In the past, Citrix was found to have a Zero-Day vulnerability in its Citrix NetScaler Application Delivery Controller (ADC), which made it possible for malicious actors to carry out remote code execution.
It was discovered that the zero-day vulnerability was being used in the wild, hence it was assigned the CVE ID 2023-3519 and the severity rating of 9.8 (Critical). Citrix did provide fixes to address the vulnerability, but there was no way to determine whether or not a particular Citrix appliance had been compromised.
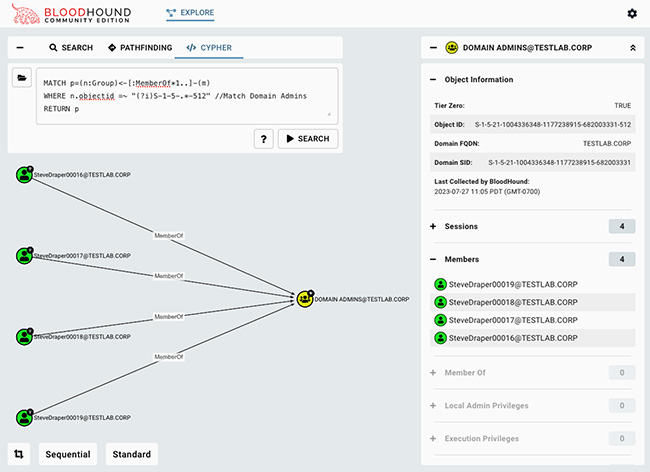
A new report states that it has been discovered that more than 1900 NetScalers are still infected with a backdoor. This information was obtained during a recent investigation.
Mandiant has launched a tool to assist business defenders in determining whether Citrix networking devices have been hacked in light of the fact that thousands of Citrix networking products are still susceptible to a major vulnerability that has not been patched and are accessible on the internet.
Citrix ADC and Citrix Gateway version 13.1, Citrix ADC and Citrix Gateway version 13.0, Citrix ADC and Citrix Gateway version 12.1, Citrix ADC, and Citrix Gateway version 12.0 are all compatible versions with which the IoC Scanner may be utilized.
On July 18, Citrix released a patch for the zero-day critical vulnerability (CVE-2023-3519) in its NetScaler application delivery controller and gateway products. The company also recommended that businesses that use the vulnerable products immediately deploy the fix. The vulnerability might be exploited to allow for the execution of unauthenticated remote code. The vulnerability is already being aggressively exploited by a number of threat organizations, who are doing so by establishing web shells within corporate networks and carrying out hundreds of attacks.
According to the findings of the researchers, there are still close to 7,000 examples available on the web. Around 460 of them had Web shells installed, most likely as a result of being compromised.
This application, which may be found on GitHub, was developed by Mandiant and has the ability to determine the file system paths of known malware, post-exploitation activities in shell history etc. The independent Bash script may be executed directly on a Citrix ADC device to search for known indications in files, processes, and ports. (The utility must be executed on the appliance in live mode while logged in as root.) According to Mandiant, it can also examine a forensic image that has been mounted for use in an investigation.
This application has a wide variety of functionality, such as scanning,
File system path that could be a malware
Shell history for suspicious commands
NetScaler directories and files that match with IOCs
Suspicious file permissions or ownership
Instances of Crontab
Malicious processes running on the system
This solution, which was created in partnership with Citrix and Mandiant, has the only purpose of assisting enterprises in preventing compromised systems and scanning for evidence of their presence.
According to Mandiant, the IoC Scanner will do a “best-effort job” of detecting compromised items; nevertheless, it is possible that it may not be able to locate all infected devices or determine whether or not the device is susceptible to being exploited. According to the company, “This tool is not guaranteed to find all evidence of compromise, or all evidence of compromise related to CVE 2023-3519,” which is a vulnerability.
InfoSec tools | InfoSec services | InfoSec books | Follow our blog