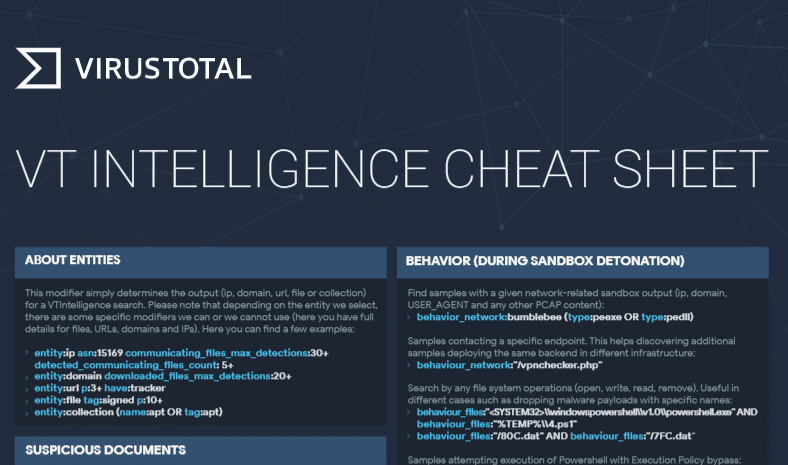
VirusTotal cheat sheet makes it easy to search for specific results
Opening the Blackbox of VirusTotal, analyzing online phishing scan engines
The Antivirus Hacker’s Handbook
Infosec books | InfoSec tools | InfoSec services
InfoSec and Compliance – With 20 years of blogging experience, DISC InfoSec blog is dedicated to providing trusted insights and practical solutions for professionals and organizations navigating the evolving cybersecurity landscape. From cutting-edge threats to compliance strategies, this blog is your reliable resource for staying informed and secure. Dive into the content, connect with the community, and elevate your InfoSec expertise!
Dec 21 2022

Opening the Blackbox of VirusTotal, analyzing online phishing scan engines
The Antivirus Hacker’s Handbook
Infosec books | InfoSec tools | InfoSec services
Dec 20 2022
Microsoft has disclosed details of a now-fixed security vulnerability dubbed Achilles (CVE-2022-42821, CVSS score: 5.5) in Apple macOS that could be exploited by threat actors to bypass the Gatekeeper security feature.
The Apple Gatekeeper is designed to protect OS X users by performing a number of checks before allowing an App to run. In fact, you will not be able to execute code that wasn’t signed by an Apple developer, you will not be able to run apps that weren’t downloaded from Apple’s store if the device is not jailbreaked of course.
The flaw was discovered on July 27, 2022, by Jonathan Bar Or from Microsoft, it is a logic issue that was addressed with improved checks.
“On July 27, 2022, Microsoft discovered a vulnerability in macOS that can allow attackers to bypass application execution restrictions imposed by Apple’s Gatekeeper security mechanism, designed to ensure only trusted apps run on Mac devices. We developed a proof-of-concept exploit to demonstrate the vulnerability, which we call “Achilles”.” reads the post published by Microsoft.
Microsoft researchers explained that Gatekeeper bypasses can be used by threat actors to install malware on macOS systems.
The experts pointed out that Apple’s Lockdown Mode introduced in July does not prevent the exploitation of the Achilles bug.
The Achilles vulnerability relies on the Access Control Lists (ACLs) permission model to add extremely restrictive permissions to a downloaded file (i.e., “everyone deny write, writeattr, writeextattr, writesecurity, chown”), to block the Safari browser from setting the quarantine extended attribute.
Below is the POC developed by Microsoft:

while video POC is available here.
Dec 20 2022
On Friday, Google released a beta version of Client-side encryption (CSE) for Gmail. This newest service is only useful to organisations that can produce their own decryption keys because CSE is designed for organisational use.
Google has now made “end-to-end encryption” available for Gmail on the web, following Meta’s 2016 offer to use it for WhatsApp. However, it only provides client-side encryption (CSE).
Notably, Client-side encryption (Google refers to as E2EE) was already available for users of Google Drive, Google Docs, Sheets, Slides, Google Meet, and Google Calendar (beta).
“We’re expanding customer access to client-side encryption in Gmail on the web. Google Workspace Enterprise plus, Education plus, and Education Standard customers are eligible to apply for the beta until January 20th, 2022”, Google announces.
Sensitive information in the email body and attachments are rendered unreadable by Google servers using client-side encryption in Gmail. Customers retain control of both the identity service used to access encryption keys.
“You can use your own encryption keys to encrypt your organization’s data, in addition to using the default encryption that Google Workspace provides,” explains Google.
“With Google Workspace Client-side encryption (CSE), content encryption is handled in the client’s browser before any data is transmitted or stored in Drive’s cloud-based storage.

“That way, Google servers can’t access your encryption keys and decrypt your data. After you set up CSE, you can choose which users can create client-side encrypted content and share it internally or externally.”
Google Workspace already uses the latest cryptographic standards to encrypt all data at rest and in transit between our facilities. Client-side encryption supports a wide range of data sovereignty and compliance requirements while enhancing the secrecy of your data.
For customers of Google Workspace Enterprise Plus, Education Plus, and Education Standard, Gmail E2EE beta is presently available.
By submitting their Gmail CSE Beta Test Application, which should include the email address, Project ID, and test group domain, they can apply for the beta until January 20, 2023.
Google says this feature will be OFF by default and can be enabled at the domain, OU, and Group levels (Admin console > Security > Access and data control > Client-side encryption).
To add client-side encryption to any message, click the lock icon and select additional encryption, compose your message and add attachments as normal.
Also, the feature is not available to Google Workspace Essentials, Business Starter, Business Standard, Business Plus, Enterprise Essentials, Education Fundamentals, Frontline, and Nonprofits, as well as legacy G Suite Basic and Business customers. Also, the service has not yet been rolled out for personal accounts.
Finally, End-to-end encryption is something we take for granted in the modern era when hacking and data leakage is becoming more frequent occurrences.

Dec 19 2022
is this website safe ? In this digital world, Check website safety is most important concern since there are countless malicious websites available everywhere over the Internet, it is very difficult to find a trustworthy website. We need tobrowse smart and need to make sure the site is not dangerous by using Multiple approaches.
In general, it is good to type the website URL instead of copy-paste or clicking an URL. Also, check to see the website working with HTTP OR HTTPS.
In order to find, is this website safe , we need to figure it out if the URL received from an unknown source and we would recommend cross-checking the URL before clicking on it. Copy the URL to analyzers that available over the Internet and ensure it’s Integrity.
If it is a shortened URL you can unshorten itwith the siteand then analyze the actual URL.
To check website safety, the first and the most recommended method is to check online page scanners, which uses the latest fingerprinting technology to show web applications are up to date or infected by malware.
Like this number of scanners available
Website reputation check needs to be done to find the trustworthiness of website with WOT .

In order to check website safety, Ensure the website availability with https before entering the payment card details. We can audit the HTTPS availability with the SSL analyzer URL’s available over the internet.
Also, there is a range of certificates available over the Internet from low assured (domain validation) to the Most trusted Extended validation certificates, you can refer the URL for more details.
Moreover, we can verify their prompt installation with various popular checkers available
According to Google, in order to check, is this website Safe, Browsing is a service that Google’s security team built to identify unsafe websites across the web and notify users and webmasters of potential harm.
In this Transparency Report, Google discloses details about the threats we detect and the warnings we show to users.
We share this information to increase awareness about unsafe websites, and we hope to encourage progress toward a safer and more secure web.
Safe Browsing also notifies webmasters when their websites are compromised by malicious actors and helps them diagnose and resolve the problem so that their visitors stay safer.
Safe Browsing protections work across Google products and power safer browsing experiences across the Internet.
Check the Browsing Website have Any unsafe Content or not – Google Safe Browsing
Please report the dangerous URL to the services mentioned below. They are arranged in categories which should make it relatively easy to decide which services you should report the site to.
Services which blacklist Dangerous sites
There are some awesome tools to Check the website IP Address has been listed in the Global Blacklist Database.
Multirblis a free multiple DNSBL (DNS BlackList aka RBL) lookup and FCrDNS (Forward Confirmed reverse DNS aka iprev) check tool to confirm, is this website Safe.
analyzes a website through multiple blacklist engines and online reputation tools to facilitate the detection of fraudulent and malicious websites. This service helps you identify websites involved in malware incidents, fraudulent activities, and phishing websites.
Important tools for Check the Website Reputation and confirm is this website Safe
Cyber criminals are using various sophisticated techniques to fool online users to drop malware and other cyber threats to cause unbearable damages. so beware of the malicious website, don’t blindly open the website and check the website safety before open it.

Web Application Security: Exploitation and Countermeasures for Modern Web Applications
Security Analysis with search engines:

Dec 16 2022
Microsoft revised the severity rate for the CVE-2022-37958 vulnerability, the IT giant now rated it as “critical” because it discovered that threat actors can exploit the bug to achieve remote code execution.
The CVE-2022-37958 was originally classified as an information disclosure vulnerability that impacts the SPNEGO Extended Negotiation (NEGOEX) security mechanism.
The SPNEGO Extended Negotiation Security Mechanism (NEGOEX) extends Simple and Protected GSS-API Negotiation Mechanism (SPNEGO) described in [RFC4178].
The SPNEGO Extended Negotiation (NEGOEX) Security Mechanism allows a client and server to negotiate the choice of security mechanism to use.
The issue was initially rated as high severity because the successful exploitation of this issue required an attacker to prepare the target environment to improve exploit reliability.
Microsoft addressed the vulnerability with the release of Patch Tuesday security updates for September 2022.
IBM Security X-Force researcher Valentina Palmiotti demonstrated that this vulnerability is a pre-authentication remote code execution issue that impacts a wide range of protocols. It has the potential to be wormable and can be exploited to achieve remote code execution.
“The vulnerability could allow attackers to remotely execute arbitrary code by accessing the NEGOEX protocol via any Windows application protocol that authenticates, such as Server Message Block (SMB) or Remote Desktop Protocol (RDP), by default.” reads the post published by IBM. “This list of affected protocols is not complete and may exist wherever SPNEGO is in use, including in Simple Message Transport Protocol (SMTP) and Hyper Text Transfer Protocol (HTTP) when SPNEGO authentication negotiation is enabled, such as for use with Kerberos or Net-NTLM authentication.”
Unlike the CVE-2017-0144 flaw triggered by the EternalBlue exploit, which only affected the SMB protocol, the CVE-2022-37958 flaw could potentially affect a wider range of Windows systems due to a larger attack surface of services exposed to the public internet (HTTP, RDP, SMB) or on internal networks. The expert pointed out that this flaw can be exploited without user interaction or authentication.
IBM announced it will release full technical details in Q2 2023 to give time organizations to apply the security updates.

Mastering Windows Security and Hardening: Secure and protect your Windows environment from intruders, malware attacks, and other cyber threats
Dec 16 2022

Network Security Checklist via Ethical Hackers Academy
Network Security Assessment: Know Your Network

InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Dec 16 2022
This recent phishing campaign tricks victims by using Facebook posts in its chain of attacks. The emails that were sent to the targets made it appear as though one of the recipients’ Facebook posts violated copyright, and they threatened to remove their accounts if no appeal was made within 48 hours.
“The content of this Facebook post appears legitimate because it uses a dummy ‘Page Support’ profile with the Facebook logo as its display picture. At first glance, the page looks legitimate, but the link provided in this post leads to an external domain”, according to Trustwave.
Here the Facebook post pretends to be “Page Support,” using a Facebook logo to appear as if the company manages it.
The main phishing URL, hxxps:/meta[.]forbusinessuser[.]xyz/main[.]php, which resembles Facebook’s copyright appeal page, is reached by clicking the link in the post.
Particularly, any data that victims enter into the form after hitting the send button, along with the victim’s client IP and geolocation data will be forwarded to hackers.
Also, threat actors may gather more data to get through fingerprinting protections or security questions while gaining access to the victim’s Facebook account.
The victim is then redirected to the next phishing website, where a false 6-digit one-time password (OTP) request with a timer is displayed.
Any code entered by the victim will fail, and if the “Need another way to authenticate?” button is pressed, the site will redirect to the real Facebook site.
According to Trustwave, multiple Facebook profiles have fake messages that look to be support pages and direct users to phishing websites.
Therefore, these fake Facebook ‘Violation’ notifications use real Facebook pages to redirect to external phishing sites. Users are urged to take extreme caution when receiving false violation alerts and to not fall for the initial links’ seeming legitimacy.
The Totally Awesome Phish Trivia Book: Uncover The History & Facts Every Phish Head Should Know!
InfoSecBooks | Tools | Services
Dec 15 2022
This is not the first time threat actors have used drivers signed by Microsoft in their operations, as we know it, and it seems that putting a stop to this practice has not been an easy task for Microsoft.
Evidence suggests that the Cuba ransomware gang used malicious hardware drivers certified by Microsoft’s Windows Hardware Developer Program in an attempted ransomware attack.
Remember when, in 2021, a report surfaced that revealed Microsoft had signed a driver called Netfilter, and later it turned out it contained malware? Well, it has happened again, but on a larger scale.
Sophos X-Ops Rapid Response (RR) recently discovered evidence which proves that threat actors potentially belonging to the Cuba ransomware gang used malicious hardware drivers certified by Microsoft’s Windows Hardware Developer Program in an attempted ransomware attack.
Drivers — the software that allows operating systems and apps to access and communicate with hardware devices — require highly privileged access to the operating system and its data, which is why Windows requires drivers to bear an approved cryptographic signature before allowing the driver to load.
However, cybercriminals have long since found approaches to exploit vulnerabilities found in existing Windows drivers from legitimate software publishers. These hackers make an effort to progressively move up the trust pyramid, using increasingly well-trusted cryptographic keys to digitally sign their drivers.
Sophos along with researchers from Google-owned Mandiant and SentinelOne warned Microsoft about these signed malicious drivers which were being planted into targeted machines using a variant of the BurntCigar loader utility. These two then worked in tandem to kill processes associated with antivirus (AV) and endpoint detection and response (EDR) products.
“Ongoing Microsoft Threat Intelligence Center analysis indicates the signed malicious drivers were likely used to facilitate post-exploitation intrusion activity such as the deployment of ransomware,” Microsoft said in an advisory published as part of its monthly scheduled release of security patches, known as Patch Tuesday.

Microsoft concluded its investigation by stating that “no compromise has been identified,” and proceeded to suspend the partners’ seller accounts. Moreover, they released Windows security updates to revoke the abused certificates.
Mandiant’s report is available here. In SentinelOne’s blog post, the security firm reported that it had seen several attacks where a threat actor used malicious signed drivers to evade security products which usually trust components signed by Microsoft.
The threat actors were observed to be targeting organisations in the business process outsourcing (BPO), telecommunications, entertainment, transportation, MSSP, financial and cryptocurrency sectors and in some instances, SIM swapping was the end goal.

Cuba Ransomware group was identified to be involved in gaining $60 million from attacks against 100 organisations globally, according to a joint advisory earlier this month from the US Cybersecurity and Infrastructure Security Agency (CISA) and the FBI.
The advisory also included warnings regarding the ransomware group which has been active since 2019 and continues to attack US entities in critical infrastructure, including financial services, government facilities, healthcare and public health, and critical manufacturing and information technology.
This is not the first time threat actors have used drivers signed by Microsoft in their operations, as we know it, and it seems that putting a stop to this practice has not been an easy task for Microsoft.
Dec 14 2022
Original post at https://cybernews.com/security/millions-ip-cameras-exposed/
When you spy on your neighborhood or your cafe customers, do you wonder if someone is watching Big Brother – you, in this case?
Businesses and homeowners increasingly rely on internet protocol (IP) cameras for surveillance. All too often, this gives them a false sense of security: when in fact, threat actors can not only access and watch your camera feed but exploit the unsecured device to hack into your network.
New research by Cybernews shows an exponential rise in the uptake of internet-facing cameras. After looking at 28 of the most popular manufacturers, our research team found 3.5 million IP cameras exposed to the internet, signifying an eightfold increase since April 2021.
While the default security settings have improved over the review period, some popular brands either offer default passwords or no authentication, meaning anyone can spy on the spies.
What is more, the overwhelming majority of internet-facing cameras are manufactured by Chinese companies. And while cosmetic security measures are in place, security leaders have long warned that technologies produced by Chinese companies can be exploited by China’s government.
Surge in internet-facing cameras
When we last did similar research, we discovered over 400,000 internet-facing cameras online. This time, the Cybernews research team found 3.5 million internet-facing cameras.
Since this is a convenient and cheap tool to surveil anything from a parking lot, a warehouse, your doorstep, or even monitor your child’s sleep using a baby camera, it’s not surprising to see a surge in IP camera usage.
While not surprising, the trend is worrying since internet-connected devices might be vulnerable to attacks – threat actors can gain access to the camera’s live feed, collect sensitive data, and launch further attacks on the network.
It is worrying that all analyzed brands have at least some models that allow users to keep default passwords or have no authentication setup whatsoever.
The reign of a Chinese brand
Most of the public-facing cameras we discovered are manufactured by the Chinese company Hikvision: the Cybernews research team found over 3.37 million of its cameras worldwide.
According to our researchers, they have the necessary security practice in place as they force users to create their unique passwords during an initial setup process. Nevertheless, the global popularity of Hikvision cameras has raised some eyebrows and, as is typical with China-manufactured technology, it and other companies are facing a backlash from Western governments.
Recently, the UK parliament instructed government agencies to cease the deployment of Chinese equipment, including surveillance cameras, on to sensitive sites, saying the technology is produced by companies subject to the National Intelligence Law of the People’s Republic of China.
Hikvision’s website advertised optional demographic profiling facial analysis algorithms, including gender, race, ethnicity, and age. Following an investigation by the Guardian, the ad was removed.
In November, the US Federal Communications Commission banned authorizations for Chinese telecommunications and video surveillance equipment, saying that Huawei, ZTE, Hytera, Hikvision, and Dahua are “deemed to pose a threat to national security.”

Most insecure brands
Most analyzed brands (96.44% of the discovered cameras) force users to set passwords or generate unique default passwords on the newest models and firmware versions. While this is a good trend, it doesn’t mean that all the cameras are safe since the lion’s share of these cameras is probably comprised of older models or those operating with outdated firmware using default or weak passwords.
Anyhow, this is a fundamental shift in the trend since last year, when we found that only 5.25% of analyzed cameras asked users to set their passwords.
As of today, 3.56% (127,000) of all analyzed cameras recommend changing the default password but do not enforce it. Sometimes, they don’t even mention it in the initial setup process, with the recommendation being on a blog post instead.
Even more concerning is that over 21,000 cameras did not have any authentication setup, allowing anyone to access them, leaving owners at risk of cyberattack.

According to the research, most public-facing cameras that might be using default credentials are operational in the United States, where we identified over 458,000 such devices.
Germany, which took second place in our research last year, covering over 50,000 cameras, didn’t even make it into the top 10 countries this time.
The second most affected country is Vietnam, with nearly 365,000 cameras, followed by the UK (nearly 250,000).
Visual here: Top 10 Countries with the most internet-connected cameras that could be using default credentials:

