May 18 2021
Detecting attackers obfuscating their IP address inside AWS
The feature and its exploitation potential
“Amazon Virtual Private Cloud (Amazon VPC) is a service that lets you launch AWS resources in a logically isolated virtual network that you define,” AWS explains.
Customers have complete control over their virtual networking environment, and can select their own IP address range, create subnets, and configure route tables and network gateways.
Unfortunately, the feature that allows customers to control their IP addresses also allows attackers to control the IP address written to AWS CloudTrail logs when accessing a compromised account via a newly created VPC endpoint.
“This can potentially enable an attacker to fool various security protections that rely on the Cloudtrail logs, such as SIEMs and cloud security tools. In addition, analysts looking for evidence of an attack might miss it,” Hunters researchers noted.
Attackers can obfuscate their IP address by making it look like an “organizational” public IP address, an employee “home” external IP address, a (potentially whitelisted) third party service provider public IP address, or a special private, reserved, testing or documentation-only IPv4 subnet block.
They could thus make it seem that a malicious action has been performed by an employee, or make it fly under the radar of threat intelligence and reputation services.
What attackers can’t do with this technique is to change the IAM permissions the attacker has when using victims’ compromised AWS API credentials, nor bypass IP-based IAM policies.
There is a solution
This technique may allow attackers to bypass security measures that rely solely on AWS CloudTrail, an AWS web service that allows customers to log, continuously monitor, and retain account activity related to actions across their AWS infrastructure (including AWS API activity).
Defenders should not rely on the contents of the “sourceIPAddress” field in the logs to detect attackers inside AWS, making API requests/calls, the researchers noted. Instead, they should review the “vpcEndpointID” field.
“If you use VPC endpoints in your environment, the only significant difference between the logs created by legitimate actions and the attacker’s actions is the specific VPC endpoint IDs logged. We recommend addressing this use-case with more anomalous-based detection logic, detecting usage of a new VPC endpoint ID never seen before in the organization,” the researchers advised.
They also recommended AWS CloudTrail users to cross-reference their cloud events with other sensors on endpoints, on-premises, email, identity, etc, to trace inconsistent logging and missed threats.

May 17 2021
Is 85% of US Critical Infrastructure in Private Hands?
When this problem is discussed, people regularly quote the statistic that 85% of US critical infrastructure is in private hands. It’s a handy number, and matches our intuition. Still, I have never been able to find a factual basis, or anyone who knows where the number comes from. Paul Rosenzweig investigates, and reaches the same conclusion.
Public Private Partnerships (PPP): Construction, Protection, and Rehabilitation of Critical Infrastructure
Discuss objectives and legal requirements associated with PPPs, the potential advantages and limitations of PPPs, and provide guidance as to how to structure a successful PPP for infrastructure investment.

Critical Infrastructure Risk Assessment

May 17 2021
Dealing with ransomware attacks: What options do you have?
It might seem logical to try to negotiate the ransom demand down to an amount that isn’t going to break the bank but would still be enough to satiate cybercriminals’ thirst for cash. Unfortunately, this isn’t a good idea, because negotiations can backfire and even cause ransomware gangs to increase their ransom demands.
This recently happened to Acer when they attempted to negotiate a $50 million ransomware demand down to $10 million. As retaliation, the REvil gang threatened to double the ransom if they didn’t receive the $50 million.
Another example is the Egregor ransomware gang, which often threatens to publish their victims’ data online if they negotiate or fail to deliver on ransom payments. If you’re not looking to add your company’s name to the list of failed negotiations, keep reading to find out some do’s and don’ts of planning for ransomware incidents.
DO: Create a plan before crisis strikes
A ransomware attack affecting your business in today’s digital economy is a matter of “when,” not “if.” Cybersecurity is an arms race, and as technological innovation grows, cybercriminals are also constantly innovating to develop new and more damaging attack methods. That’s why it’s essential to prepare for an attack as if it were as sure as the fact that the sky is blue – hopefully enabling you to avoid any negotiations altogether.
Dealing with ransomware attacks: What options do you have?
The Ransomware Threat Landscape : Prepare for, recognize and survive ransomware attacks
The fastest-growing malware in the world
The core functionality of ransomware is two-fold: to encrypt data and deliver the ransom message. This encryption can be relatively basic or maddeningly complex, and it might affect only a single device or a whole network.
Ransomware is the fastest-growing malware in the world. In 2015, it cost companies around the world $325 million, which rose to $5 billion by 2017 and is set to hit $20 billion in 2021. The threat of ransomware is not going to disappear, and while the number of ransomware attacks remains steady, the damage they cause is significantly increasing.

