Living-off-the-land (LotL) techniques in cyber attacks refer to the use of legitimate, native tools already present in the target system to carry out malicious activities. This approach is particularly stealthy because it leverages tools and processes that are typically trusted and thus less likely to raise alarms. In the context of Operational Technology (OT) or Industrial Control Systems (ICS), such attacks can be especially dangerous due to the critical nature of the systems involved. Here’s how such an attack might work, with examples:
1. INITIAL ACCESS
- Example: A phishing email is sent to an employee in the OT/ICS environment. The email contains a seemingly harmless document that, when opened, executes a PowerShell script (a native Windows tool) to create a backdoor.
2. LATERAL MOVEMENT
- Example: Once inside the network, attackers might use legitimate system administration tools like Windows Management Instrumentation (WMI) or Remote Desktop Protocol (RDP) to move laterally across the network, searching for critical OT/ICS components.
3. ELEVATION OF PRIVILEGES
- Example: Attackers might use built-in tools like Netstat to identify security software or firewall settings and then use other native scripts or commands to disable these defenses, or to elevate their access privileges within the system.
4. DISCOVERY AND INFORMATION GATHERING
- Example: Tools like Tasklist or Systeminfo (native to Windows) are used to gather information about the system, such as running processes, installed software, or network configurations relevant to the OT/ICS environment.
5. EXPLOITATION AND MANIPULATION
- Example: In an ICS environment, attackers might use standard industrial communication protocols like Modbus or DNP3 (which are legitimate and essential for normal operations) to send malicious commands to control systems, potentially disrupting physical processes like power generation or water treatment.
6. PERSISTENCE AND EXFILTRATION
- Example: Attackers could use standard data transfer tools like FTP or even Windows BITS (Background Intelligent Transfer Service) to exfiltrate stolen data, or to maintain persistence by regularly updating malware or downloading additional tools.
7. CLEANUP
- Example: To erase their tracks, attackers might use native cleanup tools or scripts to delete logs or any evidence of their activities, making detection and forensics much more difficult.
In late 2022, a significant cyber-physical incident occurred in Ukraine, attributed to the Russia-linked threat actor Sandworm. This event targeted Ukrainian critical infrastructure and utilized a multi-event cyber attack strategy, incorporating innovative techniques to impact industrial control systems (ICS) and operational technology (OT). The Sandworm actor employed OT-level living-off-the-land (LotL) techniques, likely causing a substation’s circuit breakers to trip and resulting in an unplanned power outage. This outage coincided with mass missile strikes across Ukraine’s critical infrastructure. Additionally, Sandworm executed a second disruptive event by deploying a new variant of CADDYWIPER malware in the victim’s IT environment.
This attack exemplifies the latest advancements in Russia’s cyber-physical attack capabilities, particularly visible since Russia’s invasion of Ukraine. The techniques used indicate a maturing offensive OT arsenal, capable of identifying novel OT threat vectors, developing new capabilities, and leveraging various types of OT infrastructure for attacks. Utilizing LotL techniques likely reduced the time and resources required for the cyber-physical attack. Although the initial intrusion point remains undetermined, the rapid development of the OT component of this attack suggests the actor’s ability to swiftly create similar capabilities against other OT systems globally.
Sandworm, active since at least 2009, is a versatile threat actor conducting espionage, influence, and attack operations, primarily supporting Russia’s Main Intelligence Directorate (GRU). The group’s primary focus has been Ukraine, where it has orchestrated disruptive and destructive attacks using wiper malware, especially during Russia’s re-invasion in 2022. However, Sandworm’s activities extend globally, underlining the Russian military’s extensive ambitions and interests in various regions. The group’s global threat activity and novel OT capabilities necessitate proactive measures from OT asset owners to mitigate potential risks.
