No doubt, the digital frame is a hot state of the art technology item today. Some digital frames in the market carry a risk of infection through a
Trojan horse (malware) which is capable of monitoring keystrokes and sending useful information back to its originator. In Jan 2008 there were multiple reports that digital picture frames attempted to install malware on devices connected to the frame. It’s Jan 2009, and digital frames are still embedded with malwares.
According to SF chronicle article by Deborah Gage (Jan 2, 2009, pg. c1) “These popular devices are now so powerful that they’ve become computers in themselves, although people who buy them don’t always realize that. And like computers, the frames are capable of carrying code that logs keystrokes, steals data and calls out to other malicious code once it’s installed itself on a PC. “ “Users don’t realize that bad guys can make use of each and every computer they can control, even if you don’t do Internet banking or have any sensitive information,” said Karel Obluk, the chief technology officer of AVG, a security vendor with offices in the United States and Europe. “They can profit by spam or other illegal activities and make (your) PC part of an illegal network. It’s something that users should always be reminded of.”
Consumers have to be wary of devices which have memory on-board.
December 29, 2008 (Computerworld) Amazon.com Inc. last week warned customers running Windows XP that a Samsung digital photo frame it sold until earlier this month might have come with malware on the driver installation CD. Amazon’s advisory identified the malware as “W32.Sality.AE,” the name assigned by Symantec Corp.
According to Samsung’s alert, “a batch of Photo Frame Driver CDs contains a worm virus in the Frame Manager software. This is a risk of the customers host PCs being infected with this worm virus.”
The Samsung SPF-85H is no longer available on Amazon.com.
“Samsung has issued an alert. … Our records indicate that you have purchased one of the digital photo frames through the Amazon.com website and are therefore affected by this alert,” said Amazon in the note.
Based on various security advisories — Only users running Windows XP are at risk from this virus or a Trojan, Samsung and Amazon said; Windows Vista is immune.
Some considerations to safeguard against Trojans:
Turn off autorun in Windows, to stop Trojan and malware exploits from installing itself on your system.
To find a Trojan on your system, configure Windows to show hidden files.
Utilize antivirus software which look for Trojans and keep it turned on and up-to-date. Scan new devices for malware upon connection to a system.
Perform application vulnerability assessment on digital frame which will look for hidden Trojans.
Perform regular assessment to find new vulnerabilities
Buy photo frames manufactured by vendors who can guarantee exclusion of malwares.
Do your due diligence to find out for known vulnerabilities before buying a digital frame
Who should be responsible for to make sure digital frames are malware free or perhaps both? (consumer/vendors)
AP Impact: Viruses Hit Digital Photo Frames, GPS
httpv://www.youtube.com/watch?v=R19VKUyeXag
Tags: amazon, anti botnet, anti trojan, anti virus, anti worm, illegal network, infection, Malware, photo frame, samsung, Trojan horse


![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=fdb4c0e1-9dfb-4fb9-b9cc-67ec87f659a8)
![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=d4964396-d1ae-4bb1-9d8d-389448380f94)
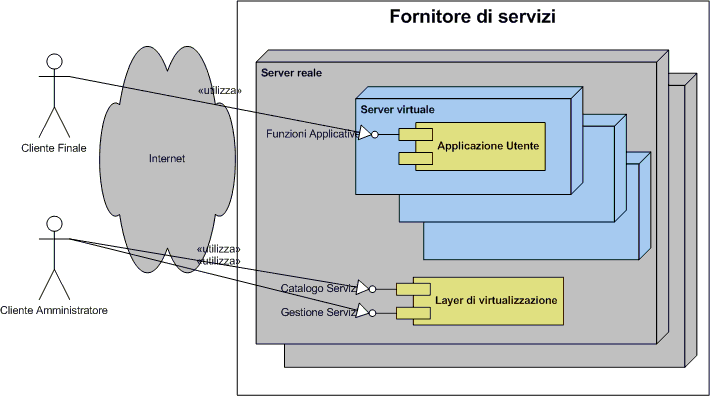

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=b3cd3c31-214f-4a4e-8317-417d5f9f3177)


![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=eea54cc4-9d5a-43d1-af8a-db857566fd66)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=388a1882-ddc8-487a-bc63-9310f0c69ecc)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=02d47642-2651-4395-b8dd-28e3a18dc505)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=28dcae72-914e-4823-9632-cd34145194b7)

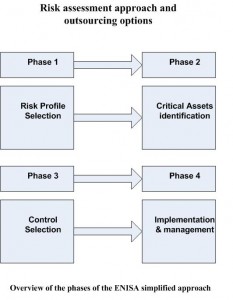
![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=f4c7607a-8a48-4ed1-bba2-9bb41450aa23)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=a4367ffd-91c3-481f-b56e-6c1bbc7cc7ea)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=6b35ca8c-42a0-4753-be84-5a6d5b4c5394)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=7df2ef1d-242f-4110-8903-59f134349e57)
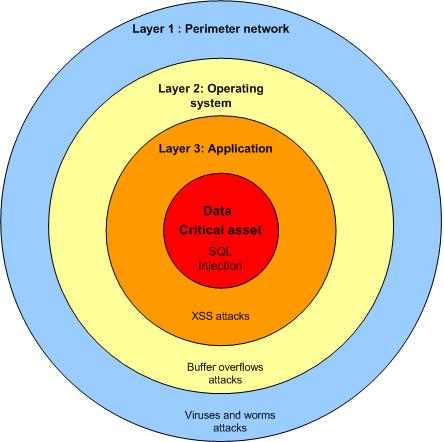
 The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level.
The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level. 




![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=7906ca23-c8d5-4148-9905-df5252c98958)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=9f925ef4-f878-4862-8d25-1401b5ee1189)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=6ccd3b7c-e7f3-4bb6-bd66-6c81a2930cba)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=cfd48ae7-5a1d-4bec-bec0-786b2dbb25ac)



