs for Security Operation Center (SOC) – Guide
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Aug 26 2023
The cybersecurity insurance sector is experiencing swift expansion, with its value surging from around $13 billion in 2022 to a projected $84 billion by 2030, reflecting a robust 26% compound annual growth rate (CAGR). However, insurance providers are encountering challenges when it comes to accurately assessing the potential hazards associated with providing coverage for this category of risk.
Conventional actuarial models are ill-suited for an arena where exceptionally driven, innovative, and astute attackers are actively engaged in orchestrating events that lead to insurable incidents. Precisely gauging potential losses holds utmost importance in establishing customer premiums. However, despite a span of twenty years, there exists a substantial variance in loss ratios across insurance providers, ranging from a deficit of 0.5% to a surplus of 130.6%. The underwriting procedures lack the necessary robustness to effectively appraise these losses and set premiums that reflect a reasonable pricing.
The problem is with the nature of the threat. Cyber attackers escalate and adapt quickly, which undermines the historical-based models that insurance companies rely on. Attackers are continually shifting their maneuvers that identify victims, cause increasing loss, and rapidly shift to new areas of impact.
Denial of service attacks were once popular but were superseded by data breaches, which cause much more damage. Recently, attackers expanded their repertoire to include ransomware-style attacks that increased the insurable losses ever higher.
Trying to predict the cornerstone metrics for actuary modelers – the Annual Loss Expectancy and Annual Rate of Occurrence – with a high degree of accuracy is beyond the current capabilities of insurers. The industry currently conducts assessments for new clients to understand their cybersecurity posture to determine if they are insurable, what should be included/excluded from policies, and to calculate premiums. The current process is to weigh controls against best practices or peers to estimate the security posture of a policyholder.
However, these rudimentary practices are not delivering the necessary level of predictive accuracy.
The loss ratio for insurance firms has been volatile, in a world where getting the analysis wrong can be catastrophic. Variances and unpredictability make insurers nervous. At maximum, they want a 70% loss ratio to cover their payouts and expenses and, according to the National Association of Insurance Commissioners Report on the Cyber Insurance Market in 2021, nearly half of the top 20 insurers, representing 83% of the market, failed to achieve the desired loss ratio.
In response to failures to predict claims, insurers have been raising premiums to cover the risk gap. In Q4 2021 the renewals for premiums were up a staggering 34%. In Q4 2022 premiums continued to rise an additional 15%.
There are concerns that many customers will be priced out of the market and the insurance industry and left without a means of transferring risk. To the detriment of insurers, the companies may make their products so expensive that they undermine the tremendous market-growth opportunity. Additionally, upper limits for insurability and various exception clauses are being instituted, which diminish the overall value proposition for customers.
What is needed are better tools to predict cyber attacks and estimate losses. The current army of insurance actuaries has not delivered, but there is hope. It comes from the cyber risk community that looks to manage these ambiguous and chaotic risks by avoiding and minimizing losses.
These cybersecurity experts are motivated by optimizing limited resources to prevent or quickly undermine attacks. As part of that continuous exercise, there are opportunities to apply best practices to the insurance model to identify the most relevant aspects that include defensive postures (technology, behaviors, and processes) and understanding the relevant threat actors (targets, capabilities, and methods) to determine the residual risks.
The goal would be to develop a unified standard for qualifying for cyber insurance that would adapt to the rapid changes in the cyber landscape. More accurate methodologies will improve assessments to reduce insurers’ ambiguity so they may competitively price their offerings.
In the future, such calculations will be continuous and showcase how a company will benefit by properly managing security in alignment with shifting threats. This should bring down overall premium costs.
The next generation of cyber insurance will rise on the foundations of new risk analysis methodologies to be more accurate and sustain the mutual benefits offered by the insurance industry.

The Cyber Insurance Imperative, 2nd Edition: Updated for Today’s Challenging Risk Landscape
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Aug 25 2023
Cloud Hosting Provider Lost all Customer Data Following Ransomware Attack
There has been a cyber attack on two cloud hosting providers, namely CloudNordic and Azero Cloud, which Certiqa Holding owns. The cyberattack has resulted in complete data loss for all their customers.
The cloud attack was reportedly on Friday, April 18, 2023, at around 4 AM when CloudNordic and Azero cloud were exposed to a ransomware attack in which the threat actors shut down all the systems, including customer systems, e-mail systems, customers’ websites, and everything they gained access to.
Both companies mentioned that they could not and didn’t want to pay the ransom demanded by the threat actors. However, the IT teams of CloudNordic and Azero Cloud are working with external experts to get complete information about the attack and possible recreation.
Unfortunately, the companies could not recover or recreate any customer data, and they have lost every piece of data on their customers, mail servers, web servers, etc.
CloudNordic and Azero Cloud are highly affected by this cyber attack, and they have lost largely critical customer data but have re-established communications.
This means they have now deployed blank systems, including name servers, web servers, and mail servers. However, none of them contain any previous data.
The company has sorted out a way to restore the DNS administration interface that can enable users to get email and the web working again.
As per the report submitted to Cyber Security News, both companies attempted to migrate between data centers and had some infected systems before the migration, which the company did not know.
Nevertheless, some servers used to manage all the servers were still wired to the previous network. Threat actors gained access to the administration systems with this network misconfiguration, which paved their way toward the backup systems (both primary and secondary backup).
The attackers encrypted all the systems they had access to, including all the virtual machines. Large amounts of data were reported to have been encrypted by the ransomware, but there seems to be no evidence of data being copied.
Both companies claimed there seemed to be no evidence of a data breach and regretted the inconvenience caused to their customers.
With the rise in cyberattacks and cybercriminals, every organization must implement multiple security measures and monitor every piece of traffic to prevent these kinds of cyberattacks.

