- GRC Solutions offers a collection of self-assessment and gap analysis tools designed to help organisations evaluate their current compliance and risk posture across a variety of standards and regulations. These tools let you measure how well your existing policies, controls, and processes match expectations before you start a full compliance project.
- Several tools focus on ISO standards, such as ISO 27001:2022 and ISO 27002 (information security controls), which help you identify where your security management system aligns or falls short of the standard’s requirements. Similar gap analysis tools are available for ISO 27701 (privacy information management) and ISO 9001 (quality management).
- For data protection and privacy, there are GDPR-related assessment tools to gauge readiness against the EU General Data Protection Regulation. These help you see where your data handling and privacy measures require improvement or documentation before progressing with compliance work.
- The Cyber Essentials Gap Analysis Tool is geared toward organisations preparing for this basic but influential UK cybersecurity certification. It offers a simple way to assess the maturity of your cyber controls relative to the Cyber Essentials criteria.
- Tools also cover specialised areas such as PCI DSS (Payment Card Industry Data Security Standard), including a self-assessment questionnaire tool to help identify how your card-payment practices align with PCI requirements.
- There are industry-specific and sector-tailored assessment tools too, such as versions of the GDPR gap assessment tailored for legal sector organisations and schools, recognising that different environments have different compliance nuances.
- Broader compliance topics like the EU Cloud Code of Conduct and UK privacy regulations (e.g., PECR) are supported with gap assessment or self-assessment tools. These allow you to review relevant controls and practices in line with the respective frameworks.
- A NIST Gap Assessment Tool helps organisations benchmark against the National Institute of Standards and Technology framework, while a DORA Gap Analysis Tool addresses preparedness for digital operational resilience regulations impacting financial institutions.
- Beyond regulatory compliance, the catalogue includes items like a Business Continuity Risk Management Pack and standards-related gap tools (e.g., BS 31111), offering flexibility for organisations to diagnose gaps in broader risk and continuity planning areas as well.
Self-assessment tools
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
- AI Agents and the New Cybersecurity Frontier: Understanding the 7 Major Attack Surfaces
- Understanding AI/LLM Application Attack Vectors and How to Defend Against Them
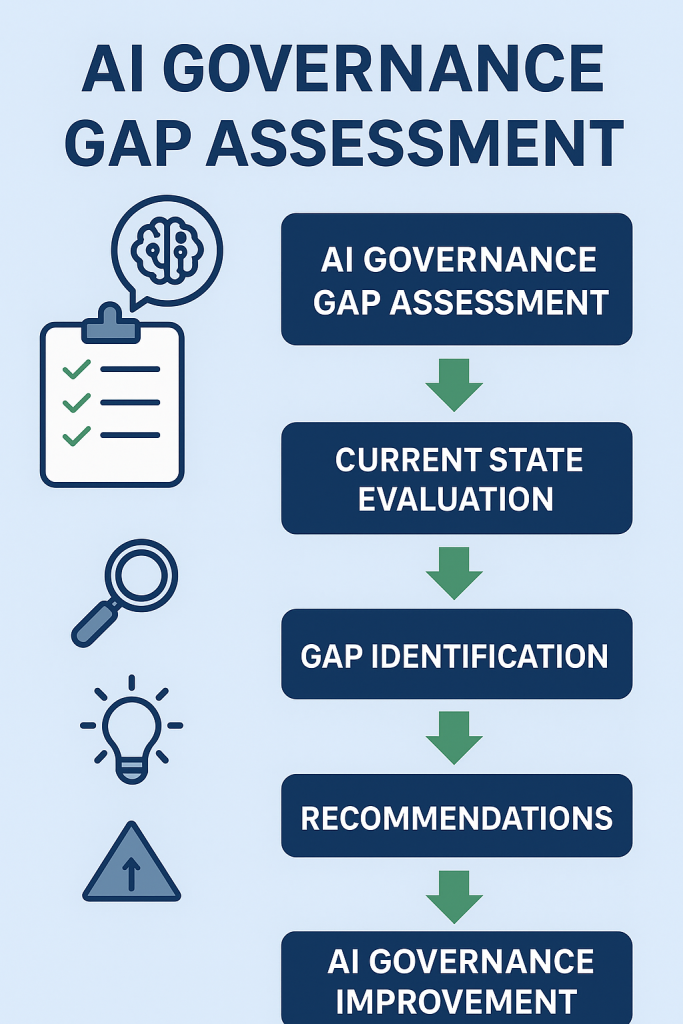
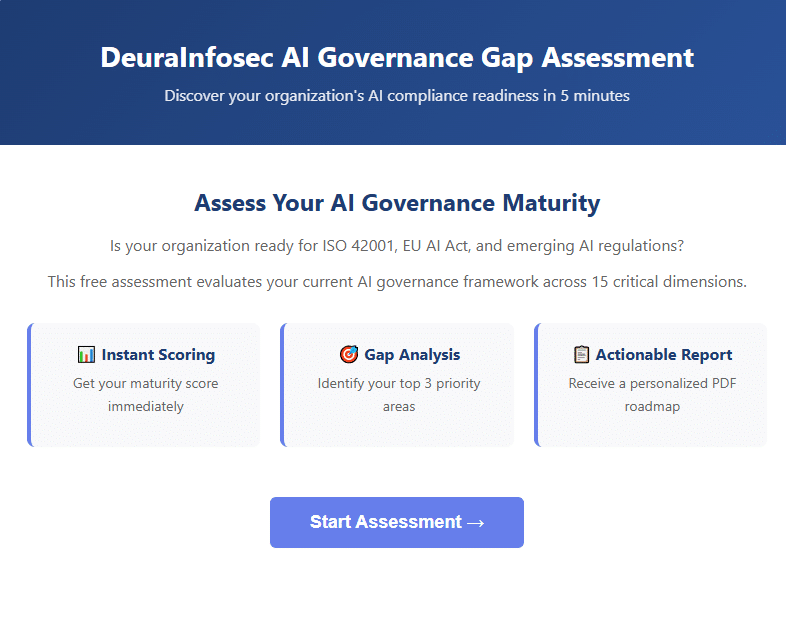
- AI Governance Assessment for ISO 42001 Readiness
- Beyond ChatGPT: The 9 Layers of AI Transforming Business from Analytics to Autonomous Agents
- CMMC Level 2 Third-Party Assessment: What It Is, Why It Matters, and What to Expect