More on: How to Stop Your Remote Workforce from Being Hacked

InfoSec and Compliance – With 20 years of blogging experience, DISC InfoSec blog is dedicated to providing trusted insights and practical solutions for professionals and organizations navigating the evolving cybersecurity landscape. From cutting-edge threats to compliance strategies, this blog is your reliable resource for staying informed and secure. Dive into the content, connect with the community, and elevate your InfoSec expertise!
Apr 02 2021
“CISA has determined that this exploitation of Microsoft Exchange on-premises products poses an unacceptable risk to Federal Civilian Executive Branch agencies and requires emergency action,” the agency said in supplementary guidance to the earlier CISA Emergency Directive (ED) 21-02. “This determination is based on the current exploitation of these vulnerabilities in the wild, the likelihood of the vulnerabilities being exploited, the prevalence of the affected software in the federal enterprise, the high potential for a compromise of agency information systems, and the potential impact of a successful compromise.”
Apr 02 2021

Today, rapid digitalization has placed a significant burden on software developers supporting remote business operations. Developers are facing continuous pressure to push out software at high velocity. As a result, security is continuously overlooked, as it doesn’t fit into existing development workflows.
The way we build software is increasingly automated and integrated. CI/CD pipelines have become the backbone of modern DevOps environments and a crucial component of most software companies’ operations. CI/CD has the ability to automate secure software development with scheduled updates and built-in security checks.
Developers can build code, run tests, and deploy new versions of software swiftly and securely. While this approach is efficient, major data breaches have demonstrated a significant and growing risk to the CI/CD pipeline in recent months.
The growing threat to CI/CD pipelines
Pipeline as Code is a practical guide to automating your development pipeline in a cloud-native, service-driven world.

Apr 01 2021
The fundamentals of a formal, effective application security plan should start with business objectives, tools, processes and most of all, data, with the primary driver for securing applications focused on protecting data.
While it is important to surgically address the insecurities in a mission-critical application, it is equally important to continuously upskill the development and security teams, and create a culture where security is not looked at simply a ‘check-the-box’ item.
According to Setu Kulkarni, vice president of strategy at WhiteHat Security, the first step is to identify the right inflection points for injecting application security.
“CISOs need to recognize that no SDLC is built the same and no application is at the same level of maturity within its life cycle,” he said. “We have learned that testing applications continuously in production is critical to identify the real, exploitable vulnerabilities that create the maximum risk of being breached in production.”
Kulkarni noted one way to (almost always) ensure that security does not become an afterthought is to “top & tail” – in other words, make sure that your team gets a voice when the exit criteria is being defined during the requirements phase, and make sure the team is testing in pre-production and production.
“Everything in between is really a negotiation based on the maturity of the SDLC and the application itself. The most consequential best practice is to ensure that the Dev, Sec and Ops teams get accurate and actionable insight from the AppSec tests that are executed,” he said. “After all, the only way to eventually have security operate at the speed of DevOps is through some level of automation, and the efficacy of automation is directly proportional to the accuracy of the data used to drive the automation.”
Doug Dooley, COO of Data Theorem, pointed out that the business driver for AppSec is about privacy, trust and reputation that is directly tied to the brand of those who build and publish the applications.
He noted traditional AppSec testing focused on static and dynamic application security testing, including static application security testing (SAST) and dynamic application security training (DAST).
“However, with a more modern application stack, AppSec programs are starting to factor in third-party risks introduced by open source and software development kits, covered by software composition analysis,” Dooley explained.
Further, cloud-native applications make infrastructure services just another software extension of the application buildout, so many AppSec programs increasingly add cloud security tools, such as cloud security posture management (CSPM).

Apr 01 2021
New research suggests the overall state of cloud security continues to improve at a time when more organizations rely on multiple cloud service providers.
A survey of 1,900 security and IT professionals published this week by the Cloud Security Alliance (CSA) in collaboration with AlgoSec, a provider of network security tools, finds only 11% of respondents said they encountered a cloud security incident in the past year. The most common problems encountered were issues with a specific cloud provider (26%), security misconfigurations (22%) and attacks such as denial-of-service exploits (20%).
When asked about the impact of the cloud outages, more than a quarter of respondents said it took more than half a day to recover.
Despite growing confidence in cloud platforms, however, security remains a major area of focus. Top areas of concern include network security (58%), lack of cloud expertise (47%), migrating workloads to the cloud (44%) and insufficient staff to manage cloud environments (32%). In all, 79% of respondents noted some kind of issue involving IT staffing.
In the report, 52% of respondents reported they employed cloud-native tools to manage security as part of their application orchestration process, with half (50%) using orchestration and configuration management tools such as Ansible, Chef and Puppet. Less than a third (29%) said they used manual processes to manage cloud security.
Less clear, though, is who within the IT organization is responsible for cloud security. More than a third (35%) said their security operations team managed cloud security, followed by the cloud team (18%) and IT operations (16%). Other teams, such as network operations, DevOps and application owners, are all below 10%, the survey found.

Apr 01 2021
CDN and cybersecurity firm Akamai warns of a worrying escalation in ransom DDoS attacks since the beginning of the year.
The company recently mitigated three of the six biggest volumetric DDoS attacks it has ever dealt, two of which were ransom DDoS attacks.
One of these two ransom DDoS attacks targeted a gambling company in Europe and peaked at 800Gbps, but the most worrisome aspect of the attack was its sophistication.
According to the company, the rise of the Bitcoin price is motivating the cybercriminals in intensifying their efforts and their attack bandwidth to carry out powerful attacks with extortion purposes.
“The most recent extortion attack — peaking at more than 800 Gbps and targeting a European gambling company — was the biggest and most complex we’ve seen since the widespread return of extortion attacks that kicked off in mid-August 2020. Since the start of the campaign, show-of-force attacks have grown from 200+ Gbps in August to 500+ Gbps by mid-September, then ballooned to 800+ Gbps by February 2021.” reads the analysis published by Akamai. “But the size of the extortion attack wasn’t the only notable characteristic of the actors’ modus operandi.”

Mar 31 2021
IETF has formally deprecated the TLS 1.0 and TLS 1.1 cryptographic protocols because they lack support for recommended cryptographic algorithms and mechanisms
The Internet Engineering Task Force (IETF) formally deprecates Transport Layer Security (TLS) versions 1.0 (RFC 2246) and 1.1 (RFC 4346). Both versions lack support for current and recommended cryptographic algorithms and mechanisms. TLS version 1.2 was recommended for IETF protocols in 2008 and became obsolete with the introduction of TLS version 1.3 in 2018.
The TLS protocol was designed to allow client/server applications to communicate over the Internet in a secure way preventing message forgery, eavesdropping, and tampering.
The move to deprecate old versions aims at making products using them more secure.
The IETF now only recommends the use of the two latest versions TLS 1.2 and TLS 1.3.
Experts pointed out that older versions of the protocol were using cryptographic algorithms that were hit by multiple attacks over the years, including as BEAST, LUCKY 13, POODLE, and ROBOT.
Recently the US National Security Agency (NSA) published a guide urging organizations on eliminating obsolete Transport Layer Security (TLS) protocol configurations.
However, the number of organizations that are still using the deprecated versions of the protocol is still high.

Mar 31 2021
Ismael Valenzuela (McAfee/SANS) and Vicente Diaz (Threat Intel Strategist at Virustotal)
SANS Institute‘s #SEC530 course co-authored by Ismael Valenzuela (@aboutsecurity), providing students access to VTIntelligence to help them make TTPs actionable.
MITRE Enterprise ATT&CK Framework
Comparing Layers in ATT&CK Navigator – MITRE ATT&CK®
Mar 31 2021
When it comes to data protection, security and compliance, organizations must keep the potential technology risk within acceptable limits, which means mobilizing efforts to identify data lakes and applications where personally identifiable information (PII) and other sensitive information is stored. Organizations should then use digital transformation as the catalyst to lock those applications down with the proper controls to prevent the unauthorized use of data and use analytics to gain visibility into the management-sensitive data.
The key to any data privacy compliance is proper data protection because under these laws, consumers retain the right to deny and revoke the collection of their data. The first step in any plan around compliance is to have a basic understanding of whose data you have, where it is, and who has access to it. This principle is the foundation of identity management and governance.
Source: 3 steps to meeting data privacy regulation compliance through identity programs
Active Directory Administration Cookbook: Actionable, proven solutions to #identitymanagement and authentication on servers and in the cloud