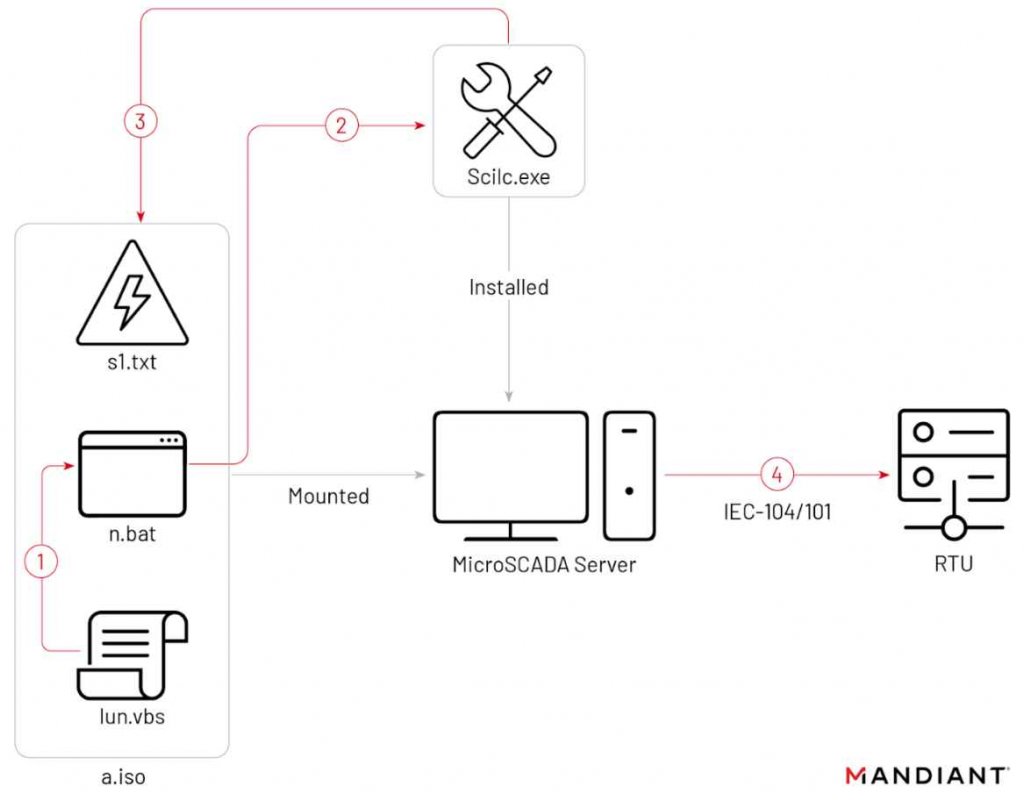
As per mandiant research, the 2022 intrusion began or prior to June 2022, culminating in two disruptive events on October 10 and 12. Sandworm accessed the OT environment via a hypervisor hosting a SCADA management instance for a substation, potentially having SCADA system access for up to three months. On October 10, Sandworm used an optical disc (ISO) image, “a.iso,” to execute a native MicroSCADA binary, likely for malicious control commands to switch off substations. The attackers, got into the operational technology (OT) system through a key piece of software (a hypervisor) that managed the control system (SCADA) of a power substation. This means they had access to the system that controls how the power substation works. For up to three months, they could have been inside this system without being detected. On October 10, they used a special file (an ISO image named “a.iso”) to run a command in the control system that was likely intended to turn off power substations.
This case underscores the evolving nature of cyber threats, particularly in critical infrastructure sectors. The increasing sophistication and rapid development of such attacks highlight the need for enhanced cybersecurity measures, continuous monitoring, and preparedness against novel and complex cyber threats in OT and ICS environments.
In OT/ICS environments, such LotL attacks are particularly concerning because they:
- Are harder to detect due to the use of legitimate tools.
- Can cause significant physical and operational damage.
- May bypass traditional security measures that don’t account for malicious use of native tools.
Defending against such attacks requires a combination of robust cybersecurity practices, including employee training, network segmentation, constant monitoring for anomalous behaviors, and regular updating and patching of all systems.
Business internet safety guide
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory