Phishing is among the biggest cyber threats facing organisations. According to Proofpoint’s 2021 State of the Phish Report, more than 80% of organisations fell victim to a phishing attack last year.
One of the most frustrating things about this is that most people know what phishing is and how it works, but many still get caught out.
The growing sophisticated of phishing scams has contributed to that. They might still have the same objective – to steal our personal data or infect our devices – but there are now countless ways to do that.
In this blog, we look at five of the most common types of phishing email to help you spot the signs of a scam.
1. Email phishing
Most phishing attacks are sent by email. The crook will register a fake domain that mimics a genuine organisation and sends thousands of generic requests.
The fake domain often involves character substitution, like using ‘r’ and ‘n’ next to each other to create ‘rn’ instead of ‘m’.
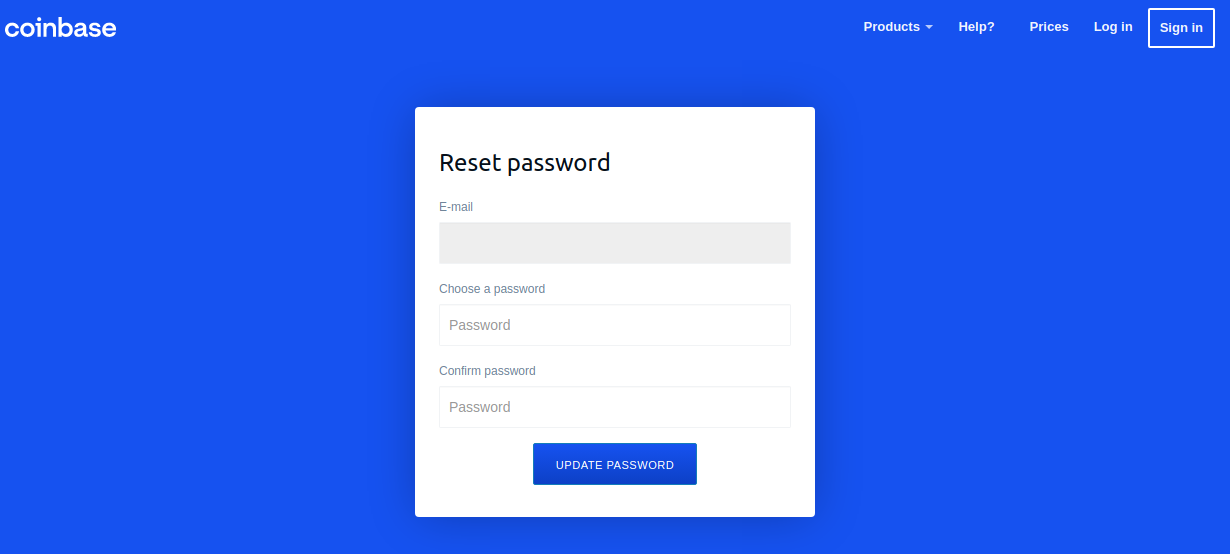
In other cases, the fraudsters create a unique domain that includes the legitimate organisation’s name in the URL. The example below is sent from ‘olivia@amazonsupport.com’.

The recipient might see the word ‘Amazon’ in the sender’s address and assume that it was a genuine email.
There are many ways to spot a phishing email, but as a general rule, you should always check the email address of a message that asks you to click a link or download an attachment.
2. Spear phishing
There are two other, more sophisticated, types of phishing involving email.
The first, spear phishing, describes malicious emails sent to a specific person. Criminals who do this will already have some or all of the following information about the victim:
- Their name;
- Place of employment;
- Job title;
- Email address; and
- Specific information about their job role.
You can see in the example below how much more convincing spear phishing emails are compared to standard scams.

The fraudster has the wherewithal to address the individual by name and (presumably) knows that their job role involves making bank transfers on behalf of the company.
The informality of the email also suggests that the sender is a native English speaker, and creates the sense that this is a real message rather than a template.
3. Whaling
Whaling attacks are even more targeted, taking aim at senior executives. Although the end goal of whaling is the same as any other kind of phishing attack, the technique tends to be a lot subtler.
Tricks such as fake links and malicious URLs aren’t helpful in this instance, as criminals are attempting to imitate senior staff.
Whaling emails also commonly use the pretext of a busy CEO who wants an employee to do them a favour.

Emails such as the above might not be as sophisticated as spear phishing emails, but they play on employees’ willingness to follow instructions from their boss. Recipients might suspect that something is amiss but are too afraid to confront the sender to suggest that they are being unprofessional.
4. Smishing and vishing
With both smishing and vishing, telephones replace emails as the method of communication.
Smishing involves criminals sending text messages (the content of which is much the same as with email phishing), and vishing involves a telephone conversation.
One of the most common smishing pretexts are messages supposedly from your bank alerting you to suspicious activity.

In this example, the message suggests that you have been the victim of fraud and tells you to follow a link to prevent further damage. However, the link directs the recipient to a website controlled by the fraudster and designed to capture your banking details.
5. Angler phishing
A relatively new attack vector, social media offers several ways for criminals to trick people. Fake URLs; cloned websites, posts, and tweets; and instant messaging (which is essentially the same as smishing) can all be used to persuade people to divulge sensitive information or download malware.
Alternatively, criminals can use the data that people willingly post on social media to create highly targeted attacks.
As this example demonstrates, angler phishing is often made possible due to the number of people containing organisations directly on social media with complaints.

Organisations often use these as an opportunity to mitigate the damage – usually by giving the individual a refund.
However, scammers are adept at hijacking responses and asking the customer to provide their personal details. They are seemingly doing this to facilitate some form of compensation, but it is instead done to compromise their accounts.
Your employees are your last line of defence
Organisations can mitigate the risk of phishing with technological means, such as spam filters, but these have consistently proven to be unreliable.

Malicious emails will still get through regularly, and when that happens, the only thing preventing your organisation from a breach is your employees’ ability to detect their fraudulent nature and respond appropriately.
Our Phishing Staff Awareness Course helps employees do just that, as well as explaining what happens when people fall victim and how they can mitigate the threat of an attack.
The Science of Human Hacking
👇 Please Follow our LI page…
DISC InfoSec
#InfoSecTools and #InfoSectraining
























![CYBER SECURITY FOR TOP EXECUTIVES: Everything you need to know about Cybersecurity by [Alejandra Garcia]](https://m.media-amazon.com/images/I/51UZgLnDdYS.jpg)