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Aug 24 2023
The OWASP Amass project performs network mapping of attack surfaces and external asset discovery using open-source information gathering and active reconnaissance techniques.

Osmedeus is a workflow engine for offensive security that allows you to build and run a reconnaissance system on a wide range of targets, including domains, URLs, CIDRs, and GitHub repositories. It was designed to establish a strong foundation and can adapt and function automatically to perform reconnaissance tasks.

PhoneInfoga is an advanced tool to scan international phone numbers. It allows you to gather basic information such as country, area, carrier, and line type, then use various techniques to find the VoIP provider or identify the owner. It works with a collection of scanners that must be configured for the tool to be effective.

Sherlock allows you to search social media accounts by username across social networks.

Shodan is a search engine for Internet-connected devices. Discover how internet intelligence can help you make better decisions. The entire Shodan platform (crawling, IP lookups, searching, and data streaming) is available to developers. Use their API to understand whether users connect from a VPN, whether the website you’re visiting has been compromised, and more.

Social Analyzer is an API, CLI, and web app for analyzing and finding a person’s profile across social media and websites. It includes different analysis and detection modules; you can choose which modules to use during the investigation process. The analysis and public extracted information from this OSINT tool could help investigate profiles related to suspicious or malicious activities such as cyberbullying, cyber grooming, cyberstalking, and spreading misinformation.

SpiderFoot is an OSINT automation tool. It integrates with just about every data source available and utilizes a range of methods for data analysis, making that data easy to navigate. SpiderFoot has an embedded web-server for providing a clean and intuitive web-based interface but can also be used completely via the command-line.

theHarvester is a simple to use, yet powerful tool designed to be used during the reconnaissance stage of a red team assessment or penetration test. It performs OSINT gathering to help determine a domain’s external threat landscape. The tool gathers names, emails, IPs, subdomains, and URLs by using multiple public resources.
OSINT Tools: A Practical Guide to Collection, Analysis, and Visualization
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Aug 22 2023

One of Mississippi’s largest hospital systems, Singing River Health System, suffered a cyberattack last week, leading to the shutdown of various internal services. The hospital system, which operates multiple hospitals and clinics along the Gulf Coast, detected unusual activity on its network and is cooperating with law enforcement. As a result of the attack, certain internal systems were taken offline to ensure their integrity during the investigation. The hospital’s IT security team is working to restore the offline systems, but the process is expected to take time. The hospital has not confirmed whether the attack involved ransomware or if a ransom will be paid. Patient services, including lab test results and radiology exams, are facing delays due to the attack. The incident highlights the ongoing challenges that hospitals face from cyberattacks, as this year has seen several healthcare institutions targeted by such attacks.
https://therecord.media/mississippi-hospital-system-takes-services-offline-after-cyberattack
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Aug 20 2023

https://www.theregister.com/2023/08/21/microsoft_dns_booboo_breaks_hotmail
Someone at Microsoft has some explaining to do after a messed up DNS record caused emails sent from Hotmail accounts using Microsoft’s Outlook service to be rejected and directed to spam folders starting on Thursday.
Late on Thursday evening, Hotmail users began reporting that some emails were being returned with errors related to Sender Policy Framework (SPF), and thus recipient email services were unable “to confirm that [a] message came from a trusted location.”
SPF, for those unfamiliar with it, is a method of outbound email authentication that helps avoid email spoofing, impersonation and phishing. If, for example, a service like Hotmail were to have one of its subdomains removed from the DNS TXT record that stores its SPF list, then recipient services may assume it’s junk.
And that appears to be just what happened.
Reddit users posting to the Sysadmin subreddit verified they were experiencing SPF issues with Hotmail. One user pulled up Hotmail’s SPF record and found that Redmond had made two changes: removing spf.protection.outlook.com from the record, and changing the SPF failure condition from soft to hard. That meant any suspicious messages from Hotmail should be rejected rather than just sent to spam.
Microsoft support forum advisors confirmed that the issue was known, which was further confirmed by a look at the Office service status page. Per Microsoft: “Some users may receive non-delivery reports when attempting to send emails from hotmail.com.”
At time of writing, the status page indicated that “a recent change to email authentication” was the potential root cause of the outage. Microsoft said it made a configuration change to remediate impact, but shortly after said the problem may have been worse than it appeared at first glance.
“We’ve identified that additional configuration entries are impacted, and we’re implementing further configuration changes to resolve the issue,” Microsoft said. Not long after that was posted, Microsoft indicated configuration changes were complete and the problem was fixed.
Microsoft didn’t respond to our questions about the incident, only saying the issue had been resolved.
Aug 16 2023
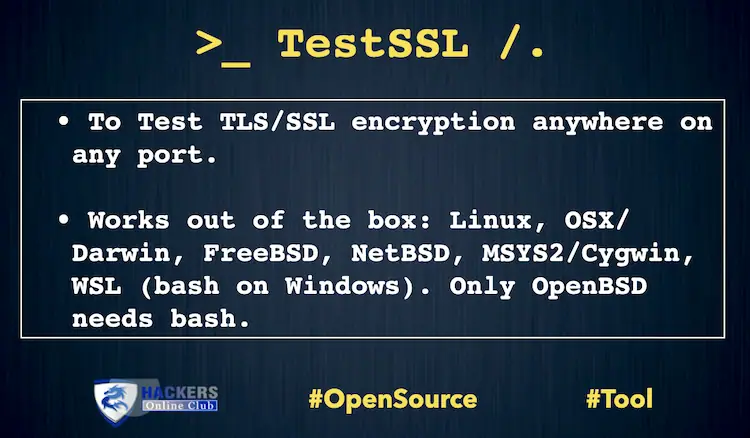
Testing TLS/SSL encryption anywhere on any port.
testssl.sh is a free command line tool, which checks a server’s service on any port for the support of TLS/SSL ciphers, protocols as well as some cryptography flaws on Linux servers, even it runs on macOS too.
It is also available in Kali Linux OS to test TLS/SSL encryption.
This software is free. You can use it under the terms of GPLv2, see LICENSE.
Attribution is important for the future of this project — also in the internet. Thus if you’re offering a scanner based on testssl.sh as a public and/or paid service in the internet you are strongly encouraged to mention to your audience that you’re using this program and where to get this program from. That helps us to get bugfixes, other feedback and more contributions.
Testssl.sh is working on every Linux/BSD distribution out of the box. Latest by 2.9dev most of the limitations of disabled features from the openssl client are gone due to bash-socket-based checks.
As a result you can also use e.g. LibreSSL or OpenSSL >= 1.1.1 . testssl.sh also works on other unixoid systems out of the box, supposed they have /bin/bash >= version 3.2 and standard tools like sed and awk installed. An implicit (silent) check for binaries is done when you start testssl.sh . System V needs probably to have GNU grep installed. MacOS X and Windows (using MSYS2, Cygwin or WSL) work too.
You can download testssl.sh branch 3.2 just by cloning this git repository:
git clone –depth 1 https://github.com/drwetter/testssl.sh.git
3.2 is now the latest branch which evolved from 3.1dev. It’s in the release candidate phase. For the former stable version help yourself by downloading the ZIP or tar.gz archive. Just cd to the directory created (=INSTALLDIR) and run it off there.
