What is Smishing and Why?
Smishing is a type of social engineering attack. Social engineering is when a cyber attacker tricks their victim into doing something they should not do, such as giving money, their password, or access to their computer. Cyber attackers have learned the easiest way to get something is just ask for it. This concept is not new, con artists and scammers have existed for thousands of years, it’s just that the Internet makes it very simple for any cyber attacker to pretend to be anyone they want and target anyone they want.
Phishing is one of the most common forms of social engineering as it’s one of the simplest and most effective and an attack method we are all familiar with. However, both organizations and individuals are becoming not only far more aware of how phishing attacks work, but much better at spotting and stopping them. Phishing is still an effective attack method, but it is getting harder and harder for cyber criminals to be effective with phishing. This is where smishing comes in.
Smishing vs Phishing
Smishing is very similar to phishing, but instead of sending emails trying to trick people, cyber attackers send text messages. The term smishing is a combination of the words SMS messaging and phishing. You may have noticed a rise in random text messages that are trying to get you to click on links or respond to text messages. That’s smishing.
Why the Increase in Smishing Attacks?
- It is harder for organizations to secure mobile devices. Security teams often have neither the visibility nor control of employees’ mobile devices like they do for workstations. This means it’s harder to both secure and monitor mobile devices.
- There are far fewer security controls that effectively identify and filter smishing attacks. This means when a cyber attacker sends a smishing text message to victims, that message is far more likely to make it and not be filtered.
- A text message tends to be much shorter than an email, there is far less context or information, making it harder to determine if the message is legitimate or not. In other words, people are more likely to fall victim.
- Texting tends to be far more informal than email, as such people tend to trust and act on text messages more. In other words, people are more likely to fall victim.
The Smishing Attacks
So, what type of text messaging attacks are there? While these attacks are always evolving, some of the most common are detailed below.
Links
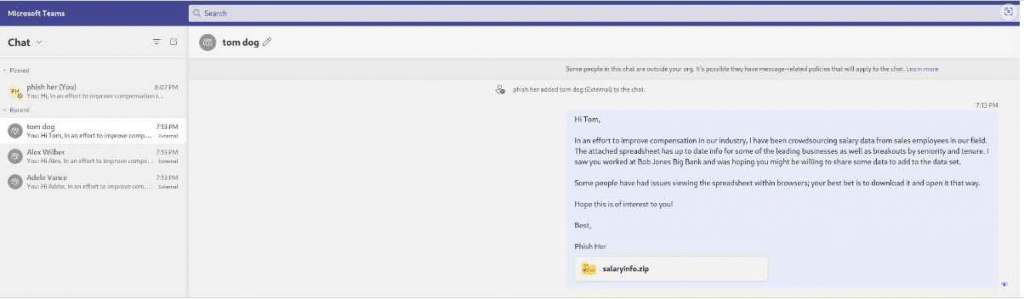
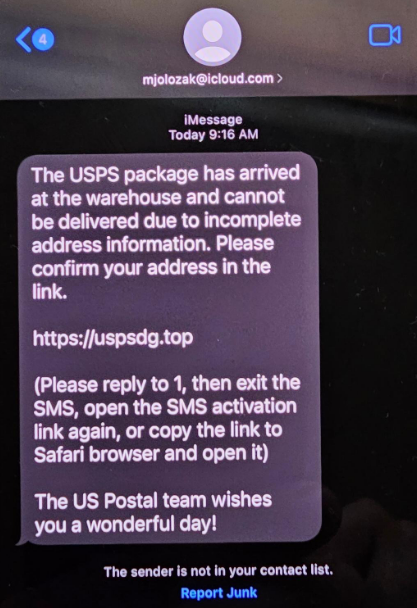
The text message entices you to click on a link, often through a sense of urgency, something too good to be true, or simple curiosity. Once you click on the link, the goal is usually to harvest your personal information (by getting you to fill out a survey) or your login and password (to your bank or email account, for example). Notice how, in the link in the message below, the cyber attacker uses HTTPS, an encrypted connection to make the link look more legitimate.
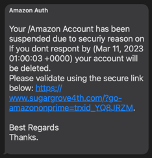
Scams
In these attacks, the cyber attacker will attempt to start a conversation with you, build trust, and ultimately scam you. Romance scams are one common example where cyber criminals randomly text millions of people to find those who are lonely or emotionally vulnerable, build a pretend romance, and then take advantage of them.
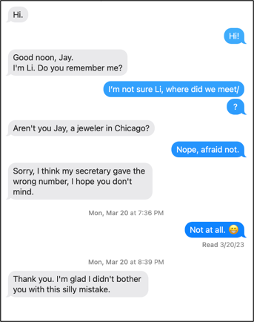
Call-Back
Like some phishing emails, the text message has a phone number in it and is urging the victim to call. Once the victim calls the phone number they are then scammed.
What to Do About Smishing Attacks?
While many security training programs focus on phishing, we far too often neglect text based smishing attacks. In fact, this can create a situation where your workforce is highly aware of phishing attacks but may mistakenly think that cyber attackers only use email for attacks. From a training perspective, we recommend you teach people that cyber attackers can use a variety of different methods to trick people, to include both email phishing and text based smishing. For smishing, we do not recommend that you try to teach people about every different type of attack possible. Not only will this likely overwhelm your workforce, but cyber attackers are constantly changing their lures and techniques. Instead, like in phishing training, focus on the most commonly shared indicators and clues of an attack. This way, your workforce will be trained and enabled regardless of the method or lures cyber attackers use. Of note, the indicators below are the same indicators of an email phishing attack.
- Urgency: Any message that creates a tremendous sense of urgency, trying to rush the victim into making a mistake. An example is a message from the government stating your taxes are overdue and if you don’t pay right away you will end up in jail.
- Pressure: Any message that pressures an employee to ignore or bypass company policies and procedures. Gift card scams are often started with a simple text message.
- Curiosity: Any message that generates a tremendous amount of curiosity or is too good to be true such as notice of an undelivered UPS package or receiving an Amazon refund.
- Sensitive: Any message that requests (or requires) highly sensitive information such as your password or unique codes.
- Tone: Any message that appears to be coming from a coworker, but the wording does not sound like them, or the overall tone is wrong.
Smishing Minefield: Defusing Text Message Threats

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot