by Mike Holcomb

Checkout previous OSINT posts here
InfoSec and Compliance – With 20 years of blogging experience, DISC InfoSec blog is dedicated to providing trusted insights and practical solutions for professionals and organizations navigating the evolving cybersecurity landscape. From cutting-edge threats to compliance strategies, this blog is your reliable resource for staying informed and secure. Dive into the content, connect with the community, and elevate your InfoSec expertise!
Nov 27 2024
Sep 10 2024
The article lists 33 open-source cybersecurity tools designed to improve security for various platforms, including Linux, Windows, and macOS. These tools cover a wide range of security needs, from identity management and encryption to vulnerability scanning, threat intelligence, and forensic analysis. Examples include Authentik for identity management, Grype for vulnerability scanning, and MISP for threat intelligence sharing. These solutions offer flexibility and transparency, enabling organizations to customize their security infrastructure.
Open-source cybersecurity tools provide transparency and flexibility, allowing users to examine and customize the source code to fit specific security needs. These tools make cybersecurity accessible to a broader range of organizations and individuals.
In this article, you will find a list of 33 open-source cybersecurity tools for Linux, Windows, and macOS that you should consider to enhance protection and stay ahead of potential threats.
For more, visit Help Net Security

OSINT Techniques: Resources for Uncovering Online Information
Operator Handbook: Red Team + OSINT + Blue Team Reference
AI and OSINT: The Future of Cyber Investigation
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot
Apr 04 2024
The framework conducts reconnaissance on active assets and completes its operation with a scan for vulnerabilities, secrets, misconfigurations, and potential phishing domains, utilizing open-source and proprietary tools.
Some of the features that make Mantis stand out are:
“Last year, we explored open-source frameworks our organization can use to monitor assets. We wanted to set up an asset discovery framework that allows us to add custom scripts, enable or disable tools to run based on configs, scale, and deploy the framework across a cluster of VMs. We also wanted to find a way to ingest domains from DNS services into our databases. This led us to create Mantis, an asset discovery framework that could help bug bounty hunters as well as security teams,” Prateek Thakare, lead developer of Mantis, told Help Net Security.
Mantis is CPU intensive, so it’s advisable to run it on a dedicated virtual machine.
“We are planning to have our dashboard making it easier to view and monitor the assets. We will also work on improvising the discovery, recon, and scan process by adding new tools and custom scripts,” Thakare concluded.
Mantis is available for free on GitHub.

The OSINT Handbook: A practical guide to gathering and analyzing online information

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot
Mar 12 2024
CloudGrappler is an innovative open-source tool designed to detect the presence of notorious threat actors in cloud environments.
This tool is a beacon of hope for security teams struggling to keep pace with the sophisticated tactics of groups like LUCR-3, also known as Scattered Spider.
CloudGrappler leverages the power of CloudGrep, a tool developed by Cado Security, to offer high-fidelity, single-event detections of activities associated with well-known threat actors in popular cloud platforms such as AWS and Azure.
It acts as a cyber detective, sifting through the vast amounts of data in cloud environments to identify suspicious and malicious activities that often go unnoticed.
CloudGrappler includes several components designed to streamline the threat detection process:
It is based on a subset of activity from Permiso’s library of hundreds of detections, and it helps organizations detect threats targeting their cloud infrastructure.
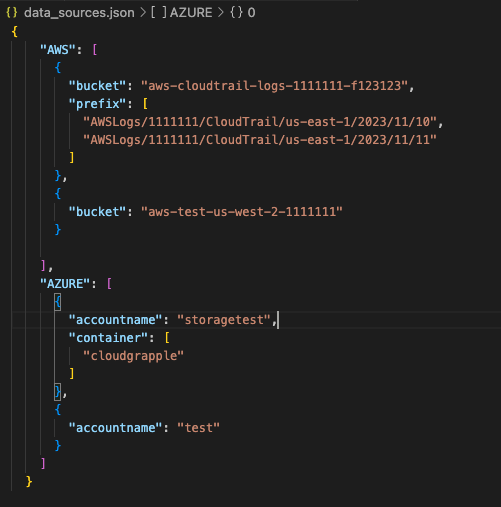
CloudGrappler is not just about detecting suspicious activities. it also provides valuable threat intelligence to help security professionals understand the risks in their environment and develop targeted response strategies.
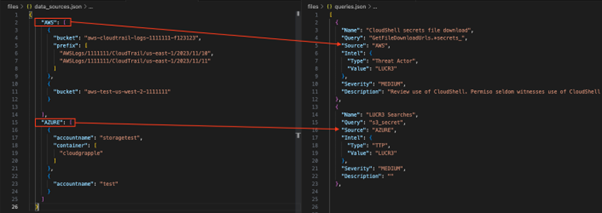
The tool’s output includes information on the threat actor involved, the severity of the detected activity, and a description of the potential implications.
For those interested in enhancing their cloud security posture, CloudGrappler is available on GitHub.
The repository includes detailed instructions on setting up and using the tool, making it accessible to security teams of all sizes.
As cloud environments become increasingly complex and threat actors’ activities more sophisticated, tools like CloudGrappler are essential for maintaining a robust security posture.
CloudGrappler represents a significant step forward in the fight against cybercrime by offering an open-source solution for detecting and analyzing threats in cloud environments.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Open Source Intelligence Methods and Tools: A Practical Guide to Online Intelligence
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Feb 26 2024
Web Check offers thorough open-source intelligence and enables users to understand a website’s infrastructure and security posture, equipping them with the knowledge to understand, optimize, and secure their online presence.
Unlike similar services, Web Check is free. There’s no signup, tracking, logging, or ads. Anyone can deploy their instance easily.
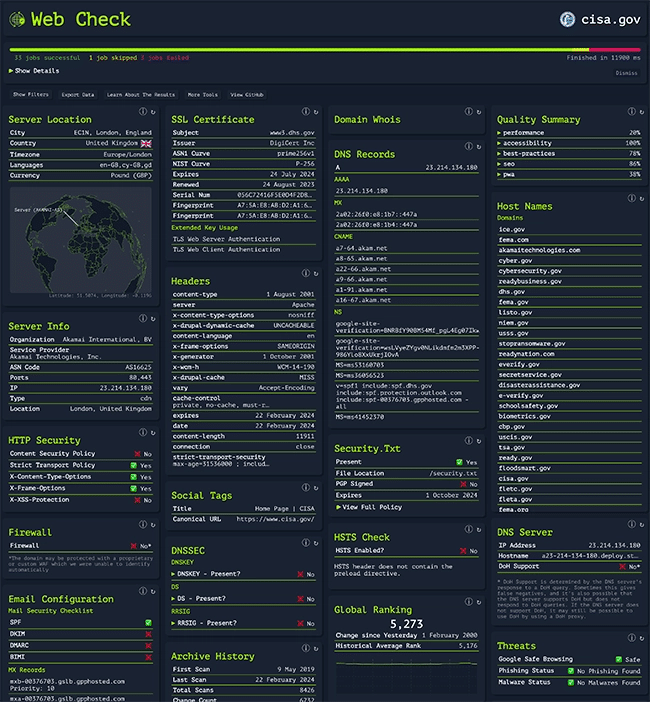
Web Check provides insight into the inner workings of any specified website, enabling users to identify possible security vulnerabilities, scrutinize the underlying server architecture, inspect security settings, and discover the various technologies employed by the site.
Currently, the dashboard will show IP info, SSL chain, DNS records, cookies, headers, domain info, search crawl rules, page map, server location, redirect ledger, open ports, traceroute, DNS security extensions, site performance, trackers, associated hostnames, carbon footprint.
“When you’re looking into any website or server, either as part of an OSINT investigation or just out of curiosity, there’s a couple of checks that you always start with. Think domain registrar records, SSL chain, server info, page list, tech stack, etc. None of these are hard to find individually, usually with a combination of bash commands and online tools. However, fetching, collating, and analyzing all this data is time-consuming. I created Web Check to automate this process. It locates, processes, and visualizes everything you need to provide a good starting point for your investigation. It takes just seconds to generate a full report, with no fluff,” Alicia Sykes, the creator of Web Check, told Help Net Security.
“I’m always looking for ways to increase and improve the data returned. The web scene is constantly changing, so there are always new and interesting insights you can glean from sites. I’m working on some new checks to include this data. I’m also working on a public API to be used programmatically or integrated into researchers’ existing workflows. Due to it being free to use, I must also improve performance to keep compute costs down continuously,” Sykes concluded.
Web Check is available for free on GitHub.

Must read: 15 open-source cybersecurity tools you’ll wish you’d known earlier
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Feb 08 2024
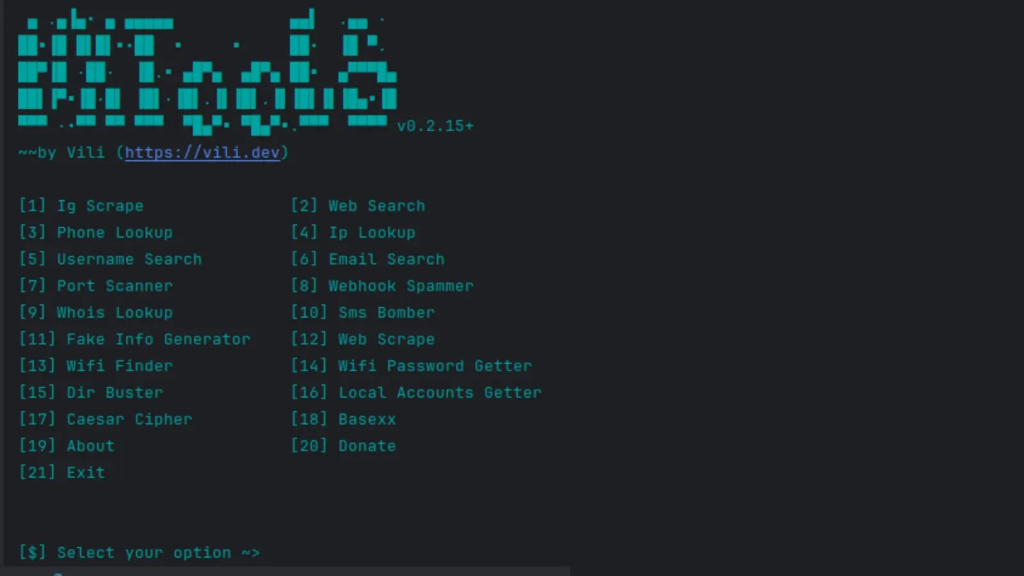
Discover the power of H4X-Tools, a versatile toolkit designed for scraping, OSINT (Open-Source Intelligence), and beyond.
From extracting information from social media accounts to conducting phone and IP lookups, H4X-Tools offers a wide array of functionalities to aid researchers, developers, and security enthusiasts alike.
Explore its features, installation process, and community-driven development in this article. Toolkit for scraping, OSINT and more.
Submit feature requests and bugs in the issues tab.
If you want to help with the development, follow the instructions in contributing and simply open a pull request. You can also donate to keep the project alive and me motivated!
Some tools might not work on Windows systems.
| Tool Name | Description |
|---|---|
| Ig Scrape | Scrapes information from IG accounts. |
| Web Search | Searches the internet for the given query. |
| Phone Lookup | Looks up a phone number and returns information about it. |
| Ip Lookup | Looks up an IP/domain address and returns information about it. |
| Port Scanner | Scans for open ports in a given IP/domain address. |
| Username Search | Tries to find a given username from many different websites. |
| Email Search | Efficiently finds registered accounts from a given email. Thanks to holehe. |
| Webhook Spammer | Spams messages to a discord webhook. |
| WhoIs Lookup | Looks up a domain and returns information about it. |
| SMS Bomber | Spams messages to a given mobile number. |
| Fake Info Generator | Generates fake information using Faker. |
| Web Scrape | Scrapes links from a given url. |
| Wi-Fi Finder | Scans for nearby Wi-Fi networks. |
| Wi-Fi Password Getter | Scans for locally saved Wi-Fi passwords. |
| Dir Buster | Bruteforce directories on a website. |
| Local Accounts Getter | Scans for all local accounts and their information. |
| Caesar Cipher | Encrypts/decrypts/bruteforce a message using the Caesar cipher. |
| BaseXX | Encodes/decodes a message using Base64/32/16. |
| About | Tells you about the tool. |
| Donate | My crypto addresses where to donate. |
| Exit | Exits the tool. |
-IG Scrape requires you to log in, in order to use it.
-SMS Bomber only works with US numbers.
-You might get rate limited after using some of the tools for too long.
I’ll upload already built executables to the releases tab, but I’d recommend installing the tool manually by following the instructions below. This way you also get the freshest version.
Important
Make sure you have Python and Git installed.
view the wiki page for more detailed tutorial.
git clone https://github.com/vil/h4x-tools.gitcd h4x-toolssh setup.sh in terminal to install the tool.git clone https://github.com/vil/h4x-tools.gitcd h4x-toolssetup.bat file.Setup files will automatically build the tool as an executable. You can also run the tool using python h4xtools.py in the terminal.
Also, dependencies can be installed manually using pip install -r requirements.txt.
OSINT Cracking Tools: Maltego, Shodan, Aircrack-Ng, Recon-Ng
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Aug 24 2023
The OWASP Amass project performs network mapping of attack surfaces and external asset discovery using open-source information gathering and active reconnaissance techniques.

Osmedeus is a workflow engine for offensive security that allows you to build and run a reconnaissance system on a wide range of targets, including domains, URLs, CIDRs, and GitHub repositories. It was designed to establish a strong foundation and can adapt and function automatically to perform reconnaissance tasks.

PhoneInfoga is an advanced tool to scan international phone numbers. It allows you to gather basic information such as country, area, carrier, and line type, then use various techniques to find the VoIP provider or identify the owner. It works with a collection of scanners that must be configured for the tool to be effective.

Sherlock allows you to search social media accounts by username across social networks.

Shodan is a search engine for Internet-connected devices. Discover how internet intelligence can help you make better decisions. The entire Shodan platform (crawling, IP lookups, searching, and data streaming) is available to developers. Use their API to understand whether users connect from a VPN, whether the website you’re visiting has been compromised, and more.

Social Analyzer is an API, CLI, and web app for analyzing and finding a person’s profile across social media and websites. It includes different analysis and detection modules; you can choose which modules to use during the investigation process. The analysis and public extracted information from this OSINT tool could help investigate profiles related to suspicious or malicious activities such as cyberbullying, cyber grooming, cyberstalking, and spreading misinformation.

SpiderFoot is an OSINT automation tool. It integrates with just about every data source available and utilizes a range of methods for data analysis, making that data easy to navigate. SpiderFoot has an embedded web-server for providing a clean and intuitive web-based interface but can also be used completely via the command-line.

theHarvester is a simple to use, yet powerful tool designed to be used during the reconnaissance stage of a red team assessment or penetration test. It performs OSINT gathering to help determine a domain’s external threat landscape. The tool gathers names, emails, IPs, subdomains, and URLs by using multiple public resources.
OSINT Tools: A Practical Guide to Collection, Analysis, and Visualization
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Jun 23 2023
Altdns is a DNS recon tool that allows for the discovery of subdomains that conform to patterns. Altdns takes in words that could be present in subdomains under a domain (such as test, dev, staging) and takes in a list of subdomains you know of.
From these two lists provided as input to Altdns, the tool then generates a massive output of “altered” or “mutated” potential subdomains that could be present. It saves this output so that it can then be used by your favorite DNS brute-forcing tool.

The OWASP Amass project performs network mapping of attack surfaces and external asset discovery using open-source information gathering and active reconnaissance techniques.
The high adoption rate of Amass potentially means better data consistency and integration with other tools. As such, it can constitute a trustworthy tool to use in proof of concepts and engagements, and it may be easier to convince your clients or manager to use it for periodic mapping of the organization’s attack surface.