Mar 31 2021

Cyber Strategy – Risk-driven Security and Resiliency
Provides a process and roadmap for any company to develop its unified Cybersecurity and Cyber Resiliency strategies. It demonstrates a methodology for companies to combine their disassociated efforts into one corporate plan with buy-in from senior management that will efficiently utilize resources, target high risk threats, and evaluate risk assessment methodologies and the efficacy of resultant risk mitigations. The book discusses all the steps required from conception of the plan from preplanning (mission/vision, principles, strategic objectives, new initiatives derivation), project management directives, cyber threat and vulnerability analysis, cyber risk and controls assessment to reporting and measurement techniques for plan success and overall strategic plan performance. In addition, a methodology is presented to aid in new initiative selection for the following year by identifying all relevant inputs.
“This is the tour de force on designing, implementing and maintaining a modern cyber security and resiliency program. This book is a necessity for all information security and resiliency professionals.” – Howard Taylor, CISO of Radware
This book lays out a systematic process for developing corporate strategy in the area of cyber (meaning IT) security and resilience.
NBlog – book review on “Cyber Strategy” discuss pros & cons
Mar 30 2021
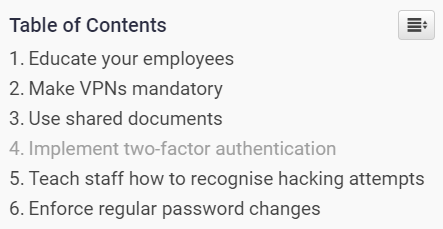
A summary of the tactical and strategic moves CISOs can make to reduce security risk:
Are you doing enough? Do you understand your risks? What if the brightest aren’t always the best choice for your company?
The Smartest Person in the room
![The Smartest Person in the Room: The Root Cause and New Solution for Cybersecurity by [Christian Espinosa]](https://m.media-amazon.com/images/I/41KIWmjt6sL.jpg)
Mar 30 2021
Here are five signs that a virtual CISO may be right for your organization.
Companies produce more data than ever, and keeping track of it all is the first step to securing it. A virtual CISO can identify what data needs to be protected and determine the negative impact that compromised data can have, whether that impact is regulatory, financial or reputational.
Risk increases with employee count, but there are many additional factors that contribute to an organization’s complexity: the number of departments, offices and geographies; how data is used and shared; the distribution of architecture; and the life cycle of applications, data and the technology stack.
A virtual CISO offers an unbiased, objective view, and can sort out the complexity of a company’s IT architecture, applications and services. They can also determine how plans for the future add complexity, identify and account for the corresponding risk, and recommend security measures that will scale to support future demand.
For many organizations, potential vulnerabilities, especially those that share a great deal of data within the organization, may not be obvious at first glance. Virtual CISOs can identify both internal and external threats, determine their probability and quantify the impact they could have on your organization. And at a more granular level, they can determine if those same threats are applicable to competitors, which can help maintain competitiveness within your market.
Organizations in regulated industries like healthcare, finance, energy/power and insurance will have data that is more valuable, which could make them a bigger target for bad actors. Exposure is even more of a concern due to potential noncompliance. Virtual CISOs bring a wealth of expertise on regulatory standards. They can implement processes to maintain compliance and offer recommendations based on updates to applicable rules and regulations.
An organization without a great deal of sensitive data may have a much greater tolerance for risk than a healthcare provider or a bank, but an honest assessment is important in determining how much risk each organization should accept. A virtual CISO can coordinate efforts to examine perceived and actual risk, identify critical vulnerabilities and provide a better picture of risk exposure that can inform future decisions.
Cybersecurity is growing more complex, and organizations of all sizes, especially those in regulated industries, require a proven security specialist who can address the aforementioned challenges and ensure that technology and processes are in place to mitigate security risks.

