In this Help Net Security interview, Yaron Edan, CISO at REE Automotive, discusses the cybersecurity landscape of the automotive industry, mainly focusing on electric and connected vehicles.
Edan highlights the challenges of technological advancements and outlines strategies for automakers to address cyber threats effectively. Additionally, he emphasizes the importance of consumer awareness in ensuring vehicle security.
Can you describe the state of cybersecurity in the automotive industry, especially in the context of electric and connected vehicles?
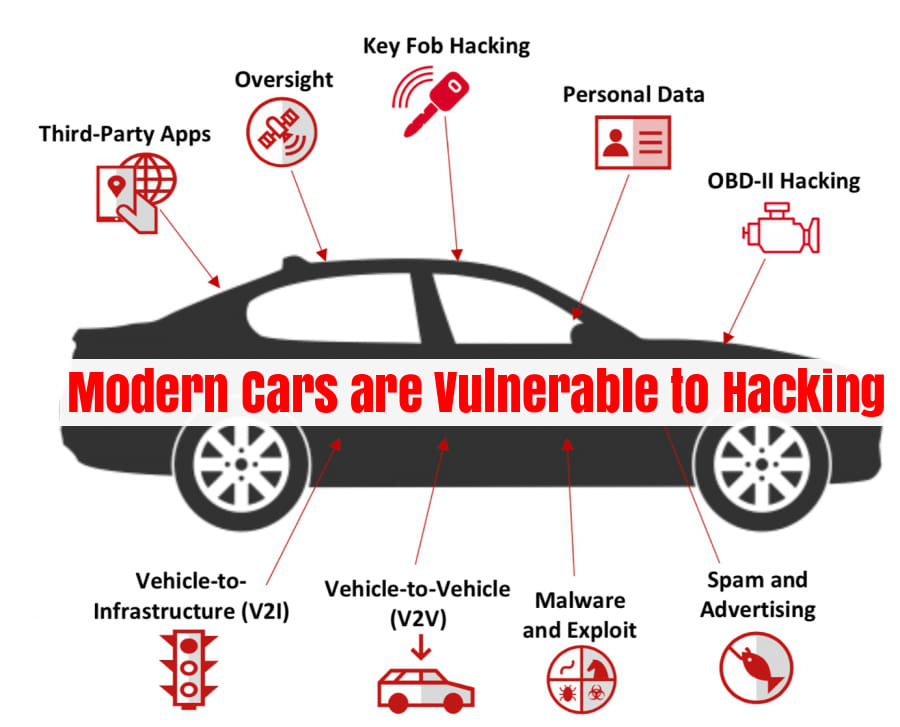
The automotive industry is experiencing a digital breakthrough transforming how vehicles are designed, manufactured, and used, primarily driven by the introduction and popularity of electric and autonomous vehicles. Technological advancements have been introduced and integrated throughout the vehicle life cycle. This brings numerous benefits like enhanced safety and improved efficiency to the cars we drive daily, but it also brings new and pressing cybersecurity challenges.
Now that our vehicles are becoming increasingly connected to the internet can go through Over-the-Air (OTA) updates, use remote management, contain Advanced Driver Assistance Systems (ADAS), and employ AI, the potential avenues for cyberattacks have expanded for threat actors to exploit in a significant way.
What steps are automakers taking to address cybersecurity challenges in their latest vehicle models?
We use different forms and increasing amounts of software in our vehicles. The first challenge is in the supply chain, not just in terms of who provides the software; the issue penetrates each layer. Automakers need to understand this from a risk management perspective to pinpoint the onset and location of each specific risk. Suppliers must be involved in this process and continue to follow guidelines put in place by the automaker.
The second challenge involves software updating. As technology continues to evolve and more features are added, cybercriminals find new ways to exploit flaws and gaps in systems that we may not have been aware of because of the newness of the technology. Regular software updates must be administered to products to patch holes in systems, improve existing vulnerabilities and improve product performance.
In order to address these challenges, automakers need to conduct an initial risk assessment to understand what kind of threats and the type of threat actors are active within each layer of the product and supply chain in the automotive industry. From the experience gained from the initial risk assessment, a procedure must be put in place to ensure each internal and external employee and supplier knows their role in maintaining security at the company.
The procedure determines which types of threat actors are active within the automotive industry, where they are located, and each threat’s severity. This is complicated because threat actors reside worldwide in large numbers, and each group uses various forms of attacks to various degrees. Automakers use the information collected daily to help protect their assets. Additionally, audits must be conducted regularly to evaluate each supplier and employee to verify the procedures are followed correctly, don’t need to be updated, etc.
Can you explain how vehicle manufacturers integrate cybersecurity into the design and development process?
Once you have a factory line running, the first step to integrate cybersecurity into the manufacturing process is to secure the operation technology (OT) policy by understanding the risk and how to close the gaps. Manufacturers must deal with OT threats, which involve thousands of unique threats coming from the product lines, sensors, and other equipment involved in the manufacturing process, instead of systems like computers.