May 14 2021
Magecart gang hides PHP-based web shells in favicons
Magecart cybercrime gang is using favicon to hide malicious PHP web shells used to maintain remote access to inject JavaScript skimmers into online stores.
Magecart hackers are distributing malicious PHP web shells hidden in website favicon to inject JavaScript e-skimmers into online stores and steal payment information.
Researchers from Malwarebytes observed threat actors, likely Magecart Group 12, using this technique in attacks aimed at online stores running on Magento 1 websites.
The web shells employed in the attacks are tracked as Smilodon or Megalodon, they dynamically load JavaScript skimming code via server-side requests into online stores. This technique allows bypassing most client-side security tools.
“While performing a crawl of Magento 1 websites, we detected a new piece of malware disguised as a favicon. The file named Magento.png attempts to pass itself as ‘image/png’ but does not have the proper PNG format for a valid image file.” reads the analysis published by Malwarebytes.
May 13 2021
Security at Bay: Critical Infrastructure Under Attack
The attack perpetrated by hackers on oil company Colonial Pipeline highlights the dangers that are facing Industrial Control Systems (ICS) and the need for change in the information security landscape,
The attack took place on May 7th where hackers used ransomware to cripple the defense of the company. As a result, all operations were forced to shut down as well as operating systems used by the company. A group named DarkSide claimed to be responsible for Colonial Pipelines attack.
The hacker group is active since august and are part of a professional crime industry that have caused damage of billions of dollars. President Biden has delivery remarks that point out to the involvement of Russia in the development of the ransomware. It is not clear if the Colonial company has paid the demands.
The attack brought to light how critical national infrastructure (CNI) is vulnerable and the need of new methodologies to address new menaces that are evolving on a daily basis on many different ways. As far as we know this attack have proved that the understanding of information security has become outdated as well the solutions that were supposed to protect companies assets.
The impact of the attack was far beyond then expected. Consumers were directely impacted with a hike on prices. Also, in South east some drivers started to stocking up as available oil dropped down in fuel stations. About 5,500 miles of pipeline were shutdown. To figure it out in numbers it represents 45% of fuel comsumed from texas to new york.
As reported by Recorded Future ransomware attack groups are gainning momentum and wide spreading throughout every and all sector. From industry to education everyone is on target of ransomware. It is importante to notice that hackers are publishing part of the data and demanding money to do not publish all the data stolen.
While the United States leads the attack of ransomware hackers are aiming to make other countries victims. Freedom and security are deeply rooted in the american dream, but today all the nation see this rights going down with the dangers of information security.
The US Department of Justice and a group of companies have created a task force to manage the issue of ransomware threat. However, the tools that were released by equation group in the past can be the tipping point to new attacks or development of new ways to bypass known protections.
Little is known yet how the company was breached but it was certanly that the goal was to obtain money instead of corrupting the system. Some parts of the system were restored and the company said it will update their systems. Part of operations are manual at this time but its not sure when the supplies will return to normal.
The question now is if the available supplies will be enough. The disruption of the supplies could lead to an impact on many sectors. Bitdefender released a decryption tool on january for an older version of the ransomware, but they said that for this new version the tool do not work. According to Bloomberg 100GB was stolen in just two hours. This is a remarkable event to be considered as the largest and successful act of cyberwarfare.
Finally we need to develop new systems and new tecnologies as this could be the starting of a surge of new threat actors and new attacks that can not be stopped by the actual protection solutions.
Sources:
https://therecord.media/ransomware-tracker-threat-groups-focus-on-vulnerable-targets/
May 13 2021
Researcher hacked #Apple #AirTag two weeks after its launch
The Apple AirTag has been available for just a couple of weeks and hacking community is already working on it to demonstrate that how to compromise it.
“The German security researcher Stack Smashing tweeted today (via The 8-bit) that he was able to “break into the microcontroller of the AirTag” and modified elements of the item tracker software.” reported the 9to5Mac website.
“A microcontroller is an integrated circuit (IC) used for controlling devices usually via a microprocessing unit, memory, and other peripherals. According to AllAboutCircuits, “these devices are optimized for embedded applications that require both processing functionality and agile, responsive interaction with digital, analog, or electromechanical components.”
Now, the German security researcher Stack Smashing claims that he was able to hack the Apple device breaking into its microcontroller and modifying its NFC URL for Lost Mode.
The researcher explained that has found a way to modify the tracker software running on the tag, he was able to modify its NFC URL.
Smashing published a video PoC of the hack, it shows two Apple AirTag devices and one of them was hacked by the researcher.
The regular item tracker used in the test opens the Find My website, while the modified one opens an arbitrary URL that was chosen by the expert.