Aquatone is a tool for the visual inspection of websites across a large number of hosts and is convenient for quickly gaining an overview of HTTP-based attack surface. Aquatone is started by piping the output of a command into the tool. It doesn’t really care how the piped data looks, as URLs, domains, and IP addresses will be extracted with regular expression pattern matching. This means you can give it the output of any tool you use for host discovery.

Assetfinder lets you find domains and subdomains potentially related to a given domain. Implemented:

Gobuster is a tool used to brute-force:

Gotator is a tool to generate DNS wordlists through permutations.

HTTPX is a fully featured HTTP client library for Python 3. It includes an integrated command line client, has support for both HTTP/1.1 and HTTP/2, and provides both sync and async APIs.

Naabu is a port scanning tool written in Go that allows you to enumerate valid ports for hosts in a fast and reliable manner. It is a really simple tool that does fast SYN/CONNECT/UDP scans on the host/list of hosts and lists all ports that return a reply.

MASSCAN is an Internet-scale port scanner. It can scan the entire Internet in under 5 minutes, transmitting 10 million packets per second, from a single machine. Its usage (parameters, output) is similar to Nmap, the most famous port scanner.

WhatWeb identifies websites. Its goal is to answer the question, “What is that Website?”. WhatWeb recognises web technologies including content management systems (CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices. WhatWeb has over 1800 plugins, each to recognise something different. WhatWeb also identifies version numbers, email addresses, account IDs, web framework modules, SQL errors, and more.

Open Source Intelligence Methods and Tools: A Practical Guide to Online Intelligence
InfoSec tools | InfoSec services | InfoSec books
Feb 06 2023
pen Source Intelligence (OSINT) tools are an invaluable resource for companies, organizations cybersecurity researchers and students. In this article, we will explore the 15 best OSINT tools that you can use for your investigations and education purposes.
OSINT, or Open Source Intelligence, refers to the practice of gathering information from publicly available sources. In the information and digital age, there are countless tools and resources available for OSINT practitioners to use, making it easier than ever to collect and analyze information. Here are the 15 best OSINT tools that you can use for your investigations:
Maltego is a powerful and sophisticated OSINT tool for gathering data from public sources. Developed by Paterva, Maltego OSINT allows users to quickly uncover relationships between large amounts of disparate data which can then be used to build intelligence profiles.
With Maltego OSINT, users are able to extract information from multiple online sources using simple graphic representations. This includes the ability to map out social networks, capture contact details and business data, track domain names and IP addresses, uncover digital evidence such as documents or images stored on websites, find related news articles and more.
Furthermore, by automating the process of gathering publicly available data in this way, Maltego OSINT enables users to quickly discover hidden connections that would otherwise remain undetected. Visit the official website of Maltego here.
Shodan is a search engine for the Internet of Things (IoT) devices and an OSINT tool that is used to uncover vulnerable and exposed devices connected to the Internet, otherwise known as smart devices.
Shodan was created by John Matherly in 2009 and is considered to be the world’s first computer search engine. Shodan can be used to detect security vulnerabilities on public websites, as well as provide detailed information about each web server it finds.
Shodan has become increasingly popular among cybersecurity and IT security professionals who use it for vulnerability assessment, penetration testing, and network mapping. Shodan also helps them identify insecure services such as misconfigured cloud databases, FTP servers, telnet servers, and SSH servers that are exposed on the internet without authentication or encryption.
Additionally, Shodan provides detailed technical information about each device it finds including IP address, operating system type, open ports, running software programs and associated vulnerabilities. That is why Shoden is a perfect OSINT tool out there. Visit the official website of Shodan here.
TheHarvester is a powerful OSINT tool used to find information related to domains and email addresses. It can be used by security professionals, IT administrators, and hackers alike to collect information from different sources on the internet.
TheHarvester was created as an alternative for doing research on public resources such as search engines, PGP key servers, and social networks. It allows users to quickly gather large amounts of data from sites like Google, Bing, Yahoo!, Dogpile, LinkedIn, Twitter and many more.
All of the gathered data can be exported into several formats such as HTML/XML or even saved as a text file. Additionally, it includes an API that allows users to customize their searches according to their specific needs. Visit the official TheHarvester page on Kali here.
Recon-ng is an OSINT tool used for reconnaissance and data gathering. It is a full-featured web application that can be used to gather subsets of public information related to a target, such as usernames, names, email addresses, domain names and other relevant details.
Recon-ng has been designed to automate the process of gathering intelligence about a given target as quickly and efficiently as possible. The Recon-ng OSINT tool provides users with access to multiple resources such as Google, Bing, Twitter, Shodan and more.
The platform also allows users to interact with each resource using the same interface which simplifies the data-gathering process significantly compared to traditional methods. It enables users to quickly collect comprehensive information on a target without having to manually search multiple online sources or databases. Visit the official Recon-ng page on Kali here.
Spiderfoot is an excellent OSINT tool designed to automate the process of gathering information about a specific target. Spiderfoot enables users to have quick and easy access to a wide range of data sources.
It is capable of collecting information from over 200 sources, such as DNS records, WHOIS information and public resources like Shodan, VirusTotal, Google and others. Spiderfoot can be used for reconnaissance, investigative research and even threat hunting by allowing users to quickly identify potential threats or vulnerabilities in their environment.
The tool works by scanning the internet for publicly available data from various sources based on the user’s input query parameters. The collected data can then be mapped out into an interactive graph with various visual indicators which make it easier to interpret the gathered information.
This feature makes it much easier for security professionals to recognize trends or anomalies within their networks which can help them detect malicious activities or threats early on. Visit the official website of Spiderfoot here.
OSINT Framework is a website and information-gathering tool used by security professionals for investigative purposes. It is a collection of free and publicly available tools that can be used to conduct online investigations.
OSINT Framework provides users with an easy-to-use platform to quickly search, collect and analyze data from various sources such as social media platforms, websites, forums, blogs and more. By using this framework, security professionals are able to gather a wealth of information in order to identify potential threats or anomalies on the web.
The OSINT Framework enables users to access public records and other sources of information quickly and efficiently. It utilizes specialized search engines and databases such as Google Hacking Database (GHDB) as well as several other open-source intelligence tools such as Recon-ng, Maltego and Shodan. Visit the official website of OSINT Framework here.
Foca (Fingerprinting Organizations with Collected Archives) is an OSINT tool used by cybersecurity professionals to collect data from the internet. It can be used to find information on any subject, including people, companies, and other organizations. The tool gathers data from a variety of sources such as social media platforms, websites, and search engines.
The tool helps users to collect information quickly and efficiently by providing them with a set of tools for searching, collecting and analyzing the collected data. It provides users with advanced filtering options that allow them to narrow down their searches and find relevant information easily.
Foca also has features such as keyword analysis which enables users to analyze text-based content or images in order to identify patterns or trends in the collected data. Additionally, it offers other features like automated report generation which allows users to generate reports quickly without having to manually gather all the necessary data themselves. Visit the official GitHub repository of FOCA here.
Metagoofil is a powerful OSINT tool used for gathering publicly available information about a particular target. It is especially useful for penetration testers, security professionals, and researchers who need to collect data from websites in order to perform reconnaissance on their targets.
Metagoofil was developed by Edge Security in 2006 as part of the framework for its security consulting services. This tool can be used to scan websites, search engines, and public document archives such as PDFs and Microsoft Office documents. It then searches for specific keywords related to the target and collects the relevant information from these sources.
With its easy-to-use interface, Metagoofil allows users to quickly find files containing sensitive information such as usernames, passwords, email addresses, IP addresses, etc., which can then be used in further attacks or research projects. Visit the official Metagoofil page on Kali here.
GHunt is a new OSINT tool that lets users extract information from any Google Account using an email. The information that GHunt extracts include:
Visit GHunt’s GitHub repository here.
The Russian counterweight to America’s Google, Yandex has been extremely popular in Russia and offers users the option to search across the internet for thousands of images. This is in addition to its reverse-image functionality which is remarkably similar to Google.
A good option included within is that you could sort images category wise which can make your searches more specific and accurate.
Tip: In my personal experience; Yandex image search results are far more accurate and in-depth than Google Images. Visit Yandex here.
Allowing you to track satellites from afar, N2YO is a great tool for space enthusiasts. It does so by featuring a regularly searched menu of satellites in addition to a database where you could make custom queries along the lines of parameters such as the Space Command ID, launch date, satellite name, and an international designator.
You could also set up custom alerts to know about space station events along with a live stream of the International Space Station(ISS)! Visit the official website of N2YO here.
TinEye is the original reversed image search engine, and all you have to do is submit a proper picture to TinEye to get all the required information, like where it has come from and how it has been used.
Instead of using keyword matching, it uses a variety of approaches to complete its tasks, including picture matching, signature matching, watermark identification, and numerous other databases to match the image.
In conclusion, these 15 OSINT tools are among the best available for conducting investigations using publicly available information. Whether you are a professional investigator or a curious individual, these tools can help you gather and analyze information more efficiently and effectively. Visit the official website of TinEye here.
Have I Been Pwned is an online service that helps people determine if their personal data has been compromised. It works by using email addresses to track data breaches, allowing users to know whether their information has been leaked or stolen due to a hack or other incident.
Have I Been Pwned was created in 2013 by Troy Hunt, a Microsoft Regional Director and security expert. The site provides users with detailed information about the source of any breach affecting their personal data, as well as the types of data that may have been leaked. This allows them to take appropriate steps to protect themselves from future attacks.
Have I Been Pwned or HIBP currently tracks more than 12 billion accounts across over 600 major data breaches, providing one of the most comprehensive databases for checking if your account details have been exposed online. Visit Have I Been Pwned here.
In conclusion, OSINT tools are an invaluable resource for anyone looking to stay ahead of the curve in the world of digital intelligence. The 15 Best OSINT tools outlined in this article provide an excellent overview for any user, from the novice to the professional, to get started. By using these tools and understanding their functions, users can empower themselves to become better researchers and find valuable data more quickly.