If you want to know how to secure your IP camera give a look at the original post published on CyberNews:
About the author: Jurgita Lapienytė, Chief Editor
A Security System for a Digital Camera: Using Cryptographic Secrecy in Steganographic Embedding
#InfoSecTools and #InfoSectraining
Ask DISC an InfoSec & compliance related question
Dec 14 2022
More good news: We know how ransomware “gangs” work and, for the most part, what they’re after.
Ransomware is opportunistic and the barriers to entry for operators are relatively low as the tools, infrastructure, and access that enables these attacks have proliferated across various online illicit communities through the ransomware-as-a-service (RaaS) model. Ransomware affiliates can rent the malware and be paid a commission from the victim’s extortion fee.
Initial access brokers—i.e. threat actors who sell ransomware operators and affiliates access into victim networks—are constantly scanning the internet for vulnerable systems. Leaked credentials from breaches and other cyber incidents can lead to brute force or credential stuffing attacks. Employees need to constantly be aware of increasingly sophisticated social engineering schemes. Threat actors can use any of these mechanisms to breach systems, escalate privileges, move laterally, and ideally take actions on objectives, dropping that malware on a victim’s network and encrypting all of their files.
Previously I wrote about the role of detection, isolation, mitigation, and negotiation in the event of a ransomware attack. Having this level of preparedness is essential today.
But one of the most effective ways to stop a ransomware attack is to deny them access in the first place; without access, there is no attack. The adversary only needs one route of access, and yet the defender has to be aware and prevent all entry points into a network. Various types of intelligence can illuminate risk across the pre-attack chain—and help organizations monitor and defend their attack surfaces before they’re targeted by attackers.
The best vulnerability intelligence should be robust and actionable. For instance, with vulnerability intelligence that includes exploit availability, attack type, impact, disclosure patterns, and other characteristics, vulnerability management teams predict the likelihood that a vulnerability could be used in a ransomware attack.
With this information in hand, vulnerability management teams, who are often under-resourced, can prioritize patching and preemptively defend against vulnerabilities that could lead to a ransomware attack.
Having a deep and active understanding of the illicit online communities where ransomware groups operate can also help inform methodology, and prevent compromise. Organizations must be able to monitor for, and be alerted to, stolen login credentials before they reach criminal actors. This intelligence can mitigate account takeover and break the chain leading to brute force or credential stuffing attacks.
When cyber threat actors successfully infiltrate your network, the subsequent attack is not always immediate; sometimes, they will install tools that can help them further invade and seek access to the most valuable data. Technical intelligence helps security teams detect indicators of compromise, or IOCs, and the presence of Cobalt Strike beacons, which can unknowingly be present in your systems and later help a ransomer carry out an attack.
In order to help employees and executives understand various ransomware-related risks, organizations should seek to implement tabletop exercises designed by companies with expertise preparing for, and responding to, a ransomware event. These simulated scenarios should cover how to spot (and report) social engineering schemes like phishing attacks, which lure employees to click on links or interact with harmful attachments that could allow ransomware malware to be deployed on company devices.
By spending time building out and rehearsing a response plan prior to an attack scenario, your team will be equipped with informed decision-making during a ransomware-related emergency. But rest assured: It’s best to have the right intelligence at-hand, including the data, expert insights, and tools that can help to prevent an attack in the first place and keep your organization running without interruption.

Responding to a Ransomware Attack: A playbook
Dec 14 2022
In a recent find, security researcher Jeremiah Fowler and the Website Planet research team discovered an open and unprotected database that contained 9,098,506 records of credit card transactions.
What’s worse, the trove of personal and financial was left exposed on a misconfigured server without any password or security authentication.
The owner of the database was identified as Cornerstone Payment Systems, a credit card processing company based in California. Upon being informed, they took swift action to restrict public access the very same day, thanking the researchers for reporting the exposure.
Cybercrimes related to credit and financial data are especially dangerous because access to data such as partial credit card numbers, account or transaction information, names, contacts, and donation comments allow threat actors to establish a target profile.
These criminals are then able to launch highly targeted phishing campaigns or social engineering attacks. It is estimated that 98% of cyber attacks involve some form of social engineering.
In this data leak, the Personally Identifiable Information (PII) included merchants, users, and customer names, partial credit card numbers, type of card, expiration date, physical addresses, and email addresses, security or access tokens, phone numbers, and more.
Furthermore, information regarding the transaction was also included such as donation details, recurring payments, and comments. The donation details had the dollar amount and what the donation was for such as payments for goods or services, and any other transaction.
Additionally, electronic check payment data included bank names and check numbers. The notes also had authorization tokens and if the payment was declined, or accepted, and reasons for the decision.
Cybercriminals would be able to use such information to reach out to customers while pretending to be legitimate merchants or organizations. This sensitive information warrants that criminals can build a relationship of trust with their victims to obtain additional payment information or a Social Security Number (SSN) or other information for nefarious purposes.