May 12 2021
WiFi devices going back to 1997 vulnerable to new Frag Attack

Source: WiFi devices going back to 1997 vulnerable to new Frag Attack
A Belgian security researcher has discovered a series of vulnerabilities that impact the WiFi standard, with some bugs dating back as far back as 1997 and affecting devices sold for the past 24 years.
The vulnerabilities, known as Frag Attacks, allow an attacker within a device’s WiFi radio range to gather information about the owner and run malicious code to compromise a device, may it be a computer, smartphone, or other smart device.
Devices are also vulnerable even if the WiFi standard’s security protocols were activated, such as WEP and WPA.
Design flaws in the WiFi standard itself
“Three of the discovered vulnerabilities are design flaws in the WiFi standard and therefore affect most devices,” said Mathy Vanhoef, the Belgian academic and security researcher who found the Frag Attacks.
The rest are vulnerabilities caused “by widespread programming mistakes [in the implementation of the WiFi standard] in WiFi products,” Vanhoef said.
“Experiments indicate that every WiFi product is affected by at least one vulnerability and that most products are affected by several vulnerabilities,” said Vanhoef, who is also scheduled to give an in-depth talk about his findings later this year in August at the USENIX ’21 security conference.
“The discovery of these vulnerabilities comes as a surprise because the security of WiFi has in fact significantly improved over the past years,” the Belgian researcher said.
Prior to disclosing the Frag Attacks today, Vanhoef previously discovered the KRACK and Dragonblood attacks. Vanhoef’s previous findings have helped the WiFi standard improve its security posture, but his latest findings reside in older sections of the WiFi protocol, not improved by his previous discoveries, and already deployed with devices in the real world for decades.

May 11 2021
Significance of risk management in cyber insurance to determine premium
By DISC InfoSec
The limited availability of data on cyber incidents has made it difficult to develop full probabilistic models for use in pricing cyber insurance cover. While a few insurance companies, brokers and other companies have developed pricing models that provide quantifiable probabilistic estimates of potential losses based on Fair methodology, the vast majority of insurers still continue to use scenario-based approaches for estimating the potential frequency and severity of cyber incidents. Assessments of frequency and severity are usually based on publicly available data on past incidents. There are a few commercial companies that collect and market data on past incidents.
The insurability of a given risk is usually economically viable only where Risks must be quantifiable: the probability of occurrence of a given peril, its severity and its impact in terms of damages and losses must be assessable.
In the case of data confidentiality breaches, data on past breaches provides insurance companies with a basis to assess the level of risk based on different company characteristics and estimate the per record cost of a breach. Therefore, part of the underwriting process involves understanding the business activities and number and types of information records held by the company. Given the longer experience with data breach notification laws and the more developed stand-alone cyber insurance market, much of the available data is based on experience in the United States.
Insurance companies also focus significant attention on the company’s security practices and policies, depending on company size and amount of coverage being sought. For smaller companies/coverage amounts, the underwriting process will focus on basic cyber security practices such as use of a firewall, anti-virus/malware software and data encryption, as well as frequency of data backups and use of intrusion detection tools. In some cases, applications may ask about compliance with specific standards, such as the International Organization for Standardization standard on Information Security (ISO/IEC 27001); the US National Institute of Standards and Technology (NIST) Framework for Improving Critical Infrastructure Cybersecurity; or the UK Cyber Essentials. Companies that hold payment card information might also be asked about their compliance with the PCI Data Security Standard while US companies with health records might be asked about their compliance with Health Insurance Portability and Accountability Act security requirements. Some stand-alone cyber insurance applications also request information on plans and policies, such as data protection policies, network access policies, internal auditing policies, disaster recovery plans, etc., as well as governance processes in place for those policies. Larger companies would face additional scrutiny, potentially involving on-site interviews, security audits and/or penetration testing. Risk and vulnerability assessments by external security consultants are offered by some companies as an additional service included as part of the insurance policy.
Insurance companies use the information gathered through the underwriting process to determine premium levels or deny the coverage. Some insurers may also establish minimum security standards that must be maintained through the coverage period in order for coverage to be maintained or sustained, such as timely patching of vulnerabilities and/or other software updates.