These threats can be especially dangerous if left ignored because of the simplicity of the equipment used in this stage. Suppose you are a threat actor and you want to damage an automaker. In that case, it is much more difficult to conduct a cyberattack on the cloud or the employees of an automaker. Still, the factory line is easier to attack because it uses equipment that is easier to breach and actions are less detected. This is a very common area for threat actors to target.
What key strategies are you recommending for protecting connected and electric vehicles against cyber threats?
Automotive companies must take a proactive approach to addressing cybersecurity threats instead of being reactive. This allows security teams to avoid threats instead of responding later once the damage has already been done. A few proactive strategies I’d recommend for companies are the following.
- Conduct a risk assessment to understand and prioritize current and future risks.
- Develop company-wide security policies and procedures so all employees know their roles in maintaining security.
- Hold regular security training and awareness programs to educate employees.
- Implement strong network security measures, including firewalls, detection systems, and encryption, to monitor your network traffic for any anomalies regularly.
- Regularly backup critical data and store it in secure locations.
- Develop a comprehensive incident response plan outlining steps to be taken during a cyberattack.
- Conduct periodic security audits to evaluate the effectiveness of security measures and identify improvement areas.
Cybersecurity is an ongoing process that requires constant vigilance and adaptation – current strategies will likely become outdated and need to be reworked as new threats emerge.
What role do regulatory bodies play in shaping cybersecurity standards for electric and connected vehicles?
Regulatory bodies play a role in shaping cybersecurity standards, but they do not help you secure your products directly – that is up to each individual player in the automotive supply chain. The goal of regulatory bodies is to provide automakers with best practices on steps to take in the event of a cyber hack, what players to communicate with, and how deep to reach depending on the severity of the threat.
Once an automaker is compliant with certain regulatory rules, they will then ask the regulatory bodies to come to conduct an onsite visit, where they conduct an audit for months at a time, trying to hack each layer they can and look for any areas of weakness, to identify what needs to be patched up. This process needs to be repeated until the automaker is fully compliant.
What are the best practices that consumers should be aware of to ensure the cybersecurity of their electric or connected vehicles?
Consumers need to make sure the data collected in the vehicle stays private. For example, if you have an electric vehicle (EV) and you need to charge it, you might visit a public charging station. Not many people know this, but your vehicle data can be easy to hack at public charging stations because you are not only transferring electricity but also data.
To prevent this from happening, vehicle owners need to ask the right questions. Owning an EV is no different than when a homeowner goes to buy a large kitchen appliance, for example. The right questions need to be asked, including – who made it, whether the company has a cybersecurity procedure in place, whether it is currently compliant with regulatory body requirements, etc. Making sure that all software is regularly up to date is also essential. EV users must download official software from trusted brands using a secure network.
Along with automakers, consumers are partially responsible for their own security, which needs to be stressed to the general public more. Without this knowledge, consumers are left highly vulnerable to hacks from cybercriminals.

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory

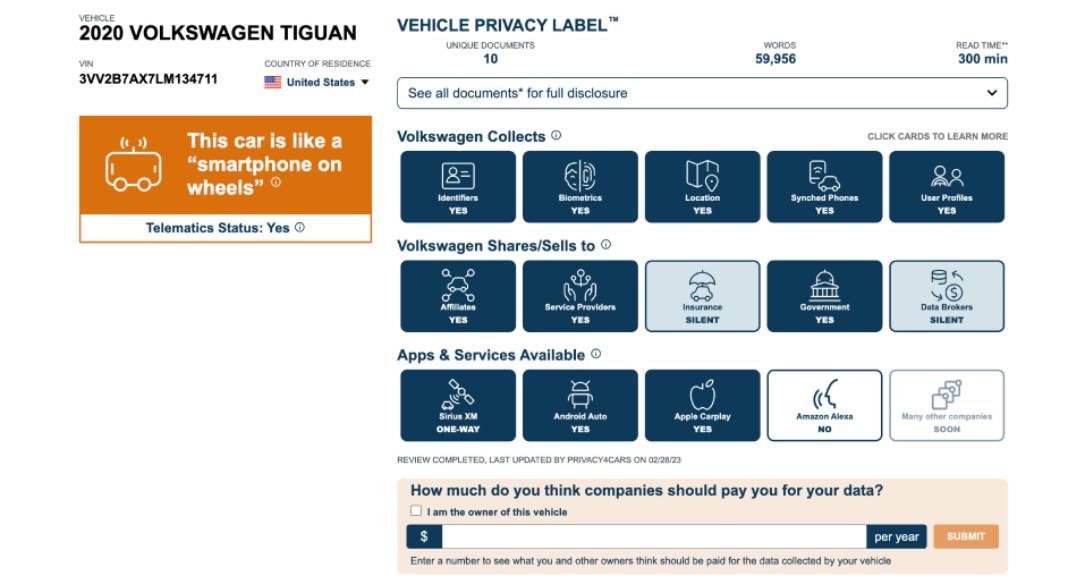 A privacy report for a 2020 Volkswagen Tiguan.
A privacy report for a 2020 Volkswagen Tiguan.