Threat actors have begun utilizing an innovative approach to zero-point font obfuscation, a pre-existing technique, in an attempt to deceive users of Microsoft Outlook. They do so by creating an illusion that certain phishing emails have been thoroughly scanned and cleared by antivirus programs, thus increasing the chances of these deceptive emails bypassing security protocols. This not only aids in evading security measures but also enhances the probability of recipients falling prey to these fraudulent schemes.
Jan Kopriva, an analyst at the SANS Internet Storm Center, encountered a phishing email that cleverly employed text written in zero-pixel size font. This technique, originally documented by Avanan (a subsidiary of Check Point) researchers in 2018 and known as ZeroFont Phishing, was being utilized in a distinct and innovative manner, according to Kopriva’s observations. Historically, cyber attackers have integrated zero font size text within phishing emails to disrupt the continuity of text that is visible, making it increasingly difficult for automated email scanning systems like those implemented by Outlook to flag suspicious emails.
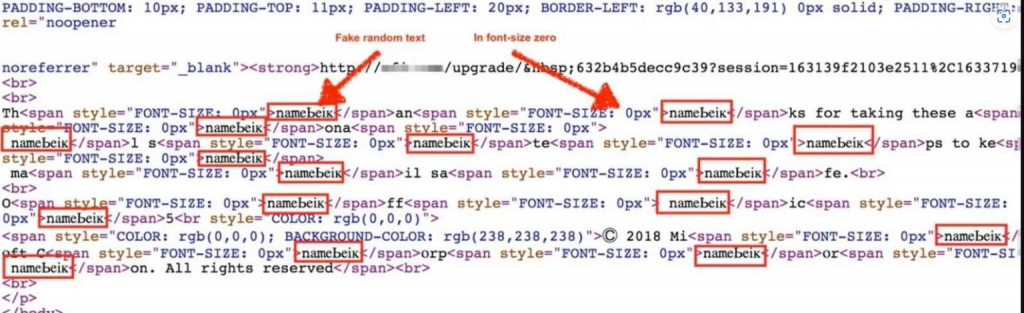
However, Kopriva noticed a variation in the use of the ZeroFont technique, which diverged from its original purpose. Instead of utilizing it to obstruct automated scanning systems from labeling the email as potentially harmful or fraudulent, it was applied to craft an illusion of trustworthiness for the recipient. Kopriva elaborated that the technique was being used to modify the text that is usually displayed in Outlook’s listing pane—a section adjacent to the body of emails that provides users with a sneak peek into the email content.
Rather than presenting the typical email subject line followed by the initial few lines of the email—which could potentially raise red flags about a phishing attempt—the listing pane under this technique displayed the subject line and an additional line of text. This added text falsely indicated that the email had undergone a security scan and was deemed safe by a threat protection service.
Avanan researchers have also discovered another manipulation of this technique, dubbed the “One Font” technique. In these instances, threat actors embed extremely small text within the zero- or one-point font range as part of their strategy to develop more elusive and sophisticated phishing scams. This minuscule font size effectively dismantles email scanning techniques relying on semantic analysis, generating confusion for the scanning systems while remaining undetectable to the recipients due to its unreadable size.
In the specific phishing email Kopriva analyzed, the attackers ingeniously incorporated text that implied the email had been verified and secured. This was achieved by inserting text in zero font size ahead of the email’s actual content. As a result, in Outlook’s listing pane, the user would see text confirming the email’s security status immediately below the subject line—instead of the true opening line of the phishing email. This deceptive approach takes advantage of Outlook’s method of displaying email text, thus exploiting it to the attacker’s benefit.
Kopriva acknowledged the possibility that this tactic has been deployed undetected for a while now. Nonetheless, it represents an additional tool in the arsenal of cyber threat actors, enhancing their ability to launch effective phishing campaigns. As defenders against cyber threats, awareness of this tactic is crucial. He recommends that organizations actively engaged in conducting security awareness training focused on phishing should incorporate information on this technique. This knowledge would empower employees to recognize and appropriately respond to deceptive emails employing this technique as an anti-detection strategy, thus fortifying organizational defenses against such cyber threats.
PHISHING SCAM AND PREVENTIVE MEASURES
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory



