In the latest edition of Verizon’s Data Breach Investigations Report (DBIR) for 2024, a concerning trend has been highlighted, a significant 68% of data breaches are now occurring due to social engineering attacks.
This revelation underscores the increasing sophistication and prevalence of these tactics in the cyber threat landscape.
Social engineering exploits the human factor, manipulating individuals into breaking normal security procedures.
The DBIR’s findings suggest that despite advancements in technology, human vulnerabilities remain a critical weak point.
The report indicates that phishing, pretexting, and other forms of social engineering are not only prevalent but are also becoming more sophisticated.

Verizon’s 2024 DBIR has revised its methodology to provide clearer insights into breaches involving the human element.
It excludes cases of malicious privilege misuse to focus on incidents that could potentially be mitigated through improved security awareness and training.
The Role Of Ransomware And Extortion
The report also sheds light on the role of ransomware and extortion in the cybersecurity threat landscape.
Approximately one-third of all breaches involved these tactics, with pure extortion attacks marking a significant rise over the past year.
This shift indicates a strategic evolution among cybercriminals, who are increasingly leveraging ransomware and extortion to capitalize on their attacks.
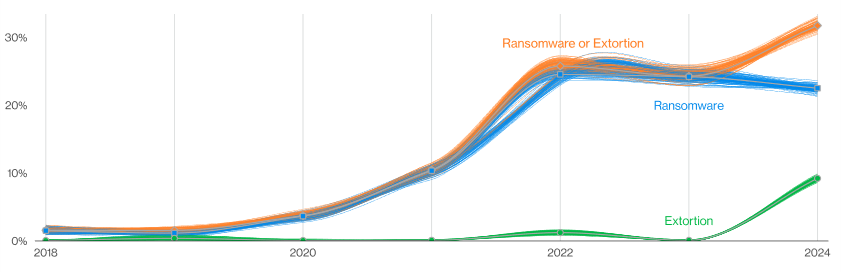
The combination of ransomware and other forms of extortion has been particularly impactful, affecting 32% of breaches and being a top threat across 92% of industries surveyed.
This highlights the critical need for organizations to enhance their defensive strategies against these forms of cyberattacks.
Third-Party Vulnerabilities And Preventive Measures
An expanded concept of breaches involving third-party entities was introduced in this year’s report.
This includes incidents where partner infrastructure is compromised or where indirect software supply chain issues occur.
The report notes a 68% increase in such breaches, primarily fueled by zero-day exploits used in ransomware and extortion attacks.

This finding emphasizes the importance of diligent vendor selection and the need for organizations to prioritize security in their supply chains.
By choosing partners with robust security measures, companies can significantly mitigate the risk of being compromised through third-party vulnerabilities.
Verizon’s 2024 DBIR provides a stark reminder of the persistent and evolving threats in the digital world.
With a significant portion of breaches attributable to social engineering, the human element continues to be a critical battleground in cybersecurity.
Organizations must prioritize comprehensive security training and robust protocols to safeguard against these insidious attacks.
Meanwhile, the rise of ransomware and extortion, along with the vulnerabilities in third-party partnerships, calls for an urgent reassessment of current security strategies and vendor management practices.
Social Engineering: The Science of Human Hacking

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot












![CYBER SECURITY FOR TOP EXECUTIVES: Everything you need to know about Cybersecurity by [Alejandra Garcia]](https://m.media-amazon.com/images/I/51UZgLnDdYS.jpg)