Checkout our previous posts on OSINT
OSINT Techniques: Resources for Uncovering Online Information
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Jan 31 2023
Feb 02 2022
The internet is making the world a much smaller place over the period, allowing millions of users throughout the globe to interact and share digital information, ushering the rest of the world into the ‘digital world.’
Open-source intelligence (OSINT) in the digital world describes all the public data you can access and view.
Images are also incredibly helpful in an OSINT investigation since they can reveal what a target seems like, where the target has been, or any devices that were used.
Researchers can utilize pics to create the intelligence image, discover equipment used to capture photographs, determine where and when photos were taken, and determine if a social media profile relates to a target utilizing search engines and free resources.
This article is a list of tools and tips. It will show you how to look for, obtain, extract, and analyze digital photos.
Table of Contents
Practical Threat Intelligence and Data-Driven Threat Hunting: A hands-on guide to threat hunting with the ATT&CK™ Framework and open source tools

Jul 31 2021
This OSINT tutorial demonstrates the “RECON-NG tool” on Kali Linux. It discovers the type of Anti-Virus software (AV) the victim is running on their internal network.
It’s impossible to circumvent every Anti-Virus, yet an experienced attacker knows it is possible to avoid a specific AV software for a sufficient period. If an attacker discovers which Anti-Virus the victim is running, the attacker develops their virus undetectable by that Anti-Virus.
The Recon-NG is a robust tool for performing automatic data collection and network footprinting. One can access a variety of websites to get passive data or aggressively investigate the victim for details. It offers several functionalities that enable the attacker to capture user data for social engineering, network traffic for network analysis, and more.
Consider it a data-gathering version of Metasploit. Anybody aware of Metasploit will feel at ease with this GUI, which looked and feel like Metasploit.
RECON-NG relies on sending repetitive requests to a DNS server to determine whether the DNS server has a cache containing the Anti-Virus supplier’s website. If that runs, it means that the victim at an organization is using that particular Anti-Virus program. As a result, viewing the website requires upgrading the antivirus signatures. When the DNS server does not have a cache of the AV company’s website, one can assume that nobody inside the company has asked for the Anti-Virus company’s website.
Let us get rolling!
Table of Contents