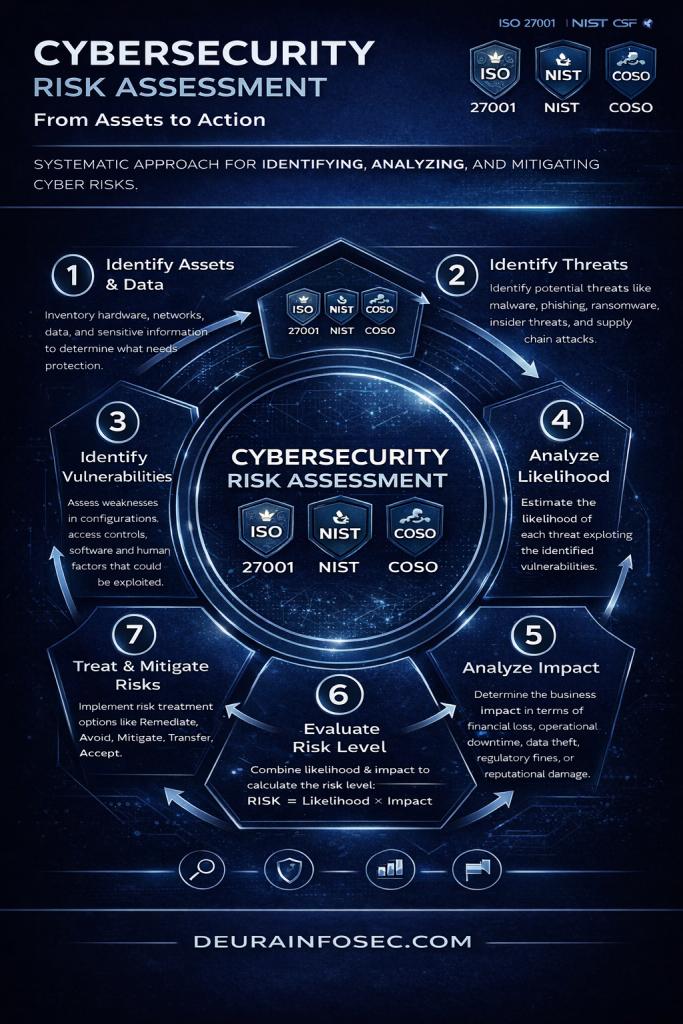
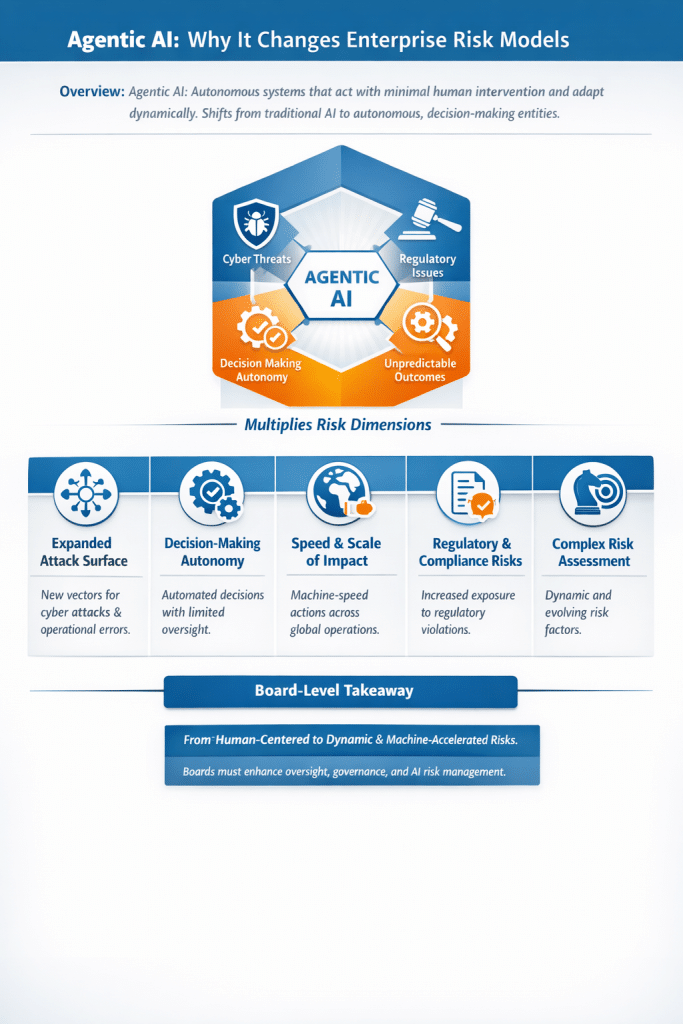
Summary of Sections 2.0 to 5.2 from the ENISA report Cybersecurity of AI and Standardisation, followed by my opinion.
2. Scope: Defining AI and Cybersecurity of AI
The report highlights that defining AI remains challenging due to evolving technology and inconsistent usage of the term. To stay practical, ENISA focuses mainly on machine learning (ML), as it dominates current AI deployments and introduces unique security vulnerabilities. AI is considered across its entire lifecycle, from data collection and model training to deployment and operation, recognizing that risks can emerge at any stage.
Cybersecurity of AI is framed in two ways. The narrow view focuses on protecting confidentiality, integrity, and availability (CIA) of AI systems, data, and processes. The broader view expands this to include trustworthiness attributes such as robustness, explainability, transparency, and data quality. ENISA adopts the narrow definition but acknowledges that trustworthiness and cybersecurity are tightly interconnected and cannot be treated independently.
3. Standardisation Supporting AI Cybersecurity
Standardisation bodies are actively adapting existing frameworks and developing new ones to address AI-related risks. The report emphasizes ISO/IEC, CEN-CENELEC, and ETSI as the most relevant organisations due to their role in harmonised standards. A key assumption is that AI is fundamentally software, meaning traditional information security and quality standards can often be extended to AI with proper guidance.
CEN-CENELEC separates responsibilities between cybersecurity-focused committees and AI-focused ones, while ETSI takes a more technical, threat-driven approach through its Security of AI (SAI) group. ISO/IEC SC 42 plays a central role globally by developing AI-specific standards for terminology, lifecycle management, risk management, and governance. Despite this activity, the landscape remains fragmented and difficult to navigate.
4. Analysis of Coverage – Narrow Cybersecurity Sense
When viewed through the CIA lens, AI systems face distinct threats such as model theft, data poisoning, adversarial inputs, and denial-of-service via computational abuse. The report argues that existing standards like ISO/IEC 27001, ISO/IEC 27002, ISO 42001, and ISO 9001 can mitigate many of these risks if adapted correctly to AI contexts.
However, limitations exist. Most standards operate at an organisational level, while AI risks are often system-specific. Challenges such as opaque ML models, evolving attack techniques, continuous learning, and immature defensive research reduce the effectiveness of static standards. Major gaps remain around data and model traceability, metrics for robustness, and runtime monitoring, all of which are critical for AI security.
4.2 Coverage – Trustworthiness Perspective
The report explains that cybersecurity both enables and depends on AI trustworthiness. Requirements from the draft AI Act—such as data governance, logging, transparency, human oversight, risk management, and robustness—are all supported by cybersecurity controls. Standards like ISO 9001 and ISO/IEC 31000 indirectly strengthen trustworthiness by enforcing disciplined governance and quality practices.
Yet, ENISA warns of a growing risk: parallel standardisation tracks for cybersecurity and AI trustworthiness may lead to duplication, inconsistency, and confusion—especially in areas like conformity assessment and robustness evaluation. A coordinated, unified approach is strongly recommended to ensure coherence and regulatory usability.
5. Conclusions and Recommendations (5.1–5.2)
The report concludes that while many relevant standards already exist, AI-specific guidance, integration, and maturity are still lacking. Organisations should not wait for perfect AI standards but instead adapt current cybersecurity, quality, and risk frameworks to AI use cases. Standards bodies are encouraged to close gaps around lifecycle traceability, continuous learning, and AI-specific metrics.
In preparation for the AI Act, ENISA recommends better alignment between AI governance and cybersecurity governance frameworks to avoid overlapping compliance efforts. The report stresses that some gaps will only become visible as AI technologies and attack methods continue to evolve.
My Opinion
This report gets one critical thing right: AI security is not a brand-new problem—it is a complex extension of existing cybersecurity and governance challenges. Treating AI as “just another system” under ISO 27001 without AI-specific interpretation is dangerous, but reinventing security from scratch for AI is equally inefficient.
From a practical vCISO and governance perspective, the real gap is not standards—it is operationalisation. Organisations struggle to translate abstract AI trustworthiness principles into enforceable controls, metrics, and assurance evidence. Until standards converge into a clear, unified control model (especially aligned with ISO 27001, ISO 42001, and the NIST AI RMF), AI security will remain fragmented and audit-driven rather than risk-driven.
In short: AI cybersecurity maturity will lag unless governance, security, and trustworthiness are treated as one integrated discipline—not three separate conversations.
Source: ENISA – Cybersecurity of AI and Standardisation

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
- The Modern CISO: From Security Operator to CEO-Level Risk Strategist in the Age of AI
- The Real AI Threat Isn’t the Model. It’s the Decision at Scale
- Agentic AI: The New Shadow IT Crisis Demanding Immediate Governance
- Expanding Risk, Shrinking Authority: The Modern CISO Dilemma
- Stop Debating Frameworks. Start Implementing Safeguards