What is ISO 27002?
ISO 27002, officially named “ISO/IEC 27002 Information Security, Cybersecurity and Privacy Protection – Information Security Controls,” is a widely used and well-known information security standard published by the International Organization for Standardization (ISO). ISO 27002 provides detailed guidelines for the implementation of the controls listed in ISO 27001 Annex A, because ISO 27001 provides only a high-level description of each control. ISO 27002 has become an internationally recognized set of industry best practices that support the implementation of ISO 27001.
The basics
What is the purpose of ISO 27002?
The main purpose of ISO 27002 is to help organizations implement the Annex A controls from ISO 27001, because ISO 27001 does not provide explanations for how these controls should be implemented. ISO 27002 is designed to work in conjunction with ISO 27001, as ISO 27001 describes how to manage security by implementing an Information Security Management System (ISMS).
Why is ISO 27002 important?
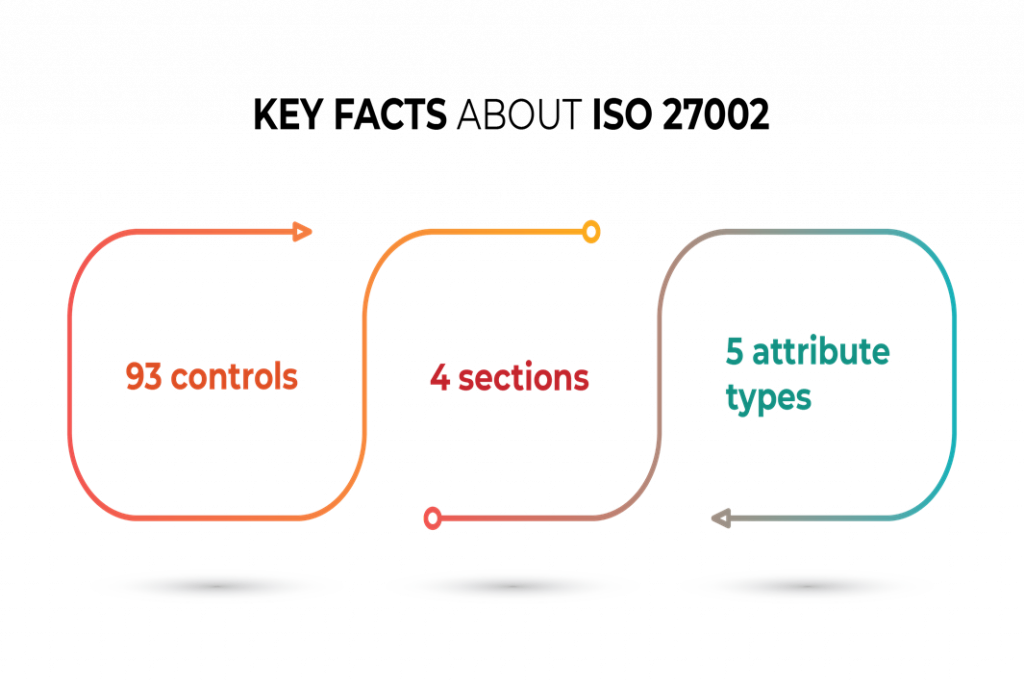
ISO 27002 is important because it is the only standard in the ISO 27k series that provides implementation guidance on all 93 controls defined in Annex A of ISO 27001. By using the detailed guidance in ISO 27002, companies can have a much better understanding of the best practices for controls.
ISO 27002 certification – Is it possible?
Certification against ISO 27002 is not possible. ISO 27002 is non-certifiable because, unlike ISO 27001, it is not a management standard. Instead, ISO 27002 is a code of practice (or best practices) for the implementation of security controls that support the ISMS defined in ISO 27001.
How does ISO 27002 support the ISMS?
ISO 27002 supports the ISMS by providing detailed guidance on how to implement the controls necessary to establish and operate an ISMS within a company. For example, ISO 27002 takes a whole page to explain one control, while ISO 27001 dedicates only one sentence to each control. This ensures that organizations have a comprehensive set of guidelines to use as a framework to deploy an effective ISMS in a structured manner.
What is the current version of ISO 27002?
As of the publication date of this article, the current version of ISO 27002 is ISO/IEC 27002:2022. The new 2022 revision of ISO 27002 was published on February 15, 2022.
What is the difference between ISO 27001 and 27002?
As already explained in brief, ISO 27001 is the main standard, and companies can get certified against it; companies cannot certify against ISO 27002:2022 because it is only a supporting standard.
In its Annex A, ISO 27001 provides a list of security controls and what must be achieved with those controls, but it does not explain how they can be implemented. ISO 27002 lists those very same controls and provides guidance on how they could be implemented; however, this guidance in ISO 27002 is not mandatory, i.e., companies can decide whether to use those guidelines or not.
Requirements & security controls
What are the requirements for ISO 27002?
ISO 27002 does not contain explicit requirements for companies to follow — for requirements, you should see ISO 27001. However, ISO 27002 does provide guidance on information security controls that can be applied in an organization.
What are the sections of ISO 27002?
The structure of ISO 27002 is listed and briefly explained below:
- Clause 5: Organizational controls – This section contains all controls related to various organizational issues, comprising 37 controls.
- Clause 6: People controls – This section focuses on controls related to human resources security, comprising 8 controls.
- Clause 7: Physical controls — This section focuses on controls related to the physical environment and equipment, comprising 14 controls.
- Clause 8: Technological controls — This section focuses on controls related to technological solutions, comprising 34 controls.
- Annex A: Using attributes — This annex provides a matrix of all the new controls, it compares their attributes, and provides suggestions on how to use the controls according to their attributes.
- Annex B: Correspondence with ISO/IEC 27002:2013 — This annex provides a mapping between controls from the 2022 revision and the controls from the previous 2013 version.
What is a security control?
ISO 27002 defines a control as “a measure that modifies and/or maintains risk.” Put simply, a control (or a safeguard) is a practice that can be implemented to reduce a risk to an acceptable level. Some examples of security controls include an Access control policy (5.15), Configuration management (8.9), and Secure coding (8.28).
How many controls are there in ISO 27002?
The 2022 revision of ISO 27002 has reduced the number of controls from 114 to 93. Some of the reasons for this reduction in the number of controls include technological advancements and an improvement in the understanding of how to apply security practices.
What are control attributes?
Control attributes provide a standardized way to sort and filter controls against different views to address the needs of different groups.
Attributes options for each control are as follows:
- Control types: Preventive, Detective, and Corrective
- Information security properties: Confidentiality, Integrity, and Availability
- Cybersecurity concepts: Identify, Protect, Detect, Respond, and Recover
- Operational capabilities: Governance, Asset management, Information Protection, Human Resource Security, Physical Security, System and Network Security, Application Security, Secure Configuration, Identity and Access Management, Threat and Vulnerability Management, Continuity, Supplier Relationships Security, Legal and Compliance, Information Security Event Management, and Information Security Assurance
- Security domains: Governance and Ecosystem, Protection, Defense, and Resilience
These attributes will ease the integration of ISO 27002:2022 controls with other similar security frameworks, like NIST Risk Management Framework. You can read more about the differences between the 2013 and 2022 versions of ISO 27002 in the last section of this article.
How are the controls structured?
The layout for each ISO control in ISO 27002 consists of the following elements:
- Control title: The short name of the control
- Attribute table: A table that shows the value(s) of each attribute for the given control
- Control: A brief description of the control
- Purpose: An explanation of why the control should be implemented
- Guidance: Instructions for how the control should be implemented
- Other information: Additional explanatory text, or references to related documents
The layout is designed to provide comprehensive information and guidance for each control, helping organizations understand and implement the necessary security measures.
How to implement ISO 27002 controls
To effectively implement ISO 27002 controls, follow a process that assesses the organization’s needs; identifies the appropriate controls, and customizes them if necessary; implements them using a structured approach; and then monitors, measures, and continuously improves them. Once completed, the implemented control should address needs at a combined technological, organizational/process, people, and documentation level.
For example, the implementation of control 8.9 Configuration management will address the following aspects:
Technology. The technology whose configuration needs to be managed could include software, hardware, services, or networks. Smaller companies will probably be able to handle configuration management without any additional tools, whereas larger companies probably need some software that enforces defined configurations.
Organization/processes. You should set up a process for proposing, reviewing, and approving security configurations, as well as the processes for managing and monitoring the configurations.
People. Make employees aware of why strict control of security configurations is needed, and train them to define and implement security configurations.
Documentation. ISO 27001 requires this control to be documented. If you are a small company, you can document the configuration rules in your security operating procedures. Larger companies will typically have a separate procedure that defines the configuration process.
Download ISO27000 family of information security standards today!
- ISO/IEC 27002:2022 – Code of Practice (Download now)
- ISO/IEC 27001 2022 – Specification (Download now)
- ISO27001 2013 ISMS Requirement (Download now)
- ISO27002 2013 Code of Practice for ISMS (Download now)
- ISO27003 – Implementation Guidance
- ISO27004 – Information Security Metrics
- ISO27005 – Information Security Risk Management
- ISO27006 – ISMS Certification Guide

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory




June 6th, 2024 8:56 am
[…] What is ISO 27002:2022 […]