Cyber-insurance is an insurance product used to protect businesses and individual users from Internet-based risks, and more generally from risks relating to information technology infrastructure and activities. Cyber insurance purchased by an insured (first party) from an insurer (the second party) for protection against the claims of another (the third party). The first party is responsible for its own damages or losses whether caused by itself or the third party.
Cyber insurance may offer services products and countermeasures to protect business from known and unknown risks. There are now mandatory breach notification state laws (in many states) and regulation (HIPAA) which require breach notification. In services area cyber insurance may help organization to cover the cost of notifications and sometime may notify on behalf of an organization. The breach notification service may be necessary for SMB’s to acquire due to lack of necessary in-house resources. Depending on your business, few other items you may want to consider under cyber insurance are data restoration cost, payment of ransom, identity theft protection and reissuing of cards, potential downtime due to DDoS and potential regulatory fines.
How does a second party, an insurance company determine that first party premium (an amount to be paid for an insurance policy) and even decide that first party is insurable. The insurance company will look at organization’s security posture maturity based on industry standards and regulations (ISO, NIST, CSC, CSF) and determine if their Security Program is worthy of cyber insurance. Based on the existing security posture of an organization the second party will determine the risk they are willing to take and first party will determine the cost they are willing to pay for the premium. In the some cases insured might be able to absorb losses of the breach which were not covered by insurance but for some SMB’s these losses may be business limiting.
A point–in-time evaluation of an organization’s information security posture in constantly evolving, threat landscape only increases the challenge of insurance company to determine the first party premium. The insurance company may require a continuous feed to an organization security posture dash board which may also include but not limited to monitoring of security incident response on regular basis. Before making a decision on cyber insurance premium, an insurance company should utilize an in-house expertise or collaborate with InfoSec consulting organization to evaluate the frequency and severity of cyber threats facing an organization information security management system.
At end of the day, cyber insurance is a proactive security measure to counter potential data breaches and network security failures. Routinely, organizations are willing to spend money on security initiatives after the breach which is reactive action. Proactive security measures such as (developing sound security policies, compulsory cloud security, continuous monitoring, strong security awareness, effective BCP, proactive patching, resilient incident response plan…) may help not only to reduce the overall risk landscape but can assist in lowering the cyber insurance premium.
Proactive information security program which include but not limited to the basic cybersecurity measures may require acquiring cyber insurance. Insured organization (first party) may need to keep up with the basic cyber security measures to prevent voiding the coverage. When a functional and operational information security program which has a clear definition of an organization risk threshold becomes a priority, it can minimize potential risk of security breach and should be able to absorb losses for future security breach with cyber insurance as a part of risk management strategy.
DISC InfoSec assist in acquiring the cyber insurance which is aligned with business objectives and based on organization risk threshold. Before coverage is issued by the underwriter, in some cases, organization is asked to mitigate some risks to lower the premium. DISC InfoSec assist in compliance with standards, coverage inclusion/exclusion and risk mitigation process for organization acquiring cyber insurance.
Cyberinsurers mandate multifactor authentication
Checkout our previous blog posts on cyber insurance
Cyber Insurance explained in a simple and joyful way.

More Cyber Insurance titles:

May 10 2021
City of Tulsa, is the last US city hit by ransomware attack
One of the biggest cities in the US by population size, the City of Tulsa, was victim of a ransomware attack that affected its government’s network and forced the shutdown of official websites over the weekend.
Shortly after the attack, that took place Friday night, the city issued a statement to inform that no customer information has been comprised in the security breach.
The City’s IT and security staff have shut down impacted internal systems to avoid the spreading of the threat. Emergency services such as 911 and the city’s public safety response will continue to operate normally.
“According to the Tulsa Police Department (TPD), 911 is operational and Tulsa’s public safety response is continuing as normal.” reported the Krmg website.
“As for utility billing, Tulsa police say new account registration is currently unavailable. Tulsans can make a payment on their account and view their bill as a guest as long as they have their new account number and customer ID, plus the name on their account exactly as it appears on their bill.”
The City of Tulsa reported the incident to the authorities and is investigating the infection with the help of external security experts.
The impact is believed to have impacted a small portion of the infrastructure, and internal experts are attempting to recover impacted systems from backups.
Unfortunately, ransomware attacks against cities in the US are very frequent and in many cases the victims opted to pay the ransomware to restore the operations.
City of Tulsa, is the last US city hit by ransomware attack
May 09 2021
iPhone Hack Allegedly Used to Spy on China’s Uyghurs

U.S. intelligence said that the Chaos iPhone remote takeover exploit was used against the minority ethnic group before Apple could patch the problem.
In 2019, a Chinese security researcher working with the internet security and antivirus company Qihoo 360 unveiled an intricately woven exploit: One that would allegedly let a remote attacker easily jailbreak an iPhone X iOS 12.1.
The researcher, Qixun Zhao, dubbed the exploit Chaos, for good reason. As this proof-of-concept video allegedly shows, a successful exploit would allow a remote attacker to jailbreak an iPhoneX, with the targeted user none the wiser, allowing the intruder to gain access to a victim’s data, processing power and more. It worked as a drive-by malware download, only requiring that the iPhone user visit a web page containing Qixun’s malicious code.
It would have made a superb spying tool, seeing how it would let an attacker easily take control of even the newest, most up-to-date iPhones, enabling a snooper to read a victim’s messages and passwords and to track their location in near-real time.
Source: iPhone Hack Allegedly Used to Spy on China’s Uyghurs

May 08 2021
Microsoft warns of a large-scale BEC campaign to make gift card scam
Microsoft is warning of a large-scale BEC campaign that targeted hundreds of organizations leveraging typo-squatted domains registered days before the attacks.
Business email compromise (BEC) attacks represent a serious threat for organizations worldwide, according to the annual report released by FBI’s Internet Crime Complaint Center, the 2020 Internet Crime Report, in 2020, the IC3 received 19,369 Business Email Compromise (BEC)/Email Account Compromise (EAC) complaints. The reports states that BEC/EAC crimes caused $1.8 billion in losses.
Now Microsoft is warning of a large-scale BEC campaign that targeted more than 120 organizations with gift card scam.
The attackers targeted organizations in multiple industries, including the consumer goods, process manufacturing and agriculture, real estate, discrete manufacturing, and professional services sectors. The threat actors leverage typo-squatted domains to trick the recipients into believing that the emails were originating from valid senders.
Microsoft warns of a large-scale BEC campaign to make gift card scam

May 08 2021
Records and Information Management: Fundamentals of Professional Practice