Testssl.sh has minimal requirements. As stated you don’t have to install or build anything. You can just run it from the pulled/cloned directory. Still if you don’t want to pull the GitHub repo to your directory of choice you can pull a container from dockerhub and run it:
docker run –rm -ti drwetter/testssl.sh <your_cmd_line>
Or if you have cloned this repo you also can just cd to the INSTALLDIR and run
docker build . -t imagefoo && docker run –rm -t imagefoo example.com
For more please consult Dockerfile.md.
Currently in the release candidate phase for version 3.2. Bigger features will be developed in a separate branch before merged into a 3.3dev to avoid hiccups or inconsistencies.
Version 3.0.X receives bugfixes, labeled as 3.0.1, 3.0.2 and so on. This will happen until 3.2 is released.
Support for 2.9.5 has been dropped. Supported is >= 3.0.x only.
InfoSec tools | InfoSec services | InfoSec books | Follow our blog
Aug 08 2023
Cloud misconfiguration — incorrect control settings applied to both hardware and software elements in the cloud — are threat vectors that amplify the risk of data breaches. A new report from cloud security vendor Qualys, authored by Travis Smith, vice president of the company’s Threat Research Unit lifts the lid on risk factors for three major cloud service providers.
Smith wrote that Qualys researchers, analyzing misconfiguration issues at Amazon Web Services, Microsoft Azure and Google Cloud Platform, found that within Azure, 99% of the disks are either not encrypted or aren’t using customer-managed keys that give users control of encryption keys that protect data in software as a service applications.
The study, which reviewed encryption, identity and access management and failures to monitor external-facing assets examined risks to unauthorized access due to:
Smith wrote that the company’s reachers found that 85% of the keys aren’t rotated, meaning automatic key rotation isn’t enabled. Amazon offers automatic key rotation — generating new cryptographic material — on a 365 day cycle for keys.
Qualys also reported that in GCP environments, 97.5% of virtual machine disks for critical virtual machines lack encryption using customer-supplied encryption keys.
Jump to:
Qualys found poor implementation levels of IAM in all three major providers:
Qualys noted that a common mistake by users across the three platforms is public exposure of data:
Recommendations by the firm included reviewing research by the Center for Internet Security including work Qualys participated in: mapping of individual controls to the MITRE ATT&CK tactics and techniques.
Qualys contributed to developing these CIS benchmarks for AWS, Azure and GCP. The benchmarks will help offer some valuable insight and context for defenders to better prioritize the hundreds of hardening controls available in cloud environments.
Qualys also looked at how firms are deploying controls to harden their cloud postures across the three major platforms, noting that privilege escalation (96.03%), initial access (84.97%) and discovery (84.97%) are passing at the highest rates.
Efforts to control attacks early are helping to ameliorate more harmful consequences further along the the kill chain:
Smith wrote that since crypto mining malware is a threat to cloud environments, organizations should consider mitigating such controls to reduce their organizational risk in the cloud.
“The lesson from these data points is that almost every organization needs to better monitor cloud configurations,” said Smith, adding that scans for CIS controls failed 34% of the time for AWS, 57% for Microsoft Azure and 60% for GCP (Figure A).
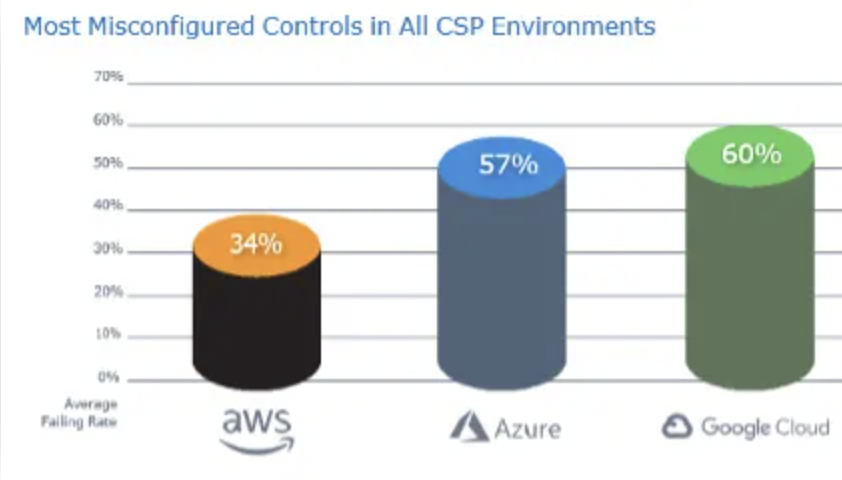
“Even if you believe your cloud configurations are in order, the data tells us that not regularly confirming status is a risky bet. Scan the configurations often and make sure the settings are correct. It takes just one slip-up to accidentally open your organization’s cloud to attackers,” wrote Smith.
InfoSec tools | InfoSec services | InfoSec books
Jul 25 2023

The lack of resources can pose significant risks to security in various contexts, including personal, organizational, and national security. Here are some ways in which a lack of resources can impact security:
To mitigate these risks, it’s crucial for individuals, organizations, and governments to recognize the importance of investing in security measures and resource allocation. Proactive planning and strategic allocation of resources can help strengthen security and reduce vulnerabilities in various domains.
InfoSec books | InfoSec tools | InfoSec services
Jul 15 2023
Article by Dejan Kosutic
The General Data Protection Regulation (GDPR) has already raised many controversies, and one of the biggest ones is certainly which documents are required. For example, often you see companies who think having a privacy policy and a consent form on their website is enough; however, this is only a small part of the documents that are required to be fully compliant with this new privacy regulation.
Therefore, we created a list of GDPR documentation requirements to help you find all mandatory documents at one place . Please note that the names of the documents are not prescribed by the GDPR, so you may use some other titles; you also have a possibility to merge some of these documents.
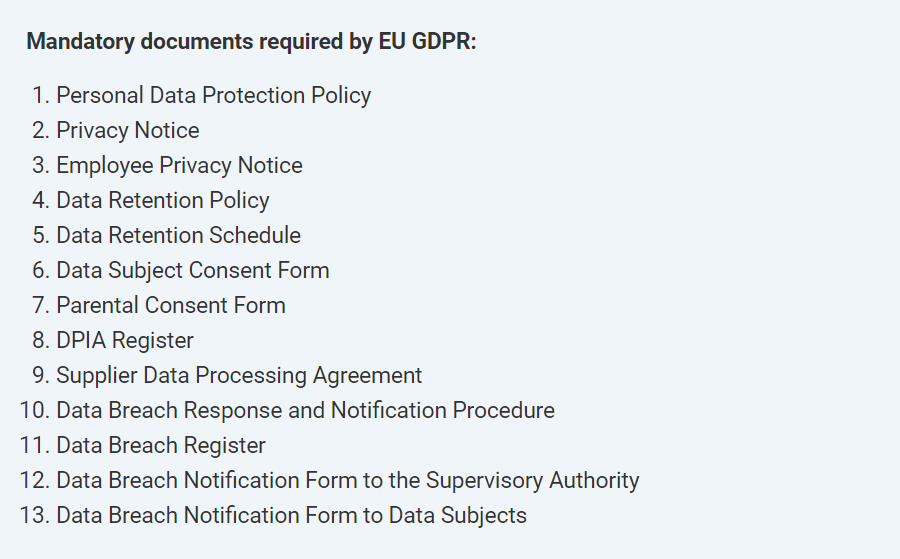
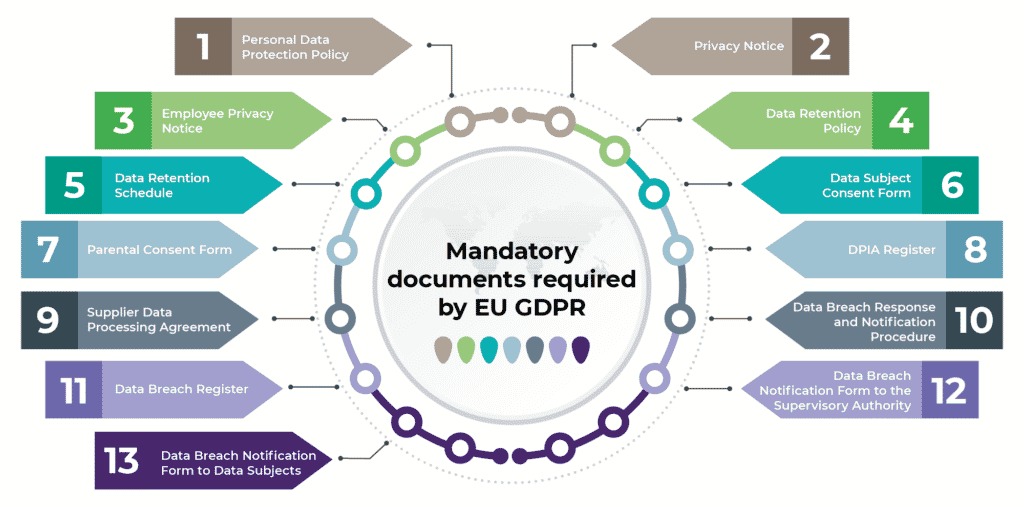
Here are the documents that you must have if you want to be fully GDPR compliant:
Jun 28 2023
Since April, Sudan has been rocked by fighting between two factions of its army. At first, the violence was contained in the capital city, Khartoum, but in recent days fighting has flared up in western Darfur, ground zero for a genocide that started back in 2003 and left hundreds of thousands dead.
Arab militiamen, known as janjaweed, or “devils on horseback,” were able to kill so many in Darfur in such a short time because the area is so remote — there was no one to witness the atrocities or hold the perpetrators to account, so they continued apace.
That’s what makes this latest conflict so different: Technology is allowing third-party observers to document human rights abuses in near real time thanks to, among other things, low-orbit satellites.
Researchers like Nathaniel Raymond, the executive director of Yale’s Humanitarian Research Lab, have been using satellites not just to document the violence, but with the right on-the-ground intelligence, to predict attacks before they happen.
The team recently documented evidence of war crimes in Ukraine with a report that provided both photographic and other proof that Russia was behind the systematic relocation of thousands of children from Ukraine into Russia and Russian-controlled regions of Ukraine.
Now Raymond and the team are working with the U.S. State Department to document human rights abuses in Sudan. It is a bit of a homecoming for them — they pioneered the use of satellite analysis and open-source intelligence in Darfur more than a decade ago and now they are back with better tools and a focus on ending a crisis that is decades in the making.
This conversation has been edited for length and clarity.
Click Here: Let’s start at the beginning. Can you explain how you got into this work?
https://therecord.media/tracking-atrocities-satellites-sudan-darfur-nathaniel-raymond-click-here

InfoSec tools | InfoSec services | InfoSec books
Jun 27 2023
By Chris Hall
This article gives some guidance on how to transition to ISO27001:2022 from the 2013 version.

This approach is tried and tested in that I have used it to successfully transition an organization to the new version. In the transition audit there were no nonconformities.
#iso27001 #iso27001transition
How to transition to the 2022 version of ISO27001

Jun 26 2023
Jun 24 2023
Exploitation, Detection, and Mitigation Strategies
The Complete Active Directory Security Handbook – by Picus Security
Download pdf

InfoSec tools | InfoSec services | InfoSec books

May 22 2023
Insider attacks often catch organizations by surprise because they’re tricky to spot.
Banking on reactive solutions like antivirus software or a patch management solution to avoid such attacks is not wise.
Understanding what contributes to the increasing number of insider threats and addressing these factors is the only way to secure your enterprise against such attacks.
An insider attack is often defined as an exploit by malicious intruders within an organization.
This type of attack usually targets insecure data. Insider threats might lurk within any company; in some industries, they can account for more than 70% of cyberattacks.
More often than not, insider attacks are neglected. Perhaps this is why they have been on a constant rise.
A survey by CA Technologies in 2018 found that about 90% of organizations feel vulnerable to insider attacks.
Organizations also feel that the data most vulnerable to insider attacks is sensitive personal information (49%), intellectual property (32%), employee data (31%), and privileged account information (52%).
Many insider attacks are associated with excessive access privileges. While it might be unpleasant or inconvenient not to trust employees, organizations must be vigilant.
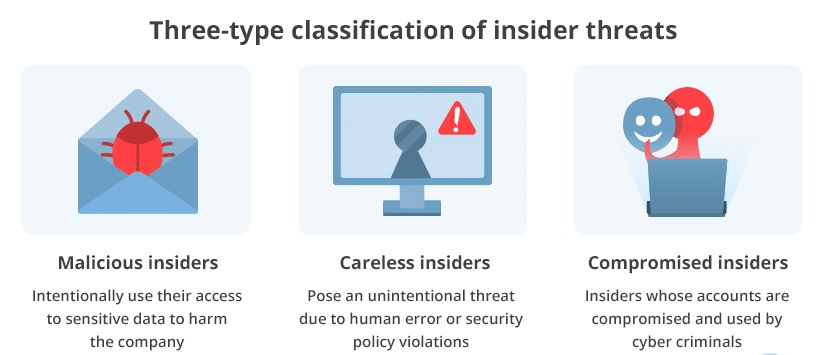
This can be accomplished by monitoring possible sources of cyberattacks. A big problem is that many companies are unaware of how to identify and combat insider threats.
Questions then arise: Where can you find the best network security tools to gain more knowledge on combating insider attacks? What security standards should you follow to stay within your industry’s security compliance requirements and protect your digital assets better? How do you differentiate between a malicious insider and a non-malicious one?
Here are some tell-tale signs you can monitor to avoid an insider attack. Be on the lookout for anyone who:
Once you have started monitoring, you can implement security measures to prevent attacks from occurring. We’ve put together a short list of solutions for curbing insider threats.
Zero Trust, a new cybersecurity buzzword, is a holistic approach for tightening network security by identifying and granting access, or “trust”.
No specific tool or software is associated with this approach, but organizations must follow certain principles to stay secure.
More users, applications, and servers and embracing various IoT devices expands your network perimeter.
How do you exert control and reduce your overall attack surface in such cases?
How can you ensure that the right access is granted to each user?
IT security at some organizations reflects the age-old castle-and-moat defense mentality that everything inside an organization’s perimeter should be trusted while everything outside should not.
This concept focuses on trust too much and tends to forget that we might know little about the intentions of those we deem “insiders.”
The remedy is Zero Trust, which revokes excessive access privileges of users and devices without proper identity authentication.
Privileged access management (PAM) means extending access rights to trusted individuals within an organization.
A privileged user has administrative access to critical systems and applications.
For example, if an IT admin can copy files from your PC to a memory stick, they are said to be privileged to access sensitive data within your network.
This also applies to accessing data via physical devices, logging in, and using different applications and accounts associated with the organization.
A privileged user with malicious intent might hijack files and demand your organization pay a ransom.
PAM takes some effort, but you can start simple. For instance, you can remove an employee’s access to the data associated with their previous role.
Consider an employee moving from finance to sales. In this case, the rights to access critical financial data must be revoked because we do not want to risk the organization’s financial security.
By implementing PAM, you can:
Not all insider attacks are intentional; some happen because of negligence or lack of awareness.
Organizations should make it mandatory for all their employees to undergo basic security and privacy awareness training sessions regularly.
Employees can also be quizzed on these sessions to make the training more effective.
Ensuring employees are acquainted with the cost consequences that negligence can cause the organization can help prevent unintentional insider threats significantly.
With so much to lose, it’s a wonder more companies aren’t taking steps to reduce their chance of suffering from an insider attack.
As mentioned earlier, no particular software or tool is behind the security approaches mentioned above.
Rather, your organization must address these aspects while developing a homegrown security solution or utilizing a similar service or product from a vendor.
By doing so, you can protect your organization from bad actors within or outside of your organization.
However, to specifically tackle the threat posed by insiders who regularly misuse their access credentials or bring malicious plug-and-play devices to work, we recommend looking into other security protocols, such as identity and access management and user behavior analytics, to prevent internal security mishaps.
Predicting Insider Attacks: Using Machine Learning & Artificial Intelligence Algorithms