Mar 29 2021
Mar 29 2021
DEVSECOPS
Enough about culture and on to DevSecOps. What kind of culture allows it to thrive?
This kind of culture leads, not to diminishing returns, but to cohesion in the team and growth in technical acumen. Do those failures get pointed out and documented? Of course – the team doesn’t really want to spend another 4 hours on another night correcting the same mistake. The person doesn’t get called out, but the failure gets pointed out.
DevSecOps culture also lends itself to letting those doing the work determine what works best for them, which empowers them to be better professionals. Over time, the team notices patterns in failures and successes, and knows best what product or service would overcome those failures and automate successes.
Perhaps you aren’t currently part of a corporate culture for proper DevSecOps to thrive, for whatever reason (e.g., current management attitude, a change in leadership). You could work on creating a subculture. You might have a co-worker with whom you can work to make improvements while not negatively impacting the current speed of production. Or you have some leeway to introduce a tool that can help slightly.
Regardless of what else it’s called – DevOps with a security focus, DevOpsSec, Secure DevOps – the end result is to have Development, Operations, and Security work together to iteratively create a good and secure product that is delivered timely. When the culture adopts these elements, DevSecOps will flourish.

Mar 29 2021
We’ve recently witnessed large companies that were hit with major data breaches and cybersecurity incidents point the finger of blame at the lowest hanging fruit – their employees. While it’s understood that employees have a certain level of accountability when it comes to their role in the organization’s broader security strategy, it’s up to company leadership to arm them with the resources and knowledge to effectively thwart cyber threats.
With 90% of security incidents stemming from human error, a culture strong in security awareness is no longer a nice-to-have, it is a top priority and an absolute must across all organizations, regardless of their size or industry. Businesses who change risky employee behavior methodically and effectively through personalized, timely, and relevant learning will see an improvement to their overall security posture and a reduction in the number of security incidents.
Cyber threats today have become increasingly sophisticated and more personalized. Therefore, it stands to reason that the training and coaching offered to employees needs to meet the same level of personalization in order to effectively combat these threats and change risky habits and behaviors over time.
Transformational Security Awareness


Mar 29 2021
We’re sure you’ve heard of OpenSSL, and even if you aren’t a coder yourself, you’ve almost certainly used it.
OpenSSL is one of the most popular open-source cryptography libraries out there, and lots of well-known products rely on it, especially on Linux, which doesn’t have a standard, built-in encryption toolkit of its own.
Even on Windows and macOS, which do have encryption toolkits built into their distributions, you may have software installed that includes and uses OpenSSL instead of the operating system’s standard cryptographic libraries.
As its name suggests, OpenSSL is very commonly used for supporting network-based encryption using TLS, which is the contemporary name for what used to be called SSL.
TLS, or transport layer security, is what puts the padlock into your browser, and it’s probably what encrypts your email in transit these days, along with protecting many other online communications initiated by your computer.
So, when an OpenSSL security advisory reports exploitable vulnerabilities in the software…
…it’s worth paying attention, and upgrading as soon as you can.

Mar 29 2021
Unknown attackers hacked the official Git server of the PHP programming language and pushed unauthorized updates to insert a backdoor into the source code.
On March 28, the attackers pushed two commits to the “php-src” repository hosted on the git.php.net server, they used the accounts of Rasmus Lerdorf, the PHP’s author, and Jetbrains developer Nikita Popov.
Maintainers of the project are investigating the supply chain attacks, experts believe attackers have compromised the git.php.net server.
“We don’t yet know how exactly this happened, but everything points towards a compromise of the git.php.net server (rather than a compromise of an individual git account).” wrote Popov. “While investigation is still underway, we have decided that maintaining our own git infrastructure is an unnecessary security risk, and that we will discontinue the git.php.net server. Instead, the repositories on GitHub, which were previously only mirrors, will become canonical. This means that changes should be pushed directly to GitHub rather than to git.php.net.”
The maintainers of the PHP reverted the changes and are reviewing the repositories to detect any other evidence of compromise beyond the two referenced commits.
In the future, in order to access the repositories, users will now need to be part of the php organization on GitHub and their account will have 2FA enabled. Adopting this new configuration it is possible to merge pull requests directly from the GitHub web interface.
At this time, it is not immediately clear if the backdoor was downloaded and distributed by other parties before the malicious commits were detected.