Records and Information Management: Fundamentals of Professional Practice, Fourth Edition presents principles and practices for systematic management of recorded information. It is an authoritative resource for newly appointed records managers and information governance specialists as well as for experienced records management and information governance professionals who want a review of specific topics. It is also a textbook for undergraduate and graduate students of records management or allied disciplines—such as library science, archives management, information systems, and office administration—that are concerned with the storage, organization, retrieval, retention, or protection of recorded information.
The fourth edition has been thoroughly updated and expanded to:
- Set the professional discipline of RIM in the context of information governance, risk mitigation, and compliance and indicate how it contributes to those initiatives in government agencies, businesses, and not-for-profit organizations
- Provide a global perspective, with international examples and a discussion of the differences in records management issues in different parts of the world. Its seven chapters are practical, rather than theoretical, and reflect the scope and responsibilities of RIM programs in all types of organizations.
- Emphasize best practices and relevant standards.
The book is organized into seven chapters that reflect the scope and responsibilities of records and information management programs in companies, government agencies, universities, cultural and philanthropic institutions, professional services firms, and other organizations. Topics covered include the conceptual foundations of systematic records management, the role of records management as a business discipline, fundamentals of record retention, management of active and inactive paper records, document imaging technologies and methods, concepts and technologies for organization and retrieval of digital documents, and protection of mission-critical records. In every chapter, the treatment is practical rather than theoretical. Drawing on the author’s extensive experience supplemented by insights from records management publications, the book emphasizes key concepts and proven methods that readers can use to manage electronic and physical records.
Records and Information Management 4th Edition by Dr. William Saffady now available
May 07 2021
Your Passwords Are Useless!
May 07 2021
Possible attacks on the TCP/IP protocol stack and countermeasures
The task of a computer security system is to safeguard the information transmitted over the network and to adequately preserve the data stored in it.
Excluding in this discussion threats due to natural disasters, we can classify the man-made risk, to which an information system is subject, into intentional threats or unintentional threats due to negligence or inexperience.
Businesses need to protect themselves from these threats, which can put both applications and assets at serious risk.
Intentional human threats can come from individuals with an interest in acquiring information or limiting the operation of business processes, driven by the pursuit of financial or political gain, or simply for fun.
An intentional attack can come from individuals outside the organisation or from internal staff such as ex-employees, disgruntled employees or malicious actors. In fact, personnel who are familiar with the security systems and the structure of the information system and who have the authorisation to access the system itself, can get hold of information or insert malicious code more easily.
The development of the Internet and the distributed processing of information over shared lines has certainly made security a necessary duty. Therefore, the corporate network, if not adequately protected, could be subject to unauthorized access with possible network compromise and information theft.
May 07 2021
Data leak implicates over 200,000 people in Amazon fake product review scam
There is an ongoing battle between the e-commerce giant and dubious sellers, worldwide, who wish to hamstring competitors and gain an edge by generating fake reviews for their products.
This can include paying individuals to leave a glowing review or by offering free items in return for positive, public feedback.
How they operate and stay under Amazon’s radar varies, but an open ElasticSearch server has exposed some of the inner workings of these schemes.
On Thursday, Safety Detectives researchers revealed that the server, public and online, contained 7GB of data and over 13 million records appearing to be linked to a widespread fake review scam.
It is not known who owns the server but there are indicators that the organization may originate from China due to messages written in Chinese, leaked during the incident.
The database contained records involving roughly 200,000 – 250,000 users and Amazon marketplace vendors including user names, email addresses, PayPal addresses, links to Amazon profiles, and both WhatsApp and Telegram numbers, as well as records of direct messages between customers happy to provide fake reviews and traders willing to compensate them.
According to the team, the leak may implicate “more than 200,000 people in unethical activities.”
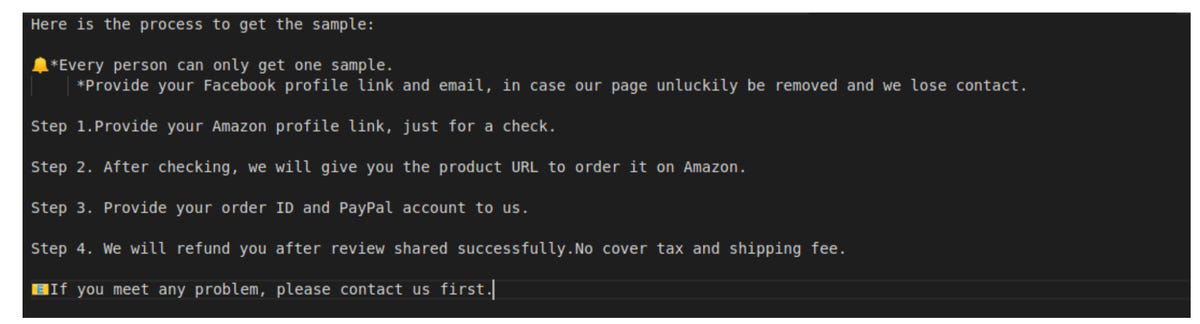
The database, and messages contained therein, revealed the tactics used by dubious sellers. One method is whereby vendors send a customer a link to the items or products they want 5-star reviews for, and the customer will then make a purchase.
Several days after, the customer will leave a positive review and will send a message to the vendor, leading to payment via PayPal — which may be a ‘refund,’ while the item is kept for free.
As refund payments are kept away from the Amazon platform, it is more difficult to detect fake, paid reviews.
Data leak implicates over 200,000 people in Amazon fake product review scam
« Previous Page — Next Page »