InfoSec tools | InfoSec services | InfoSec books

May 15 2023
Today, API security company Salt Security announced it is now an Amazon Web Service (AWS) Web Application Firewall (WAF) Ready Partner. This service helps customers discover Partner solutions validated by AWS Partner Network (APN) Solutions Architects that integrate with AWS WAF to accelerate adoption of an enhanced and holistic security approach. AWS WAF is available to all AWS customers and all AWS Regions and can be deployed directly from the AWS console.
This partnership differentiates Salt Security as an APN member with a product that works with AWS WAF and is generally available for AWS customers. AWS WAF Ready Partners help customers quickly identify easy-to-deploy solutions that can help detect, mitigate, and analyse some of the most common internet threats and vulnerabilities.
Today, businesses of all shapes and sizes are focused on ensuring that websites and applications are protected from external threats that can lead to a loss of revenue, loss of customer trust, and loss of brand reputation. Implementing a WAF can be a challenging task that requires deep security experience that can be expensive and hard to find in-house. AWS WAF Ready Partners offer customers a simpler solution to deploying and maintaining their application layer security solution through easy-to-deploy solutions in order to detect, mitigate, and analyze some of the most common internet threats and vulnerabilities.
Gilad Barzilay, head of business development, Salt Security said: “As an AWS Software Path Partner and member of AWS ISV Accelerate Program, Salt is proud to expand our existing relationship with AWS by becoming an AWS WAF Ready Partner. Many of our customers rely on Salt to secure their APIs on AWS. By achieving these designations, we make it easier and faster for businesses to protect the APIs running on their AWS environments. Our customers benefit from our unique cloud-scale API data lake architecture, which applies AI and ML for API discovery and threat protection.”
“Deploying the Salt platform took almost no effort,” said Jason Weitzman, senior application security engineer at Xolv Technology Solutions. “It integrated quickly with our existing Cloudflare, AWS, Jira and other systems. It also started identifying errors and delivering insights on how to craft better APIs within minutes.”
The Salt platform deploys out of band, to avoid any interference with application performance or availability. The Salt platform pairs with AWS WAF as an API traffic collection point and to block detected attackers. To support the seamless integration and deployment of solutions such as the Salt platform, AWS established the AWS Service Ready Program. The program helps customers identify solutions integrated with AWS services and spend less time evaluating new tools, and more time scaling their use of solutions that are integrated with AWS services.
APIs are a hot topic among cybersecurity professionals and C-suites at the moment due to their increasingly vital business roles. Earlier this year Salt released a new API report that showed a 400% Increase in Attackers, demonstrating the prevalence.

Security of services hosted in the Cloud with Le WAF: Web Application Firewall
InfoSec tools | InfoSec services | InfoSec books

