Web Application Security: A 2023 Guide | Cyber Press
Written by: Cyber Writes

Web App Security

InfoSec tools | InfoSec services | InfoSec books
Jun 24 2023
Web Application Security: A 2023 Guide | Cyber Press
Written by: Cyber Writes

Web App Security

InfoSec tools | InfoSec services | InfoSec books

Dec 19 2022
is this website safe ? In this digital world, Check website safety is most important concern since there are countless malicious websites available everywhere over the Internet, it is very difficult to find a trustworthy website. We need tobrowse smart and need to make sure the site is not dangerous by using Multiple approaches.
In general, it is good to type the website URL instead of copy-paste or clicking an URL. Also, check to see the website working with HTTP OR HTTPS.
In order to find, is this website safe , we need to figure it out if the URL received from an unknown source and we would recommend cross-checking the URL before clicking on it. Copy the URL to analyzers that available over the Internet and ensure it’s Integrity.
If it is a shortened URL you can unshorten itwith the siteand then analyze the actual URL.
To check website safety, the first and the most recommended method is to check online page scanners, which uses the latest fingerprinting technology to show web applications are up to date or infected by malware.
Like this number of scanners available
Website reputation check needs to be done to find the trustworthiness of website with WOT .

In order to check website safety, Ensure the website availability with https before entering the payment card details. We can audit the HTTPS availability with the SSL analyzer URL’s available over the internet.
Also, there is a range of certificates available over the Internet from low assured (domain validation) to the Most trusted Extended validation certificates, you can refer the URL for more details.
Moreover, we can verify their prompt installation with various popular checkers available
According to Google, in order to check, is this website Safe, Browsing is a service that Google’s security team built to identify unsafe websites across the web and notify users and webmasters of potential harm.
In this Transparency Report, Google discloses details about the threats we detect and the warnings we show to users.
We share this information to increase awareness about unsafe websites, and we hope to encourage progress toward a safer and more secure web.
Safe Browsing also notifies webmasters when their websites are compromised by malicious actors and helps them diagnose and resolve the problem so that their visitors stay safer.
Safe Browsing protections work across Google products and power safer browsing experiences across the Internet.
Check the Browsing Website have Any unsafe Content or not – Google Safe Browsing
Please report the dangerous URL to the services mentioned below. They are arranged in categories which should make it relatively easy to decide which services you should report the site to.
Services which blacklist Dangerous sites
There are some awesome tools to Check the website IP Address has been listed in the Global Blacklist Database.
Multirblis a free multiple DNSBL (DNS BlackList aka RBL) lookup and FCrDNS (Forward Confirmed reverse DNS aka iprev) check tool to confirm, is this website Safe.
analyzes a website through multiple blacklist engines and online reputation tools to facilitate the detection of fraudulent and malicious websites. This service helps you identify websites involved in malware incidents, fraudulent activities, and phishing websites.
Important tools for Check the Website Reputation and confirm is this website Safe
Cyber criminals are using various sophisticated techniques to fool online users to drop malware and other cyber threats to cause unbearable damages. so beware of the malicious website, don’t blindly open the website and check the website safety before open it.

Web Application Security: Exploitation and Countermeasures for Modern Web Applications
Security Analysis with search engines:

Oct 04 2022
A cybersecurity framework provides a formal and comprehensive set of guidelines to help organizations define their security policies, assess cybersecurity posture, and improve resilience. Cybersecurity frameworks specify security controls, risk assessment methods, and suitable safeguards to protect information systems and data from cyberthreats. Though originally developed for government agencies and other large organizations, cybersecurity frameworks can also be a useful source of security best practices for medium and small businesses. Without getting too formal, let’s see what cybersecurity frameworks exist, why you may want to use one, and how to hand-pick the cybersecurity processes and actions that apply to your specific web application security program.
Depending on the organization, a successful cyberattack can have serious social, economic, or even political consequences. Whether they result in a denial of service, a data breach, or a stealthy and persistent presence in targeted systems, cyberattacks are now a permanent concern not only for business and government but even for military operations. Well-defined cybersecurity programs are vital for organizations of all sizes, but simply saying “secure everything” isn’t good enough, especially given the complexity of today’s interconnected information systems and supply chains. And with data security and privacy high on the agenda, a systematic and formalized approach is necessary to identify specific security controls that keep sensitive information inaccessible to malicious actors.
With public and private organizations of all sizes facing similar cybersecurity events and challenges, it became clear that a common cybersecurity framework would benefit everyone. By working to a common set of best-practice policies and recommendations, everyone would be able to define their own cybersecurity practices and protective technologies while maintaining a common baseline for auditing and certification. And for organizations that may lack the resources or technical resources to design their own policies from scratch, having such a starter policy kit could be the only way to come up with a reasonably complete and effective cybersecurity policy.
You can think of a cybersecurity framework as a common box of parts for building cybersecurity policies. More formally, a cybersecurity framework can be any document that defines procedures and goals to guide more detailed policies. Existing documents that contain such cybersecurity guidelines include:
In 2013, a US presidential executive order was issued calling for a standardized cybersecurity framework to describe and structure activities and methodologies related to cybersecurity. In response to this, NIST developed its Framework for Improving Critical Infrastructure Cybersecurity, commonly called the NIST Cybersecurity Framework (NIST CSF). It is a detailed policy document created not only to help organizations manage and reduce their cybersecurity risk but also to create a common language for communicating about cybersecurity activities. While the framework was initially intended only for companies managing critical infrastructure services in the US private sector, it is now widely used by public and private organizations of all sizes.
The NIST CSF is divided into three main components:
The framework core provides a unified structure of cybersecurity management processes, with the five main functions being Identify, Protect, Detect, Respond, and Recover. For each function, multiple categories and subcategories are then defined. This is where organizations can pick and mix to put together a set of items for each function that corresponds to their individual risks, requirements, and expected outcomes. For clarity and brevity, each function and category has a unique letter identifier, so for example Asset Management within the Identify function is denoted as ID.AM, while Response Planning within the Response function is RS.RP.
Each category includes subcategories that correspond to specific activities, and these subcategories get numerical identifiers. To give another example, subcategory Detection processes are tested under the Detection Processes category and Detect function is identified as DE.DP-3. Subcategory definitions are accompanied by references to the relevant sections of standards documents for quick access to the normative guidelines for each action.
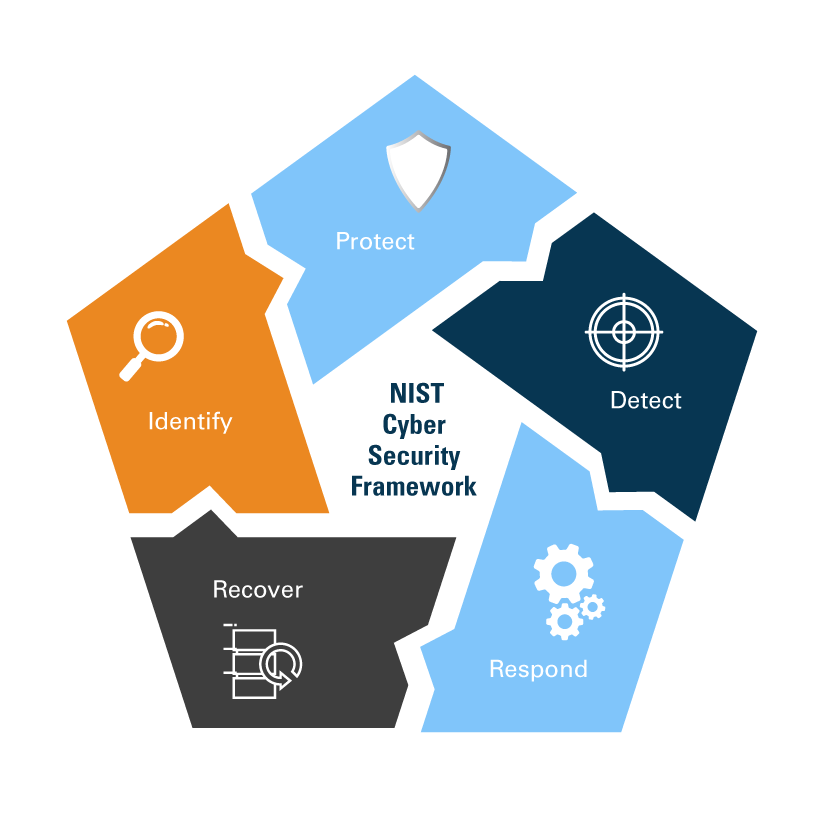
By design, the NIST CSF has an extremely broad scope and covers far more activities than any specific organization is likely to need. To apply the framework to web application security, you start by analyzing each of the five functions as they relate to your existing and planned application security activities and risk management processes. Then, you select the categories and subcategories relevant to your specific needs and use them as the backbone of your own security policy to ensure you cover all the risks and activities you need. For general web application security, a skeleton cybersecurity policy would need to include at least the following subcategories for each function:
Learn to identify security vulnerabilities in applications and implement secure code practices to prevent events like data breaches and leaks. Become familiar with DevSecOps practices, and SAST for identifying security flaws.
Dec 09 2021
The metadata stored on the file led the researchers to several WordPress database dumps, which contained multiple administrator usernames and email addresses, as well as the hashed password for the Microsoft Vancouver website.
Security researchers – us at CyberNews included – routinely use search engines that index publicly accessible Internet of Things (IoT) devices and web servers for threat intelligence. This helps us warn users and organizations that their data is being exposed and help them plug the leaks.
Back in September, while gathering intelligence on an IoT search engine, our security researchers stumbled upon a DS_STORE file that was apparently stored on a web server owned by Microsoft Vancouver.
Leaving DS_STORE files on remote web servers is dangerous because they display their folder structure, which may result in leaks of sensitive or confidential data. This is exactly what happened with the leftover DS_STORE file present on the Microsoft Vancouver web server.
“By analyzing the file, our Investigations team was able to learn about the files hosted on the Microsoft Vancouver server, as well as several database dump files stored on the server.“
These database dumps contained multiple administrator usernames and email addresses, as well as the hashed password for Microsoft Vancouver’s WordPress website.
According to the company’s website, Microsoft Vancouver is home to teams that work on developing a variety of Microsoft products, including “Notes, MSN, Gears of War, Skype, and mixed reality applications, both for desktop and HoloLens.”
On September 27, CyberNews researchers reached out to Microsoft Canada via their official contact email in order to report their findings and help secure the exposed file.
Unfortunately, we did not hear back from the company right away. Even though warnings from security researchers can sometimes get overlooked by large organizations, several additional emails are usually enough to break through and reach the eyes of security teams. As such, we made multiple additional attempts at contacting Microsoft via customer support email addresses and phone numbers listed on the company’s official websites.
On December 2, public access to the DS_STORE file was finally disabled and it is no longer leaking sensitive data. After the file was secured, we reached out to Microsoft for additional comment regarding the incident but have yet to hear back.
Exploitation and Countermeasures for Modern Web Applications