Moreover, according to Website Planet’s blog post, since many of the transactions in this database were made for donations or recurring payments to religious organizations, charity campaigns, or nonprofit groups, the criminals could target victims based on their beliefs or the causes that they support.
Many of the transaction comments the researchers saw were for religious, pro-life/anti-abortion, anti-COVID mandates, and other conservative or religious causes. It is not uncommon for hacktivists to take a vigilante stance and attack targeted individuals.
Therefore, it is essential for organizations that collect and store PII to use encryption and take other security measures to protect their sensitive data online. It is also just as necessary for the potentially affected individuals to be notified and advised to practice extra caution in all their online interactions.
Disclosure of Certain Credit Card Complaint Data
Dec 13 2022
A global survey from recruitment firm Marlin Hawk that polled 470 CISOs at organizations with more than 10,000 employees found nearly half (45%) have been in their current role for two years or less.
James Larkin, managing partner for Marlin Hawk, said that rate is slightly lower than the previous year when the same survey found 53% of CISOs had been in their positions for less than two years.
Overall, the survey found that current turnover rates are at 18% on a year-over-year basis. Approximately 62% of CISOs were hired from another company, compared to 38% that were promoted from within, the survey also found.
However, only 12% of CISOs are reporting directly to the CEO, while the rest report to other technology leadership roles, the survey revealed. It also found that more than a third of CISOs (36%) that have a graduate degree also received a higher degree in business administration or management, a 10% decline from the previous year. A total of 61% have higher degrees in another STEM field, the survey found.
Finally, the survey showed only 13% of the respondents are female, while only 20% are non-white.
The role of the CISO continues to expand—and with it the level of stress—as cyberattacks continue to increase in volume and sophistication, noted Larkin. It’s not clear whether or how much stress levels are contributing to CISO turnover rates, but it is one of the few 24/7 roles within any IT organization, added Larkin.
The role of the CISO has also come under more scrutiny in the wake of the conviction of former Uber CISO Joe Sullivan on charges of obstruction. Most CISOs view their role as defending the corporation but, in general, Larkin noted that most of them would err on the side of transparency when it comes to managing cybersecurity.
The one certain thing is that CISOs are more valued than ever. A PwC survey of 722 C-level executives found that 40% of business leaders ranked cybersecurity as the number-one most serious risk their organizations faced. In addition, 58% of corporate directors said they would benefit most from enhanced reporting around cybersecurity and technology.
As a result, nearly half of respondents (49%) said they were increasing investments in cybersecurity and privacy, while more than three-quarters (79%) said they were revising or enhancing cybersecurity risk management.
As a result, CISOs generally have more access to resources despite an uncertain economy. The issue is determining how best to apply those resources given the myriad platforms that are emerging to enhance cybersecurity. Of course, given the chronic shortage of cybersecurity talent, the biggest challenge may simply be finding someone who has enough expertise to manage those platforms.

In the meantime, most of the training CISOs and other cybersecurity professionals receive will continue to be on the job. CISOs, unlike other C-level roles that have time available for more structured training, don’t have that luxury.

Dec 13 2022
Aikido is the wiper tool that has been developed by the Or Yair of SafeBreach Labs, and the purpose of this wiper is to defeat the opponent by using their own power against them.
As a consequence, this wiper can be run without being given privileges. In addition, it is also capable of wiping almost every file on a computer, including the system files, in order to make it completely unbootable and unusable.
EDRs are responsible for deleting malicious files in two main ways, depending on the following contexts:-
As soon as a malicious file is detected and the user attempts to delete it, the Aikido wiper takes advantage of a moment of opportunity.
This wiper makes use of a feature in Windows allowing users to create junction point links (symlinks) regardless of the privileges of the users’ accounts, which is abused by this wiper.
A user who does not have the required permissions to delete system files (.sys) will not be able to delete those files according to Yair. By creating a decoy directory, he was able to trick the security product to delete the file instead of preventing it from being deleted.
Likewise, he placed a string inside the group that resembled the path intended for deletion, for example, as follows:-
Here below we have mentioned all the general qualities of the Aikido Wiper:-
It was found that six out of 11 security products tested by Or Yair were vulnerable to this exploit. In short, over 50% of the products in this category that is tested are vulnerable.
Here below we have mentioned the vulnerable ones:-
Here below we have mentioned the products that are not vulnerable:-
Between the months of July and August of this year, all the vulnerabilities have been reported to all the vendors that have been affected. There was no arbitrary file deletion achieved by the researcher in the case of Microsoft Defender and Microsoft Defender for Endpoint products.
In order to cope with the vulnerabilities, three of the vendors have issued the following CVEs:-
This exploit was also addressed by three of the software vendors by releasing updated versions of their software to address it:-
This type of vulnerability should be proactively tested by all EDR and antivirus vendors to ensure that their products are protected from similar attacks in the future.
For organizations using EDR and AV products, the researcher strongly recommends that they consult with their vendors for updates and patches immediately.


Dec 12 2022
The coming new year is a good moment for chief information security officers to reflect upon what they’ve learned this year and how to apply this knowledge going forward.
“If companies are not going to learn these lessons and mature their security practices, we will see increased scrutiny in audits and third-party risk assessments, and this may have a financial, reputational, operational, or even compliance impact on their business,” says Sohail Iqbal, CISO at Veracode.

1. Don’t wait for a geopolitical conflict to boost your security
2. The population of threat actors has exploded, and their services have become dirt cheap
3. Untrained employees can cost a company millions of dollars
4. Governments are legislating more aggressively for cybersecurity
5. Organizations should keep better track of open-source software
6. More effort should be put into identifying vulnerabilities
7. Companies need to do more to protect against supply chain attacks
8. Zero trust should be a core philosophy
9. Cyber liability insurance requirements might continue to increase
10. The “shift-left” approach to software testing is dated
11. Using the wrong tool for the wrong asset will not fix the problem
12. Organizations need help understanding their complete application architectures
13. Security should be a continuous effort
14. Have plans in place
Source for more details: 14 lessons CISOs learned in 2022

Dec 12 2022
Malware attacks are a growing problem in our increasingly digital world. By infiltrating computers and networks, malicious software can cause serious harm to those affected by it.
One of the most common types of malware is ransomware (encryption-based malware), which prevents users from accessing their files until they pay a hefty fee to the cyber attacker. This type of attack has been used to target everything from individuals to large organizations, including government agencies and healthcare providers.
In addition to financial losses, malware attacks can have devastating effects on businesses and individuals. In some cases, sensitive data can be stolen or destroyed as part of an attack. This can lead to identity theft and other forms of fraud, as well as put organizations at risk for long-term damage if confidential information is exposed or compromised.
A recent study by Atlas VPN shows how malware infection is on the rise and the trends in the new malware samples found in the first three quarters of 2022.
According to researchers, 59.58 million samples of new Windows malware were found in the first three quarters of 2022 and these make up 95.6% of all new malware discovered during that time period.
This analysis was based on data by AV-TEST GmbH, an independent organization that evaluates and rates antivirus and supplies services in IT Security and Antivirus Research. The study also includes new malware samples detected in the four quarters of 2021 and the first three quarters of 2022.
Overall, there is a downward trend in the data with the malware samples this year has decreased by 34% as compared to the same period last year. However, the numbers are still exceptionally high.
Following Windows on the list is Linux malware with 1.76 million new malware samples – 2.8% of the total malware threats in 2022.
Android malware takes third place with the first three quarters of 2022 seeing 938,379 new Android malware threats, constituting 1.5% of the total new malware.
Lastly, 8,329 samples of never before seen malware threats aimed at macOS were observed in the same period.
The study also shows that the total number of malware threats found in the first three quarters of 2022 across all operating systems amount to 62.29 million. This is about 228,164 malware threats daily.
If we make a quarter-by-quarter comparison, the first quarter of 2022 saw the most significant number of malware samples – 22.35 million. However, this number dropped by 4% to 21.49 million in the second quarter of this year. Again, it decreased by another 14% to 18.45 million.
The numbers continue to plummet into the fourth quarter of the year with 7.62 million new threats found in October and November – nearly 60% less than at the same time last year.
Malware is a pervasive threat to internet users on both personal and professional networks. It can cause serious damage to computers, networks, and data that can be expensive to fix. Fortunately, there are steps you can take to protect yourself from malware.
The most important step in protecting your network from malware is keeping your anti-malware software up to date. Regularly updating anti-malware programs ensures that they’re able to detect the latest threats and keep them away from your computer or network.
Additionally, be sure not to click on suspicious links or download files from unknown sources as these could contain malicious code that could harm your system.
Another way to stay safe online is by using a secure web browser with built-in security features like pop-up blockers, phishing protection, and ad blockers ((don’t use it on Hackread.com though :0)) for enhanced protection against malicious activities.

Dec 11 2022
A phishing scam is not only about stealing your login credentials, but it can also install malware, including ransomware, which is why it is essential to learn how to tackle this growing threat.
The number of phishing scams reported in the first quarter of 2022 set a new record of over one million total attacks, according to a report by the Anti-Phishing Working Group.
And the scams have been growing fast in recent years. The number of attempts reported in the first quarter of 2022 is more than triple the average numbers just two years before, in early 2020.
With so many attacks underway—and growing by the day—what’s the best way to recognize these scams and prevent them? We’ll look at how to recognize and protect yourself from the most common types of phishing fraud. Meanwhile, you can also learn how to detect phishing images in an email.
Phishing today refers to a type of scam that steals people’s personal information by posing as a trusted third party. For example, a scammer might pretend to be a government worker to get you to share your Social Security number or pretend to be from your bank to get you to share account details.
With so many communication channels today, there are more phishing methods than ever before. And scammers have adapted to each type of channel by leveraging trust signals inherent to each one.
This can make it hard for the untrained eye to spot a phishing scam and even difficult to recognize if you’ve been hacked after falling for an attack. The first sign that tips off most victims is an unexpected charge, damaged credit score, or depleted bank account.
Here are the six most common types of phishing scams and how to protect yourself.
Anyone can fall for an email scam; this U.S. judge did. By far the most common type of phishing attack is via email. You’re probably familiar with the spam emails we all get on a day-to-day basis, but the most sophisticated phishing attacks look very different.
These emails often look identical to official messages and notifications, including the company’s logo and exactly the same content as a real message. For example, one of today’s most common scams is a message notification from LinkedIn that’s almost impossible to tell apart from the real thing.
Another common method fraudsters use to trick victims is over the phone. These calls usually claim to have a one-of-a-kind offer or urgent, life-threatening warning.
Most scammers use a VoIP phone system that lets them change the phone number, meaning the call appears as though it’s from a local number even if it’s not.

One of the most common destinations for phishing scams is a fraudulent site that looks like the official website. The cloned site will often be identical to the real page, using the company’s logos, color scheme, and fonts.
After establishing trust with the design, the site will ask you to share personal information, anything from your email and password to your Social Security number or bank account details. For example, this attack impersonating American Express used an email message and web page almost impossible to tell apart from the real brand.
Text messages don’t have much space for the scammer’s message, but that hasn’t stopped criminals from trying new tactics to trick innocent victims. The goal of most SMS scams is to get you to click on a link or make a call, so immediately be suspicious of any message with a link or number (though of course, some legitimate messages have these as well).
One of the most common ruses right now with text scams is, ironically enough, helping to protect you from scams. You’ll often see a message “confirming” an expensive purchase or withdrawal, directing you to a number or link to cancel or investigate. There is nothing to cancel or investigate, but the scammer will pretend to resolve the situation by collecting your personal data for a future attack.
Social media has become one of the more recent additions to the phishing repertoire. Scammers reach out either using a fake lookalike account or a compromised account.
One common ruse is a friend reaching out for help, usually with an authentication code. But it’s not a friend—it’s a scammer who’s taken over their account and is trying to take over yours. Another ruse is a message from someone posing as the official company support account, asking you to provide information to verify you’re the authentic owner or to keep your page active.
This type of phishing scam requires the attacker to be nearby but can be one of the most dangerous because it’s almost impossible to detect. It works when you and the attacker are on the same Wi-Fi network, like at a coffee shop or airport. The attacker intercepts everything you send and receive and can redirect your browser to safe sites to look-alike sites without you knowing.
Once the attacker has set up a man-in-the-middle attack, they can see almost all the information you share, including usernames, passwords, credit card details, and more.
Every type of phishing requires a slightly different method to spot, and scammers are constantly developing new methods that leverage our weaknesses. But there are a few common warning signs you can look for across different types of phishing attacks.
You’ve learned how to protect yourself from phishing scams, but what if you’ve already fallen victim? If you know you’ve shared information with a scammer, here’s what you should do, based on what information you’ve shared.
No matter what kind of information you’ve shared, it’s always a good idea to report the fraud to the Federal Trade Commission at IdentityTheft.gov. Filing the report helps protect others, gives you documentation of the attack, and will provide you with recovery steps specific to your situation
Phishing attacks are on the rise, and scammers are developing even more intricate scams all the time. But if you know the most common warning signs and stay vigilant, you can protect yourself and take quick action in case you’ve been compromised.

Dec 09 2022
ThreatFabric’s security researchers have reported a new dark web platform through which cybercriminals can easily add malware to legitimate Android applications.
Dubbed Zombinder, this platform was detected while investigating a campaign in which scammers were distributing multiple kinds of Windows and Android malware, including Android banking malware like Ermac, Laplas “clipper,” Erbium, and the Aurora stealer, etc.
This comes just days after a new dark web marketplace called InTheBox surfaced online, serving smartphone malware developers and operators.
Further probe helped researchers trace the adversary to a third-party dark web service provider called Zombinder. It was identified as an app programming interface binding service launched in March 2022.

According to ThreatFabric’s blog post, numerous different threat actors are using this service and advertising it on hacker forums. On one such forum, the service was promoted as a universal binder that binds malware with almost any legitimate app.
The campaign is designed to appear as it helps users access internet points by imitating the WiFi authorization portal. In reality, it pushes several different malware strains.
In the campaign detected by ThreatFabric’s researchers, the service is distributing the Xenomorph banking malware disguised as the VidMate app. It is distributed via modified apps advertised/downloaded from a malicious website mimicking the application’s original website. The victim is lured to visit this site via malicious ads.
The Zombinder-infected app works just as it is marketed while the malicious activity carries on in the background and the victim stays unaware of the malware infection.

At the moment, Zombinder is focusing entirely on Android apps but the service operators are offering Windows apps binding services. Those who downloaded the infected Windows app were delivered the Erbium stealer as well. It is an infamous Windows malware distributed to steal stored passwords, cookies, credit card details, and cryptocurrency wallet data.
It is worth noting that two downloaded buttons on the malicious website’s landing page, one for Windows and the other for Android. when a user clicks on the Download for Windows button, they are delivered malware designed for Microsoft operating system, including Aurora, Erbium, and Laplas clipper. Conversely, the Download for Android button distributes the Ermac malware.
If you want to stay safe, do not sideload apps even if you are desperate to make a specific product work. Also, avoid installing apps from unauthentic or unknown sources onto your Android mobile phone and rely on legitimate sources such as Google Play Store, Amazon Appstore, or Samsung Galaxy Store. Always check the app’s rating, and reviews, and check out the app developers’ website before installing a new app.
Cyber Deep Web