May 11 2023
The threat is coming from inside the supply chain
BLACK HAT ASIA Threat groups have infected millions of Androids worldwide with malicious firmware before the devices have even been shipped from their manufacturers, according to Trend Micro researchers at Black Hat Asia.
The mainly mobile devices, but also smartwatches, TVs and more, have their manufacturing outsourced to an original equipment manufacturer (OEM), a process the researchers say makes them easily infiltrated.
“What is the easiest way to infect millions of devices?” posed senior threat researcher Fyodor Yarochkin, speaking alongside colleague Zhengyu Dong.
He compared infiltrating devices at such an early stage of their life cycle to a tree absorbing liquid: you put the infection at the root, and it gets distributed everywhere, out to every single limb and leaf.
The malware installation technique began as the price of mobile phone firmware dropped. Competition between firmware distributors became so furious that eventually the providers could not charge money for their product.
“But of course there’s no free stuff,” said Yarochkin, who explained that the firmware started to come with an undesirable feature – silent plugins. The team manually analyzed dozens of firmware images looking for malicious software. They found over 80 different plugins, although many of those were not widely distributed.
The plugins that were the most impactful were those that had built a business model around them and were selling underground services, marketing them out in the open on places like Facebook, in blog posts, and on YouTube.
The objective of the malware is to steal info or make money from information collected or delivered.
The malware turns the devices into proxies which are used to steal and sell SMS messages, social media and online messaging accounts, and used as monetization opportunities via adverts and click fraud.
One type of plugin, proxy plugins, allow the criminal to rent out devices for up to around five minutes at a time. For example, those renting the control of the device could acquire data on keystrokes, geographical location, IP address and more.
“The user of the proxy will be able to use someone else’s phone for a period of 1200 seconds as an exit node,” said Yarochkin. He also said the team found a Facebook cookie plugin that was used to harvest activity from the Facebook app.
Through telemetry data, the researchers estimated that at least millions of infected devices exist globally, but are centralized in Southeast Asia and Eastern Europe. A statistic self-reported by the criminals themselves, said the researchers, was around 8.9 million.
As for where the threats are coming from, the duo wouldn’t say specifically, although the word “China” showed up multiple times in the presentation, including in an origin story related to the development of the dodgy firmware. Yarochkin said the audience should consider where most of the world’s OEMs are located and make their own deductions.
“Even though we possibly might know the people who build the infrastructure for this business, its difficult to pinpoint how exactly the this infection gets put into this mobile phone because we don’t know for sure at what moment it got into the supply chain,“ said Yarochkin.
The team confirmed the malware was found in the phones of at least 10 different vendors, but that there was possibly around 40 more affected. For those seeking to avoid infected mobile phones, they could go some way of protecting themselves by going high end.
“Big brands like Samsung, like Google took care of their supply chain security relatively well, but for threat actors, this is still a very lucrative market,” said Yarochkin. ®
https://www.theregister.com/2023/05/11/bh_asia_mobile_phones/
InfoSec tools | InfoSec services | InfoSec books

May 09 2023
Trading or investing in cryptocurrencies can be highly lucrative. But the extreme price movements often discourage beginners to buy cryptocurrencies. However, with a carefully charted risk management plan, it is possible to make gains and minimize losses.
Here are the 7 golden rules of risk management for cryptocurrency traders
One of the effective risk management strategies for a cryptocurrency trader is to diversify your portfolio. You must ensure that you put only some of the investments in a few carefully chosen cryptocurrencies, instead of putting all your money in just one. For instance, you might consider buying Kusama along with Bitcoin or Ethereum, after checking the Kusama Price on that day.
A stop-loss order, in simple terms, is a preset order that will sell a part or all of the holdings automatically if the cryptocurrency price drops to some extent. It works like a safety net that helps in minimizing the loss for you, provided the market moves against you. When you set stop loss orders, you can reduce the losses and protect the investments. You need to put stop-loss orders at the proper levels.
Position sizing plays a crucial role in risk management. Regarding position sizing, you need to allocate some specific trade amount in your portfolio. You have to use the correct position size to manage the risk well. You need to ensure that you do not take a lot of trouble on a single trade, as it can lead to a lot of losses. In simple terms, you need to raise only one to 2% of the complete portfolio on one trade, so even if there is a loss, it will not impact your portfolio to a great extent.
When you have a clear profit goal at the back of your mind, you can manage risk to a great extent. You need to ensure realistic profit goals depending on the market trends and technical analysis. Avoid getting greedy when you are in the grade you set unrealistic high profits, which can lead to risky trading decisions. You have to ensure that you are disciplined, stick to the profit target, and lock in the gain at the right time.
Information and market sentiment play a crucial role in the cryptocurrency market, so you must have all the information regarding the trade and prices. When you have the correct information on the latest developments and news, you can trade well. To have the correct information, you must do some research on all the cryptocurrencies that you are trading, like the technology market capitalization trading volume and historical price performance.
Leverage makes it very easy for you to trade with a considerable capital amount, and it is eventually more than what you have. Leverage is both a boon and, of course, it can lead to huge profits and losses at the same time.
Even though leverage can help in improving your potential income, it can also increase the risk of losses to a great extent. You need to use leverage with a lot of care and thoroughly understand all the risks involved before you consider implementing it in your strategy.
Lastly, you need to ensure that you keep your leverage high and have the right stop-loss orders whenever you are trading with leverage. This will help you in managing your risk well.
Emotions like fear or greed can have a significant impact on your decision-making process, and they can also lead to impulsive trading decisions. This can lead to risks unnecessarily, so it is essential for you to keep a check on your emotions and maintain a rational approach while you are trading. You need to ensure that you avoid making any impulsive decisions based on fear or greed and stick to your risk management plan. It is OK to take a step back and reconsider your emotions when you feel that your emotions are taking over.
In short, risk management is a critical element of cryptocurrency trading, considering the volatile nature of the market. When you follow these rules for risk management, you can indeed reduce your potential losses.

Cryptocurrency Risk Management
InfoSec tools | InfoSec services | InfoSec books

Apr 16 2023